Security: Test automation From Build and Release pipe using Secrets in Key vault
We follow security guideline at various stages of our application development. Here in this short article I’m going to throw some light with respect to our VSTS build/Release pipe where we can easily secure user credentials that we use to run Test cases, Load test etc., by using Key vault.
Key vault has been in use for long and its uses are pretty much known to all of us. While accessing it from a web API it’s obvious that we secure the process of connecting to key vault. A detailed explanation of how to do this has been already included in this MSDN article. Again, the MSI takes this to a next level where don’t even have to bother storing the certificates. You can read all of that here.
Coming to what this article is about, when we have our CI/CD pipe configured, it is important for us to have access to credentials for a lot of things. for example, run integrated test. When we think of this from security stand point, given we do not have access to our certificates on the build or the test agents it becomes necessary for us to have a way to key vault (to access the secrets in it) without storing secrets or key in the deployment scripts. This is easily possible by using Azure key vault task
With service principal we can configures variable group and fetch it at the run time directly from the key vault in our build and release definitions.
As mentioned here, I’m adding the Pre-requisites again in this article for simplicity
The task has the following pre-requisites:
- An Azure subscription linked to Team Foundation Server or VSTS using the Azure Resource Manager service endpoint.
- An Azure Key Vault containing the secrets.
You can create a key vault:
- In the Azure portal
- By using Azure PowerShell
- By using the Azure CLI
Once we have the above pre-requisites, below are few more steps that will help you access the secrets from our definitions.
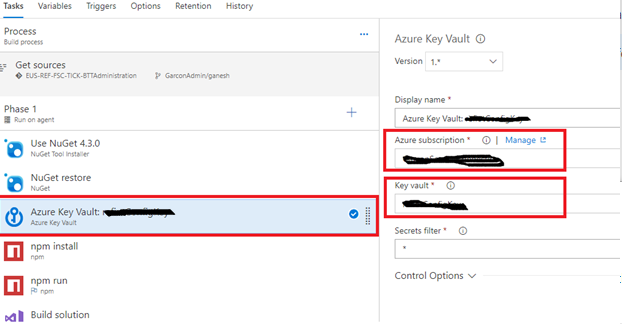
- Add Azure key vault task and point it to the service principal created along with the key vault that you want to use. A Secrets filter value of ‘*’ will pull the secrets.
- For us to able to access the secrets we need to configure variable group that’s our next step. Browse to Library-> VariableGroup
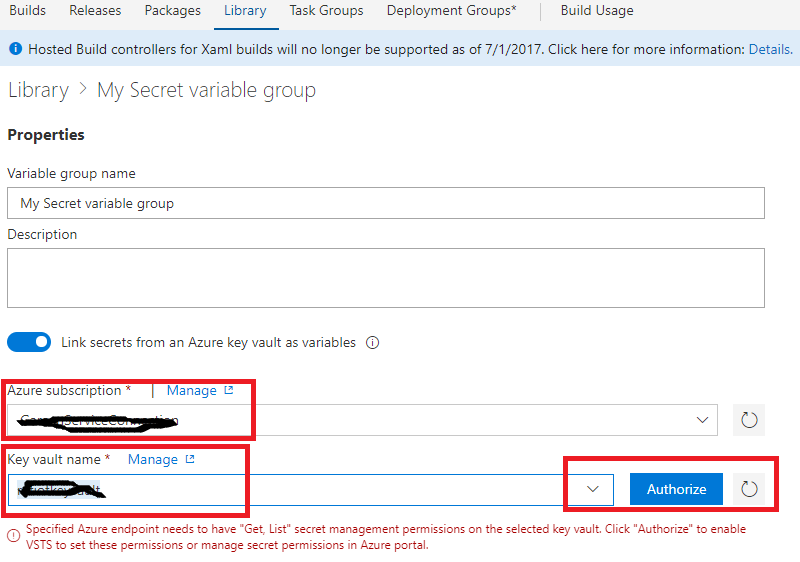
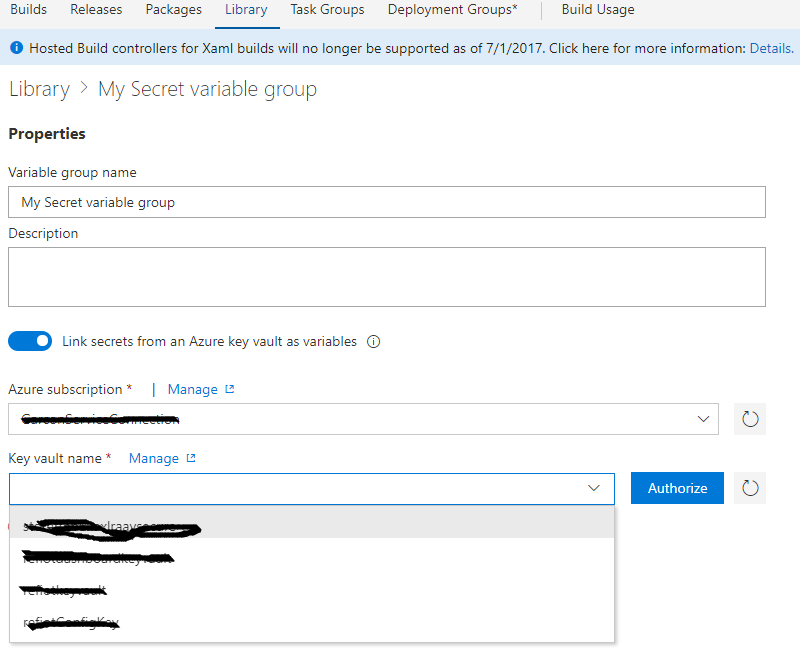
3. As shown below specify your service endpoint, and select your key value from the drop-down list
4. Its important to authorize the selected key vault so that its accessible from the build/release definition.
- Now you can select all the secrets that you want to access from the build definition by adding them as shown below.
- Finally, you can access them in your definitions as parameter. For example, you want to access the DatabaseConnection that’s part of your key vault, you can specify them as $(DatabaseConnection).
Now, that’s you get rid of secrets and certificate dependency from your build and release pipeline.
Happy coding!
Ganesh Shankaran