Information Protection approach for a hybrid environment
With the acceleration of digital transformation, it also has broad implications. The way we work and the tools we use are changing at a very rapid pace: including employees bringing their own devices to the work environment and pervasive use of SaaS applications. Because of this, the way organizations manage and secure their data must also evolve. Companies no longer operate solely within their own perimeter. Data travels to more locations than ever before, across both on-premises and cloud environments and it could be At Rest, In Motion or In Use.... While this has helped increase user's productivity and their ability to collaborate with others, it has also made protecting sensitive data more challenging. There are several reasons why a comprehensive information protection approach is so important. Data is being created and shared across boundaries, across a variety of devices, apps and cloud services. Compliance concerns add a layer of scrutiny to how data is being used and shared.
Information Protection lifecycle: Information protection lifecycle across devices, cloud apps or on-premises apps, primarily includes 4 phases: Detect, classify, protect and monitor.
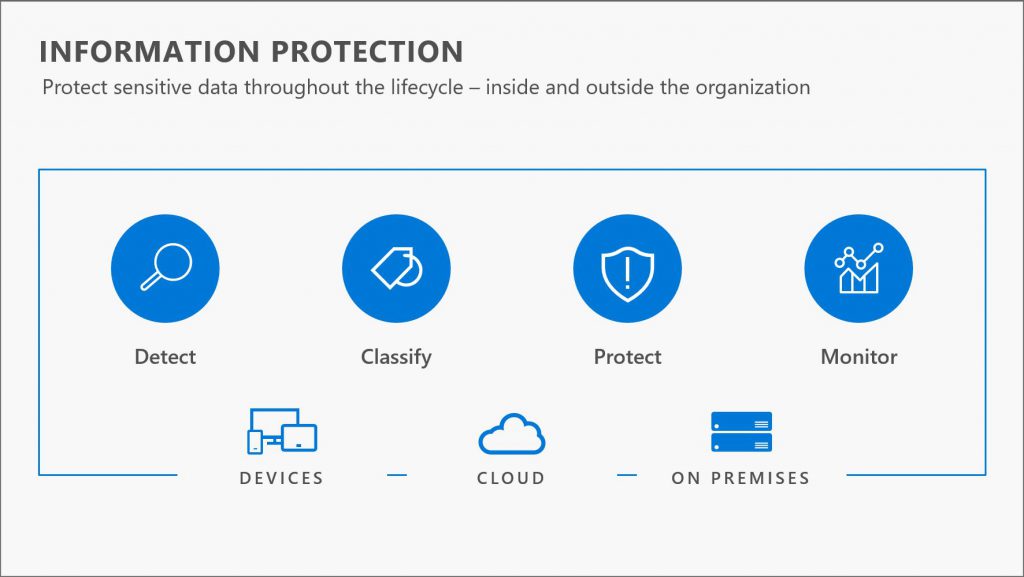
Detect: Detecting sensitive data is the first step in having an effective information protection strategy. Data when in motion needs to be tied with a sensitivity and its location. Different levels of data sensitivity will need different level of protection.
Classify: Once you have detected sensitive data, it's important to classify the data into distinct categories so that custom controls, such as policies and actions, can be applied. Once the classification scheme is set by the organization, policies can be configured and customized so that sensitive data such as intellectual property, customer info, health records, etc., are protected, stored and shared in a manner that adheres to the organization's security requirements. Classification and labeling persists with the file and can be understood and honored by other services, avoiding the need to reclassify and re-label throughout the file's journey.
Protect: Basis the Classifying and labeling of data, a protection policy rule applies some level of protection to sensitive data.
Monitor: Gaining visibility into how users are using or distributing sensitive information is an important component of your information protection strategy. In the case of unexpected activity or events involving sensitive information, organizations also need to be able to respond quickly and accurately.
Microsoft's Information Protection Approach:
Microsoft's information protection solutions address each of these steps. This includes protecting sensitive information across Devices, SaaS applications and cloud services, as well as on premises environments.

This summarizes the primary solutions that can be implemented to protect sensitive information on devices, within your Office 365 environment, and then beyond your Office 365 environment to Azure, 3rd party cloud services and apps and on-premises environments.
At the device level: (PCs, Tablets and Mobile)
- BitLocker: BitLocker Drive Encryption is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers.
- Windows Information Protection (WIP): Windows Information Protection (WIP), helps to protect against this potential data leakage without otherwise interfering with the employee experience. WIP also helps to protect enterprise apps and data against accidental data leak on enterprise-owned devices and personal devices that employees bring to work without requiring changes to your environment or other apps.
- Intune: Microsoft Intune is a cloud service that provides mobile device management, mobile application management, and PC management capabilities. Intune's mobile productivity management capabilities help organizations provide their employees access to corporate data, applications, and resources, while helping to protect their corporate information.
At Office 365 level: (Exchange Online, SharePoint Online, OneDrive for Business)
- Office 365 Data Loss Prevention (DLP) : Office 365 DLP which enables you to prevent sensitive information in Office 365 from getting into the wrong hands or being accidentally shared. With Office 365 DLP you can identify, monitor, and automatically protect sensitive information across Office 365 services.
- Office 365 Advanced Data Governance (ADG): Office 365 Advanced Data Governance applies machine learning to help customers find and retain important data while eliminating trivial, redundant and obsolete data that could cause risk if compromised. ADG enables you to classify and label documents for applying retention, expiration and deletion policies to important information.
At Cloud Services, SaaS Apps and On-Premises level: (Azure, 3rd party SaaS apps, Datacenters, file shares)
- Azure Information Protection (AIP): Azure Information Protection (AIP) helps protect sensitive information across cloud services and on-premise environments. With AIP you can classify, and label data based on sensitivity, and create different levels of protection and visual markings such as: encryption, watermarking, etc. AIP provides enhanced protection in the form of client-side protection and other advanced capabilities needed by organizations that are heavily regulated, such as Hold Your Own Key (HYOK)
- Microsoft Cloud App Security (CAS): Microsoft's Cloud App Security is a Cloud Access Security Broker (CASB) solution which provides visibility and control across cloud app usage including:
- Cloud Discovery: Discover all cloud use in your organization, including Shadow IT reporting and control and risk assessment.
- Data Protection: Monitor and control your data in the cloud by gaining visibility, enforcing DLP policies, alerting and investigation.
- Threat Protection: Detect anomalous use and security incidents. Use behavioral analytics and advanced investigation tools to mitigate risk and set policies and alerts to achieve maximum control over network cloud traffic.
Each of the above components work together to provide end-to-end protection of sensitive data across your environment. You can incrementally add additional capabilities to your environment over time as your information protection strategy becomes more sophisticated and mature. Perhaps the most important step is to understand the four phases of the information protection lifecycle, understand your company's unique needs and requirements, and then define the business policies that will govern sensitive data.
[bing_translator]
Comments
- Anonymous
September 21, 2017
Nice article. Will help pitching CASB. It would be great if you also could add GDPR.- Anonymous
September 21, 2017
thanks Gaurav. Will be working on the GDPR blog shortly.
- Anonymous
- Anonymous
September 21, 2017
Nice article which empahsis on basic security with all aspects. Great !!!!- Anonymous
September 24, 2017
Thanks Rupesh. Use it for your customer conversations.
- Anonymous