ACS Dashboard in OMS: Your Audit Report Highlights in a Glance
This post demonstrates how the OMS Log search queries listed in the mapping table for each ACS Audit Report can be used to drive visualizations for an OpsMgr Featured Audit Collection Services (ACS) Dashboard based on the security events collected by the Security and Audit Solutions in OMS Log Analytics.
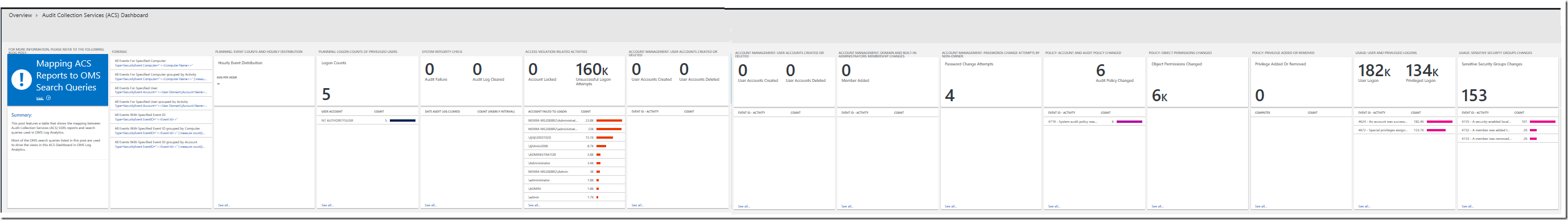
The ACS Summary Tile and Dashboard can be configured using the OMS View Designer feature in your OMS Log Analytics workspace. Adding the Security and Audit solution to an OMS workspace will allow Windows security events, Windows application events, and Windows firewall logs to be collected using direct agents or MMA agents that the user enabled.
Here are the steps to create the Summary Tile for the ACS Dashboard, and the Visualization Parts (Views) in the Dashboard Overview that provides a highlight for each ACS Audit Report using the log search queries listed in the mapping table:
(Note: Total time to create the ACS Dashboard in your OMS workspace using the View Designer may take up to 2 hours.)
Step 1: Create the ACS Summary Tile
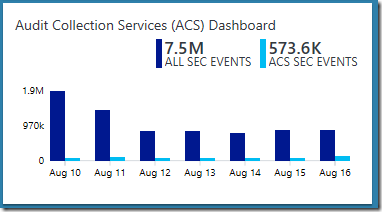
Preferred Tile Type: Two Timelines Tile
Explanation: To compare the total number of security events collected by the Security and Audit Solution with all the security events that are reported by the ACS Audit Reports, in total and over the last 7 days.
Configuration Overview:
- Chart query for all security events (ALL SEC EVENTS):
SecurityEvent
| where EventID!=0 - Chart query for ACS focused security events (ACS SEC EVENTS):
SecurityEvent
| where EventID==539 or EventID==644 or EventID==4740 or EventID==6279 or EventID between(529 .. 537) or EventID==539 or EventID==4625 or EventID==4728 or EventID==4732 or EventID==4756 or EventID==632 or EventID==636 or EventID==660 or EventID==4729 or EventID==4733 or EventID==4757 or EventID==633 or EventID==637 or EventID==661 or EventID==4723 or EventID==4724 or EventID between(627 .. 628) or EventID==624 or EventID==630 or EventID==4726 or EventID==4720 or EventID==576 or EventID==4672 or EventID==643 or EventID==4739 or EventID==612 or EventID==4719 or EventID==4670 or EventID between(608 .. 609) or EventID between (621 .. 622) or EventID between (4704 .. 4705) or EventID==516 or EventID==4612 or EventID==517 or EventID==1102 or EventID==560 or EventID==567 or EventID==4656 or EventID==4663 or EventID==576 or EventID==4672 or EventID between(4727 .. 4735) or EventID==4737 or EventID between(4754 .. 4758) or EventID between(631 .. 639) or EventID==641 or EventID between (658 .. 662) or EventID==528 or EventID==540 or EventID==4624 - Calculation Operation: Sum
- Time Interval Duration: 7 days
Step 2: Create the Further Information and Forensic Views in the Dashboard Overview
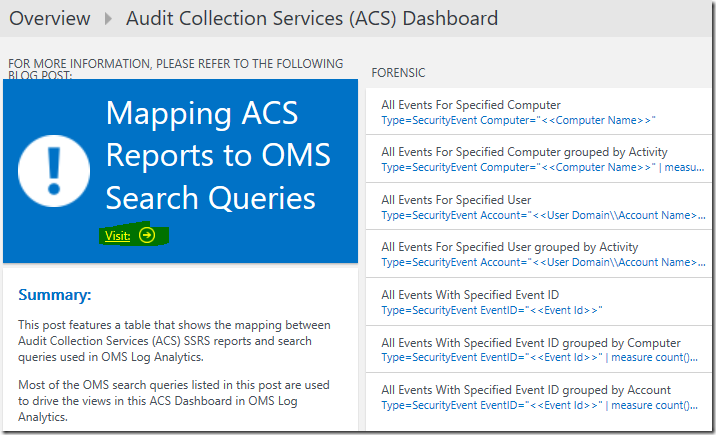
Further Information View:
Preferred Visualization Part: Information Part
Explanation: Provides a shortcut to the ACS Reports to OMS Search Queries Mapping Table for the user to acquire further information on the topic.
Configuration Overview:
Label: Mapping ACS Reports to OMS Search Queries
Summary Text:
This post features a table that shows the mapping between Audit Collection Services (ACS) SSRS reports and search queries used in OMS Log Analytics.
Most of the OMS search queries listed in this post are used to drive the views in this ACS Dashboard in OMS Log Analytics.
Forensic View:
Preferred Visualization Part: List of Queries Part
Explanation: Displays a list of search queries to analyze security events collected for a specific computer, a particular user or an Event ID. The user can click on each query and fill in the values for the filter replacing the <<string>> to display its results.
Configuration Overview:
- Query 1 Friendly Name: All Events For Specified Computer
- Query 1 Search query:
let computerName = ""; //Enter a Computer Name
SecurityEvent
| where Computer==computerName - Query 2 Friendly Name: All Events For Specified Computer grouped by Activity
- Query 2 Search query:
let computerName = “”; //Enter a Computer Name
SecurityEvent
| where Computer==computerName
| summarize count() by Activity - Query 3 Friendly Name: All Events For Specified User
- Query 3 Search query:
let accountName = ""; //Enter a User Domain\\Account Name
SecurityEvent
| where Account == accountName - Query 4 Friendly Name: All Events For Specified User grouped by Activity
- Query 4 Search query:
let accountName = ""; //Enter a User Domain\\Account Name
SecurityEvent
| where Account == accountName
| summarize count() by Activity - Query 5 Friendly Name: All Events With Specified Event ID
- Query 5 Search query:
let eventId = 0; //Replace 0 with an eventId
SecurityEvent
| where EventID == eventId - Query 6 Friendly Name: All Events With Specified Event ID grouped by Computer
- Query 6 Search query:
let eventId = 0; //Replace 0 with an eventId
SecurityEvent
| where EventID == eventId
| summarize count() by Computer - Query 7 Friendly Name: All Events With Specified Event ID grouped by Account
- Query 7 Search query:
let eventId = 0; //Replace 0 with an eventId
SecurityEvent
| where EventID == eventId
| summarize count() by Account
(Note: Please re-type the double quote characters as they may be re-encoded into a format that is not compatible with OMS Log Analytics)
For more information, please refer to the following post:
Leveraging OMS Log Search to Analyze Security Events for a Specific Computer/User/EventID
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/08/03/leveraging-oms-log-search-to-analyze-security-events-for-a-specific-computerusereventid/
Step 3: Create the Planning and System Integrity Check Views in the Dashboard Overview
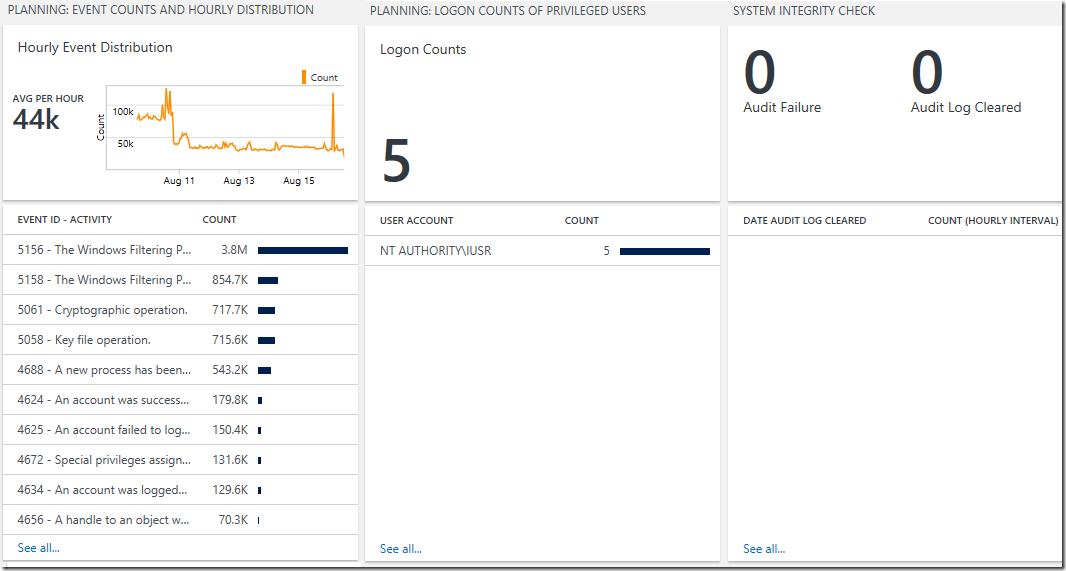
Event Counts and Hourly Distribution View:
Preferred Visualization Part: Line chart, Callout, & List Part
Explanation: The header displays a line chart of the distribution of all security events collected by the Security and Audit Solution on an hourly interval within the last 7 days. The callout shows the average amount of security events collected per hour and the list displays the top 10 security events with the highest count collected over the last 7 days.
Configuration Overview:
- Header Title: Hourly Event Distribution
- Line Chart Query:
SecurityEvent
| where EventID!=0
| summarize Count=count() by bin(TimeGenerated,1h)
| render timechart - Callout Title: Avg per hour
- Operation: Average
- Column titles: Event Id – Activity, Value: Count
- List Query:
SecurityEvent
| where EventID!=0
| summarize Count=count() by Activity
| order by Count - Navigation Query:
SecurityEvent
| where EventID!=0
| summarize Count=count() by Computer
| order by Count
For more information, please refer to the following post:
Leveraging OMS Log Search to Help Planning and Tuning of Audit Policies
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/08/02/leveraging-oms-log-search-to-help-planning-and-tuning-of-audit-policies/
Logon Counts of Privileged Users View:
Preferred Visualization Part: Number and List Part
Explanation: The header has a single number showing the total number of logon counts of privilege users and the list displays the top 10 privilege users with the highest logon counts over the last 7 days.
Configuration Overview:
- Tile Legend: Logon Counts
- Tile Query:
SecurityEvent
| where EventID==576 or EventID==4672
| where SubjectDomainName!="NT AUTHORITY" and AccountType!="Machine” - Column titles: User Account, Value: Count
- List Query:
SecurityEvent
| where EventID==576 or EventID==4672
| where SubjectDomainName!="NT AUTHORITY" and AccountType!="Machine"
| summarize Count=count() by SubjectAccount - Navigation Query:
SecurityEvent
| where EventID==576 or EventID==4672
| where SubjectDomainName!="NT AUTHORITY" and AccountType!="Machine"
| project SubjectAccount, PrivilegeList
(Note: Please re-type the double quote characters as they may be re-encoded into a format that is not compatible with OMS Log Analytics)
For more information, please refer to the following post:
Leveraging OMS Log Search to Help Planning and Tuning of Audit Policies
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/08/02/leveraging-oms-log-search-to-help-planning-and-tuning-of-audit-policies/
System Integrity Check View:
Preferred Visualization Part: Two number and List Part
Explanation: The header has one number showing the number of audit failures and a separate number showing the number of times the audit logs were cleared over the last 7 days. The list displays the number of times the audit log was cleared per hour over the last 10 hours.
Configuration Overview:
- Tile Legend 1: Audit Failure
- Tile Query 1:
SecurityEvent
| where EventID==516 or EventID==4612
| project TimeGenerated, Activity, Computer - Tile Legend 2: Audit Log Cleared
- Tile Query 2:
SecurityEvent
| where EventID==517 or EventID==1102
| project Activity, Computer, TimeGenerated - Column titles: Date Audit Log Cleared, Value: Count (Hourly Interval)
- List Query:
SecurityEvent
| where EventID==517 or EventID==1102
| summarize EventPerHour=count() by bin(TimeGenerated,1h) - Navigation Query: SecurityEvent
| where EventID==517 or EventID==1102 or EventID==516 or EventID==4612
| project TimeGenerated, Activity, Computer
For more information, please refer to the following post:
Leveraging OMS Log Search to Capture Audit Failures and Audit Log Tampering:
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/08/04/leveraging-oms-log-search-to-track-audit-failures-and-audit-log-tampering/
Step 4: Create the Access Violation Related Activities View in the Dashboard Overview
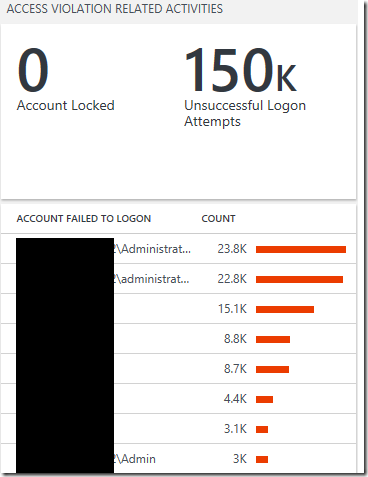
Access Violation Related Activities View:
Preferred Visualization Part: Two number and List Part
Explanation: The header has one number showing the total number of accounts locked and a separate number showing the number unsuccessful logon attempts over the last 7 days. The list displays the top 10 accounts with the highest number of failed logon attempts over the last 7 days.
Configuration Overview:
- Tile Legend 1: Account Locked
- Tile Query 1:
SecurityEvent
| where EventID==539 or EventID==644 or EventID==4740 or EventID==6279 - Tile Legend 2: Unsuccessful Logon Attempts
- Tile Query 2:
SecurityEvent
| where EventID between (529 .. 537) or EventID==539 or (EventID==4625 and Status=="0xc000006d")
| project TargetAccount, IpAddress, Computer, LogonProcessName, AuthenticationPackageName, LogonTypeName - Column titles: Account Failed to Logon, Value: Count
- List Query:
SecurityEvent
| where EventID between (529 .. 537) or EventID==539 or (EventID==4625 and Status=="0xc000006d")
| summarize count() by TargetAccount - Navigation Query:
SecurityEvent
| where EventID==624 or EventID==4720 or EventID==630 or EventID==4726
| project TimeGenerated, TargetAccount, Activity, Computer
For more information, please refer to the following post: Leveraging OMS Log Search to Identify Potential Access Violation Activities
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/07/30/leveraging-oms-log-searches-to-identify-potential-access-violation-activities/
Step 5: Create the Account Management Views in the Dashboard Overview
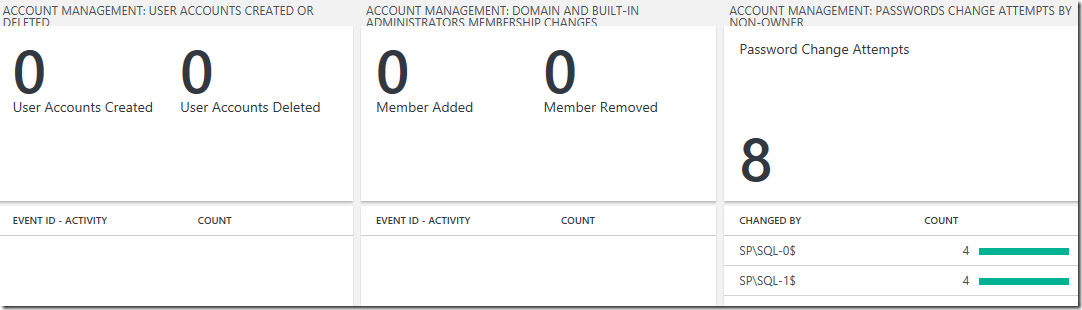
User Accounts Created Or Deleted View:
Preferred Visualization Part: Two number and List Part
Explanation: The header has one number showing the total number of user accounts created and a separate number showing the total number of user accounts deleted over the last 7 days. The list displays the top 10 user accounts created or deleted related security events with the highest count over the last 7 days.
Configuration Overview:
- Tile Legend 1: User Accounts Created
- Tile Query 1:
SecurityEvent
| where EventID==624 or EventID==4720
| project TimeGenerated, TargetAccount, CreatedBy=SubjectAccount, Computer - Tile Legend 2: User Accounts Deleted
- Tile Query 2:
SecurityEvent
| where EventID==630 or EventID==4726
| project TimeGenerated, TargetAccount, DeletedBy=SubjectAccount, Computer - Column titles: Event Id - Activity, Value: Count
- List Query:
SecurityEvent
| where EventID==624 or EventID==4720 or EventID==630 or EventID==4726
| summarize count() by Activity - Navigation Query:
SecurityEvent
| where EventID==539 or EventID==644 or EventID==4740 or EventID==6279
For more information, please refer to the following post:Leveraging OMS Log Search for Account Management and Audit Reporting
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/07/31/leveraging-oms-log-search-for-account-management-and-audit-reporting/
Domain and Built-in Administrators Membership Changes View:
Preferred Visualization Part: Two number and List Part
Explanation: The header has one number showing the total number of members added and a separate number showing the number members removed over the last 7 days. The list displays the top 10 user membership change related security events with the highest count over the last 7 days.
Configuration Overview:
- Tile Legend 1: Member Added
- Tile Query 1:
SecurityEvent
| where EventID==4728 or EventID==4732 or EventID==4756 or EventID==632 or EventID==636 or EventID==660
| search "S-1-5-32-544" or "512"
| project Action=”Add Member”, TargetUserName, Activity, SubjectAccount, MemberName, TimeGenerated, Computer - Tile Legend 2: Member Removed
- Tile Query 2:
SecurityEvent
| where EventID==4729 or EventID==4733 or EventID==4757 or EventID==633 or EventID==637 or EventID==661
| search "S-1-5-32-544" or "512"
| project Action=”Remove Member”, TargetUserName, Activity, SubjectAccount, MemberName, TimeGenerated, Computer - Column titles: Event Id - Activity, Value: Count
- List Query:
SecurityEvent
| where EventID==4728 or EventID==4732 or EventID==4756 or EventID==632 or EventID==636 or EventID==660 or EventID==4729 or EventID==4733 or EventID==4757 or EventID==633 or EventID==637 or EventID==661
| search "S-1-5-32-544" or "512"
| summarize count() by Activity - Navigation Query:
SecurityEvent
| where EventID==4728 or EventID==4732 or EventID==4756 or EventID==632 or EventID==636 or EventID==660 or EventID==4729 or EventID==4733 or EventID==4757 or EventID==633 or EventID==637 or EventID==661
| search "S-1-5-32-544" or "512"
| project TargetUserName, Activity, SubjectAccount, MemberName, TimeGenerated, Computer
(Note: Please re-type the double quote characters as they may be re-encoded into a format that is not compatible with OMS Log Analytics)
For more information, please refer to the following post:
Leveraging OMS Log Search for Account Management and Audit Reporting
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/07/31/leveraging-oms-log-search-for-account-management-and-audit-reporting/
Password Change Attempts by Non-owner View:
Preferred Visualization Part: Number and List Part
Explanation: The header has a single number showing the total number of password change attempts by non-owner and the list displays the top 10 account that are non-owners with the highest number of password changes over the last 7 days.
Configuration Overview:
- Tile Legend: Password Change Attempts
- Tile Query:
SecurityEvent
| where EventID==4723 or EventID==4724 or EventID between (627 .. 628) and SubjectAccount != "ANONYMOUS LOGON" and TargetAccount!=SubjectAccount - Column titles: Changed By, Value: Count
- List Query:
SecurityEvent
| where EventID==4723 or EventID==4724 or EventID between (627 .. 628) and SubjectAccount != "ANONYMOUS LOGON" and TargetAccount!=SubjectAccount
| project TimeGenerated, Computer, TargetAccount, ChangedBy=SubjectAccount
| summarize count() by SubjectAccount - Navigation Query:
SecurityEvent
| where EventID==4723 or EventID==4724 or EventID between (627 .. 628) and SubjectAccount != "ANONYMOUS LOGON" and TargetAccount!=SubjectAccount
| project TimeGenerated, Computer, TargetAccount, ChangedBy=SubjectAccount
(Note: Please re-type the double quote characters as they may be re-encoded into a format that is not compatible with OMS Log Analytics)
For more information, please refer to the following post:
Leveraging OMS Log Search for Account Management and Audit Reporting
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/07/31/leveraging-oms-log-search-for-account-management-and-audit-reporting/
Step 6: Create the Policy Views in the Dashboard Overview
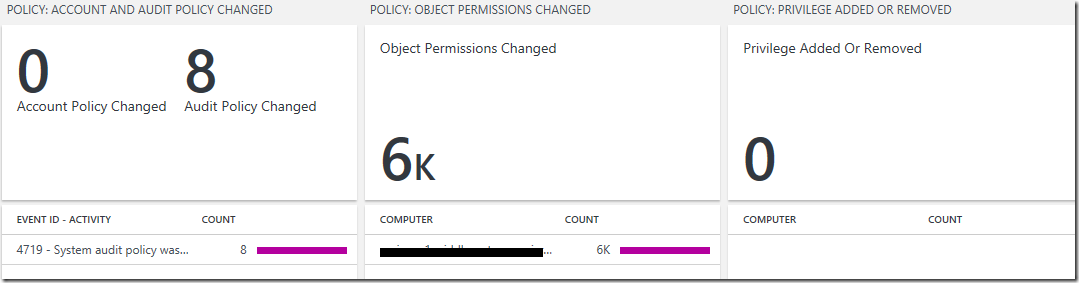
Account and Audit Policy Changed View:
Preferred Visualization Part: Two number and List Part
Explanation: The header has one number showing the total number of account policy changed and a separate number showing the total number of audit policy changed over the last 7 days. The list displays the top 10 account and audit policy changed related security events with the highest count over the last 7 days.
Configuration Overview:
- Tile Legend 1: Account Policy Changed
- Tile Query 1:
SecurityEvent
| where EventID==643 or EventID==4739
| project Computer, Activity, TimeGenerated, EventData - Tile Legend 2: Audit Policy Changed
- Tile Query 2:
SecurityEvent
| where EventID==612 or EventID==4719
| project Computer, Activity, TimeGenerated, EventData - Column titles: Event Id - Activity, Value: Count
- List Query:
SecurityEvent
| where EventID==643 or EventID==4739 or EventID==612 or EventID==4719
| summarize count() by Activity - Navigation Query:
SecurityEvent
| where EventID==643 or EventID==4739 or EventID==612 or EventID==4719
| project Computer, Activity, TimeGenerated, EventData
For more information, please refer to the following post:
Leveraging OMS Log Search to Track Policy and Permission Changes
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/08/05/leveraging-oms-log-search-to-track-policy-and-permission-changes/
- Tile Legend: Object Permissions Changed
- Tile Query:
SecurityEvent
| where EventID==4670
| project TimeGenerated, Activity, Computer, EventData - Column titles: Computer, Value: Count
- List Query:
SecurityEvent
| where EventID==4670
| summarize count() by Computer - Navigation Query:
SecurityEvent
| where EventID==4670
| project TimeGenerated, Activity, Computer, EventData
For more information, please refer to the following post:
Leveraging OMS Log Search to Track Policy and Permission Changes
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/08/05/leveraging-oms-log-search-to-track-policy-and-permission-changes/
- Tile Legend: Privilege Added Or Removed
- Tile Query:
SecurityEvent
| where EventID between (608 .. 609) or EventID between (621 .. 622) or EventID between (4704 .. 4705)
| project TimeGenerated, Activity, Computer, EventData - Column titles: Computer, Value: Count
- List Query:
SecurityEvent
| where EventID between (608 .. 609) or EventID between (621 .. 622) or EventID between (4704 .. 4705)
| summarize count() by Computer - Navigation Query:
SecurityEvent
| where EventID between (608 .. 609) or EventID between (621 .. 622) or EventID between (4704 .. 4705)
| project TimeGenerated, Activity, Computer, EventData
For more information, please refer to the following post:
Leveraging OMS Log Search to Track Policy and Permission Changes
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/08/05/leveraging-oms-log-search-to-track-policy-and-permission-changes/
Step 7: Create the Usage Views in the Dashboard Overview
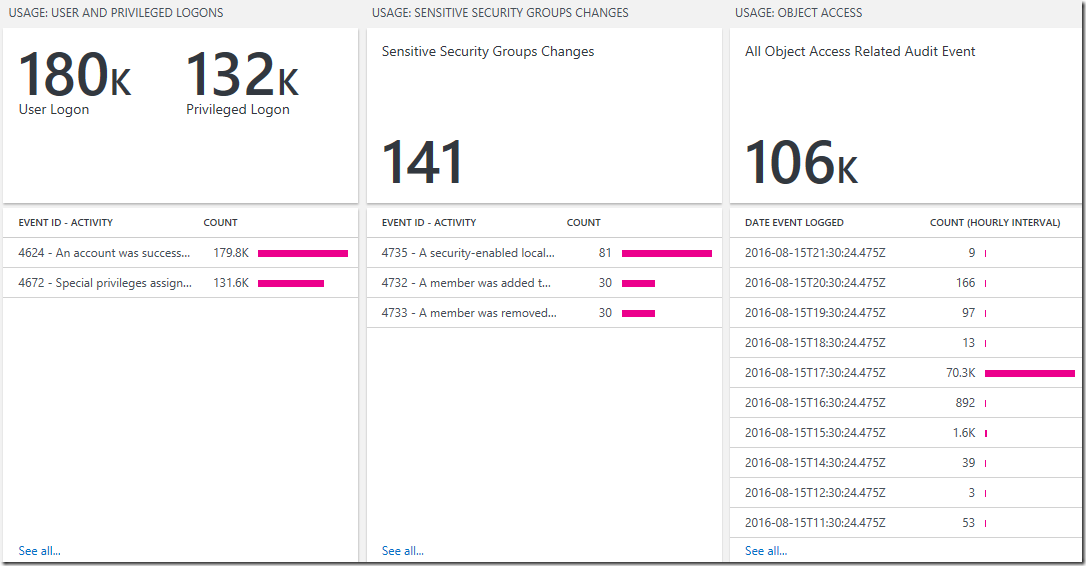
User and Privileged Logons View:
Preferred Visualization Part: Two number and List Part
Explanation: The header has one number showing the total number of user logon events and a separate number showing the total number of privileged logon events over the last 7 days. The list displays the top 10 user and privileged logon related security events with the highest count over the last 7 days.
Configuration Overview:
- Tile Legend 1: User Logon
- Tile Query 1:
SecurityEvent
| where EventID==528 or EventID==540 or EventID==4624
| project TimeGenerated, Activity, Computer, IpAddress, AuthenticationPackageName, LogonProcessName, LogonTypeName, TargetAccount - Tile Legend 2: Privileged Logon
- Tile Query 2:
SecurityEvent
| where EventID==576 or EventID==4672
| project TimeGenerated, Activity, Computer, SubjectAccount, PrivilegeList - Column titles: Event Id - Activity, Value: Count
- List Query:
SecurityEvent
| where EventID==576 or EventID==4672 or EventID==528 or EventID==540 or EventID==4624
| summarize count() by Activity
| order by count_ - Navigation Query:
SecurityEvent
| where EventID==576 or EventID==4672 or EventID==528 or EventID==540 or EventID==4624
For more information, please refer to the following post:Leveraging OMS Log Search to Report on User Logon and Object Access Events
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/08/05/leveraging-oms-log-search-to-report-on-user-logon-and-object-access-events/
Sensitive Security Groups Changes View:
Preferred Visualization Part: Number and List Part
Explanation: The header has a single number showing the total number of sensitive security groups changes and the list displays the top 10 related security events with the highest count over the last 7 days..
Configuration Overview:
- Tile Legend: Sensitive Security Groups Changes
- Tile Query:
SecurityEvent
| where EventID between (4727 .. 4735) or EventID==4737 or EventID between (4754 .. 4758) or EventID between (631 .. 639) or EventID==641 or EventID between (658 .. 662)
| project Activity, GroupName=TargetUserName, SubjectAccount, MemberName, TimeGenerated
| order by Activity desc - Column titles: Event Id - Activity, Value: Count
- List Query:
SecurityEvent
| where EventID between (4727 .. 4735) or EventID==4737 or EventID between (4754 .. 4758) or EventID between (631 .. 639) or EventID==641 or EventID between (658 .. 662)
| summarize count() by Activity - Navigation Query:
SecurityEvent
| where EventID between (4727 .. 4735) or EventID==4737 or EventID between (4754 .. 4758) or EventID between (631 .. 639) or EventID==641 or EventID between (658 .. 662)
| project Activity, GroupName=TargetUserName, SubjectAccount, MemberName, TimeGenerated
| order by Activity desc
For more information, please refer to the following post:
Leveraging OMS Log Search to Report on User Logon and Object Access Events
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/08/05/leveraging-oms-log-search-to-report-on-user-logon-and-object-access-events/
- Tile Legend: All Object Access Related Audit Event
- Tile Query: T
SecurityEvent
| where EventID==560 or EventID==567 or EventID==4656 or EventID==4663
| project Computer, Activity, TimeGenerated, EventData - Column titles: Date Event Logged, Value: Count (Hourly Interval)
- List Query:
SecurityEvent
| where EventID==560 or EventID==567 or EventID==4656 or EventID==4663
| summarize EventPerHour=count() by bin(TimeGenerated,1h) - Navigation Query:
SecurityEvent
| where EventID==560 or EventID==567 or EventID==4656 or EventID==4663
| project Computer, Activity, TimeGenerated, EventData
For more information, please refer to the following post:Leveraging OMS Log Search to Report on User Logon and Object Access Events
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/08/05/leveraging-oms-log-search-to-report-on-user-logon-and-object-access-events/
A shout out and kudos to my colleague Meir Mendelovich (OMS PM) for sharing his knowledge and his time in helping me validate the mapping table and ACS Dashboard in OMS.
To view the complete mapping between all Audit Collection Services (ACS) SSRS reports and search queries used in OMS Log Analytics, refer to:
https://blogs.msdn.microsoft.com/wei_out_there_with_system_center/2016/07/25/mapping-acs-reports-to-oms-search-queries/
Additional Resources:
Log Analytics View Designer by Brian Wren
https://azure.microsoft.com/en-us/documentation/articles/log-analytics-view-designer/
Log Analytics View Designer Tile Reference by Brian Wren
https://azure.microsoft.com/en-us/documentation/articles/log-analytics-view-designer-tiles/
Log Analytics View Designer visualization part reference by Brian Wren
https://azure.microsoft.com/en-us/documentation/articles/log-analytics-view-designer-parts/
Disclaimer:
All information on this blog is provided on an as-is basis with no warranties and for informational purposes only. Use at your own risk. The opinions and views expressed in this blog are those of the author and do not necessarily state or reflect those of my employer.
Comments
- Anonymous
August 17, 2016
Great job Wei - I am sure that everyone who uses ACS will find this Solution incredibly useful.Thanks for posting. - Anonymous
February 07, 2017
Would be great if you could export the Custom View and link the .omsdata file for us to download and import!- Anonymous
March 01, 2017
+1- Anonymous
March 01, 2017
You should be able to download from here:http://adinermie.com/scom-acs-dashboard-oms/ special thanks to Adin Ermie for compiling the omsview file.- Anonymous
March 01, 2017
No problem. thanks for the mention.
- Anonymous
- Anonymous
- Anonymous