Sign an exported certificate from an F5
I've run into this delightful scenario a few times--the network team generates CSRs and certificates for the environment, and since they want to do SSL termination on their network devices, complete the certificate process there. When you ask for an export of the certificate from, say, an F5, they will just give you the unsigned certificate--so that when you import it into your server, you end up with something unusable, since it has no private key.
Assuming you can get both the certificate *and* the private key from them, here's how you can create a usable certificate.
In my case, I received an email that had the text of both my certificate and the private key (I've truncated it and obscured some of the text):
The standard certificate part starts at -----BEGIN CERTIFICATE----- and ends at -----END CERTIFICATE----- . So, copy and paste that data (including the BEGIN and END tags) into a new text document and save it with a creative name like "CertificateFromJerkFaceNetworkEngineer.txt". The private key starts at -----BEGIN RSA PRIVATE KEY----- and ends at -----END RSA PRIVATE KEY----- . Copy and paste that text (including the BEGIN and END tags) into a new text document, and save it with an equally creative name like "HeThinksHesSoSmartGivingMeASeparatePrivateKey.txt."
Next, you need a way to sign the certificate with the private key. You can do this with the OpenSSL tools. The ones I use are at https://slproweb.com/products/Win32OpenSSL.html (Select the "Win32 Open SSL" installer that has all of the components). Download and install to default directory.
Now, for the fun part--create a certificate you can use:
C:\OpenSSL-Win32\bin\openssl.exe pkcs12 -export -in CertificateFromJerkFaceNetworkEngineer.txt -inkey HeThinksHesSoSmartGivingMeASeparatePrivateKey.txt -out CertificateWithAKeyYouCanActuallyUse.p12 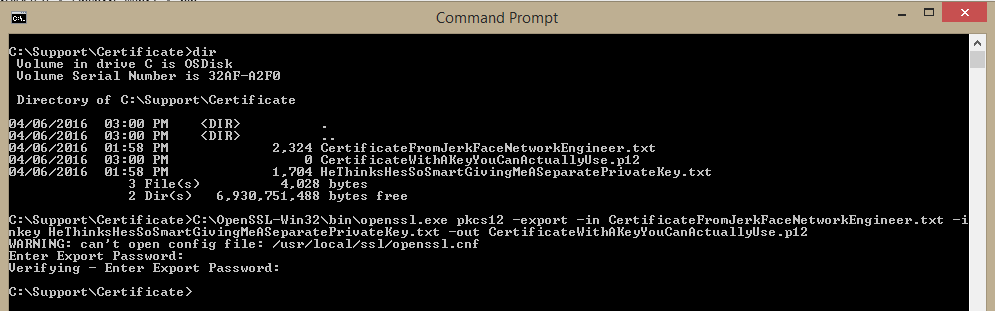
When prompted, enter a password twice (once to enter, once to confirm). You are now the proud owner of a .p12 file than you can import through the normal certificate import process.
Comments
- Anonymous
April 09, 2016
good stuff
thanks
