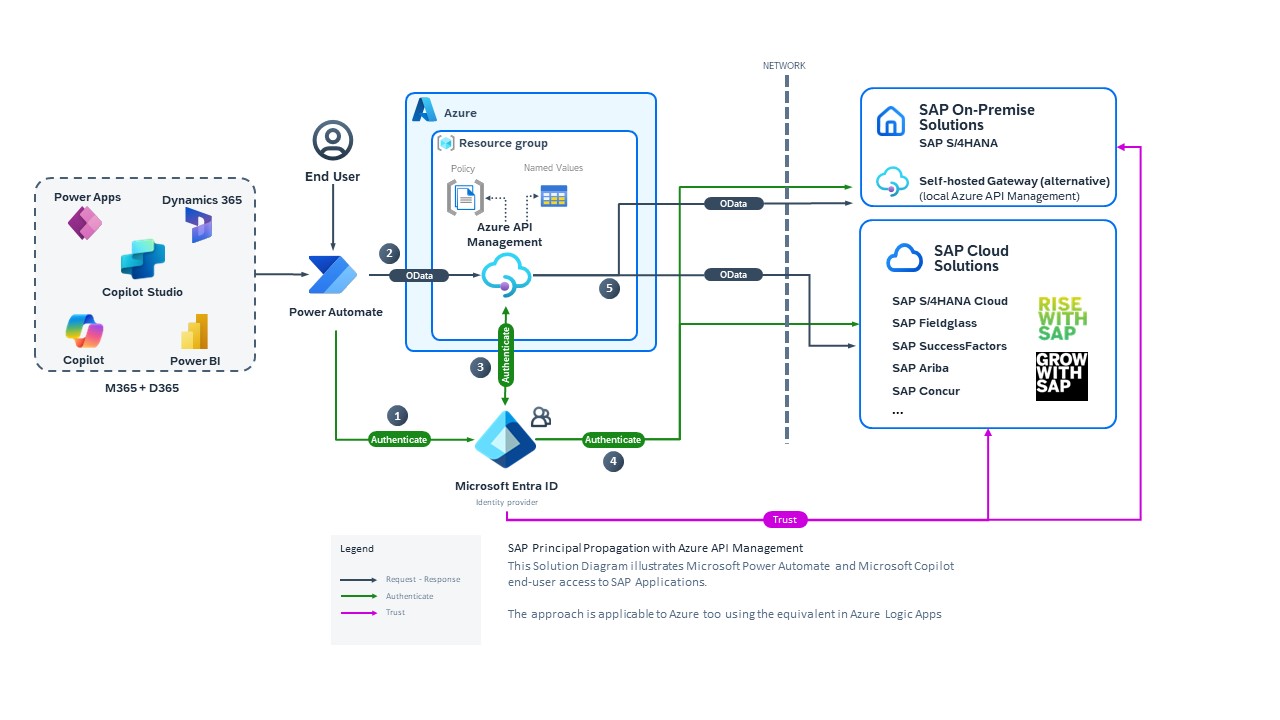
Microsoft Entra ID, Azure API Management und SAP für SSO über den SAP OData-Konnektor einrichten
Sie können den SAP OData-Konnektor für Power Platform so einrichten, dass Microsoft Entra ID-Anmeldeinformationen für Single Sign-On (SSO) bei SAP verwendet werden. Dadurch können Ihre Benutzenden auf SAP-Daten in Power Platform-Lösungen zugreifen, ohne sich mehrmals bei mehreren Diensten anmelden zu müssen. Ihre Berechtigungen und zugewiesenen Rollen in SAP werden dabei trotzdem berücksichtigt.
Dieser Artikel führt Sie durch den Prozess, einschließlich der Einrichtung einer Vertrauensstellung zwischen SAP und Microsoft Entra ID und der Konfiguration von Azure API Management zum Konvertieren des Microsoft Entra ID-OAuth-Tokens in ein SAML-Token, das für OData-Aufrufe an SAP verwendet wird.
Weitere Einblicke und Kontext zum Einrichtungsprozess erhalten Sie auch im Blogbeitrag Hurra! Der SAP OData-Conn unterstützt jetzt OAuth2 und SAP Principal Propagation.
Anforderungen
- SAP-Instanz
- Azure API-Managementressource
Laden Sie die SAML-Metadaten des lokalen Anbieters von SAP herunter
Um eine Vertrauensstellung zwischen SAP und Microsoft Entra ID mit SAML 2.0 einzurichten, laden Sie zunächst die Metadaten-XML-Datei von SAP herunter.
Führen Sie diese Schritte als SAP-Basis-Administrator im SAP GUI aus.
Führen Sie im SAP GUI die Transaktion SAML2 aus, um den entsprechenden SAP-mandantenabhängigen Assistenten zu öffnen. Wählen Sie dann die Registerkarte Lokaler Anbieter aus.
Klicken Sie auf Metadaten, und wählen Sie Metadaten herunterladen aus. Sie werden die SAP-SAML-Metadaten in Microsoft Entra ID in einem späteren Schritt hochladen.
Notieren Sie sich den URI-kompatiblen Anbieternamen.
Anmerkung
Microsoft Entra ID erfordert, dass dieser Wert URI-konform ist. Wenn der Anbietername bereits festgelegt und nicht URI-konform ist, sollten Sie ihn nicht ändern, ohne vorher Ihr SAP-Basis-Team zu konsultieren. Das Ändern des Anbieternamens kann bestehende SAML-Konfigurationen beeinträchtigen. Die Schritte zum Ändern würden den Rahmen dieses Artikels sprengen. Wenden Sie sich an Ihr SAML-Basis-Team, um Unterstützung zu erhalten.
Weitere Informationen finden Sie in der offiziellen SAP-Dokumentation.
SAP-Metadaten in de Microsoft Entra ID-Unternehmensanwendung importieren
Führen Sie diese Schritte als Microsoft Entra ID-Administrator im Azure-Portal aus.
Wählen Sie Microsoft Entra ID>Unternehmensanwendungen.
Wählen Sie Neue Anwendung aus.
Suchen Sie nach SAP Netweaver.
Geben Sie der Unternehmensanwendung einen Namen,und wählen Sie dann Erstellen aus.
Wechseln Sie zu Single Sign-On, und wählen Sie SAML aus.
Wählen Sie Metadatendatei hochladen und dann die Metadatendatei aus, die Sie aus SAP heruntergeladen haben.
Wählen Sie Hinzufügen aus.
Ändern Sie die Antwort-URL (Assertionsverbraucherdienst-URL) in den SAP-OAuth-Token-Endpunkt. Die URL hat das Format
https://<SAP server>:<port>/sap/bc/sec/oauth2/token.Ändern Sie die Anmelde-URL in einen URI-kompatiblen Wert. Dieser Parameter wird nicht verwendet und kann auf einen beliebigen, URI-kompatiblen Wert festgelegt werden.
Wählen Sie Speichern.
Unter Attribute und Ansprüche wählen Sie Bearbeiten.
Vergewissern Sie sich, dass Anspruchsname – eindeutige Benutzer-ID (Namens-ID) auf user.userprincipalname [nameid=format:emailAddress] festgelegt ist.
Wählen Sie unter SAML-ZertifikateHerunterladen für Zertifikat (Base64) und Verbundmetadaten-XML aus.
Microsoft Entra ID als vertrauenswürdigen Identitätsanbieter für OAuth 2.0 in SAP konfigurieren
Gehen Sie wie im Abschnitt Microsoft Entra ID-Dokumentation Abschnitt für SAP NetWeaver und OAuth2 beschrieben vor.
Kehren Sie zu diesem Artikel zurück, sobald der OAuth2-Client in SAP erstellt wurde.
Weitere Informationen finden Sie in der offiziellen SAP-Dokumentation zu SAP NETWEAVER. Beachten Sie, dass Sie eine Fachkraft für die SAP-Administration sein müssen, um auf die Informationen zugreifen zu können.
Erstellen Sie eine Microsoft Entra ID-Anwendung, welche die Azure API-Management-Ressource darstellt
Richten Sie eine Microsoft Entra ID-Anwendung ein, die Zugriff auf den Microsoft Power Platform SAP-OData-Konnektor gewährt. Diese Anwendung ermöglicht es einer Azure API Management-Ressource, OAuth-Token in SAML-Token zu konvertieren.
Führen Sie diese Schritte als Fachkraft für die Microsoft Entra ID-Administration im Azure-Portal aus.
Wählen Sie Microsoft Entra ID>App-Registrierung>Neue Registrierung aus.
Geben Sie einen Namen ein, und wählen Sie Registrieren aus.
Wählen Sie Zertifikate und Geheimnisse>Neuer geheimer Clientschlüssel aus.
Geben Sie eine Beschreibung ein, und wählen Sie dann Hinzufügen aus.
Kopieren Sie dieses Geheimnis und speichern Sie es an einem sicheren Ort.
Wählen Sie API-Berechtigungen>Berechtigung hinzufügen aus.
Wählen Sie Microsoft Graph>Delegierte Berechtigungen aus.
Suchen Sie nach openid und wählen Sie es aus.
Wählen Sie Berechtigungen hinzufügen aus.
Wählen Sie Authentifizierung>Plattform hinzufügen>Web aus.
Legen Sie Umleitungs-URIs auf
https://localhost:44326/signin-oidcfest.Wählen Sie Zugriffstoken und ID-Token und dann Konfigurieren aus.
Wählen Sie API bereitstellen aus.
Wählen Sie neben Anwendung-ID-URIHinzufügen aus.
Übernehmen Sie den Standardwert und wählen Sie Speichern aus.
Wählen Sie Ein Bereich hinzufügen.
Stellen Sie Bereichsnamen auf user_impersonation ein.
Stellen Sie Wer kann zustimmen? auf Administratoren und Benutzer ein.
Wählen Sie Ein Bereich hinzufügen.
Kopieren Sie die Anwendungs- (Client-)ID.
Autorisieren Sie die Azure API Management-Ressource für den Zugriff auf SAP Netweaver mit der Microsoft Entra ID-Unternehmensanwendung
Wenn eine Microsoft Entra ID-Unternehmensanwendung erstellt wird, wird eine entsprechende App-Registrierung erstellt. Suchen Sie die App-Registrierung, welche der Microsoft Entra ID-Unternehmensanwendung entspricht, die Sie für SAP NetWeaver erstellt haben.
Wählen Sie Eine API bereitstellen>Eine Client-Anwendung hinzufügen aus.
Fügen Sie die Anwendungs-ID (Client) der Microsoft Entra ID-App-Registrierung Ihrer Azure API Management-Instanz unter Client-ID ein.
Wählen Sie den Bereich user_impersonation und dann Anwendung hinzufügen aus.
Den Microsoft Power Platform SAP OData-Konnektor für den Zugriff auf APIs autorisieren, die von Azure API Management verfügbar gemacht werden
Wählen Sie in der Microsoft Entra ID-App-Registrierung von Azure API Management die Option API verfügbar machen> aus und fügen Sie die Client-ID des Power Platform SAP OData-Konnektors
6bee4d13-fd19-43de-b82c-4b6401d174c3unter den autorisierten Clientanwendungen hinzu.Wählen Sie den Bereich user_impersonation und wählen Sie dann Speichern aus.
SAP OAuth konfigurieren
Erstellen Sie einen OAuth 2.0-Client in SAP, der es Azure API Management ermöglicht, Token im Namen von Benutzern abzurufen.
Weitere Informationen finden Sie in der offiziellen Dokumentation von SAP.
Führen Sie diese Schritte als SAP-Basis-Administrator im SAP GUI aus.
Führen Sie die Transaktion SOAUTH2 aus.
Wählen Sie Erstellen aus.
Gehen Sie auf der Seite Client-ID wie folgt vor:
- Wählen Sie für OAuth 2.0 Client-ID einen SAP-Systembenutzer aus.
- Geben Sie eine Beschreibung ein, und wählen Sie dann Weiter aus.
Wählen Sie auf der Seite Client-AuthentifizierungWeiter aus.
Gehen Sie auf der Seite Typeneinstellungen gewähren wie folgt vor:
- Wählen Sie für Vertrauenswürdiger OAuth 2.0-IdP den Microsoft Entra ID-Eintrag aus.
- Wählen Sie Aktualisierung zulässig, und dann Weiter.
Wählen Sie auf der Seite Bereichszuweisung die Option Hinzufügen, wählen Sie die OData-Dienste aus, die Azure API-Management verwendet (z. B. ZAPI_BUSINESS_PARTNER_0001), und dann Weiter aus.
Klicken Sie auf Fertig stellen.
Azure-API Management konfigurieren
Importieren Sie die SAP OData-XML-Metadaten in Ihre Azure API Management-Instanz. Wenden Sie dann eine Azure API-Management-Richtlinie an, um die Token zu konvertieren.
Öffnen Sie Ihre Azure API Management-Instanz, und führen Sie die Schritte zum Erstellen einer SAP OData-API aus.
Wählen Sie unter APIsBenannte Werte.
Fügen Sie die folgenden Schlüssel-Wert-Paare hinzu:
| Taste | Wert |
|---|---|
| AADSAPResource | Lokaler SAP-Anbieter-URI |
| AADTenantId | Ihre Mandaten-GUID |
| APIMAADRegisteredAppClientId | Anwendungs-GUID der Microsoft Entra ID |
| APIMAADRegisteredAppClientSecret | Geheimer Clientschlüssel aus vorherigem Schritt |
| SAPOAuthClientID | SAP-Systembenutzer |
| SAPOAuthClientSecret | SAP-Systembenutzerpasswort |
| SAPOAuthRefreshExpiry | Ablauf der Tokenaktualisierung |
| SAPOAuthScope | OData-Bereiche, die während der SAP-OAuth-Konfiguration ausgewählt wurden |
| SAPOAuthServerAddressForTokenEndpoint | SAP-Endpunkt für Azure API-Management, der aufgerufen werden soll, um den Tokenabruf durchzuführen |
Anmerkung
Beachten Sie, dass sich die Einstellungen für SAP SuccessFactors geringfügig unterscheiden. Weitere Informationen finden Sie in der Azure API Management-Richtlinie für SAP SuccessFactors.
Anwenden der Azure API-Management-Tokenrichtlinie
Verwenden Sie Azure API Management-Richtlinien, um ein von Microsoft Entra ID ausgestelltes Token in ein Token zu konvertieren, das SAP NetWeaver akzeptiert. Dafür nutzen Sie den OAuth2SAMLBearer-Flow. Weitere Informationen finden Sie in der offiziellen SAP-Dokumentation.
Kopieren Sie das Beispiel für eine Azure API-Management-Richtlinie von der offiziellen GitHub-Seite von Microsoft.
Öffnen Sie das Azure-Portal.
Wechseln Sie zu Ihrer Azure API-Management-Ressource.
Wählen Sie APIs und dann die ODate-API aus, die Sie zuvor erstellt haben.
Wählen Sie Alle Vorgänge aus.
Wählen Sie unter Eingangsverarbeitung die Option Richtlinien </> aus.
Löschen Sie die vorhandene Richtlinie und fügen Sie die kopierte Richtlinie ein.
Wählen Sie Speichern.
Zugehöriger Inhalt
- SAP-OData-Konnektor
- Der SAP OData-Connector unterstützt jetzt OAuth2 und SAP Principal Propagation | Power Automate Community-Blog
- Azure API Management-Richtlinie für SAP SuccessFactors | GitHub
- SAP OData-Konnektor für SAP SuccessFactors | SAP-Community-Blog
- Der SAP Business Accelerator Hub bietet auch Inhalte rund um die SAP Integration Suite Policy für SuccessFactors und NetWeaver. Sie müssen über ein SAP-Konto verfügen, um auf diese Inhalte zugreifen zu können.