Just how secure are the activities in your customer’s Office 365 tenants?
 Garrett Bundy Garrett Bundy |
 |
Hello Partners,
Recently I was working with a partner who was concerned about their customer’s office 365 tenant and the security associated with it. Part of the concern was that the customer wanted to see what activities had been accomplished in the admin center by any global admins in the tenant. If your customer’s came to you today and asked you the same questions, would you be able to quickly pull up these reports? Did you even know that they are available?
The very first thing that you need to do is enable activity logging in the admin console. By default not all the activities in Exchange Online, SharePoint Online and Azure Active Directory are logged and we must turn them on manually as an account that has the appropriate permissions. In order to do this you must have access to make changes in the Protection Center. If you need help with this part please see Permissions in Office 365. Once you are logged in, you can enable the basic logging from inside the Protection Center interface. Additional mailbox specific logging can be enabled through PowerShell (including non-owner mailbox access, messaging routing and delivery). Once enabled through the PowerShell interface, this data will be available through all acquisition means discussed in this post.
For additional reference on what information and events are recorded once you enable auditing, please see Audited activities in Office 365
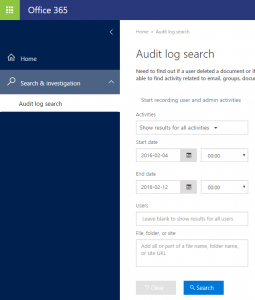
Protection Center Audit Log
To enable audit logging through the UI, simply navigate to “Search & investigation” and drilling down on the “Start recording user and admin activities” link, see screenshot below. If this link is not shown on your screen, it means logging has already been enabled and you can start using the search interface to acquire data.
Non-owner auditing with Exchange remote PowerShell
To enable the additional mailbox specific events requires a remote PowerShell connection to the Exchange Service. You are required to authenticate yourself against the service, create a remote PowerShell session and enable logging by command line with your specific parameters.
The authentication and remote session pieces of this will be a recurring theme as it establishes a platform to submit commands for discrete queries and actions in your tenancy that we will utilize as part of the investigate and remediate process.
The following script will enable non-owner mailbox access auditing on every mailbox in your tenancy once your session is established.
#Authenticate and issue a credential for the remote PS session$userCredential = Get-Credential #Connect to the Exchange remote PowerShell service $ExoSession = New-PSSession -ConfigurationName Microsoft.Exchange –ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $userCredential -Authentication Basic -AllowRedirectionImport-PSSession $ExoSession #Enable global audit logging for every mailbox in your tenancy Get-Mailbox -ResultSize Unlimited -Filter {RecipientTypeDetails -eq "UserMailbox"} | Set-Mailbox -AuditEnabled $true -AuditLogAgeLimit 365 #To enable auditing for a single mailbox, replace the content within quotes with either the display name or the email address of the mailbox. Set-Mailbox -Identity "<display name or address>" -AuditEnabled $true #Validate logging is enabled.Get-Mailbox | Select Name, AuditEnabled, AuditLogAgeLimit |
Now that you have setup your tenant to acquire the necessary audit data, it can take up to 12 hours for any data to appear in the user interface. Now you can go in and start looking at the audit data and take action against the information that may be uncovered.
An example Use Case
An example of a use case implemented across the 3 interfaces shows us the basic function of each and provides context to the query.
A relevant scenario would be: As an Office 365 tenant admin, you need to identify all the SharePoint activities of an individual user over a specific period of time as part of an investigation.
- Navigating to the Protection Center Audit log search feature will provide you the data you require by specifying the time range, choosing the appropriate drop down and filtering results as required.
- The same information is available via PowerShell by utilizing the Search-UnifiedAuditLog cmdlet. You can then view the results in session or output to any number of data formats for ingestion into other analytical platforms.
- The Activity API interface is a bit more complicated to setup, see details in the API section below, however provides a much broader usability as you can programmatically call into the API and facilitate data ingestion into a number of other analytical platforms such as SQL databases, partners with native integrations and/or an industry SIEM.
There is quite a bit more information out there as far as things you can do to ingest the data, analyze the data or even work with a Third Party to leverage managed IP that already exists. If you want more information, check out the Office 365 Security Team’s blog located here. I’ll be looking to post more from the security side soon!
Till Next Time,
Garrett
Technorati Tags: Garrett Bundy,Office 365,SMB,Security,Auditing