Updates to Office 365 Proxy PAC Generator
I wrote the original Proxy PAC tool for a customer almost a year ago, and since have added a lot of new functionality. Rather than updating my previous blog posts about it, I thought I would start a fresh thread. If you want some background on how Proxy PAC files work and how to distribute them to your users via GPO or WPAD, I would suggest taking a look at my posts dealing with those topics:
- Office 365 PAC File - https://blogs.technet.microsoft.com/undocumentedfeatures/2015/11/16/office-365-pac-file/
- Deploying the PAC file - https://blogs.technet.microsoft.com/undocumentedfeatures/2016/04/06/deploying-the-office-365-proxy-pac-to-manage-your-users/
Now, on to the new stuff.

Configuring
I try hard to build in good help, which you can access by running Get-Help .\Office365ProxyPac.ps1.
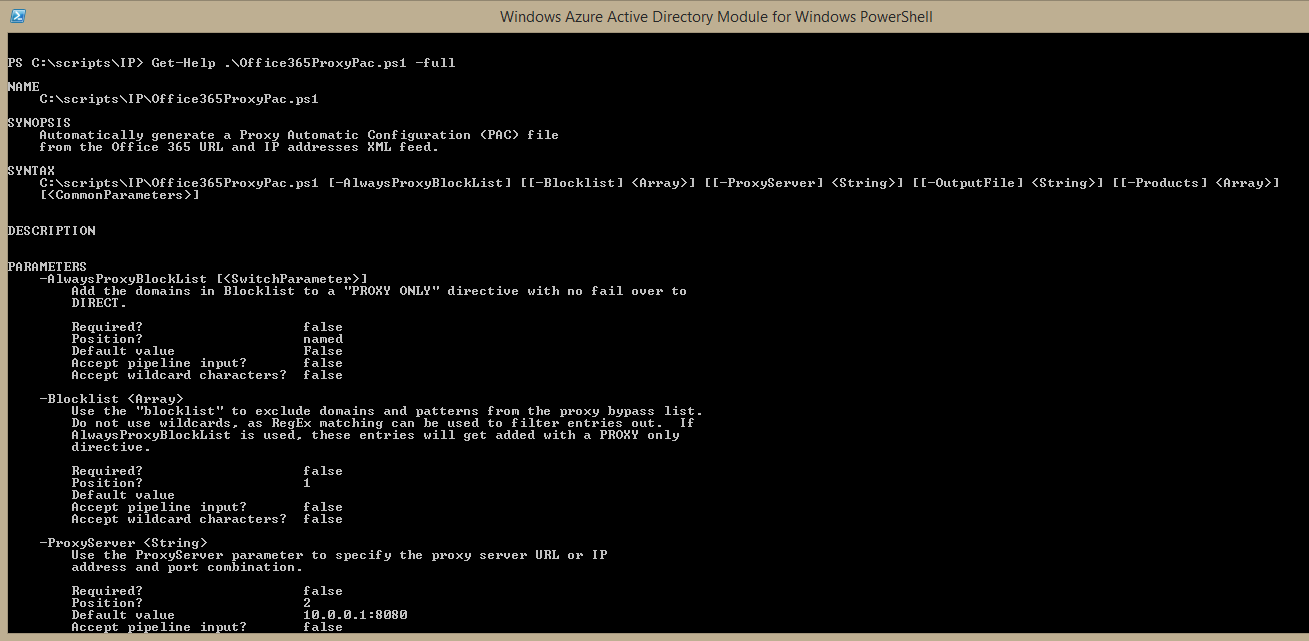
I added a few new parameters that I'm really excited about and want to share. So, without further ado:
Blocklist
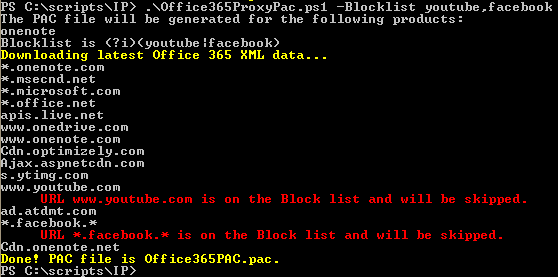
This is a feature that I put in after some questions from customers about including public URLs such as Facebook or YouTube in the O365IPAddresses.xml file. Some organizations don't really want to allow access to those URLs carte blanch, so I added a feature to exclude those from being included in the "DIRECT" directive by omitting them from the list overall. Using the feature:
.\Office365ProxyPac.ps1 -Blocklist youtube,facebook
AlwaysProxyBlocklist
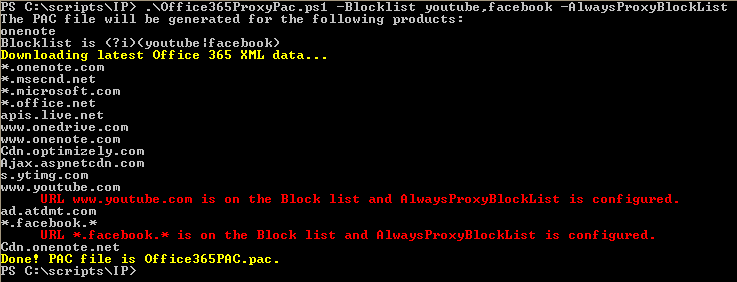
However, just to cover all the bases, maybe the customer wants to ensure that those URLs on the Blocklist are actually proxied. In that case, they can use the -AlwaysProxyBlocklist parameter, which causes the script to build a new section and assign them the PROXY directive with no fall-back configuration. To use this feature:
.\Office365ProxyPac.ps1 -Blocklist youtube,facebook
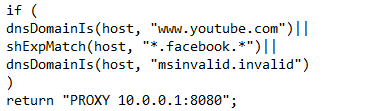
When you open the Office365PAC.pac file, you'll see this new directive:
Products
This was by far the most requested feature that I added. I received a lot of feedback about being able to only configure proxy bypass (DIRECT) for individual services, so I have finally implemented a feature to be able to do it. To use the feature:
.\Office365ProxyPac.ps1 -Products EXO,Identity
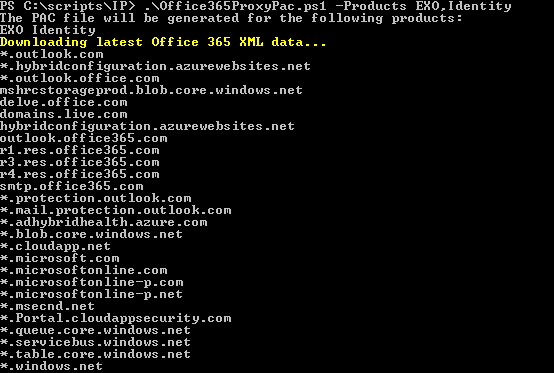
Testing
Once you've created your PAC file, I would suggest testing it to make sure you get the desired behavior. I use the FindProxyForUrl toolset (https://findproxyforurl.com/official-toolset/). After you download and extract it, you can use pactester.exe to verify that it works as planned. For my test PAC, I used the parameters -Products EXO,OneNote,Identity -AlwaysProxyBlockList -Blocklist youtube,facebook.
To run the tool, the syntax is:
pactester.exe -p <pac file> -u <url to test>
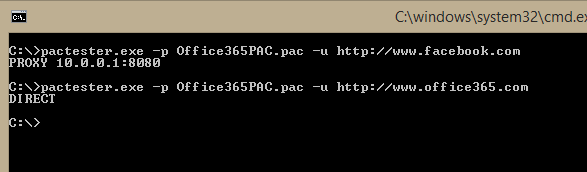
In my case, the desired result is to send URLs with the pattern facebook to the proxy and for everything else to go direct.
The updated version of the Office 365 Proxy Pac tool is available here: https://gallery.technet.microsoft.com/Office-365-Proxy-Pac-60fb28f7.
Happy Proxying!
Comments
- Anonymous
August 19, 2016
Awesome toolhow did i miss that:)- Anonymous
August 21, 2016
Thanks--we have a several large customers using it (or incorporating parts of it into their PAC file creation). I'm really excited about the new updates.
- Anonymous
- Anonymous
January 04, 2017
I'm struggling a bit to understand why my use case for this is so different from the use case and examples that it was apparently built for. We can not access any Internet sites without traversing the Proxy server. So DIRECT does nothing for us and that's the primary method used here. So it seems I don't need this script at all? What I was looking for is a way to generate a Proxy.pac which properly routed client traffic DIRECT when there is an alternate route (It's not on the Internet and Not on the Local Intranet).- Anonymous
January 04, 2017
Disregard my previous comment. I read your other Blog posting where this is explained. I understand now.
- Anonymous
- Anonymous
January 05, 2017
The example given for your "AlwaysProxyBlocklist" parameter states the wrong one (same as the example above)! - Anonymous
February 16, 2017
I was going to build a tool for this myself (to simultaneously learn more about scripting and solve my O365 PAC problem) when I came across this. Great stuff, thanks a bunch!! However, I'm running into a problem where the script will only generate a correct PAC file when a single Product is chosen.- When '-Product' flag is omitted, Script outputs that PAC will be generated for All products, but actual .PAC file only contains the hard coded dnsDomainIs(host, "office365.com"):- When '-Product WAC,O365' is used, or any combination of more than 1 Product, Script outputs that PAC will be generated for selected products, but actual .PAC file only contains the hard coded dnsDomainIs(host, "office365.com"):- When '-Product O365' is used, PAC file is generated correctly with all the domains listed under that product in the XML. So PAC file generator is only working for a single product. Wondering if maybe the XML format changed since last update of this script?- Anonymous
February 16, 2017
NM.....I didn't have the correct powershell installed, so that's why I couldn't run it. Great tool!- Anonymous
February 22, 2017
Thanks! If you're looking for ways to deploy it, you can read my post on WPAD.
- Anonymous
- Anonymous
- Anonymous
July 18, 2017
The BlockList function is good. However, I need to explicitly put in every public URL individually.Is there an easier method to omit/put together all the Non-Microsoft URLs in the xml?- Anonymous
August 01, 2017
I don't have a way to omit them or proxy them based on who "owns" the domain. I can look into that.
- Anonymous