SQL Vulnerability Assessment now available for SQL Server 2012 and up
SQL Vulnerability Assessment has been available for preview on Azure SQL Database for a couple of months, and has now been released on SSMS 17.4, supporting scanning of SQL Server 2012 and up. Whether on-premises or on a VM!
SQL Vulnerability Assessment
SQL Vulnerability Assessment (VA) is your one-stop-shop to discover, track and remediate potential database vulnerabilities. It can be used as an excellent preventive security measure, providing visibility into your security state and offering actionable steps to investigate, manage and resolve security issues and enhance your database fortifications.
[caption id="attachment_2915" align="aligncenter" width="879"]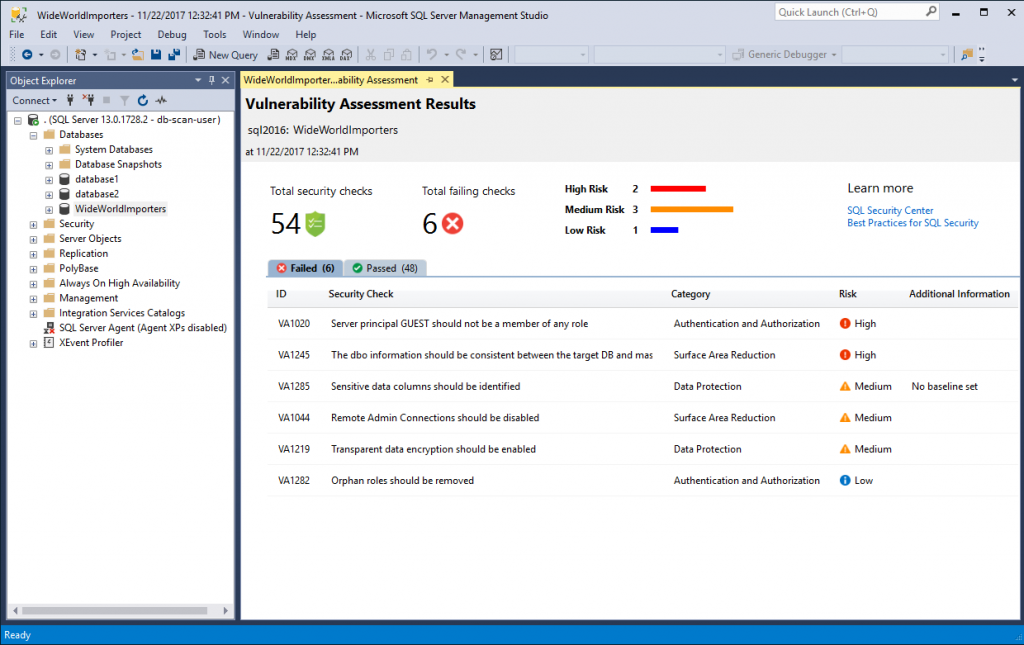 Vulnerability Assessment report in SSMS[/caption]
Vulnerability Assessment report in SSMS[/caption]
Not only does VA expose some of the possible security flaws you have in your database system, it also provides remediation scripts to resolve issues within a couple of mouse clicks. In addition, you can accept specific results as your approved baseline state, and the VA scan report will be customized accordingly to expect these values.
[caption id="attachment_2935" align="aligncenter" width="741"]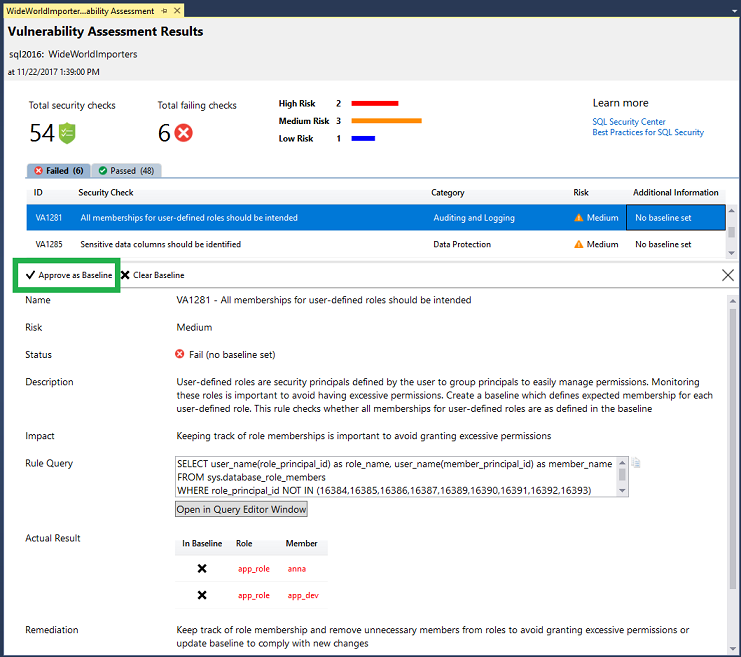 Approving a VA result as your baseline[/caption]
Approving a VA result as your baseline[/caption]
Beyond improving your database security, VA can be an invaluable tool to help meet data privacy requirements or help comply with data protection regulations like the EU GDPR. VA simplifies the processes involved in addressing these, and also facilities ongoing monitoring of your database protection status.
What are people saying about Vulnerability Assessment?
VA was designed to be straightforward and easy to use, giving you a simple way to improve your database security stature.
Our preview customers have been using the service to lock down their database security, and to help address their data privacy requirements.
Customers have been most impressed with the quick and lightweight nature of the scan. They are also very appreciative of the actionable remediations available directly within the VA experience.
“I personally like the tool, and the feedback from other teams has been positive. Everyone found the tool very easy to run, the findings easy to understand, and fixes were straightforward thanks to the remediation scripts. ”
- Anton Popov, Principal Security Engineer at Schneider Electric Software, LLC
“This is another example of Microsoft making security more approachable, even if you are not a security expert. After running a scan you will probably see some quick wins making your database more secure step by step.”
- Tom Kerkhove, Azure Consultant at Codit and Microsoft Azure MVP
Now in SSMS
VA has now been released as an integral part of SQL Server Management Studio (SSMS)! You can run an assessment from within SSMS on any database you connect to, whether on-premises or in the cloud. VA supports SQL Server 2012 and up.
Running a VA scan on your SQL Server includes a richer set of security checks than the scan on Azure SQL Database, since there are more relevant checks for the SQL Server surface area. When running a scan from SSMS on your Azure SQL Database, you can expect a similar result to the one you see in the Azure Portal. Your baselines do not persist across, though, so you will need to manage them separately.
To run an assessment from SSMS, all you need to do is connect to your database, right click on the database and select Tasks -> Vulnerability Assessment -> Scan for Vulnerabilities… The scan takes just a few seconds to run, and the results are stored on your local file system, (you can configure the target location). You will then see the full results report in the SSMS pane, and you can drill down to each individual result for details and remediation steps, and to set your result baseline.
For more details on working with VA, see Getting Started with SQL Vulnerability Assessment in SSMS.
Get started now
To get started with VA, download the newest version of SSMS here. VA is supported as of SSMS 17.4.
To learn more about VA, and see an assessment in action on Azure SQL Database, check out this Channel 9 demo.
Be sure to check out Getting Started with Vulnerability Assessment for more details on how to run and manage your assessment.
Try it out and let us know what you think!
Comments
- Anonymous
May 02, 2019
How and when are the rules used in SQL VA updated? Can you please provide a documentation link to this information if it exist? I can't seem to find it. ThanksAK- Anonymous
May 04, 2019
Hi AK,The VA rules are periodically updated as new security content is added and rules are updated to align with new features in SQL. There isn't currently any publicly available documentation on this process - we will consider how to expose this information better to customers.Thanks!- Anonymous
May 06, 2019
Hi Ronit,Thanks for the response. By periodically, do you mean the VA rules are updated along with Sql Server Management Studio?ThankAK- Anonymous
May 12, 2019
Hi AK,Yes, the VA rules engine used by SSMS is currently baked into SSMS - so updates to the rules would be aligned with releases of SQL Server Management Studio.
- Anonymous
- Anonymous
- Anonymous