Create an application gateway with HTTP to HTTPS redirection using the Azure portal
You can use the Azure portal to create an application gateway with a certificate for TLS termination. A routing rule is used to redirect HTTP traffic to the HTTPS port in your application gateway. In this example, you also create a virtual machine scale set for the backend pool of the application gateway that contains two virtual machine instances.
In this article, you learn how to:
- Create a self-signed certificate
- Set up a network
- Create an application gateway with the certificate
- Add a listener and redirection rule
- Create a virtual machine scale set with the default backend pool
If you don't have an Azure subscription, create a free account before you begin.
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. To get started, see Install Azure PowerShell. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
This tutorial requires the Azure PowerShell module version 1.0.0 or later to create a certificate and install IIS. Run Get-Module -ListAvailable Az to find the version. If you need to upgrade, see Install Azure PowerShell module. To run the commands in this tutorial, you also need to run Login-AzAccount to create a connection with Azure.
Create a self-signed certificate
For production use, you should import a valid certificate signed by a trusted provider. For this tutorial, you create a self-signed certificate using New-SelfSignedCertificate. You can use Export-PfxCertificate with the Thumbprint that was returned to export a pfx file from the certificate.
New-SelfSignedCertificate `
-certstorelocation cert:\localmachine\my `
-dnsname www.contoso.com
You should see something like this result:
PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\my
Thumbprint Subject
---------- -------
E1E81C23B3AD33F9B4D1717B20AB65DBB91AC630 CN=www.contoso.com
Use the thumbprint to create the pfx file:
$pwd = ConvertTo-SecureString -String "Azure123456!" -Force -AsPlainText
Export-PfxCertificate `
-cert cert:\localMachine\my\E1E81C23B3AD33F9B4D1717B20AB65DBB91AC630 `
-FilePath c:\appgwcert.pfx `
-Password $pwd
Create an application gateway
A virtual network is needed for communication between the resources that you create. Two subnets are created in this example: one for the application gateway, and the other for the backend servers. You can create a virtual network at the same time that you create the application gateway.
Sign in to the Azure portal.
Click Create a resource found on the upper left-hand corner of the Azure portal.
Select Networking and then select Application Gateway in the Featured list.
Enter these values for the application gateway:
myAppGateway - for the name of the application gateway.
myResourceGroupAG - for the new resource group.
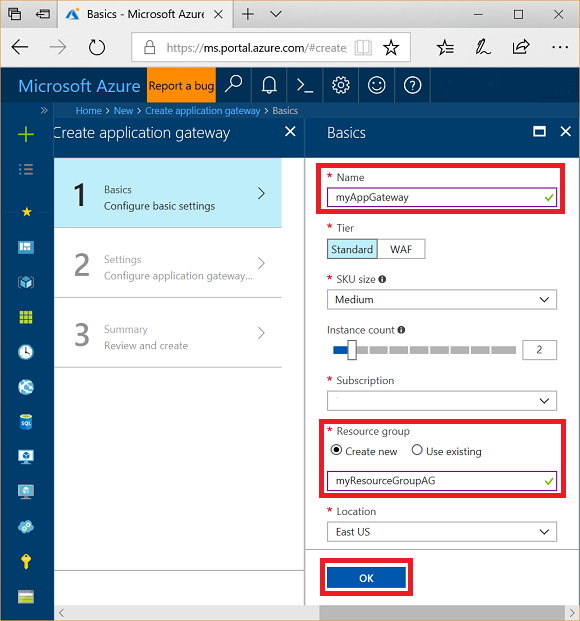
Accept the default values for the other settings and then click OK.
Click Choose a virtual network, click Create new, and then enter these values for the virtual network:
myVNet - for the name of the virtual network.
10.0.0.0/16 - for the virtual network address space.
myAGSubnet - for the subnet name.
10.0.0.0/24 - for the subnet address space.
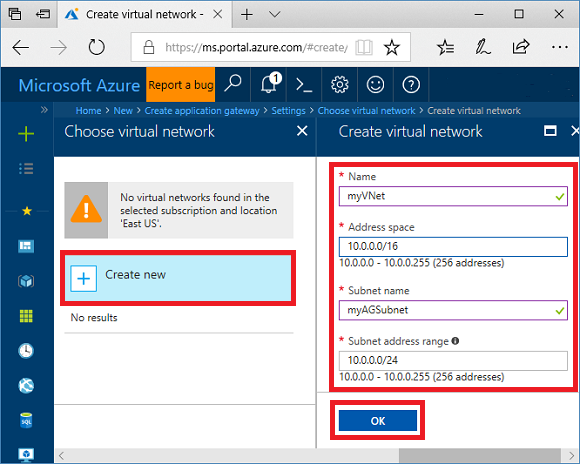
Click OK to create the virtual network and subnet.
Under Frontend IP configuration, ensure IP address type is Public, and Create new is selected. Enter myAGPublicIPAddress for the name. Accept the default values for the other settings and then click OK.
Under Listener configuration, select HTTPS, then select Select a file and navigate to the c:\appgwcert.pfx file and select Open.
Type appgwcert for the cert name and Azure123456! for the password.
Leave the Web application firewall disabled, and then select OK.
Review the settings on the summary page, and then select OK to create the network resources and the application gateway. It may take several minutes for the application gateway to be created, wait until the deployment finishes successfully before moving on to the next section.
Add a subnet
Select All resources in the left-hand menu, and then select myVNet from the resources list.
Select Subnets, and then click Subnet.
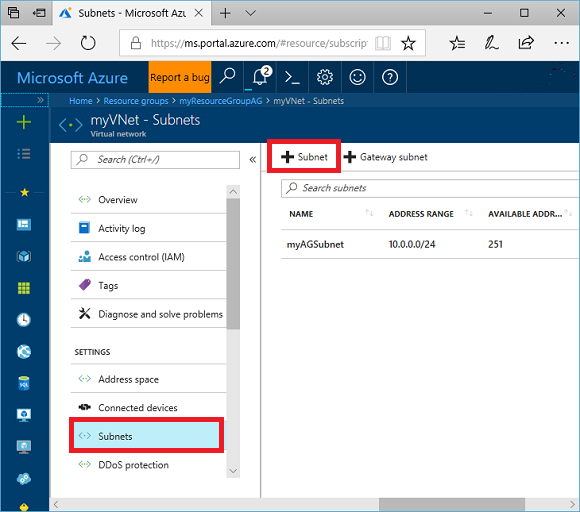
Type myBackendSubnet for the name of the subnet.
Type 10.0.2.0/24 for the address range, and then select OK.
Add a listener and redirection rule
Add the listener
First, add the listener named myListener for port 80.
- Open the myResourceGroupAG resource group and select myAppGateway.
- Select Listeners and then select + Basic.
- Type MyListener for the name.
- Type httpPort for the new frontend port name and 80 for the port.
- Ensure the protocol is set to HTTP, and then select OK.
Add a routing rule with a redirection configuration
- On myAppGateway, select Rules and then select +Request routing rule.
- For the Rule name, type Rule2.
- Ensure MyListener is selected for the listener.
- Click on Backend targets tab and select Target type as Redirection.
- For Redirection type, select Permanent.
- For Redirection target, select Listener.
- Ensure the Target listener is set to appGatewayHttpListener.
- For the Include query string and Include path select Yes.
- Select Add.
Note
appGatewayHttpListener is the default listener name. For more information, see Application Gateway listener configuration.
Create a virtual machine scale set
In this example, you create a virtual machine scale set to provide servers for the backend pool in the application gateway.
- On the portal upper left corner, select +Create a resource.
- Select Compute.
- In the search box, type scale set and press Enter.
- Select Virtual machine scale set, and then select Create.
- For Virtual machine scale set name, type myvmss.
- For Operating system disk image, ensure Windows Server 2016 Datacenter is selected.
- For Resource group, select myResourceGroupAG.
- For User name, type azureuser.
- For Password, type Azure123456! and confirm the password.
- For Instance count, ensure the value is 2.
- For Instance size, select D2s_v3.
- Under Networking, ensure Choose Load balancing options is set to Application Gateway.
- Ensure Application gateway is set to myAppGateway.
- Ensure Subnet is set to myBackendSubnet.
- Select Create.
Associate the scale set with the proper backend pool
The virtual machine scale set portal UI creates a new backend pool for the scale set, but you want to associate it with your existing appGatewayBackendPool.
- Open the myResourceGroupAg resource group.
- Select myAppGateway.
- Select Backend pools.
- Select myAppGatewaymyvmss.
- Select Remove all targets from backend pool.
- Select Save.
- After this process completes, select the myAppGatewaymyvmss backend pool, select Delete and then OK to confirm.
- Select appGatewayBackendPool.
- Under Targets, select VMSS.
- Under VMSS, select myvmss.
- Under Network Interface Configurations, select myvmssNic.
- Select Save.
Upgrade the scale set
Finally, you must upgrade the scale set with these changes.
- Select the myvmss scale set.
- Under Settings, select Instances.
- Select both instances, and then select Upgrade.
- Select Yes to confirm.
- After this completes, go back to the myAppGateway and select Backend pools. You should now see that the appGatewayBackendPool has two targets, and myAppGatewaymyvmss has zero targets.
- Select myAppGatewaymyvmss, and then select Delete.
- Select OK to confirm.
Install IIS
An easy way to install IIS on the scale set is to use PowerShell. From the portal, click the Cloud Shell icon and ensure that PowerShell is selected.
Paste the following code into the PowerShell window and press Enter.
$publicSettings = @{ "fileUris" = (,"https://raw.githubusercontent.com/Azure/azure-docs-powershell-samples/master/application-gateway/iis/appgatewayurl.ps1");
"commandToExecute" = "powershell -ExecutionPolicy Unrestricted -File appgatewayurl.ps1" }
$vmss = Get-AzVmss -ResourceGroupName myResourceGroupAG -VMScaleSetName myvmss
Add-AzVmssExtension -VirtualMachineScaleSet $vmss `
-Name "customScript" `
-Publisher "Microsoft.Compute" `
-Type "CustomScriptExtension" `
-TypeHandlerVersion 1.8 `
-Setting $publicSettings
Update-AzVmss `
-ResourceGroupName myResourceGroupAG `
-Name myvmss `
-VirtualMachineScaleSet $vmss
Upgrade the scale set
After changing the instances with IIS , you must once again upgrade the scale set with this change.
- Select the myvmss scale set.
- Under Settings, select Instances.
- Select both instances, and then select Upgrade.
- Select Yes to confirm.
Test the application gateway
You can get the application public IP address from the application gateway Overview page.
Select myAppGateway.
On the Overview page, note the IP address under Frontend public IP address.
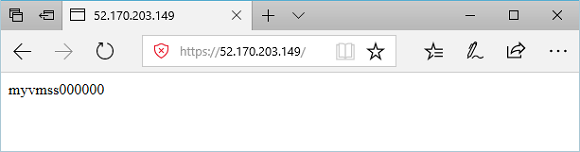
Copy the public IP address, and then paste it into the address bar of your browser. For example, http://52.170.203.149
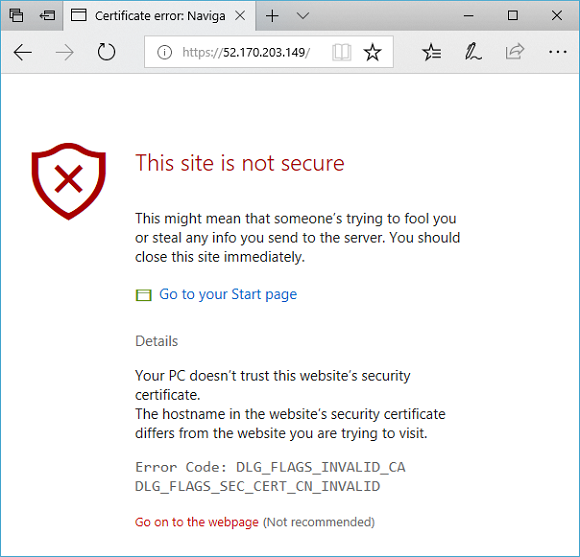
To accept the security warning if you used a self-signed certificate, select Details and then Go on to the webpage. Your secured IIS website is then displayed as in the following example:
Next steps
Learn how to Create an application gateway with internal redirection.