Can Microsoft IT be infected by computer viruses? – The answer is YES!
Hello, This is Yurika, security program manager at Customer Services and Support.
At Microsoft, there are more than 150,000 employees across more than 100 countries and regions worldwide, and over 600,000 devices are used internally (Microsoft IT). The most advanced software and technology is used in the internal IT environment, and latest security measurements are implemented, both physically and technically.
Therefore, people sometimes ask me, “Microsoft can never be infected by computer viruses, right?”
The answer is “NO”! Around 2 million viruses were detected, and 41 cases of infection were confirmed at Microsoft in the second half of 2015.
Malware Infections at Microsoft
In Microsoft internal IT environment, real-time antimalware software (anti-virus software) is required on all user devices that connect to the Microsoft corporate network. User computers must be running the latest version of the software, antimalware signatures must be no more than six days old. Windows Defender and System Center Endpoint Protection 2012 (SCEP) that come with Windows 8 and later, are the antimalware solutions that Microsoft IT deploys to its users (Windows Defender and SCEP have the same signature file and engine). The average monthly level of antimalware compliance rate at Microsoft exceeded 98 percent each month during the second half of 2015 (from July to December).
Concerning malware infection, there were two million malware detection reports in the second half of 2015. These are known malware that are detectable and blocked by signature files.
There are also new types of malware that are not reflected to the signature database. In that case, malware is not recognized when it first penetrates the computer, but is detected at timings such as regular scanning after the signature file is updated. 41 cases of such malware infection were confirmed in the second half of 2015. These infections are blocked by real-time protection of antimalware software that recognized the "suspicious behavior", and threats are blocked by Windows mitigation features or intrusion detection systems such as Windows Defender Advanced Threat Protection.
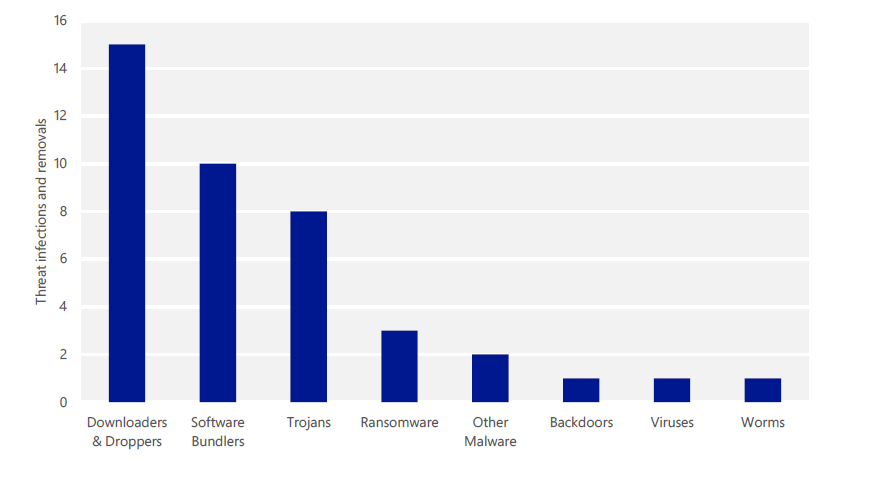
Infections and removals at Microsoft in 2H 2015, by category
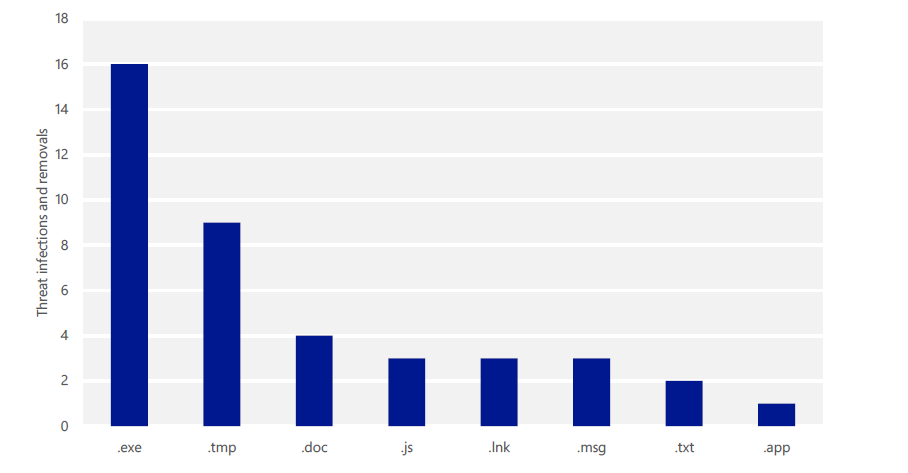
Infections and removals at Microsoft in 2H 2015, by file type
Not only Antimalware, but Defense-in-depth Measures
Antimalware software has no meaning if malware infection is not completely eliminated. That is definitely not the case. Antimalware software serve an important role as the first fort to prevent intrusion to devices. Also, it plays a key role as to disinfect malware as well as detecting it. In fact, the 2 million detections in Microsoft internal IT environment are known malware, and because antimalware software was running properly, intrusion was prevented.
On the other hand, it is true that many sophisticated attacks are designed to avoid detection by antimalware software, and technology of the software cannot prevent all attacks. That is the cause of the 41 infection cases at Microsoft.
To efficiently secure the enterprise environment, first understand the antimalware software execution status and its effect. Then, on the assumption that intrusion caused by virus infection will occur, it is important to implement security measures "in-depth". Microsoft analyzed how the 41 infection cases happened and how we can prevent the damage caused by the infections, and reflected the results to defense-in-depth measures.
Here are our top ten examples of the security measures implemented at Microsoft internal IT environment:
- Ensure that all software deployed on computers in the environment is updated to the latest version and has applied the latest security updates.
- Ensure that both Microsoft products and non-Microsoft products are updated to the latest version.
- Centralize management of users and devices using Active Directory. Use Group Policy, Intune to apply updates, and to enable security features such as firewall or SmartScreen.
- Enable antimalware software.
- Enable Windows Defender Cloud Protection in Windows 10 and configure it so that the signature files are updated real-time.
- Use the intrusion detection system.
- Use Windows Defender Advanced Threat Protection (Windows 10) to quickly detect and address threats that are not detected by antimalware software.
- Consider the necessity of technology that might become a clue to attacks, such as Java and Flash, and develop a plan to minimize its use.
- Use AppLocker to block the installation and use of unwanted software such as peer-to-peer (P2P) applications.
- Implement the Enhanced Mitigation Experience Toolkit (EMET) on important systems, to minimize exploitation of unknown vulnerabilities in your environment.
- Implement strong password policies, and strengthen authentication as necessary by using multi-factor authentication or smart cards to protect credentials.
- Enable Windows PowerShell v5 security features via Windows Management Framework 5.0:
- Script Block Logging
- System-Wide Transcripts
- Constrained PowerShell
- Antimalware integration (AMSI)
The Goal of Security is not to reach for "Zero Infection"
The security goal of Microsoft internal IT environment is not making the open rates of targeted mail to zero, nor to boost the antimalware compliance rate to 100% and prevent all virus infection.
For example, the average monthly antimalware compliance rate at Microsoft exceeded 98 percent during the second half of 2015. But we believe that attempting to boost the compliance rate of an organization with more than 600,000 devices will likely be a costly endeavor and not realistic to operate. We are aware that a certain number of users (e.g. 2 percent at Microsoft IT) have devices that do not comply with the policies, and aim to reduce the risks by implementing defense-in-depth measures.
The goal of attackers is not malware infection; it is to steal information and make money by using malware. Therefore, our goal is to prevent the attacker to achieve their goal. That is to say, to prevent information disclosure caused by security breaches, and to minimize damage when such breach occurs.
It is important to measure effectiveness of basic security measurements and to plan on the assumption that intrusion will occur. Implementing antimalware measurements only or setting uniformed numerical targets is not essential. Microsoft believes that setting a goal for overall operation and measurement from the big picture, analyzing the effectiveness, periodically reviewing and improving measurements is the key to enterprise security.
For more information on the malware infection in the Microsoft IT environment, be sure to check out "Microsoft Security Intelligence Report". We hope it will help management of your IT environment!
Malware free is the best way to be!
-Yurika