Sync users and groups automatically from Microsoft Entra ID
Important
This feature is in Public Preview. To join this preview, contact your Azure Databricks account team.
This article describes how to configure Azure Databricks to sync users, service principals, and groups from Microsoft Entra ID using automatic identity management.
How do users and groups sync automatically from Microsoft Entra ID?
You can add users, service principals, and groups from Microsoft Entra ID into Azure Databricks without configuring an application in Microsoft Entra ID using automatic identity management. When automatic identity management is enabled, you can directly search in identity federated workspaces for Microsoft Entra ID users, service principals, and groups and add them to your workspace. Databricks uses Microsoft Entra ID as the source of of record, so any changes to group memberships are respected in Azure Databricks.
Users removed from Microsoft Entra ID status shows as Deactivated in Azure Databricks. Deactivated users cannot log in to Azure Databricks or authenticate to Azure Databricks APIs. As a security best practice, we recommend revoking personal access tokens for those users.
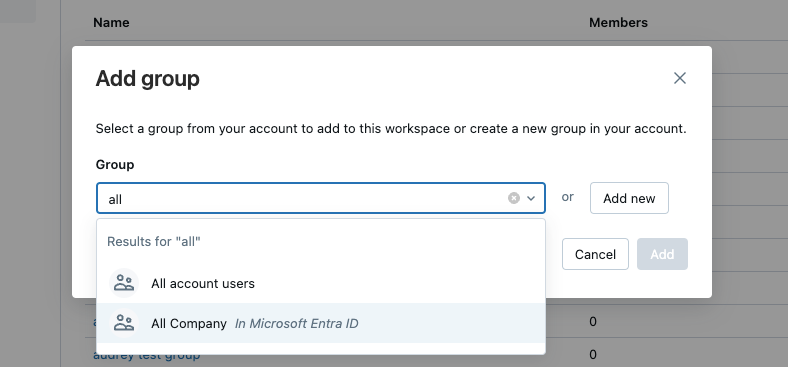
Users can also share dashboards with any user, service principal, or group in Microsoft Entra ID. Those users are automatically added to the Azure Databricks account upon login. They are not added as members to the workspace that the dashboard is in. Members of Microsoft Entra ID who do not have access to the workspace are granted access to a view-only copy of a dashboard published with embedded credentials. For more information on dashboard sharing, see Share a dashboard.
Automatic identity management is not supported in non-identity federated workspaces. For more information on identity federation, see Enable identity federation.
Automatic identity management vs SCIM provisioning
When automatic identity management is enabled, all users, groups, and group memberships sync from Microsoft Entra ID to Azure Databricks so SCIM provisioning is not necessary. If you keep the SCIM enterprise application running in parallel, the SCIM application continues to manage users and groups configured in the Microsoft Entra ID enterprise application. It does not manage Microsoft Entra ID identities that were not added using SCIM provisoning.
Databricks recommends using automatic identity management. The table below compares features of automatic identity management with teh features of SCIM provisioning.
| Features | Automatic identity management | SCIM provisioning |
|---|---|---|
| Sync users | ✓ | ✓ |
| Sync groups | ✓ | ✓ (Direct members only) |
| Sync nested groups | ✓ | |
| Sync service principals | ✓ | |
| Configure and manage Microsoft Entra ID application | ✓ | |
| Requires Microsoft Entra ID Premium edition | ✓ | |
| Requires Microsoft Entra ID Cloud Application Administrator role | ✓ | |
| Requires identity federation | ✓ |
Note
During Public Preview, nested groups are not listed in the Azure Databricks UI. See Automatic identity management UI limitations during Public Preview.
Enable automatic identity management
To enable automatic identity management, contact your Azure Databricks account team. After your account is enabled, to add and remove users, service principals, and groups from Microsoft Entra ID, follow the instructions below:
- Manage users in your account
- Manage service principals in your account
- Add groups to your account using the account console
When automatic identity management is enabled, account admins can disable it, using the Previews page.
- As an account admin, log in to the account console.
- In the sidebar, click Previews.
- Toggle Automatic identity management to Off.
When disabled, users, service principals, and groups previously provisioned remain in Azure Databricks but no longer synchronize with Microsoft Entra ID. You can remove or deactivate these users in the account console.
Audit user logins
You can query the system.access.audit table to audit which users have logged in to the workspace. For example:
SELECT
DISTINCT user_identity.email
FROM
system.access.audit
WHERE
action_name = "aadBrowserLogin"
For more information on the system.access.audit table, see Audit log system table reference.
Automatic identity management UI limitations during Public Preview
Users detail pages are unavailable in the Azure Databricks workspace UI until the user logs in.
When a user is added to a workspace using automatic identity management, their source column appears as “Databricks” instead of “External” until they log in.
Users, service principals, and groups details pages are not available in the Azure Databricks workspace UI if they are indirectly assigned to the workspace through group membership.
If a user, service principal, or group is added to Azure Databricks using automatic identity management and also added to Azure Databricks or another method, such as SCIM provisioning, then they might be listed twice, with one listing appearing inactive. The user is not inactive and can log in Azure Databricks.
Note
In this case, you can merge duplicate users, service principals, and groups by providing their external ID in Azure Databricks. Use the Account Users, Account Service Principals, or Account Groups API to update the principal to add their Microsoft Entra ID objectId in the
externalIdfield.Child group details pages are not available in the Azure Databricks workspace UI.
You cannot add Microsoft Entra ID users, service principals, and groups directly to the account console using the account console UI. However, Microsoft Entra ID identities that are added to Azure Databricks workspaces are automatically added to the account.