Use app permission policies to control user access to apps
Important
If your organization is moved to app centric management feature to manage access to apps, see Manage access to Teams apps using app centric management. Permission policies will no longer apply and you may see this message on the policy page. If policies are available, you can continue to use those. We will soon let you migrate to app centric management on your own.
As an admin, you can use app permission policies to control the apps that are available to each user in your organization. The permissions you set to allow or block all apps or specific apps are applicable to all types of apps in Teams. To understand policies, see app permission policies. You must be a Teams Administrator or have a higher role to manage these policies.
To let your org users use a Teams app or a copilot agent, you must allow it in:
- Org-wide app settings.
- Individual app's setting.
- In app permission policy.
- In Teams admin center and Microsoft 365 admin center.
The first two settings just allow an app for use in your organization, the permission policies lets you to control which users can use a specific app. You control the access on a per-user and per-app basis by creating and applying the policy to specific users. To make any apps or copilot agents available in your organization, ensure that the settings to allow these are the same in Teams admin center and in Microsoft 365 admin center in the Integrated Apps page.
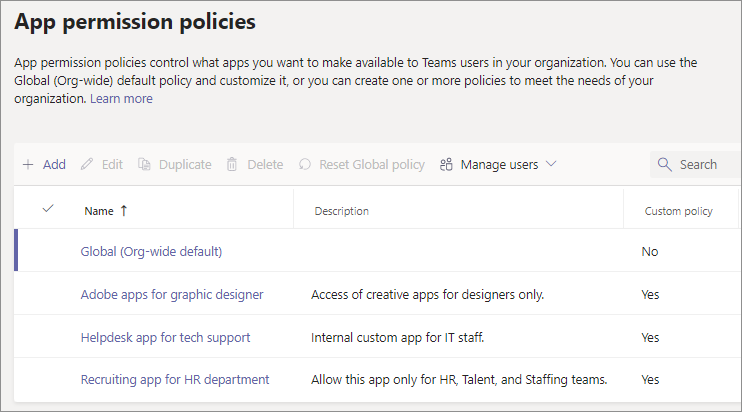
Teams admin center lets you create two types of permissions policies:
Global (Org-wide default) policy exists by default and applies to all users. Any changes made to this policy affect all users.
Custom policy apply only to those users that you apply it to. You create and use custom policies to allow apps to specific users.
If your organization is already on Teams, the app settings you configured in Tenant-wide settings in the Microsoft 365 admin center are reflected in Org-wide app settings on the Manage apps page in Teams admin center. If you're new to Teams and just getting started, by default, all apps are allowed in the org-wide global setting. It includes apps published by Microsoft, third-party software providers, and your organization.
Alternately, you can use app centric management to configure the access to apps on a per-app basis. It offers an easier method to configure access to apps. The app centric management functionality replaces app permissions policies. The feature makes it easier for you to specify the users in their organization who can add or install Teams apps on a per-app basis. You can use only one method to define access to apps in your organization. If you choose to, you can migrate from app permission policies to app centric management using our migration UI.
Note
To know about third-party app settings in Microsoft 365 Government Community Cloud High (GCCH) and Department of Defense (DoD) environment, see Manage org-wide app settings for Microsoft 365 Government.
Create an app permission policy
Use one or more custom app permission policies, if you want to control the apps that are available to different users. You can create and assign separate custom policies based on whether apps are published by Microsoft, third parties, or your organization. After you create a custom policy, you can't change it if third-party apps are disabled in org-wide app settings. To create an app permission policy, follow these steps:
Sign in to the Teams admin center and go to Teams apps > Permission policies.
Select Add.
Provide a name and description for the policy.
Under Microsoft apps, Third-party apps, and Custom apps, select one of the following options:
- Allow all apps or copilot agents
- Allow specific apps or copilot agents and block all others
- Block specific apps or copilot agents and allow all others
- Block all apps or copilot agents
If you selected Allow specific apps and block all others, add the apps that you want to allow:
- Select Allow apps.
- Search for the apps that you want to allow, and then select Add. The search results are filtered to the app developer (Microsoft apps, Third-party apps, or Custom apps).
- After choosing one or more apps, select Allow.
If you selected Block specific apps and allow all others, similarly, search and choose the apps that you want to block, and then select Block.
Select Save.
Edit an app permission policy
You can use the Teams admin center to edit the global policy or any custom policies that you've created. To edit, follow these steps:
- Sign in to the Teams admin center and access Teams apps > Permission policies.
- Select the policy by clicking to the left of the policy name, and then select Edit.
- Make the changes to allow or block specific apps in each of the three categories.
- Select Save.
Assign a custom policy for app permissions to users
App permission policies take effect only when you apply a policy to a user. See the different ways to assign the policy to users.
Teams doesn't support group policy assignments for app permission policies.
View the policies already applied to a user
You can use the Teams admin center to check the policies that are assigned to a user. To view the policies, follow these steps:
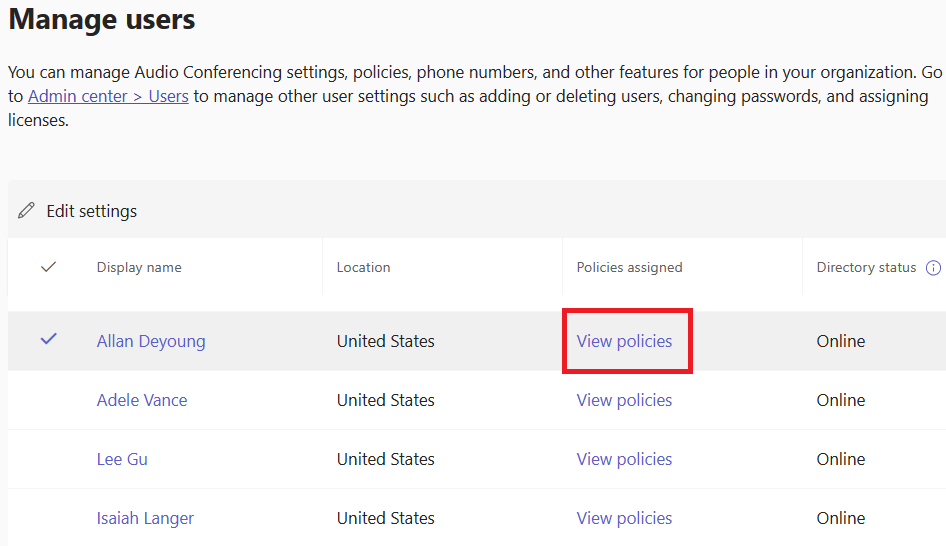
Sign in to the Teams admin center and go to Users > Manage users.
Search for and select the user by clicking the user name.
Select View policies under the Policies assigned column.
Change the existing policies for an individual user
To change existing policies, follow these steps:
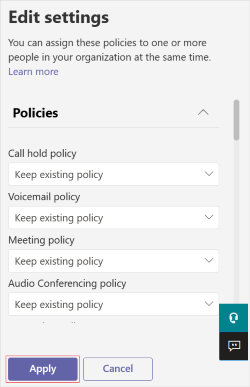
Sign in to the Teams admin center and go to Users > Manage users.
Search for and select the user by clicking to the left of the user name and then select Edit settings.
Select the policy you want to change, and then select Apply.
Note
To unassign a custom policy from a user, you can set each policy to Global (Org-wide default).
You can also change existing policies for an individual user using PowerShell. For more information, see assign policies to users.
Unassign app permission policies in bulk
When you unassign policies in bulk, you're removing policy assignments that were assigned to individual users through direct assignment. To unassign permission policies in bulk, follow these steps:
Sign in to the Teams admin center and go to Teams apps > Permission policies.
Click on the policy's name and then select Bulk unassign users from the Manage users menu.
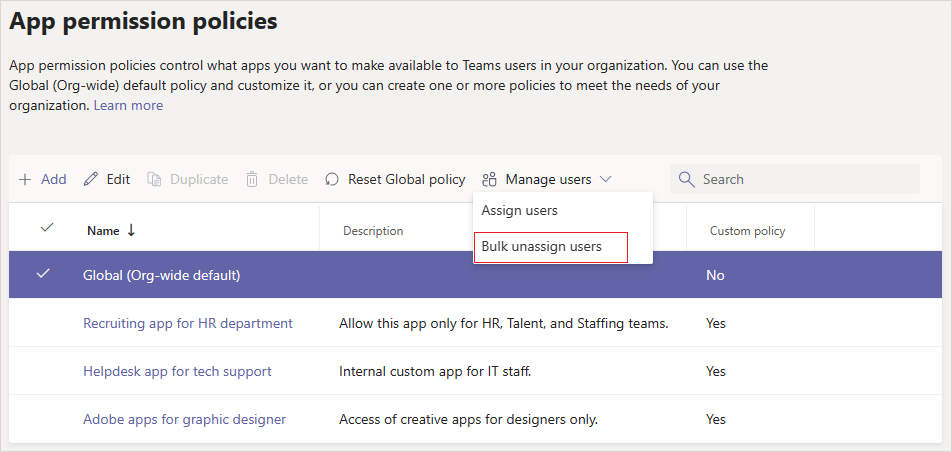
Choose the policy that you want to unassign and select Load data to get the number of users who are currently assigned to that policy.
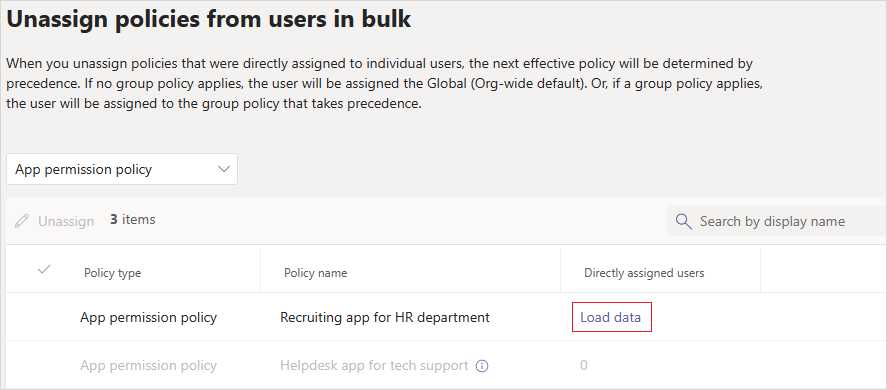
Select Unassign, and then select Confirm.
After you unassign policies, you can review operation details in the Activity log.
Considerations when using app permission policies
The following are a few considerations when using app permissions policies to grant access or to disallow access to apps:
Teams doesn't support group policy assignments for app permission policies.
App permission policies take effect only when you apply a policy to a user.
After you edit or assign a policy, it can take a few hours for changes to take effect.
A user can't interact with any functionality of an app that the user isn't allowed to use.
Users can search for blocked apps and request admin approval. Admins retain complete control to approve or ignore user requests.
App setup policies work together with app permission policies. You select apps to pin in setup policy from a set of allowed apps. However, if a user has an app permission policy that blocks the use of a pinned app, then the user can't use the app.
App policies apply to users using Teams on web, mobile, or desktop clients.