Kerberos configuration for Clients accessing Role Center from outside of intranet
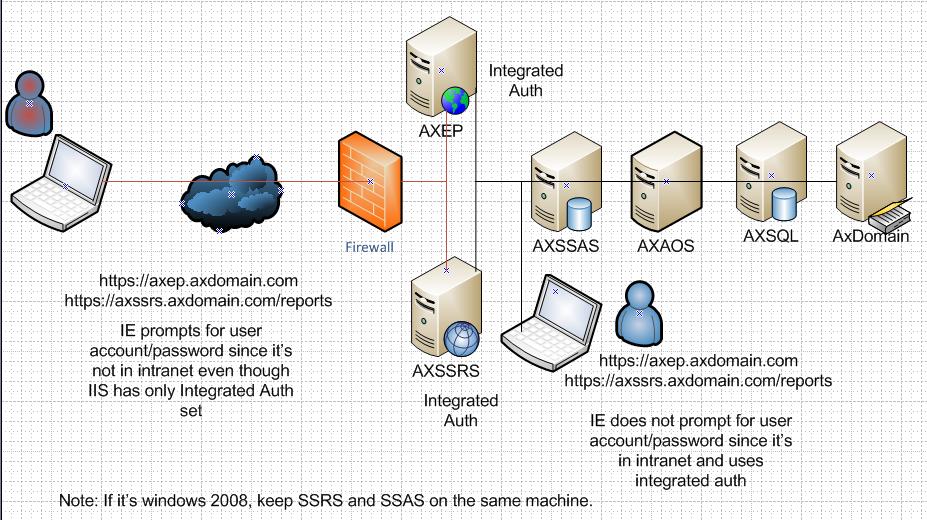
If you have EP/Role Centers rolled out in your intranet with Kerberos configured ( refer to Kerberos configuration document ) and now would like to expose this to your domain users outside of your corpnet, for example employee would access their role center from home, then you need to additionally configure Kerberos protocol configuration. You might have got enabled your firewall settings to allow them to access the EP and Reporting servers from outside network. Since the user comes outside of the network, IE will prompt them to enter the user account / password even though IIS authentication is set to windows integrated authentication. In this case, for Kerberos to work you need to configure protocol transition in Kerberos. To do that
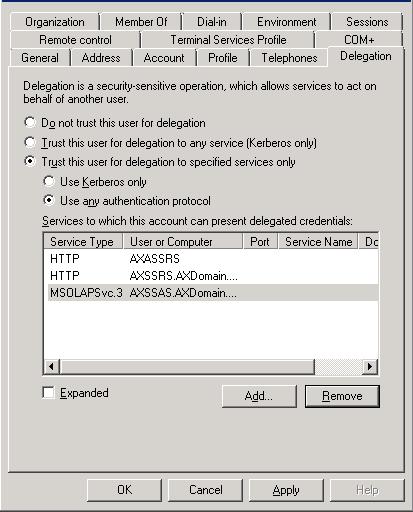
1. Open up your “Active Directory Users and Computers” admin tool on your domain controller and locate the user account that you are using as business connector proxy and right click and open up its properties window.
2. Navigate to the “Delegation” tab and change the setting to “Trust this user for delegation to specified services only” and “User any authenticate protocol”.
3. Click the add button in the “Delegation” tab. It will bring up the “Add Services” dialog.
4. Click on the “Users or Computers” button. It will bring up the “Select Users or Computers” dialog.
5. Enter the account that is used as business proxy account ( This is the same account that the EP and report web site use as the application pool and the SSAS window service logon account).
6. Click “OK”. This will close the “Select Users or Computers” dialog and list the services (SPNs registered for Kerberos for the bc proxy account) in the “All Services” list of “Add Services: dialog.
7. Click “Select All” and then “OK” in “Add Services” dialog. This will close “ADD Services dialog” and list them in “Services to which this account can present delegated credentials” list in the “Delegation” tab.
8. Click “OK” to save this setting to the user account.
9. Do “IISReset” on the EP server
The alternate approach could be to use ISA 2006 as the firewall and let ISA collect the user account/password using a form over ssl and ISA will user Kerberos constrained delegation.
https://technet.microsoft.com/en-us/library/bb794858.aspx
Comments
Anonymous
May 20, 2009
PingBack from http://asp-net-hosting.simplynetdev.com/kerberos-configuration-for-clients-accessing-role-center-from-outside-of-intranet/Anonymous
June 01, 2009
Thanks for the info, very handy. You mention in your figure to keep SSAS and SSRS on the same machine if using WIN2008? Any specific reason for that? Thanks again, OleAnonymous
June 17, 2009
Not sure this will really work. In AX you specify the Report Server url as http://ssrs/reportserver and that short name is used in the role center view. when you log into the EP portal via a public URL, it will say verify your Report Server URL since the shortname is not resolveable via the internet. If there are more settings, then please post them as articles with only partial information just frustrates those of us trying to deploy this via info from Blogs, forums, etc. ThanksAnonymous
August 06, 2009
There was a bug in Windows 2008 that prevented SSAS/SSRS on different machines with kerberos configuration. I think now there is a hotfix available from SSAS to resolve this issue.Anonymous
July 13, 2010
you can open AX client , goto Administration-->business intellgence-->reportservers--> change the report server with long name