Automating Intune DEP Profile Assignment
Update: As of April 2018, we have started rolling out our new DEP experience in Intune. Once your tenant receives this update, you will no longer need to use Graph API and automation to ensure that the profiles are assigned to DEP devices. Check here to determine if your tenant has been updated based on the UI you see: /en-us/intune/device-enrollment-program-enroll-ios
Once your tenant is updated you can go through and assign your default profile and new devices will assign it as they flow in to Intune through DEP.
Note: The Graph API calls we were using in the script below are also being updated, so the process below will no longer function once your tenant is upgraded to the new DEP experience. If you did set the automation described in the post below, you can simply go and remove the scheduled task you created so it no longer runs daily.
With Intune's migration to the Azure portal, the default Device Enrollment Program (DEP) profile functionality was eliminated. While this prevents unintentional profile assignment, we heard from customers that they want to automate the assignment of enrollment profiles. Thanks to the Microsoft Graph API, you can do just that!
Keep reading to find out how you can automate this in your environment and save your Help Desk and Intune admins a lot of time!
- Why Should I Automate DEP Profile Assignments?
- Configuration Steps
- What Else Can I Do with Graph API?
Why Should I Automate DEP Profile Assignments?
Customers who use Apple's Device Enrollment Program often have new devices flowing in to Intune daily. When this is the case, it can be a lot of work to constantly sign in to the Intune portal and ensure that all of your devices have a profile assigned prior to them reaching your end users. If a device makes it to an end user before a DEP profile is assigned, it will be treated as a standard device and not a corporate-owned DEP device. To help decrease the overhead of ensuring all devices have a profile assigned, you can leverage Graph API to do this work for you!
Configuration Steps
Delegate Rights to Execute Graph Scripts to Non-Global Admins
The first time you run this script if you are using a "service account", you will need to execute another script for this to work properly. By default, non-Global Admins do not have the ability to execute Graph API calls unless a GA delegates rights to them. To allow this account to execute the script, you first must assign it rights within Intune. The easiest way to do this is to assign the account the AAD role "Intune Service Admin" since this will give the account the user rights to execute these Graph API calls.
NOTE: You will not want to have this account enforce MFA since you are trying to automate this action. MFA requires user input, so to make this a truly automated task, do not require MFA for this account
Next, you need to run the Admin Consent script from our Intune PowerShell Samples site on GitHub. You can find a copy of this script here: https://github.com/microsoftgraph/powershell-intune-samples/blob/master/AdminConsent/GA_AdminConsent_Set.ps1
Tip: You can copy this into Notepad and save it as a .ps1
-
- Once you have a copy of the script from the link above, you will launch it with PowerShell. When prompted for the Azure AD Username, enter the UPN of your "service account" to specify this as the account you want to delegate permission to.
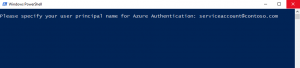
- You will then get a notice that this application needs rights that only a Global Admin can grant. Choose "sign in with another account" and complete sign in with the Global Admin (GA) account
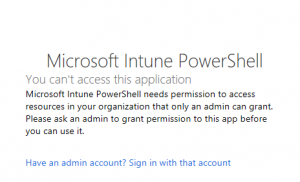
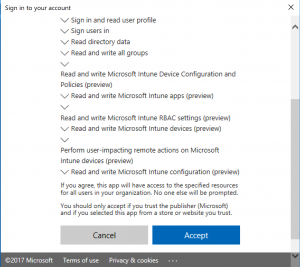
- Accept the permissions
- Once you have a copy of the script from the link above, you will launch it with PowerShell. When prompted for the Azure AD Username, enter the UPN of your "service account" to specify this as the account you want to delegate permission to.
Once this is complete, you can set up the automated DEP profile assignment.
Set Up the Automation Required to Assign DEP Profiles
There are a few pre-requisites you must complete prior to creating the Scheduled Task that will run the PowerShell script to automate assigning DEP profiles.
- Create a secure password file for the service account and store it in an accessible location (i.e. in Documents, Desktop, etc). You can create the secure password file by running this cmdlet in PowerShell:
Read-Host -Prompt "Enter your tenant password" -AsSecureString | ConvertFrom-SecureString | Out-File "<Enter File Path>\credentials.txt" - Download a copy of the automation script here: https://gallery.technet.microsoft.com/Automate-DEP-Profile-0657c740
- You need to update three variables in the PowerShell sample. You find these located towards the bottom of the script. Here are the three variables:
NOTE: To easily find the variables you need to update in the script, open in PowerShell ISE and search for #UPDATE
$User - the username of your service account that will be executing the daily task to assign DEP profiles (NOTE: this account does need admin rights to Intune, meaning it will also need an Intune license)
$Password - this is the path to the secure password file that you created previously. It needs to be created and stored on the server that will be executing the daily task. You cannot move this file around to other machines and use it since it only works on the machine it was generated on.
$global:profileID - this is the GUID of your DEP profile that you have created in Intune. To get this guid, you must navigate to the Corporate Device Enrollment profile in the Intune portal, and the GUID is located at the end of the URL. Here is an example URL that shows you where the GUID is located: https://portal.azure.com/#blade/Microsoft_Intune_Enrollment/EditAcProfileBlade/overview/profileId/af897c67-05ac-469f-b6c1-64a9fa41eaea - Once you have the script and have saved the updated variables, you will use this to create your Scheduled Task
Create the Scheduled Task
Now that you have your script, let's create our Scheduled Task. You should create this task on a server (or Windows 10 machine) in your environment that is consistently online and available, so that you can ensure the script will run at the same time every day. As a side note, on this machine you will need to make sure you have the latest Azure AD PowerShell module installed. You can install this by simply launching PowerShell as an admin and running this cmdlet: Install-Module -Name AzureAD
NOTE: If you are running a version of Windows Server (or Windows) other than Windows Server 2016 (or Windows 10) on the machine you are setting up the scheduled task, you will need to install the latest version of the Windows Management Framework to be able to install the Azure AD PowerShell module. You can download WMF 5.1 here: https://www.microsoft.com/en-us/download/details.aspx?id=54616
This will install the module on the server so that way the automation script for assigning DEP profiles will work.
Back on track, here is what we need to do to create the task…
- On the machine you have selected to host this, launch the Start Menu and search for "Task Scheduler"
- Right-click on "Task Scheduler (Local)" and choose "Create Task"
- Give your Task a name and choose which account you will have execute this task -- you will need to choose an account that exists on the machine, choose to run whether logged on or not, and store the password
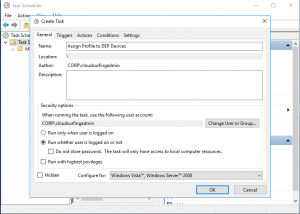
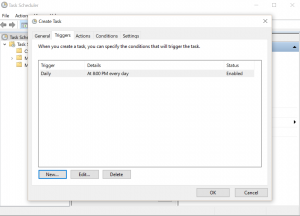
- Set up your Trigger to run this task at a specific time, daily
- Choose your Action to "Start a program" and in the "Program/script" field enter "PowerShell". In the "arguments" enter the path to your saved PowerShell script
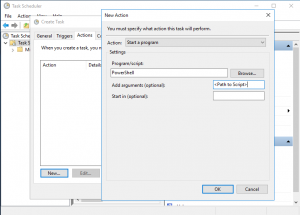
- Click "OK" to finish creating the task. To confirm, you can go to the "Task Scheduler Library" and you should see your task in the list -- it will execute at the time you chose when creating the task
- You can test the task by right-clicking on it and then choosing to "Run" it -- this will execute it now and you can then go and view your DEP devices in the Intune portal to confirm you have no unassigned DEP devices (if you still have unassigned DEP devices, this means the script did not execute successfully and you will need to determine why)
NOTE: To easily filter on devices that do not have a DEP profile assigned, follow the instructions on our docs site to do this directly in the Azure portal: /en-us/intune/device-enrollment-program-enroll-ios#assign-an-enrollment-profile-to-devices. By loading the "unassigned" filter, as an IT Pro you can see if even a single device in your environment is missing a profile.
What Else Can I Do with Graph API?
To learn more about the actions you can automate with Graph API, check out our Graph API samples on Github! You can find them all here: https://github.com/microsoftgraph/powershell-intune-samples
In this blog post, we used two of the sample scripts from GitHub. You can find both of them individually at these locations:
Authentication: https://github.com/microsoftgraph/powershell-intune-samples/tree/master/Authentication
Apple Enrollment: https://github.com/microsoftgraph/powershell-intune-samples/tree/master/AppleEnrollment
We hope this post helps you and leave us comments if you have questions or feedback!
-Sarah and Josh