Stop hurting yourself by: Locking down security in IE11 to the point that you need a 2nd or 3rd browser in your environment.
Applies to:
Windows 10 1809 (October 2018, codename RS5) / Windows Server 2019
Windows 10 1803 (tbd, codename RS4)
Windows 10 1709 (Fall Creators update, codename RS3)
Windows 10 1703 (Creators update, codename RS2)
Windows 10 1607 (Anniversary update, codename RS1) / Windows Server 2016
Windows 10 1511 (November update, codename TH2)
Windows 10 1507 (RTM, codename TH1)
Windows 8.1/Windows 2012 R2
Windows 8/Windows 2012
Windows 7 SP1/Windows 2008 R2 SP1
Windows Vista/Windows 2008
As a Premier Field Engineer (PFE), I get to go on-site and from time to time, I get to troubleshoot Internet Explorer 11 related issues.
Symptoms:
A common issue that I have noticed is that Internet Explorer 11 (IE11) has ‘security’ lock down to the point that some Webpages and Web-based Line of Business (LoB) applications don't render properly.
And what do architects, IT admin’s, Helpdesk, Field Techs end-up doing? Installing one or more 3rd party browser to work-around it.
Cause:
1) The most common mistake that I see in most environments is that the Security/Windows architect(s) goes ahead and applies one of these "Security policies" to the new Windows 10 or Windows Server 2016/2019 images without any testing of their Line of Business (LoB) applications.
· Security baseline (DRAFT) for Windows 10 v1809 and Windows Server 2019
· Security baseline for Windows 10 “April 2018 Update” (v1803) – FINAL
· Security baseline for Windows 10 “Fall Creators Update” (v1709) – FINAL
· Security baseline for Windows 10 “Creators Update” (v1703) – FINAL
· Security baseline for Windows 10 v1607 (“Anniversary Update”) and Windows Server 2016
· Security baseline for Windows 10 (v1511, "Threshold 2") — FINAL
· Security baseline for Windows 10 (v1507, build 10240, TH1, LTSB) — UPDATE
· Security baselines for Windows 8.1, Windows Server 2012 R2 and Internet Explorer 11 – FINAL
Note: This applies to Windows 10 and Windows Server 2016/2019 related security lock down too. You can’t just apply ‘security lock downs” and expect things to just work. You will have to take the time, go through, relax things for Business Productivity while you pursue with the ISV(s) or in-house developer(s) on getting it working.
What are some common issues? The "Security Zones".
The IE11 security baseline ends up changing:
· Windows Components > Internet Explorer > Internet Control Panel > Security Page > Internet Zone
· Windows Components > Internet Explorer > Internet Control Panel > Security Page > Locked-Down Internet Zone
As described in:
182569 Internet Explorer security zones registry entries for advanced users
Any webpage(s) that have a FQDN (e.g. contoso.com or fabrikam.com) or an IP address (e.g. 10.x.x.x or 20x.x.x.x), by default end-up in the “Internet Zone”.
TIP: Yeap, even if it’s internal websites.
So how do I find out what IE security zone that the webpage is in?
2689449 How to display zone information in Internet Explorer 9
Note: This applies to "Internet Explorer 11" too.
2) Or end-up upgrading from IE7/IE8/IE9/IE10 to IE11 without any testing.
Solution (Preferred):
Start out with this great blog post by Pieter Wiegleven:
The Ultimate Browser Strategy on Windows 10
The best way to fix these, is to go ahead and run “Update Readiness” to see what websites that your end-users are browsing to…
Windows Analytics - Update Readiness - Internet Explorer data collection
Then set the correct IE document mode. What IE document mode to select? And Deprecated document modes and Internet Explorer 11
And then deploy it to your environment using Enterprise Mode IE (EMIE) Enterprise Mode and the Enterprise Mode Site List
Work-around (Alternative):
Back in the ‘old’ days, a lot of folks ended up using “Internet Explorer Maintenance”:
Note: This was registry tattooing from the Windows NT4/2000 days.
Which let Helpdesk and/or Field techs, and/or end-users go to “Tools > Internet Options > Security tab > Trusted Sites” and add the websites that were having problem rendering.
But “Internet Explorer Maintenance” has been deprecated as documented here:
Missing Internet Explorer Maintenance settings for Internet Explorer 11
It was replaced with the following option:
Computer or User Configuration > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page > Site to Zone Assignment List
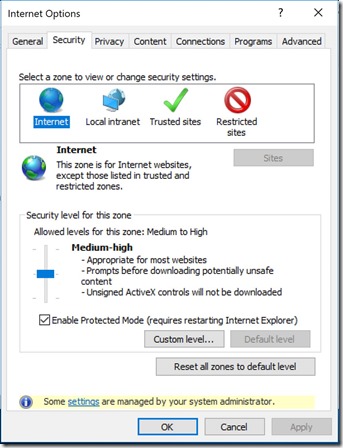
Notice the “Some settings are managed by your system adminitrator”.
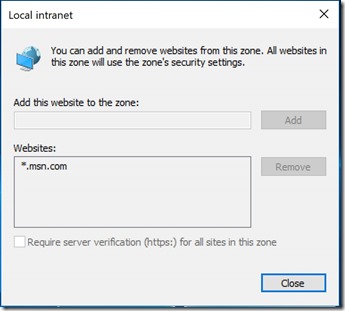
Now if you click on “Local intranet” or “Trusted sites”, its grayed out as shown on the screen captures below:
This limits on how quickly the Helpdesk/Field techs/End-users could help themselves.
As a Windows Architect or Windows IT Admin, you have the following option:
Instead of “Computer or User Configuration > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page > Site to Zone Assignment List”, use Group Policy Preferences registry keys to set the “Local Intranet” and/or “Trusted Sites”
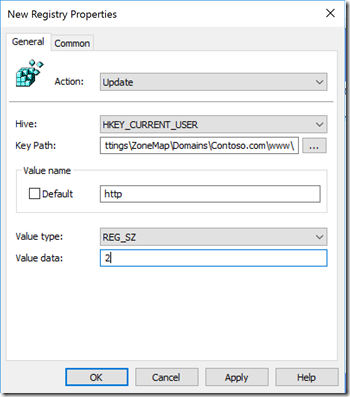
Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\TheWebsiteName.com\www\
e.g.
Next to Hive: Select “HKEY_CURRENT_USER” or “HKEY_LOCAL_MACHINE”. In this example, I’m using “HKEY_CURRENT_USER”.
Next to “Key Path:” type “Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\Contoso.com\www\” w/o the double quotes.
Next to “Value name”, I have “http” here, but you could replace it with “https” or “*” (http and https).
Next to “Value data:” set it to 2
Note: Your options are (1) Intranet zone, (2) Trusted Sites zone, (3) Internet zone, and (4) Restricted Sites zone.
Reference:
How to configure Internet Explorer security zone sites using group polices
This will provide the helpdesk/field techs/end-users to be able to fix it themselves.
Ok, for you helpdesk/field techs that need to get this fixed temporarily while it goes through the change control process. What are your options?
If you have “Local Admin” rights, you could go to:
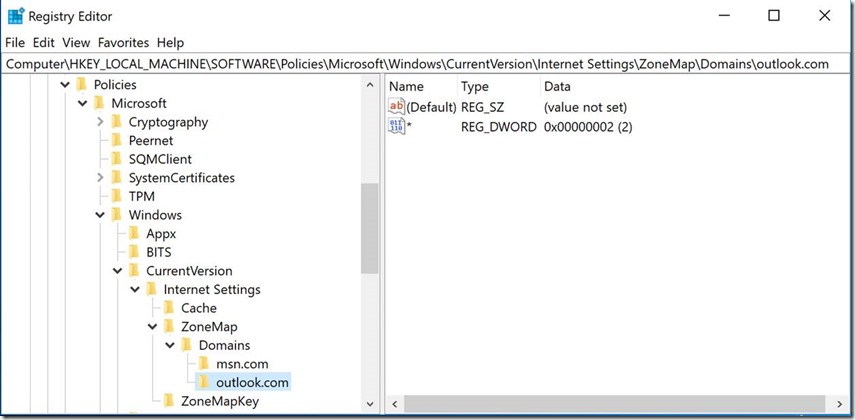
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\Contoso.com\
http (dword) 2 (hex)
or
https (dword) 2 (hex)
or
* (dword) 2 (hex)
Note: Your options are (1) Intranet zone, (2) Trusted Sites zone, (3) Internet zone, and (4) Restricted Sites zone.
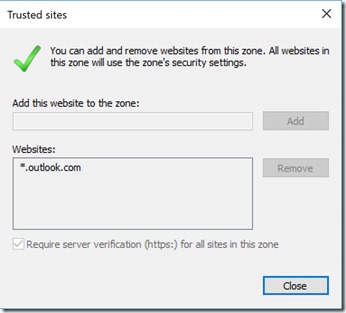
In this example, I’m showing Outlook.com, and using * which will put https://www.Outlook.com and https://www.Outlook.com in the “Trusted Sites” zones.
Thanks,
Yong Rhee (while I was in Oregon)
P.S. Other “Stop hurting yourself by:” blog posts
Stop hurting yourself by: Setting the Account lockout to 3
Stop hurting yourself by: Not applying the non-security updates for Windows and Windows Server.
Stop hurting yourself by: Not updating the drivers and firmware in Windows and Windows Server.
Stop hurting yourself by: Disabling IPv6, why do you really do it?
WMI: Stop hurting yourself by using “for /f %%s in (‘dir /s /b *.mof *.mfl’) do mofcomp %%s”
P.P.S. If you need assistance with the “Security Baseline” implementation, the Onboarding Accelerator for Windows Clients, Phase 2 covers it. For more info, please go to https://serviceshub.microsoft.com/blog/