Install Standalone CA (Certificate Authority) on Windows Server 2012 R2 for use with Operations Manager
After looking around a bit I couldn’t find a decent tutorial that addressed this specific scenario (not one that demonstrated Powershell anyway). I ended up writing this for a client who didn’t have their PKI infrastructure sorted out yet. I prefer to use Powershell as it is much faster and efficient for these steps. (Just my opinion.)
Open Powershell console as an administrator. Follow the screenshots. Few words are needed for this tutorial.
Useful commands:
Get-WindowsFeature *ad* #This will show you the currently installed features
Add-WindowsFeature ADCS-Cert-Authority 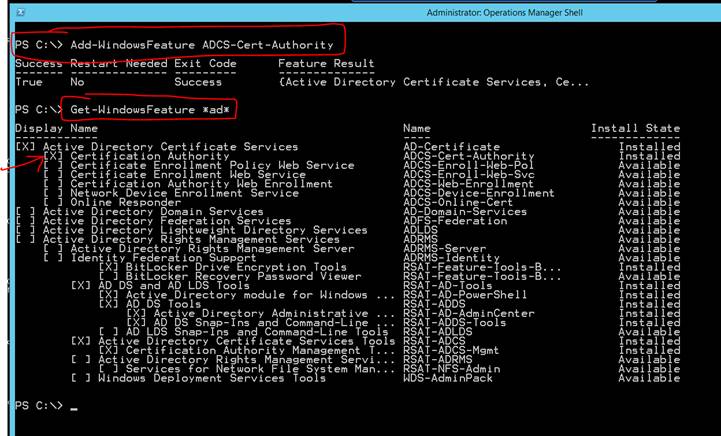
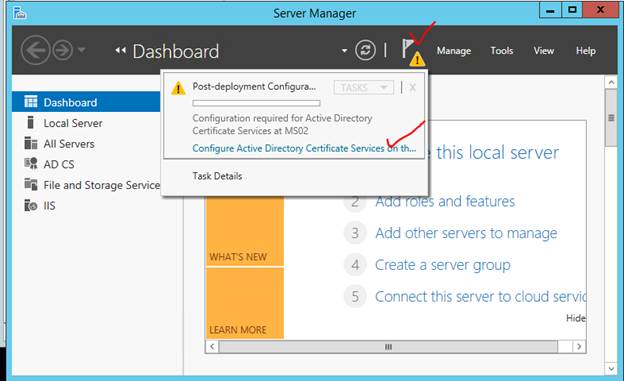
After the Certification Authority is installed, you must configure it from the Server Manager console.
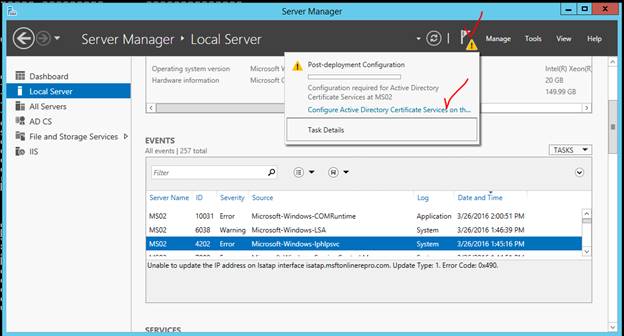
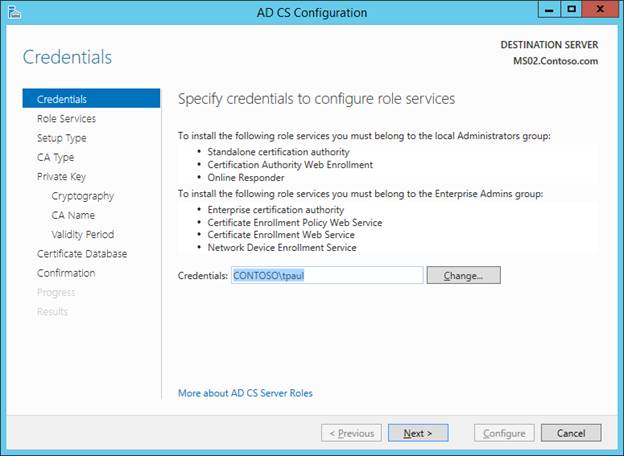
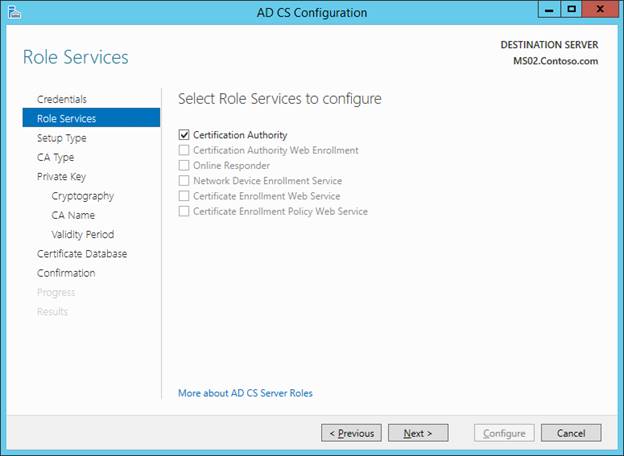
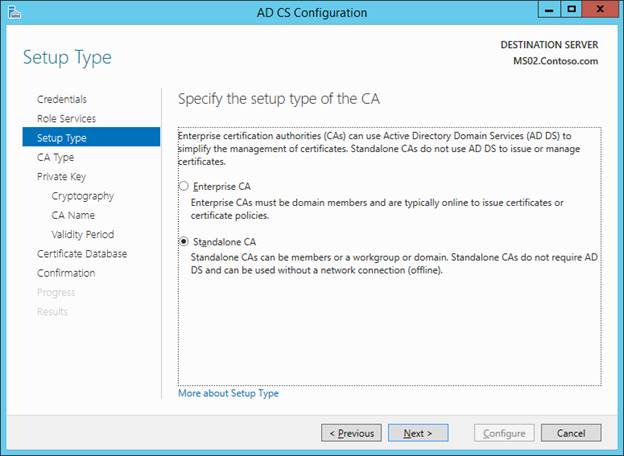
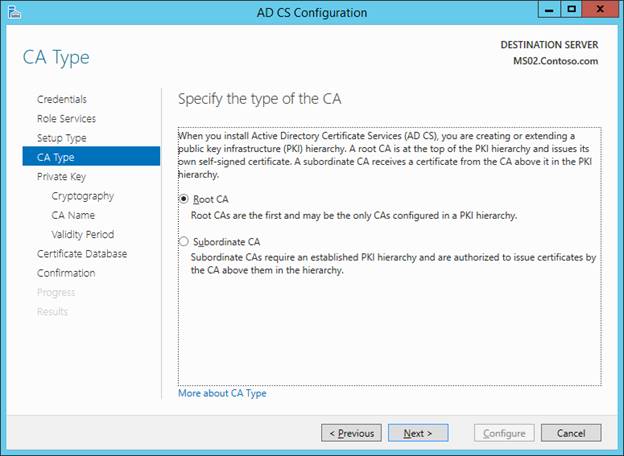
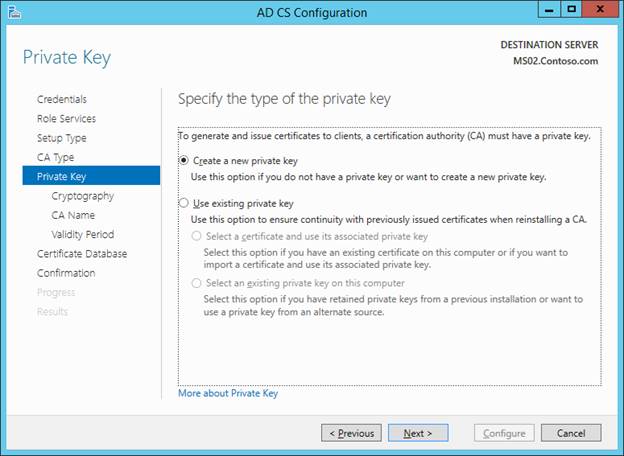
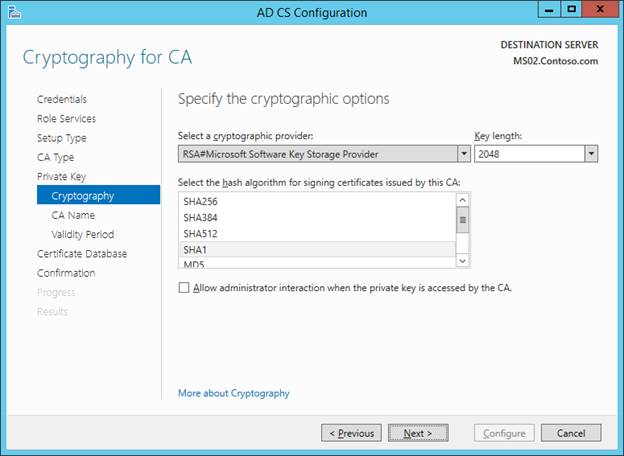
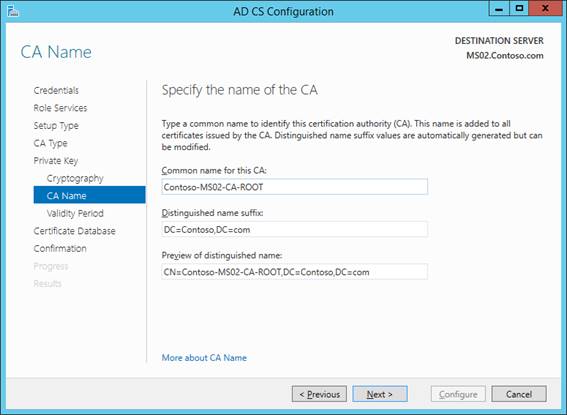
There is NO NEED TO MODIFY THE DEFAULT NAME HERE. However, I don’t think it matters much if you do.
DO NOT USE SPACES IN THE NAME.
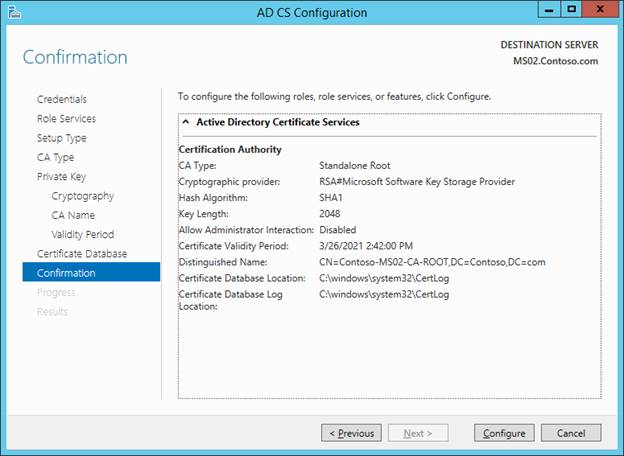
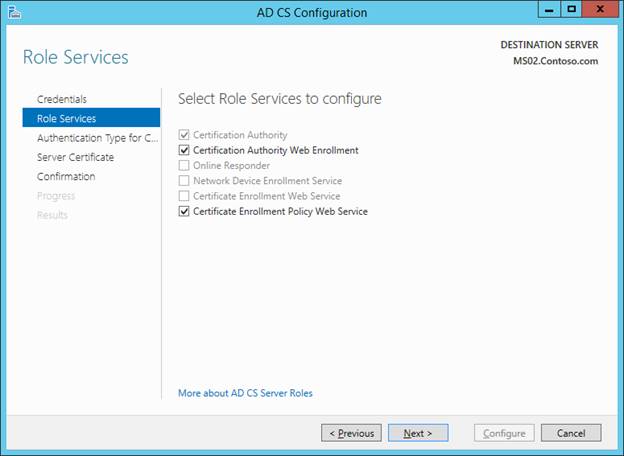
Install these features:
- Certificate Enrollment Policy Web Service
- Certification Authority Web Enrollment
# Install both features with one command
Add-WindowsFeature ADCS-Enroll-Web-Pol, ADCS-Web-Enrollment 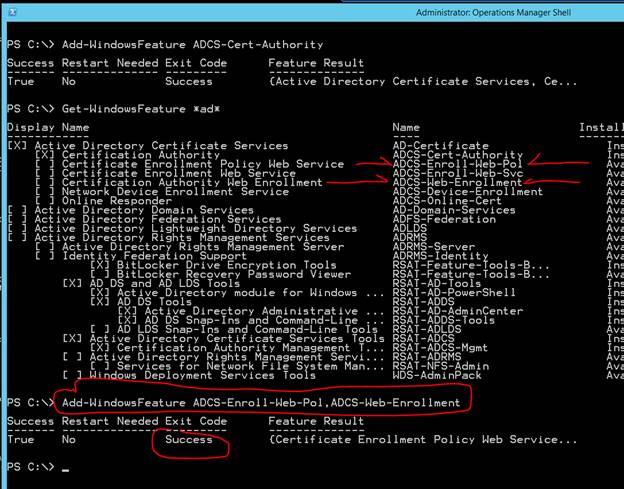
Add the management tool with this command:
Add-WindowsFeature RSAT-ADCS-Mgmt 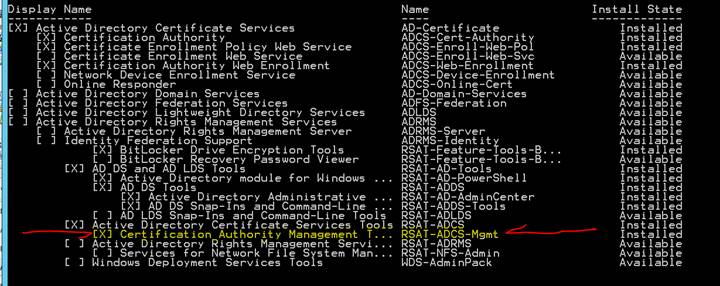
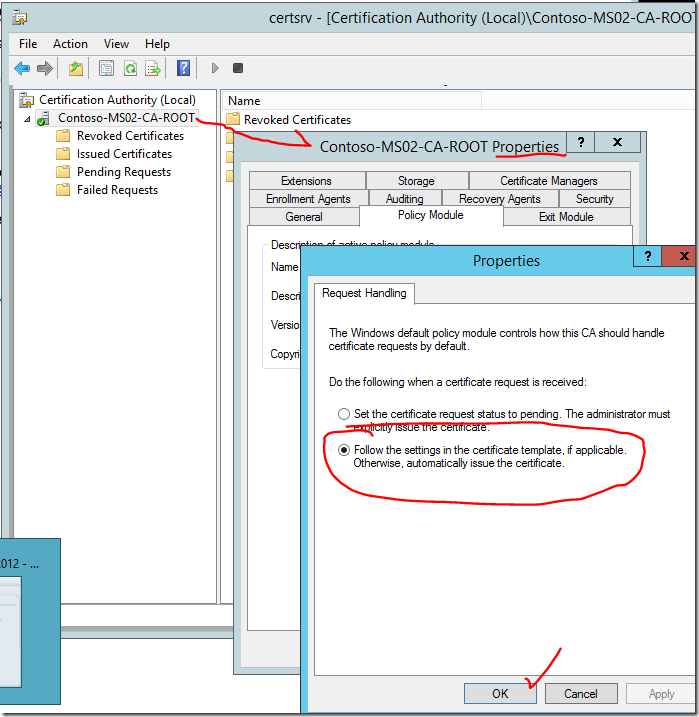
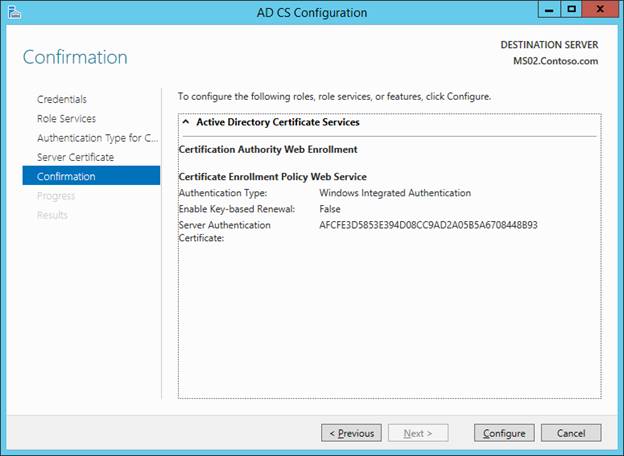
Now you must configure the services.
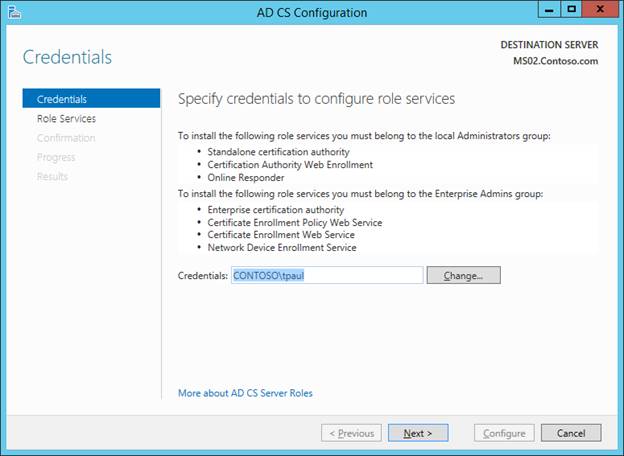
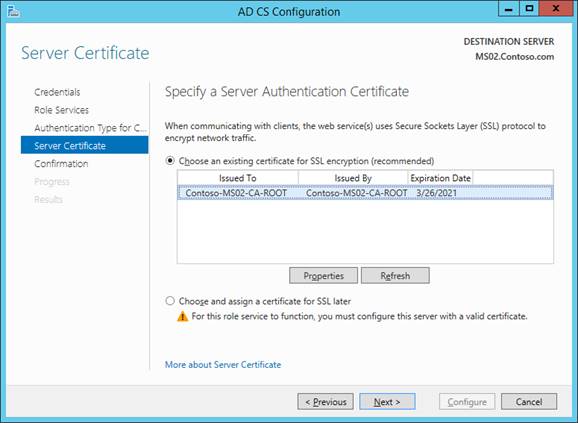
Select the certificate that you just created from the list, then click Next.
When accessing the web cert enrollment portal add your CA’s server address to the Trusted Sites.
It’s best if you use the fully qualified domain name (FQDN) as shown in the picture below.
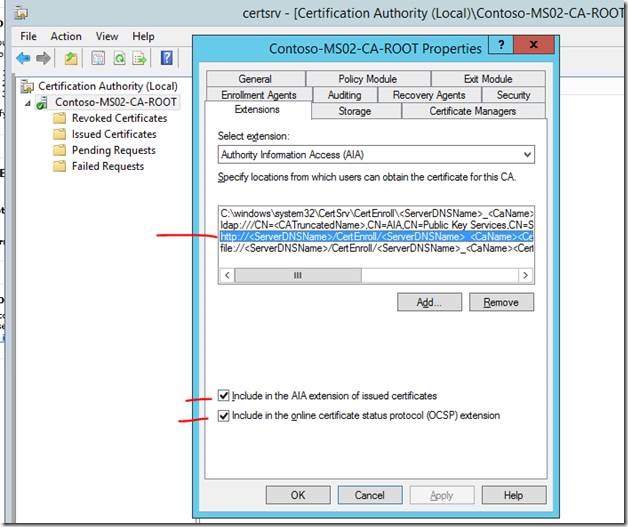
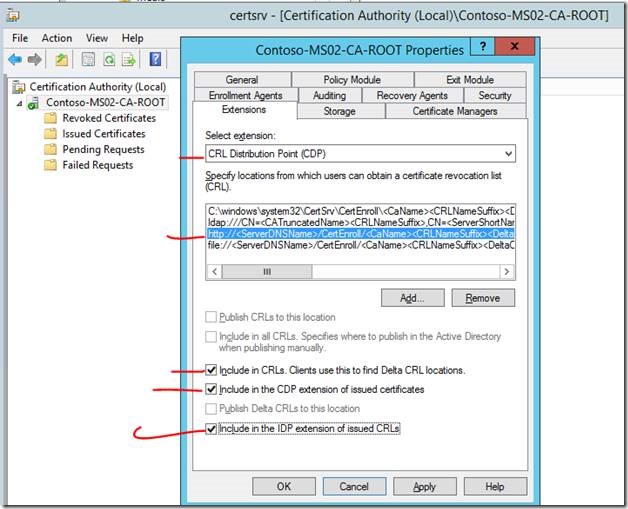
Make sure you configure the AIA and CLR extensions in the Certification Authority tool as shown in the screenshots below. This tool is accessed from the Server Manager console and should have been installed with the Powershell command above.
Make sure you configure the auto-enroll option as shown below:
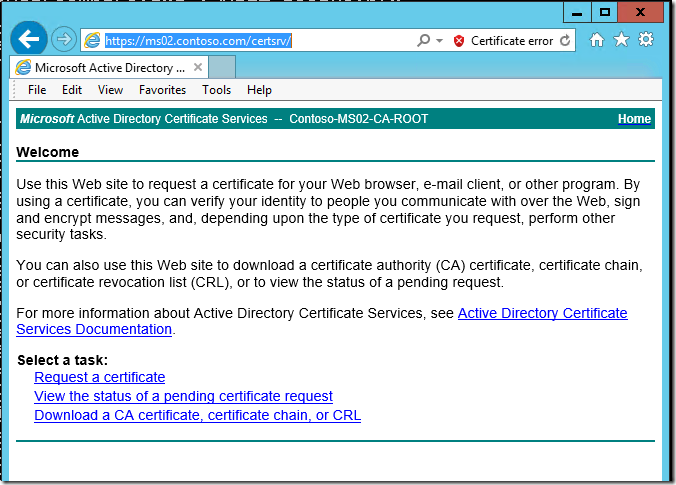
Test the enrollment page
This is what you should see.
Related: Certificate Request from Standalone CA Certificate Authority for Operations Manager, SCOM 2012/R2
Comments
- Anonymous
September 19, 2017
Hi, got an issue when trying to add the Certificate Enrollment Policy Web Service. I get an error saying ccertificateenrollmentpolicyserversetup::inializeinstalldefaults: access is denied. And it then automatically deselected it. Any ideas why this is?- Anonymous
September 19, 2017
@John, This type of error is usually related to a permissions issue. Are you a local admin? Did you launch PowerShell as an Administrator? Perhaps there is some policy or GPO that might prevent it. Hard to say from here.
- Anonymous
- Anonymous
November 22, 2018
I know its an old thread, but having the same issue in Server 2016. Find the problem. Your before you install the ADCS you need to promote your server to DC if not won't let you install the Web-Enrollment- Anonymous
November 26, 2018
As you can see from my screenshots, I did not have to promote my server to DC.
- Anonymous