Accesing Azure Security Center API with Powershell Invoke-RestMethod
Accessing Azure Security Center API with Powershell Invoke-RestMethod
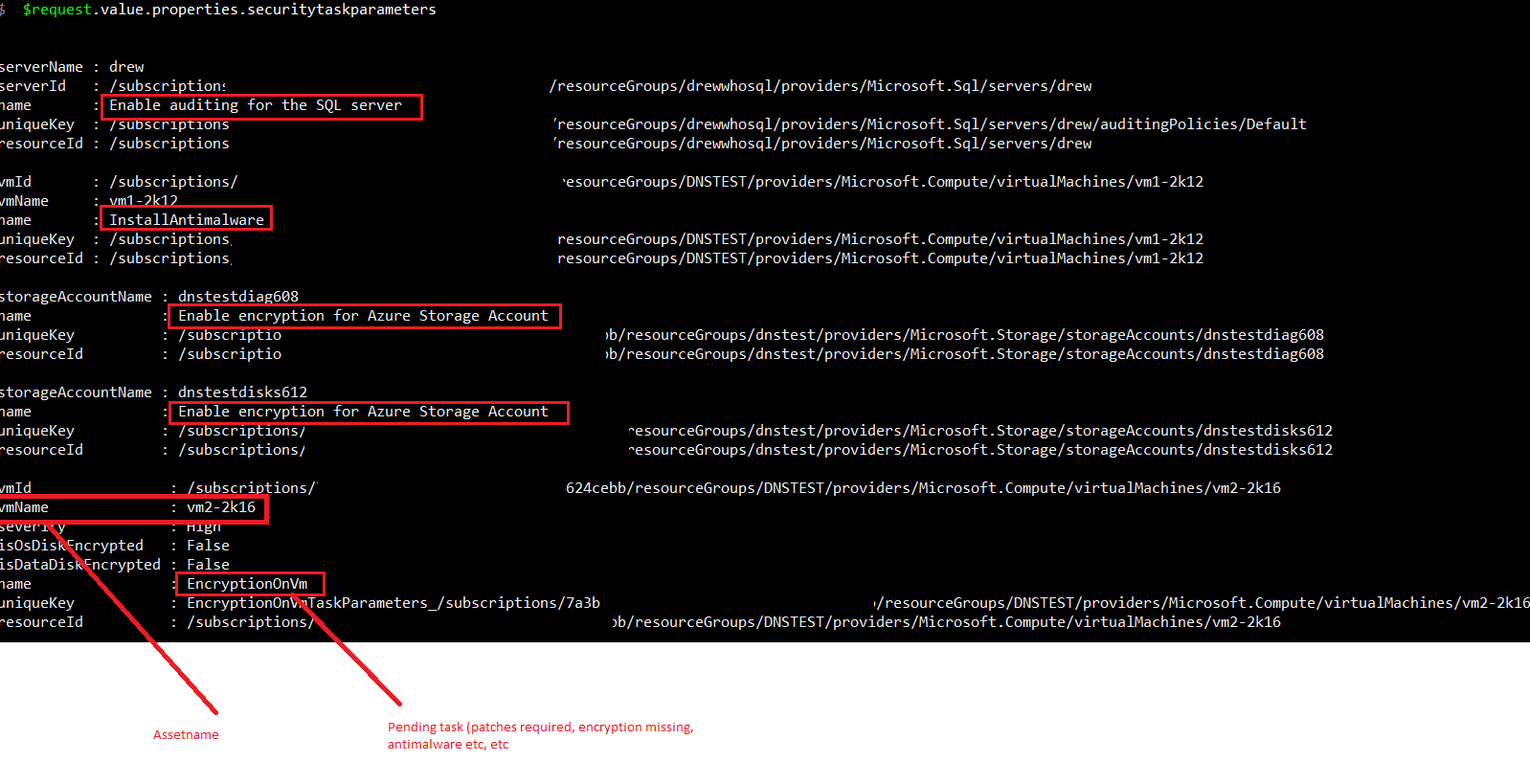
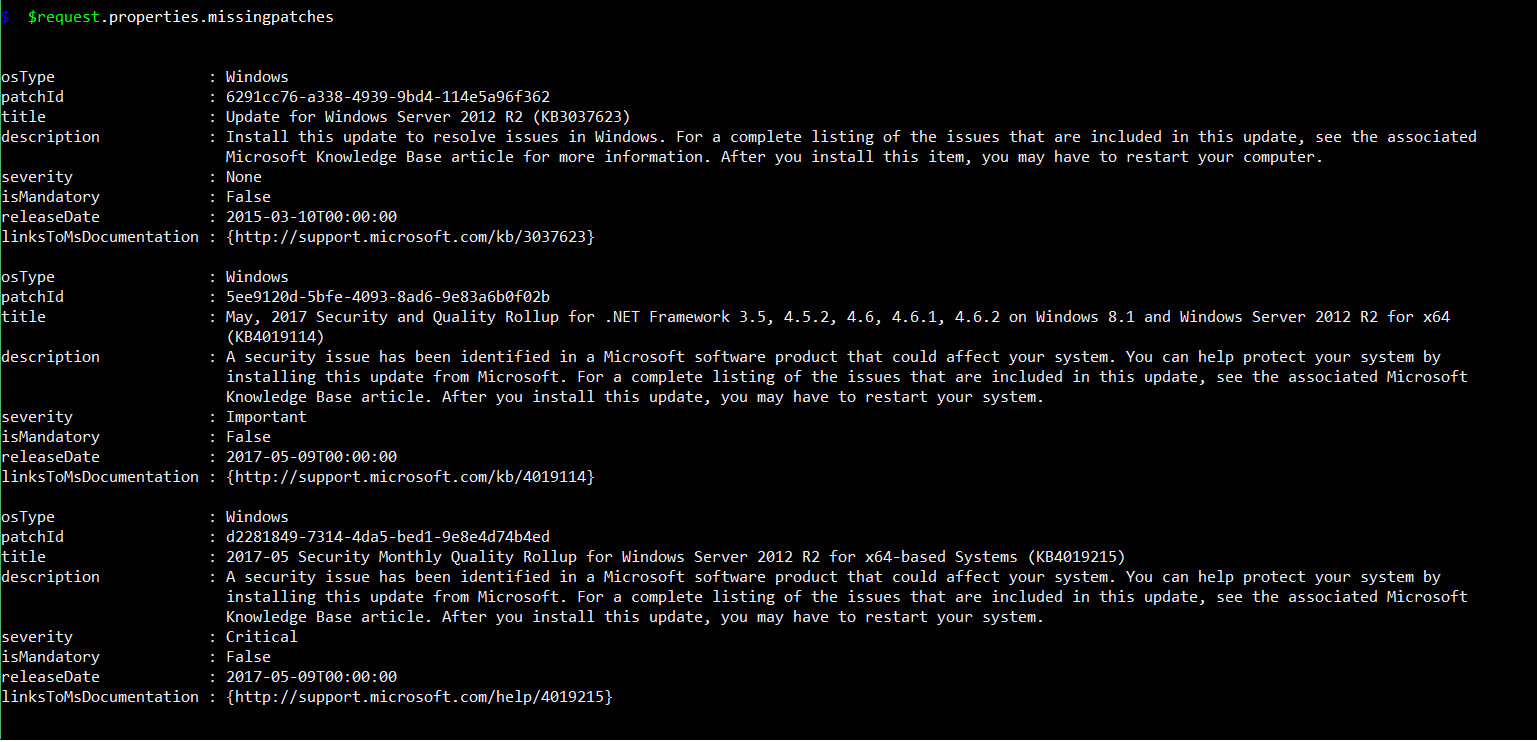
Listing missing patches on Azure VMs with Collection Results API
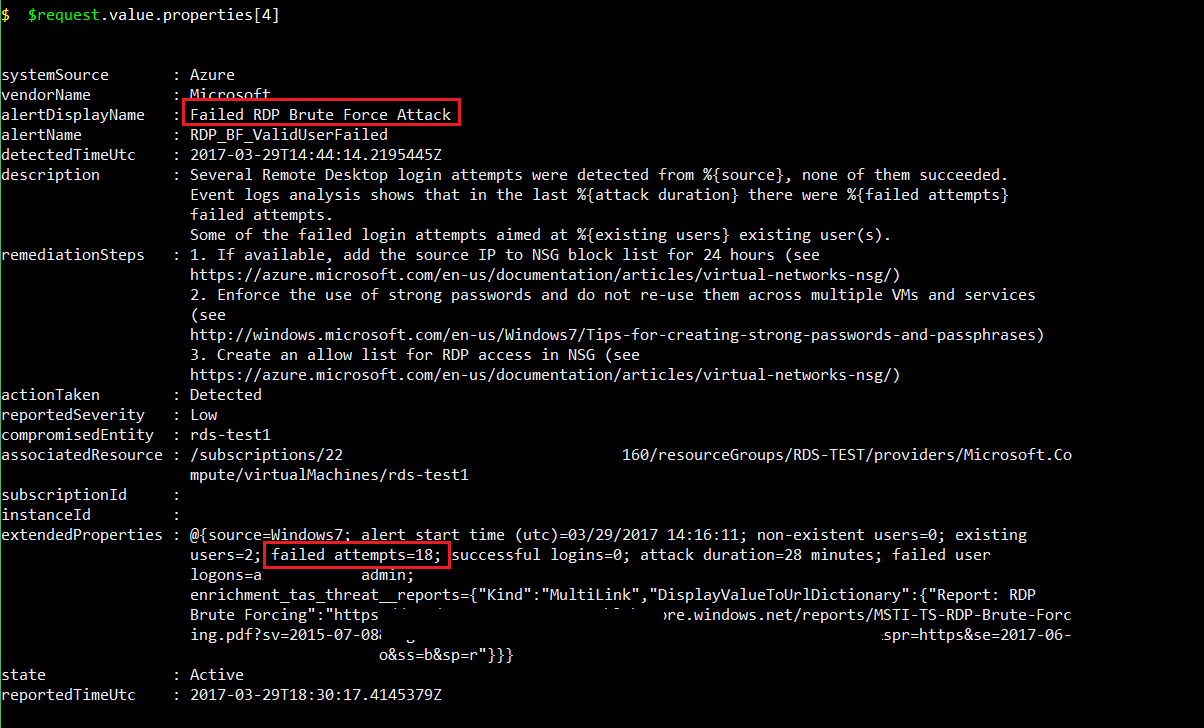
Listing Alerts using the Alert API, such as RDP brute force attempts showing failed and successful logons:
The following will allow you monitor or set your Azure Security Center settings via Powershell/REST
Getting started:
You will first need to provision a service principal that can access your Azure subscription (Windows Azure Service Management API), so your REST call can auth into your subscription.
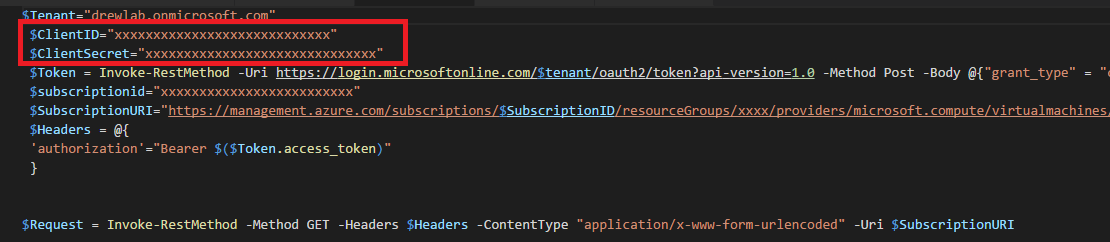
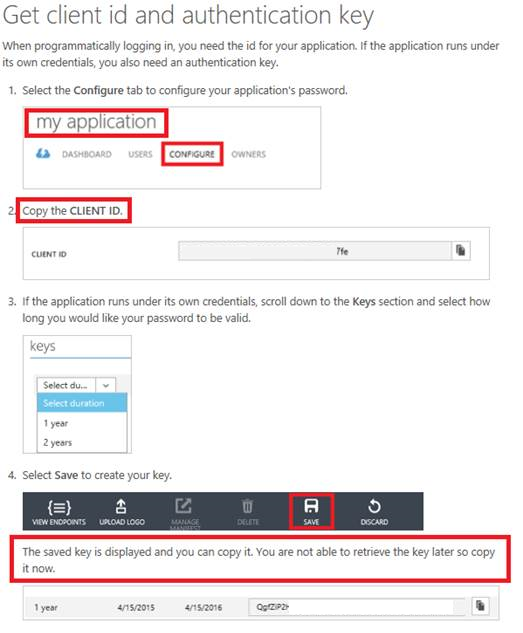
2. Save the following: application name, client id, client secret (key) , note: you can’t recall the key.. so important to save it at time of creation.
Via Azure Portal - Subscriptions, Subscription - IAM 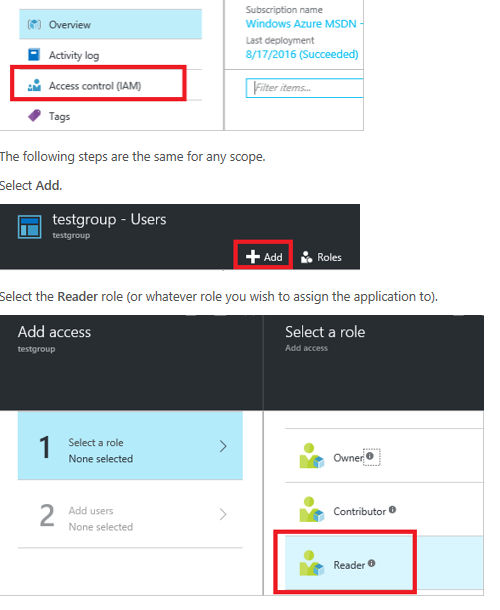
Set subscription access (you can change this at anytime) :
- read (view ASC status, policy)
- contribute (change/update ASC policy, ack alerts)
Plan on how you will use the ASC API: https://msdn.microsoft.com/en-us/library/mt704039.aspx
Azure Security resources listed in red:
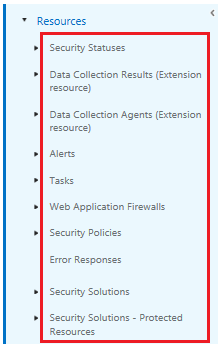
Example, we are interested in Azure Security Status: https://msdn.microsoft.com/en-us/library/mt704041.aspx
We will use the following: https://<endpoint>/subscriptions/{subscriptionId}/providers/microsoft.Security/securityStatuses?api-version={api-version} 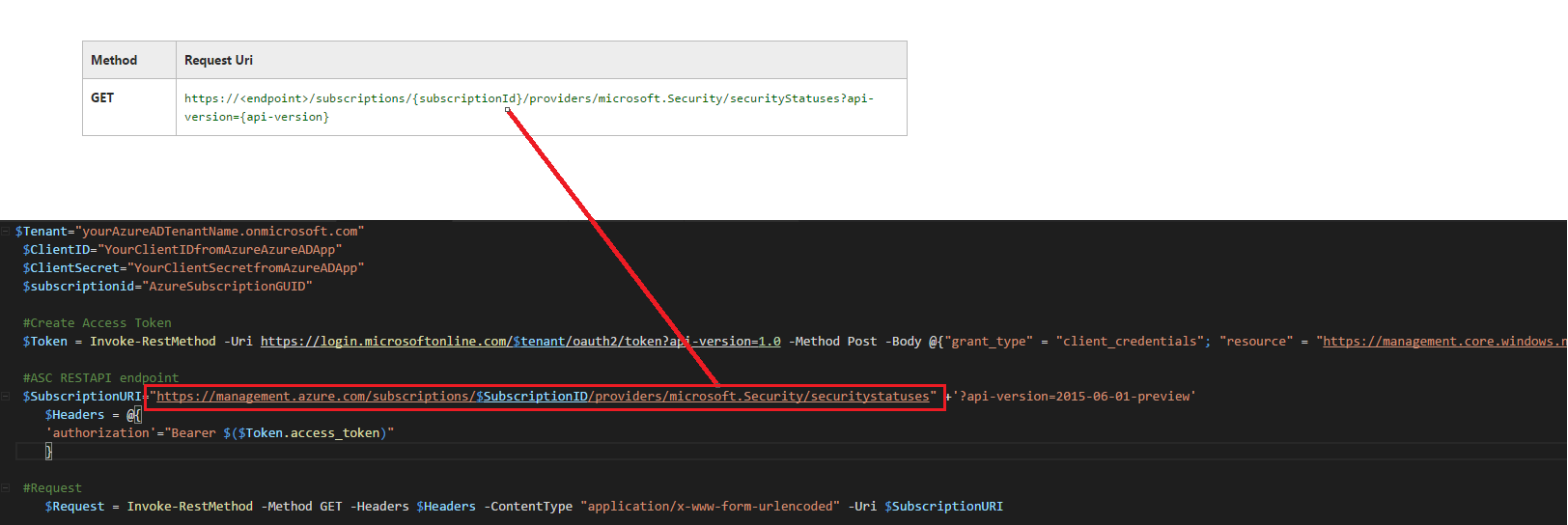
CODE:
|
|
Output for $request.value
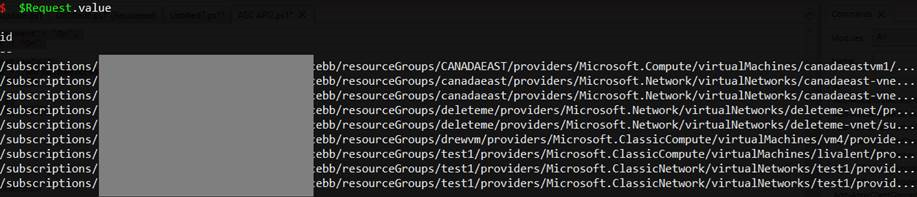
Selecting the first resource group [0] and listing ASC properties
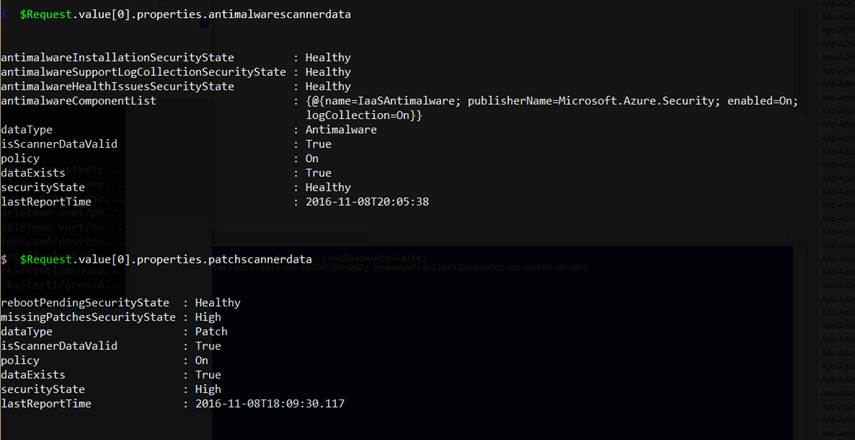
Outputting two ASC properties from collection 0
$Request.value[0].properties.antimalwarescannerdata
$Request.value[0].properties.patchscannerdata
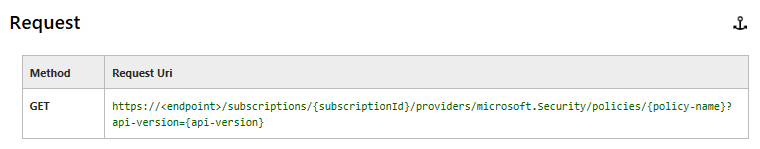
Setting ASC policy via API.
Rerernce: https://msdn.microsoft.com/en-us/library/mt704062.aspx
CODE: (Notice the URI has changed)
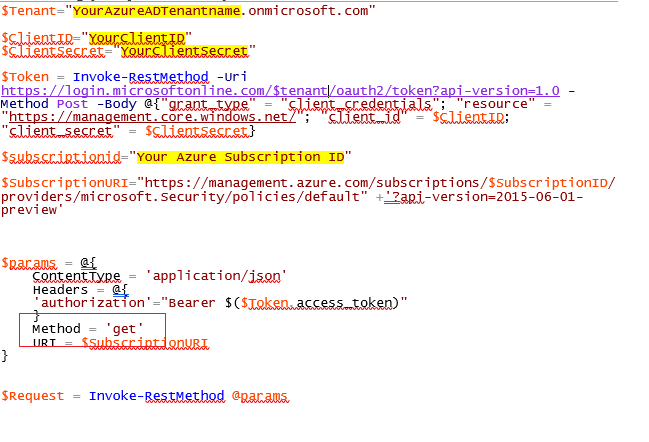
$Tenant="YourAzureADTenantname.onmicrosoft.com"
$ClientID="YourClientID"
$ClientSecret="YourClientSecret"
$Token = Invoke-RestMethod -Uri https://login.microsoftonline.com/$tenant/oauth2/token?api-version=1.0 -Method Post -Body @{"grant_type" = "client_credentials"; "resource" = "https://management.core.windows.net/"; "client_id" = $ClientID; "client_secret" = $ClientSecret}
$subscriptionid="Your Azure Subscription ID"
$SubscriptionURI="https://management.azure.com/subscriptions/$SubscriptionID/providers/microsoft.Security/policies/default" +'?api-version=2015-06-01-preview'
$params = @{
ContentType = 'application/json'
Headers = @{
'authorization'="Bearer $($Token.access_token)"
}
Method = 'get'
URI = $SubscriptionURI
}
$Request = Invoke-RestMethod @params
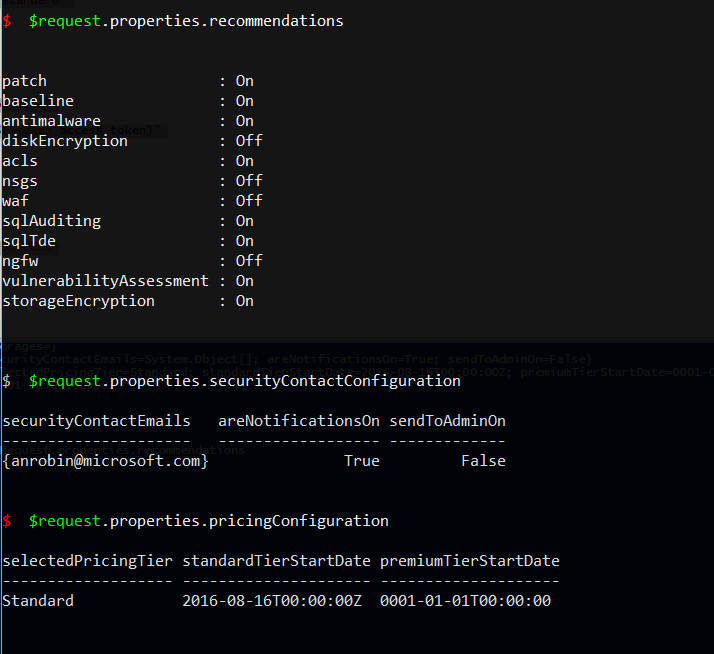
Showing settings via $Request.properties
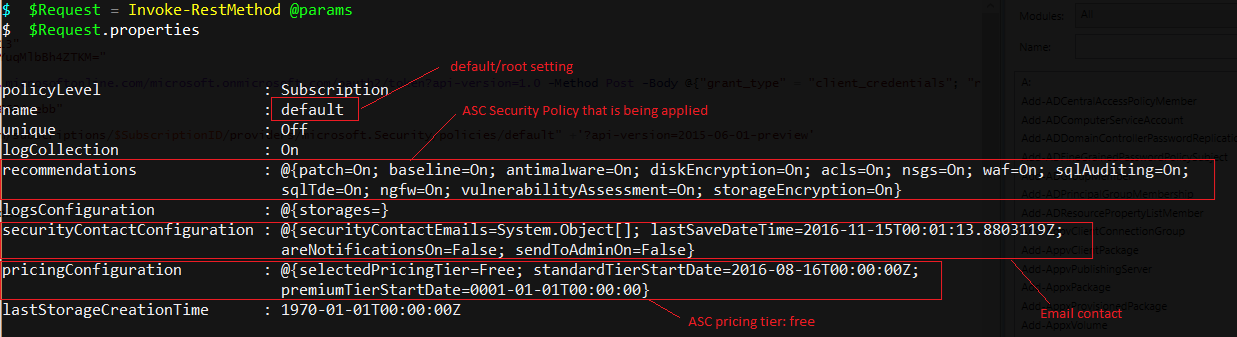
- all recommendations
- no email notification
- free tier
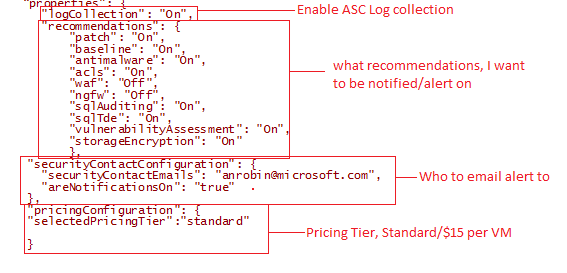
To set ASC policy, we create the following json for a PUT request
"properties": {
"logCollection": "On",
"recommendations": {
"patch": "On",
"baseline": "On",
"antimalware": "On",
"acls": "On",
"waf": "Off",
"ngfw": "Off",
"sqlAuditing": "On",
"sqlTde": "On",
"vulnerabilityAssessment": "On",
"storageEncryption": "On"
},
"securityContactConfiguration": {
"securityContactEmails": "drewwho@microsoft.com",
"areNotificationsOn": "true"
},
"pricingConfiguration": {
"selectedPricingTier":"standard"
}
CODE:
$Tenant="YourAzureADTenantname.onmicrosoft.com"
$ClientID="YourClientID"
$ClientSecret="YourClientSecret"
$Token = Invoke-RestMethod -Uri https://login.microsoftonline.com/$tenant/oauth2/token?api-version=1.0 -Method Post -Body @{"grant_type" = "client_credentials"; "resource" = "https://management.core.windows.net/"; "client_id" = $ClientID; "client_secret" = $ClientSecret}
$subscriptionid="subscriptionid"
$SubscriptionURI="https://management.azure.com/subscriptions/$SubscriptionID/providers/microsoft.Security/policies/default" +'?api-version=2015-06-01-preview'
$ASCPolicy='
{
"properties": {
"logCollection": "On",
"recommendations": {
"patch": "On",
"baseline": "On",
"antimalware": "On",
"acls": "On",
"waf": "Off",
"ngfw": "Off",
"sqlAuditing": "On",
"sqlTde": "On",
"vulnerabilityAssessment": "On",
"storageEncryption": "On"
},
"securityContactConfiguration": {
"securityContactEmails": "drewwho@microsoft.com",
"areNotificationsOn": "true"
},
"pricingConfiguration": {
"selectedPricingTier":"standard"
}
}'
$params = @{
ContentType = 'application/json'
Headers = @{
'authorization'="Bearer $($Token.access_token)"
}
Method = 'put'
URI = $SubscriptionURI
Body = $ASCPolicy
}
Invoke-RestMethod @params
Confirming Policy via get request, CODE (notice method is now 'get' and json remove)
Output: $request.properties
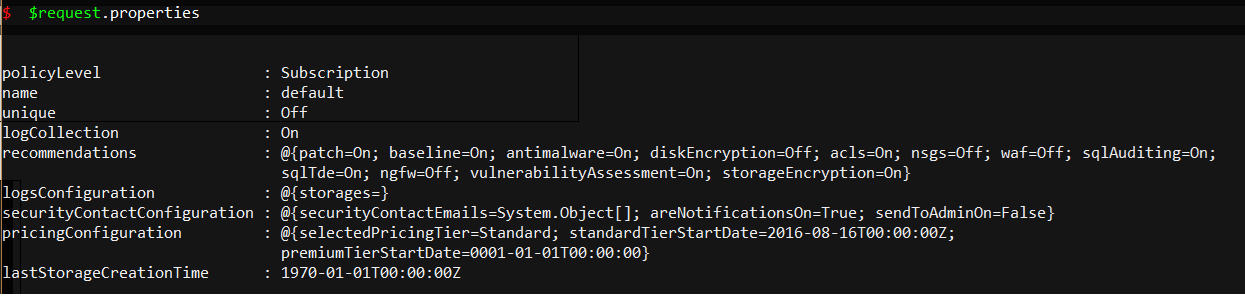
Nicely formatted output