Microsoft Threat Management Gateway (TMG) 2010 - Key Features & Capabilities
Microsoft Forefront Threat Management Gateway 2010 (TMG) is designed to provide a comprehensive, secure Web gateway that helps protect employees from Web-based threats.
Feature Highlight: HTTPS Inspection
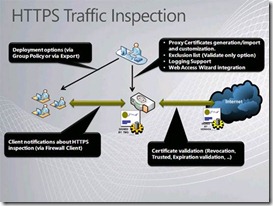
HTTPS Inspection, an innovative feature, enables Forefront TMG to inspect inside users’ SSL-encrypted Web traffic.
By inspecting within these encrypted sessions, Forefront TMG can both detect possible malware as well as limit employee Web usage to approved sites. Sensitive sites, such as banking sites, can be excluded from inspection.
Feature |
Description |
URL Filtering |
Destination URLs are examined for compliance with corporate policy and for malicious potential of destination Web site. Forefront TMG uses Microsoft Reputation Services for URL filtering, combining multiple sources to increase coverage of URLs and categorization. URLs and categories will increase as the Forefront TMG Beta 3 continues through Summer 2009. |
Web antivirus/anti-malware protection |
Inbound and outbound Web traffic is inspected for viruses and malware, including archived folders. Encrypted folders can be blocked. For large files, users are trickled the file to assure them the file is being downloaded. |
E-mail security |
Forefront TMG provides central management for Exchange and Forefront Protection 2010 for Exchange when located on the same server. Forefront TMG does not include either Exchange or Forefront Protection 2010 for Exchange. Both must be purchased and installed separately. |
HTTPS inspection |
HTTPS-encrypted sessions can be inspected for malware or exploits. Specific groups of sites—such as banking sites—can be excluded from inspection for privacy reasons. Users of the TMG Firewall Client can be notified of the inspection. |
Network Inspection System (NIS) |
Traffic can be inspected for exploits of Microsoft vulnerabilities. Based on protocol analysis, NIS enables blocking of classes of attacks while minimizing false positives. Protections can be updated as needed. |
Enhanced Network Address Translation (NAT) |
Forefront TMG now enables you to specify individual e-mail servers that can be published on a 1-to-1 NAT basis. |
Enhanced Voice over IP support |
Forefront TMG includes SIP traversal, enabling simpler deployment of Voice over IP within the network. |
Windows Server 64-bit support |
Forefront TMG is installed on Windows Server 2008 with 64-bit support. |
Feature |
Description |
Multi-layer firewall |
Forefront TMG provides access control and protection on three layers: packet filtering, stateful inspection, and application layer filtering. |
Application layer filtering |
Forefront TMG provides deep content filtering through built-in application filters. |
Granular HTTP controls |
Forefront TMG delivers customizable, granular controls to HTTP traffic, including: - File download controls - Signature-based blocking - HTTP method controls Forefront TMG provides strong controls over Web-based threats. |
DoS protections |
Forefront TMG provides resiliency against flood attacks and re-allocates resources to provide higher security inspection. |
Extensive protocol support |
Forefront TMG delivers out-of-the-box support for many protocols. New protocols can be defined. |
Highly Secure Application Publishing
Feature |
Description |
Highly secure e-mail access from Outlook Client |
Remote users can access Exchange Server using the full Outlook MAPI client over the Internet without establishing a VPN connection. The connection is encrypted for security. |
Simple Outlook Web Access and Microsoft Office SharePoint Server publishing |
Simple wizards allow quick configuration of remote access for both Outlook Web Access and SharePoint servers. Outlook Web Access users can be authenticated at the Forefront TMG server, preventing attacks by unauthenticated users. |
Highly secure publishing of Web servers, internal servers, and Terminal Services |
Remote users can access internal resources or Web servers more securely. Link translation is provided. |
Single sign on |
Forefront TMG allow users to access a group of published Web sites without being required to authenticate with each Web site. |
Delegation of basic authentication |
Forefront TMG helps protect published Web sites from unauthenticated access by requiring the Forefront TMG firewall to authenticate the user before the connection is forwarded to the published Web site. This prevents exploits from unauthenticated users from reaching the published Web server. |
Link translation to internal servers |
Forefront TMG includes a link translation feature that you can use to create a dictionary of definitions for internal computer names that map to publicly known names. Implements link translation automatically during Web publishing. |
SSL bridging support |
To guard against embedded attacks in HTTP traffic, SSL bridging allows SSL protected packets to be decrypted by Forefront TMG, inspected, and re-encrypted. |
Feature |
Description |
Site-to-site VPN |
Forefront TMG enables quick connectivity between sites via wizard-based approach. Also can be configured for tunnel-mode IPSec for support of third party devices. |
Remote access VPN |
Forefront TMG provides termination of L2TP/IPSec and PPTP VPN sessions, using the native Windows VPN services. |
Inspection of VPN traffic |
VPN traffic terminated on the Forefront TMG server is inspected according to the appropriate security policy. |
VPN quarantine |
Forefront TMG provides deep VPN client inspection and integration of your firewall policy. |
SecureNAT for VPN clients |
Forefront TMG helps ensure remote users connected to the network can gain Internet access while maintaining a strong security policy for the corporate network. |
Publish VPN servers |
Forefront TMG can be used to publish internal Windows Servers as VPN servers. |
Feature |
Description |
Enterprise policy |
Policy can be assigned to gateways, arrays, or enterprise-wide. |
Easy-to-use wizards |
Forefront TMG simplifies configuration with multiple wizards for features such as Web publishing, Web access, and array configuration. |
Real-time monitoring and reporting |
Logs may be viewed real-time or historically – including active sessions. |
Query building |
With a built-in query tool, historical data can be found quickly. Complex queries can be built. |
Report creation and publishing |
Reports can be designed for specific needs and then published locally or to a network file share. |
External logging |
Logs may be sent to a Microsoft SQL Server located on the internal network. |
Delegated permissions |
Admin roles can be delegated to users or groups. |
Feature |
Description |
Network load balancing |
Forefront TMG leverages network load balancing to provide fail over and scaling of performance. |
Network-based configuration |
You may configure one or more networks, each with distinct relationships to other networks. Access policies are defined relative to the networks and not necessarily relative to a specific internal network. Forefront TMG extends the firewall and security features to apply to traffic between any networks or network objects. |
Caching |
Forefront TMG provides caching to improve user experience and reduce bandwidth costs. With the centralized cache rule mechanism of Forefront TMG, you can configure how objects stored in the cache are retrieved and served from the cache. |
Background Intelligent Transfer Service (BITS) caching |
Forefront TMG provides the caching mechanism for data received through BITS. Any cache rule that you create can be enabled to cache BITS data. |
HTTP compression |
You can reduce file size by using algorithms to eliminate redundant data during transmission of HTTP packets. |
Diffserv (Quality of Service) |
Forefront TMG includes packet prioritization functionality (provided by the Diffserv Web filter), which scans the URL or domain and assigns a packet priority using Diffserv bits. |
URL Filtering
Quick Introduction
URL Filtering allows controlling end-user access to Web sites, protecting the organization by denying access to known malicious sites and to sites displaying inappropriate or pornographic materials, based on predefined URL categories.
The typical use case for this feature includes:
- Enhancing your security
- Lowering liability risks
- Improving the productivity of your organization
- Saving network bandwidth
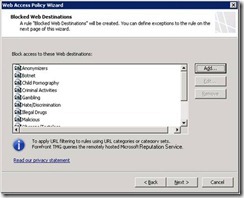
The URL Filtering administration experience is pretty straightforward. All you need to do after enabling the feature is add one or more of the predefined URL categories into Forefront TMG policy (you can find some UI snapshots further below). Once this is done, end-users browsing to a Web site included in one of those categories will be blocked and presented with a relevant notification page, which you can customize.
Additional value can be obtained from URL Filtering related reports and log entries. Have you ever wanted to understand how Web usage in your organization is distributed? And how about identifying those users who consistently violate your Web usage policy? You can do those easily now by looking at the built-in URL filtering reports.
Finally, URL Filtering categories can also be leveraged to exclude sites from being inspected by the HTTPS Traffic inspection and the Malware Inspection features. For instance, you may wish to exclude financial sites from HTTPS inspection, due to privacy considerations.
Before going into further details, note that the feature is still in Beta, so we do expect significant improvements in coverage and accuracy by the final TMG release.
URL categorization data, where does it come from?
TMG features over 80 URL categories ranging from security-oriented selections, like Phishing, Malicious and Anonymizers, through productivity-oriented categories such as Games, or Instant Messaging, and ending with liability-oriented categories like Criminal Activities and Pornography. Categories are also grouped into a higher-level hierarchy which we call Category Sets. The latter can also be used in TMG policy to simplify configuration.
As some of you may have noticed, at the RSA 2009 Conference Microsoft announced its new reputation services and its intention to provide these capabilities for our security products and solutions. Microsoft also announced several key partnerships in the URL filtering space that will be used to support these reputation services. Forefront TMG will be the first system at Microsoft to leverage and utilize Microsoft Reputation Service (MRS).
MRS is a cloud-based object categorization system hosted in Microsoft data centers and designed to provide comprehensive reputation content to enable core trust scenarios across Microsoft solutions. In the case of Forefront TMG, in order to find out the category of a URL, TMG issues an online query to MRS. MRS maintains a database with tens of millions of unique URLs and their respective categories.
Does this mean every end-user request is sent out to the cloud? No it doesn’t. To improve bandwidth utilization and performance, we have implemented a local cache (residing on a TMG server), that stores the recently queried URLs and their respective categories. Cache entries are subject to a time-to-live value, allowing refreshing the entry periodically. This local cache is expected to serve the overwhelming majority of user requests. The cache is persistent so it doesn't need to be refreshed after each reboot. TMG will query MRS only when a request cannot be served from the local cache.
But that's only the tip of the iceberg. Read on to find out why we think we are building something special with TMG and MRS together.
What is so special about Microsoft Reputation Service (MRS)?
The MRS team wanted to confront an inherent problem with traditional URL Filtering solutions: the problem domain is simply too large for any single vendor to provide a complete solution on its own. As a result, there are multiple vendors out there, each one specializing in a specific area of the solution.
Some vendors specialize in identifying malicious sites and spam URLs; others are rich with productivity related categories. Some specialize in covering the Internet's “long tail”; others are great with quick classification of previously unknown sites. Some use human-based classification where others use machine-based techniques. Some are great with Web2.0 style URLs… OK, I'll stop here as you get the idea by now. Even those vendors who employ several classification techniques and cover multiple categories can't deal with the huge and ever-expanding challenges of today's Web.
MRS team's idea was simple; let's leverage complementary capabilities of different vendors/sources to create a unified database that is best suited to deal with the challenges described above. And so, they have implemented a scalable architecture that allows incorporating multiple streams of data into a merged database. This way – each vendor/source brings its unique strengths to the table into a common solution.
MRS already integrates several data sources and others will be on-boarded in the following months. Some of these data sources are Microsoft internal, and others are the result of collaboration with 3rd party partners. One such agreement, announced during RSA, is an agreement with Marshal8e6. Other agreements have not been disclosed yet. Expect some surprises...
But the real beauty is that being a Web service, and given its unique architecture, MRS can easily incorporate new DBs completely transparently to the customers. We expect the MRS unified database to expand over time and become the recognized industry leader. TMG customers will benefit naturally from this ongoing upgrade, through our Web security subscription services.
Other interesting aspects – security, privacy, licensing
Security – Both Forefront TMG URL Filtering and MRS were designed with security in mind, following Microsoft's Security Development Lifecycle (SDL) strict standards and guidelines. Both are resilient to a variety of attacks, and the communication between the two is encrypted.
Privacy – this is a known concern when discussing cloud based services, and therefore the privacy of our customers' data is paramount. We are issuing detailed privacy statements along with the Beta 3 release to provide clarity and transparency on our privacy policies. Make sure to read those.
Licensing – URL Filtering is subscription based, and is part of the Forefront TMG Web Security Service license (together with the Malware Inspection updates).
The small (but important) things
As this is a high-level overview of the feature, we will not dive into all the small details that make for a complete, rich user experience. We will cover some of those in subsequent posts, as we go along. But here are few examples for flexibility you are likely to need/want when working with URL Filtering:
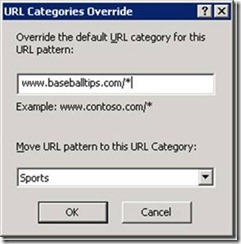
- You can locally override a URL category
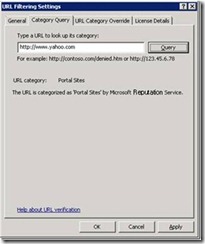
- You can query for a URL's category in the TMG UI
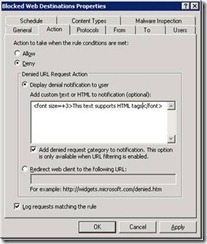
- You can customize the block page displayed to end-users, introducing your own HTML tags into the text area.
- You can leverage URL Filtering for ad blocking
- You can use the build-in TMG scripting capabilities to allow non-TMG administrators to locally override a URL (enabling advanced help-desk scenarios)
- You can use URL Filtering related reports to figure out how your organization uses the Internet (which are the top browsed categories for instance)
ü You can report classifications issues to Microsoft (this one is not available in Beta3)
A sneak peek at the UI
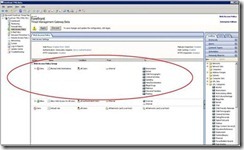
TMG Web Access Wizard allows you to easily introduce URL categories into your policy:
This is how the policy may look like after completing the Web Access Wizard (viewed from the Web Access Protection node). Note that URL Categories are standard TMG network objects, so you can use the toolbox on the right to drag-drop additional categories into an existing rule, or to create new rules.
You can query for a URL's category (available as a task in the Web Access Protection node)
You can locally override a URL's category (available as a task in the Web Access Protection node)
You can customize the block page presented to end users, introducing your own HTML tags (this is a per-rule setting available from the ‘Action’ tab of the rule’s properties)
Comments
- Anonymous
March 23, 2016
can be block web and ip and Mac address ?
or not

![clip_image003[1] clip_image003[1]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/zafaru/WindowsLiveWriter/11941080e992_DF5F/clip_image003%5B1%5D_thumb.gif)
![clip_image003[2] clip_image003[2]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/zafaru/WindowsLiveWriter/11941080e992_DF5F/clip_image003%5B2%5D_thumb.gif)
![clip_image003[3] clip_image003[3]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/zafaru/WindowsLiveWriter/11941080e992_DF5F/clip_image003%5B3%5D_thumb.gif)
![clip_image003[4] clip_image003[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/zafaru/WindowsLiveWriter/11941080e992_DF5F/clip_image003%5B4%5D_thumb.gif)
![clip_image003[5] clip_image003[5]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/zafaru/WindowsLiveWriter/11941080e992_DF5F/clip_image003%5B5%5D_thumb.gif)