A Secure Azure

 By Olivier Subramanian
By Olivier Subramanian
Olivier is a Cloud Solution Architect in the UK Customer Success Unit. He has been helping companies achieve digital transformation for over 20 years and leads the Azure security interest group in the CSU.
Cybersecurity is a big issue. As society transitions through the digital revolution, we rely more and more on the built-in applications and development of our technology to protect our data and assets than we do having 6ft concrete walls, armed guards and CCTV; and it’s something that a lot of our customers are struggling to understand, accept and embrace; because hey, who likes change?
The frequency and sophistication of cybersecurity attacks are escalating as attackers are residing within a victim’s network for an average of 140 days before going undetected, costing in the region of $4 million for one single data breach alone. Even worse, more that 75% of these intrusions are only made possible due to compromised user credentials. Sobering statistics, right?
For some, this is enough to shy away from storing their data in their own data center, let alone someone else’s, but they would be wrong to worry. Microsoft spends $1 billion a year on cyber security with much of that going into making Microsoft Azure the most trusted cloud platform there is through encrypting data at rest and in transit, machine learning for threat detection and penetration testing, and risk banded user access with the Azure Active Directory.
What with so much revenue being invested into advancing the architecture and design of the Azure cloud platform, it means that your abilities as a consumer grow with us too. Following on from Microsoft’s Ignite Conference, where our partners came together to celebrate what we’ve achieved and learn of our future, we have a few new announcements for you from our cloud platform:
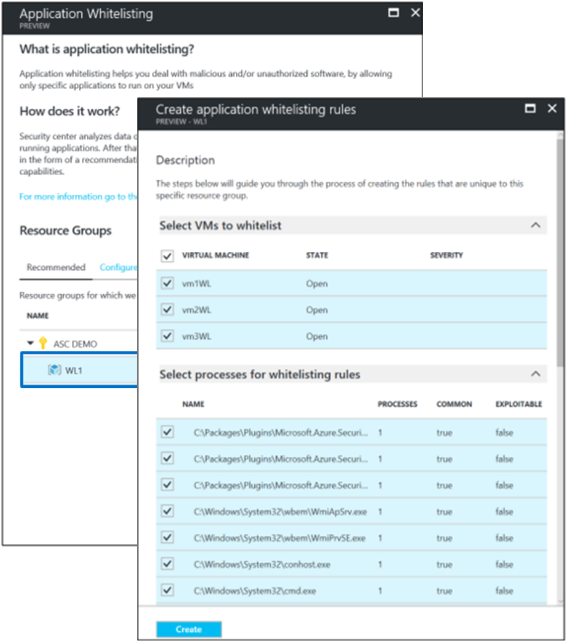
The use of prescriptive application whitelisting learns application patterns and recommends whitelists
Once compromised, an attacker will likely execute malicious code on a VM as they take action toward their objectives. Whitelisting legitimate applications helps block unknown and potentially malicious applications from running, but historically managing and maintaining these whitelists has been problematic. Azure Security Center can now automatically discover, recommend whitelisting policy for a group of machines and apply these settings to your Windows VMs using the built-in AppLocker feature. After applying the policy, Azure Security Center continues to monitor the configuration and suggests changes making it easier than ever before to leverage the powerful security benefits of application whitelisting.
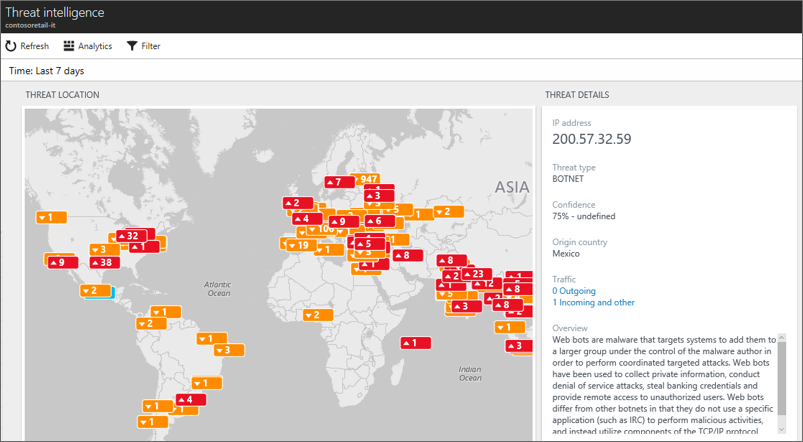
The ability to gain valuable insights about your attackers with threat intelligence from Microsoft (Interactive map and threat reports)
By using the threat intelligence option available in Security Center, IT administrators can identify security threats against the environment. For example, they can identify whether a particular computer is part of a botnet. Computers can become nodes in a botnet when attackers illicitly install malware that secretly connects the computer to the command and control. Threat intelligence can also identify potential threats coming from underground communication channels, such as the dark web. To build this threat intelligence, Security Center uses data that comes from multiple sources within Microsoft. Security Center uses this data to identify potential threats against your environment.
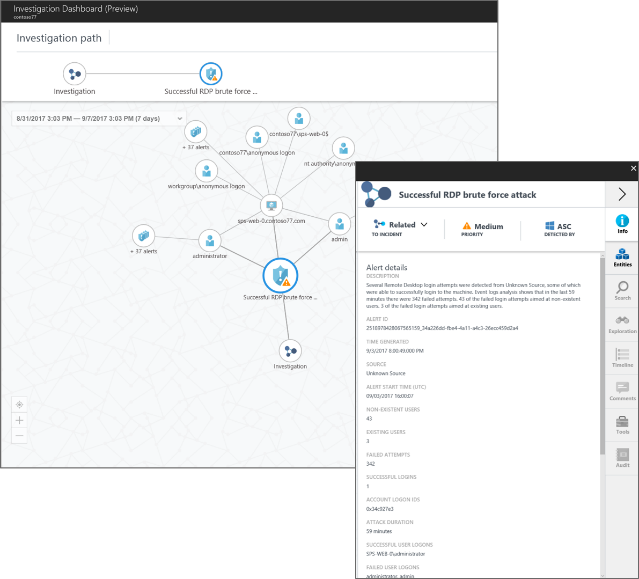
The choice to explore notable links between alerts, computers, and users to triage alerts, determine scope, and find root cause
Security Center has added a new visual, interactive investigation experience, now in preview, which helps you quickly triage alerts, assess the scope of a breach, and determine the root cause. Explore notable links between alerts, computers, and users that indicate they are connected to the attack campaign. Use predefined or ad hoc queries for deeper examination of security and operational events.
The function of automate security workflows with logic apps integration
Security Center now integrates with Azure Logic Apps to automate and orchestrate security playbooks. Create a new Logic Apps workflow using the Security Center connector, and trigger incident response actions from a Security Center alert. Include conditional actions based on alert details to tailor the workflow based on alert type or other factors. Automate common workflows such as routing alerts to a ticketing system, collecting additional data to help during an investigation, and taking corrective action to remediate a threat.
The management of security across all HYBRID cloud workloads in one console
You can now onboard VMs and computers running on-premises and in other clouds by simply installing the Microsoft Monitoring Agent on these machines. For Operations Management Suite (OMS) Security & Compliance customers, connected computers will be automatically discovered and monitored by Security Center.
