MFA: Don’t worry, your phone number won’t be published!
What happens if your identity is stolen and an attacker uses those credentials (username/password), to login to your business application or email? What if you are a domain administrator in Active Directory or a Global Administrator in Office 365? They have keys to the kingdom, access to sensitive intellectual property, and can do some real damage.
One of the best ways to safeguard against this, is to enable Multi-Factor Authentication (MFA) on user accounts. As a result, when I login to the application, I will be prompted for a second factor of authentication to validate my identity (and prove I am, who I say I am). This can be an SMS message sent to my mobile, a phone call, a verification code, a key fob, (and my favorite) a push notification to the app on my phone and authenticate using biometrics or my smartwatch to authenticate (see this article for full list of methods supported). This way, if my identity is compromised, it's another layer of protection in-place to help prevent the attacker from using the stolen credentials.
As a user, if I choose to have an SMS message sent to my smartphone for MFA, this requires me to register my mobile phone number with Azure Active Directory (Office 365). A common misperception with end-users is this number can be seen in the Global Address List (GAL) to all employees in the organization. This is not true. Using the "Authentication Phone" field, does not publish the phone number in the GAL and keeps it hidden. Moreover, the only way for a mobile phone number to appear in the GAL is either to manually populate it or during a sync from on-premises Active Directory.
How does this work?
When I setup MFA for the first time on a user's account (as an admin), or on my own account, I am prompted with options on my preferred method for multi-factor authentication. I then choose "Text code to my authentication phone" and type my mobile phone number in the field for "Authentication Phone" (as shown below).
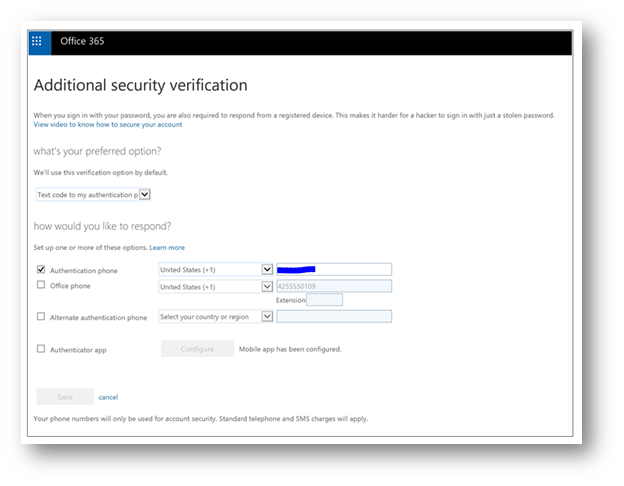
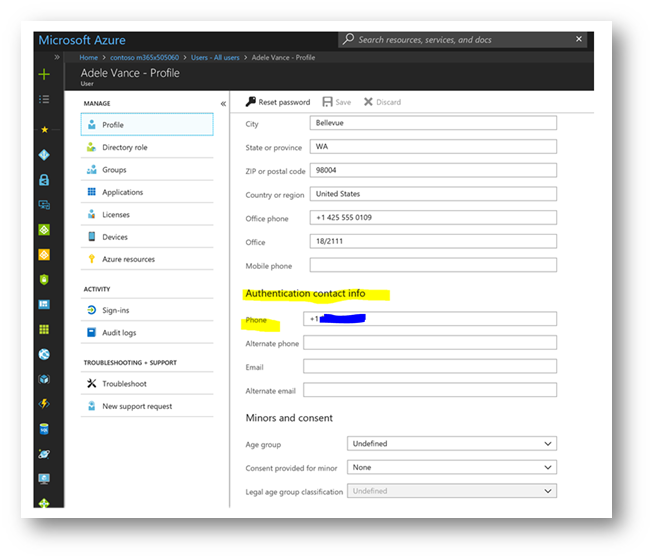
When I click save, the phone number in the "Authentication Phone" field, will be written to the user object in Azure Active Directory as seen below (note the mobile phone field is blank):
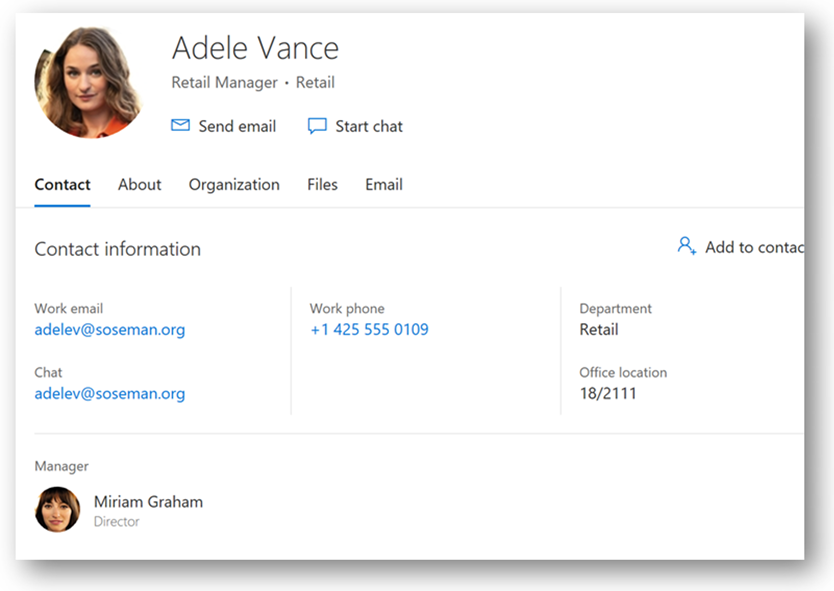
As a result, when I lookup Adele (the user account) in the Global Address List in Office 365 – the mobile phone number field is not populated, and the Authentication Phone number is not displayed on the contact card:
Can the user update this field themselves?
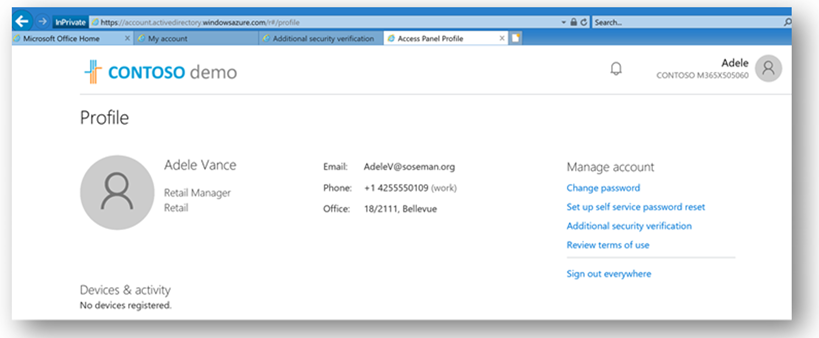
Yes, I'm glad you asked! Browsing to https://myapps.microsoft.com and clicking on my profile in the upper right corner and selecting "Additional Security Verification" will take me to the first screenshot above that allows me to specify my preferences.
Conclusion:
MFA is awesome, and if rolled out correctly with the right level of training and adoption, it can truly be frictionless. However, this is a must to help protect against identity-based attacks such as phishing email campaigns.
Enjoy!
--Matt Soseman
Comments
- Anonymous
May 13, 2019
Thank you for the useful information, is there a way to update the authentication phone number for a bulk of users by an administrator ?