Defender for Endpoint/Defender for Vulnerability Management integration
Microsoft Defender for Endpoint and Microsoft Defender Vulnerability Management integrate natively with Microsoft Defender for Cloud to provide:
- Integrated security capabilities: Security capabilities provided by Defender for Endpoint, Defender Vulnerability Management, and Defender for Cloud come together to provide end-to-end protection for machines protected by the Defender for Servers plan in Defender for Cloud.
- Licensing: Defender for Servers covers licensing for Defender for Endpoint Plan 2. Licensing is charged per hour instead of per user, lowering costs by protecting VMs only when they're in use.
- Agent provisioning: Defender for Cloud can automatically provision the Defender for Endpoint sensor on supported machines that are connected to Defender for Cloud.
- Unified alerts: Alerts and vulnerability data from Defender for Endpoint appear in Defender for Cloud in the Azure portal. You can move to the Defender portal to drill down for detailed alert information and context.
Security capabilities
Defender for Cloud integrates these security capabilities provided by Defender for Endpoint and Defender Vulnerability Management.
Vulnerability management: Provided by Defender Vulnerability Management.
- Features include an inventory of known software, continuous vulnerability assessment and insights, secure score for devices, prioritized security recommendations, and vulnerability remediation.
- Integration with Defender Vulnerability Management also provides premium features in Defender for Servers Plan 2.
Attack surface reduction: Use of attack surface reduction rules to reduce security exposure.
Next-generation protection providing antimalware and antivirus protection.
Endpoint detection and response (EDR): EDR detects, investigates, and responds to advanced threats, including advanced threat hunting, and automatic investigation and remediation capabilities.
Threat analytics. Get threat intelligence data provided by Microsoft threat hunters and security teams, augmented by intelligence provided by partners. Security alerts are generated when Defender for Endpoint identifies attacker tools, techniques, and procedures.
Integration architecture
A Defender for Endpoint tenant is automatically created when you use Defender for Cloud to monitor your machines.
Data collected by Defender for Endpoint is stored in the geo-location of the tenant as identified during provisioning.
- Customer data, in pseudonymized form, might also be stored in the central storage and processing systems in the United States.
- After you configure the location, you can't change it.
- If you have your own license for Defender for Endpoint and need to move your data to another location, contact Microsoft support to reset the tenant.
Move between subscriptions
- Move to a different subscription in the same tenant: To move your Defender for Endpoint extension to a different subscription in the same tenant, delete either the
MDE.Linux' or 'MDE.Windowsextension from the virtual machine and Defender for Cloud will automatically redeploy it. - Move subscriptions between tenants: If you move your Azure subscription between Azure tenants, some manual preparatory steps are required before Defender for Cloud deploys Defender for Endpoint. For full details, contact Microsoft support.
Health status for Microsoft Defender for Endpoint
Microsoft Defender for Servers provides visibility to the Microsoft Defender for Endpoint agents installed on your VMs.
Prerequisites
Onboarding to Microsoft Defender for Servers P2 or Defender CSPM + Microsoft Defender for Servers P1.
Visibility into health issues in Defender for Servers
Microsoft Defender for Servers provides visibility into two main types of health issues:
Installation Issues: Errors during the agent's installation.
Heartbeat Issues: Problems where the agent is installed but not reporting correctly.
Sometimes, Microsoft Defender for Endpoint doesn't apply to certain servers. This status is also shown as described in the last query.
Defender for Servers shows specific error messages for each issue type. These messages explain the problem. When available, you'll also find instructions to fix the issue.
Health status updates every four hours. This ensures the issue reflects the state from the last four hours.
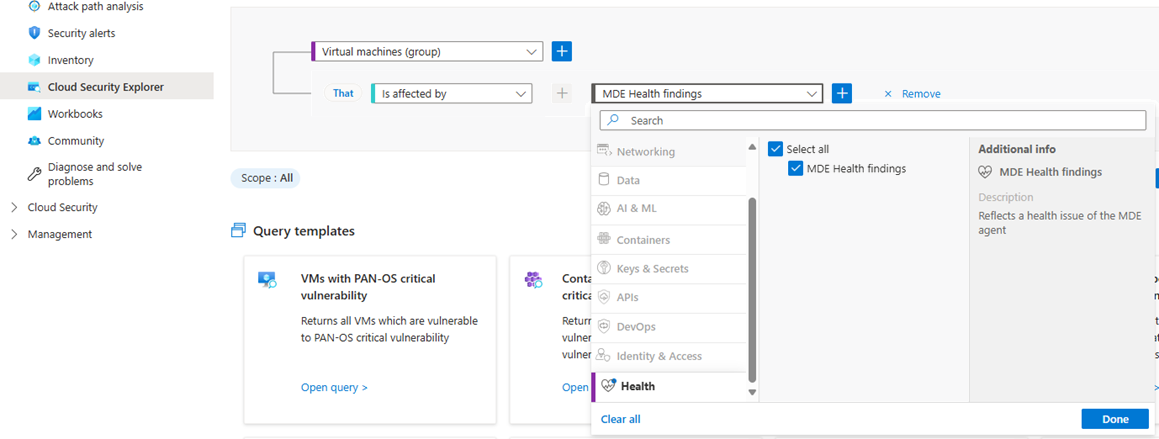
To see Microsoft Defender for Endpoint health issues, use the security explorer as follows:
To find all the unhealthy virtual machines (VMs) with the issues mentioned, run the following query:
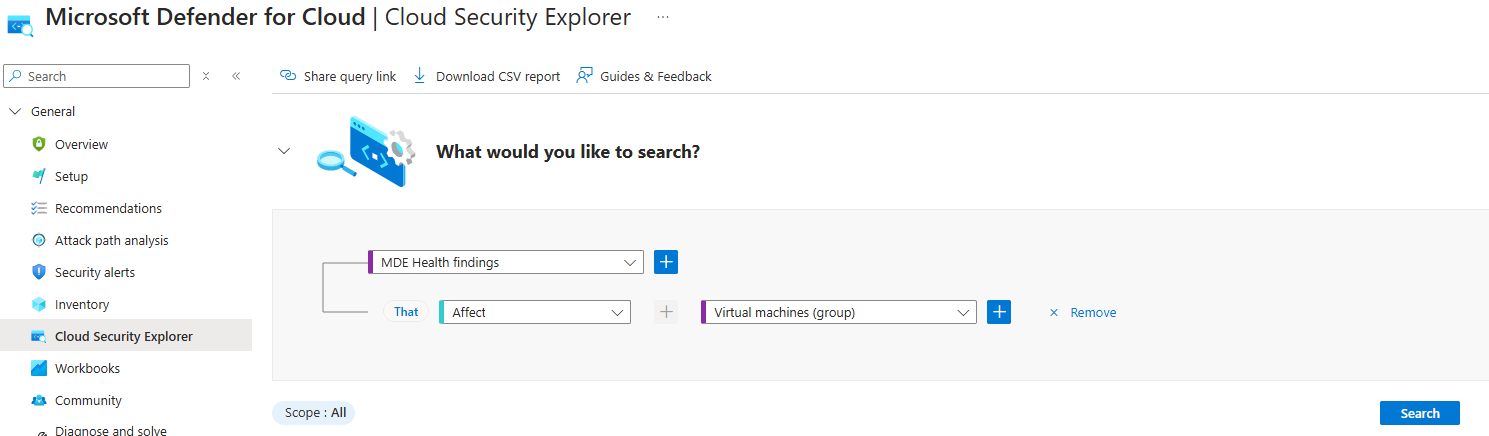
Another way to access this data:
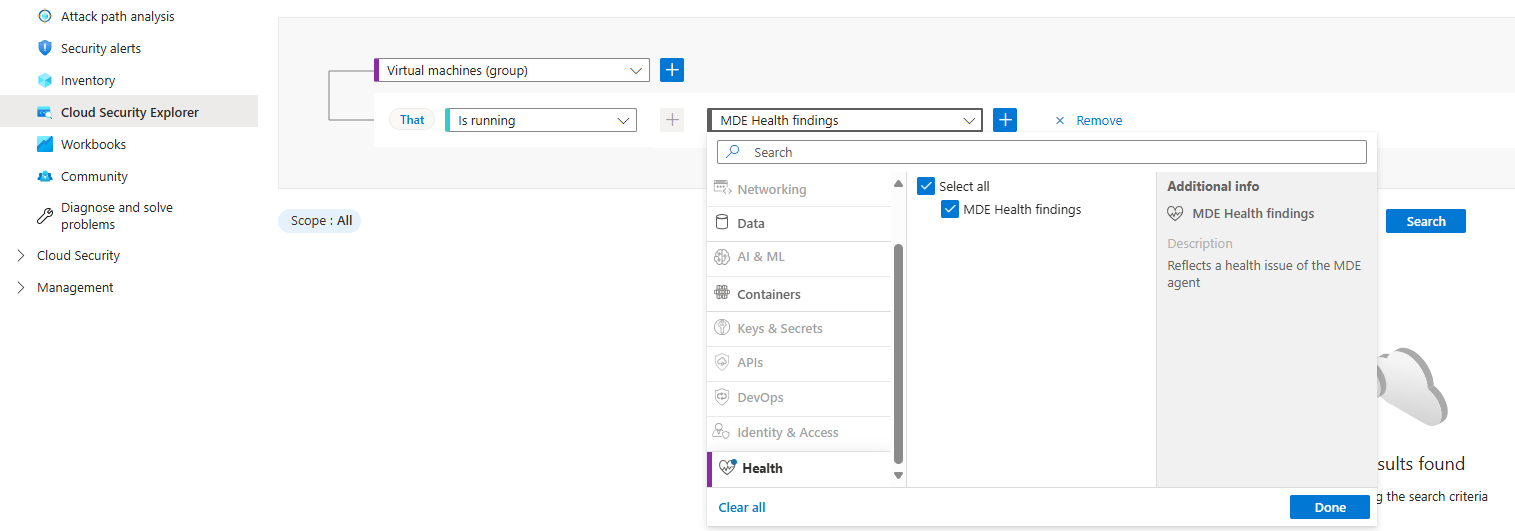
To find all the healthy VMs where Microsoft Defender for Endpoint works correctly, run the following query:
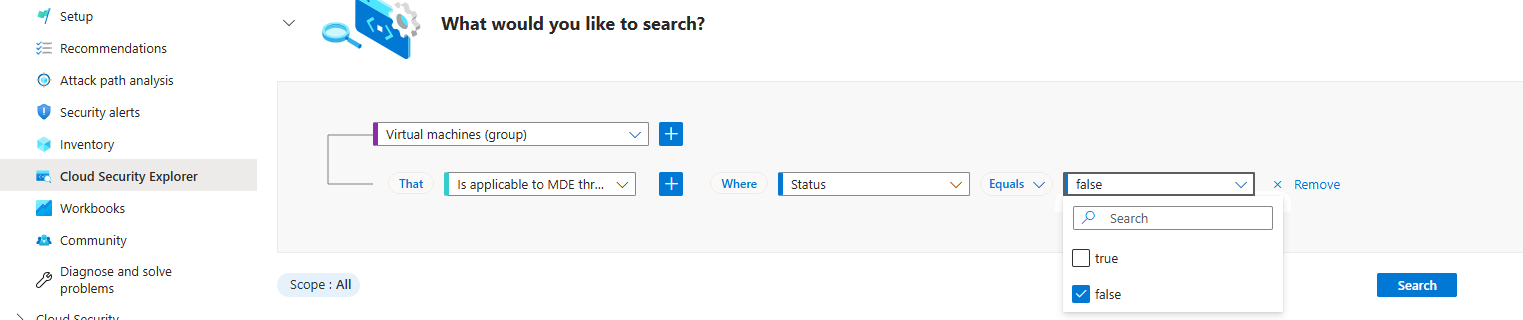
To get the list of VMs where Microsoft Defender for Endpoint isn't applicable, run the following query:
Next steps
Learn more about EDR recommendations in Defender for Servers.