Govern, Audit and Control G Suite with Microsoft! (Google Apps + Cloud App Security)
Does your organization use G Suite or Google Apps? Do you have these requirements?
- Audit activity occurring in G Suite (user logons/logoffs, settings changed, files modified, etc)
- Audit file activity? (what files are being accessed, from where, how they are being accessed, etc)
- Govern how G Suite is accessed? (Only from a managed device? Only from a managed network? Don't allow download from a non-managed computer?)
- Scan files in G Suite for sensitive data?
- And more!
In this blog we will explore how Microsoft Cloud App Security (CAS) part of Microsoft 365, can help you meet these requirements. For more information on connecting G Suite to CAS see this article. Let's get started!
Note: Microsoft nor Matt Soseman nor this blog assumes no responsibilities and offers no warranties as a result of following the instructions in this blog. This requires enabling and modifying APIs. Use at your own risk.
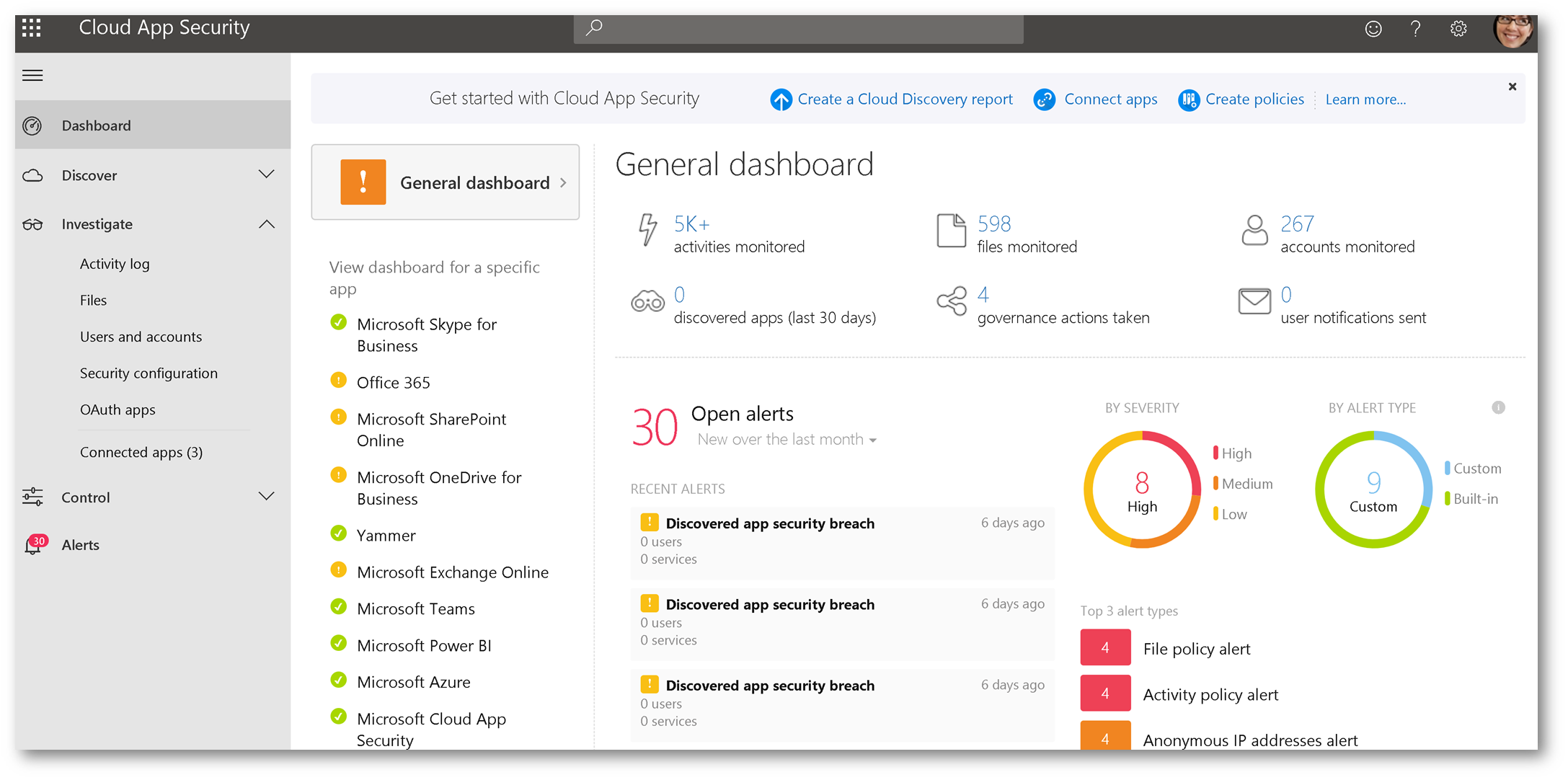
Configure G Suite within Microsoft Cloud App Security:
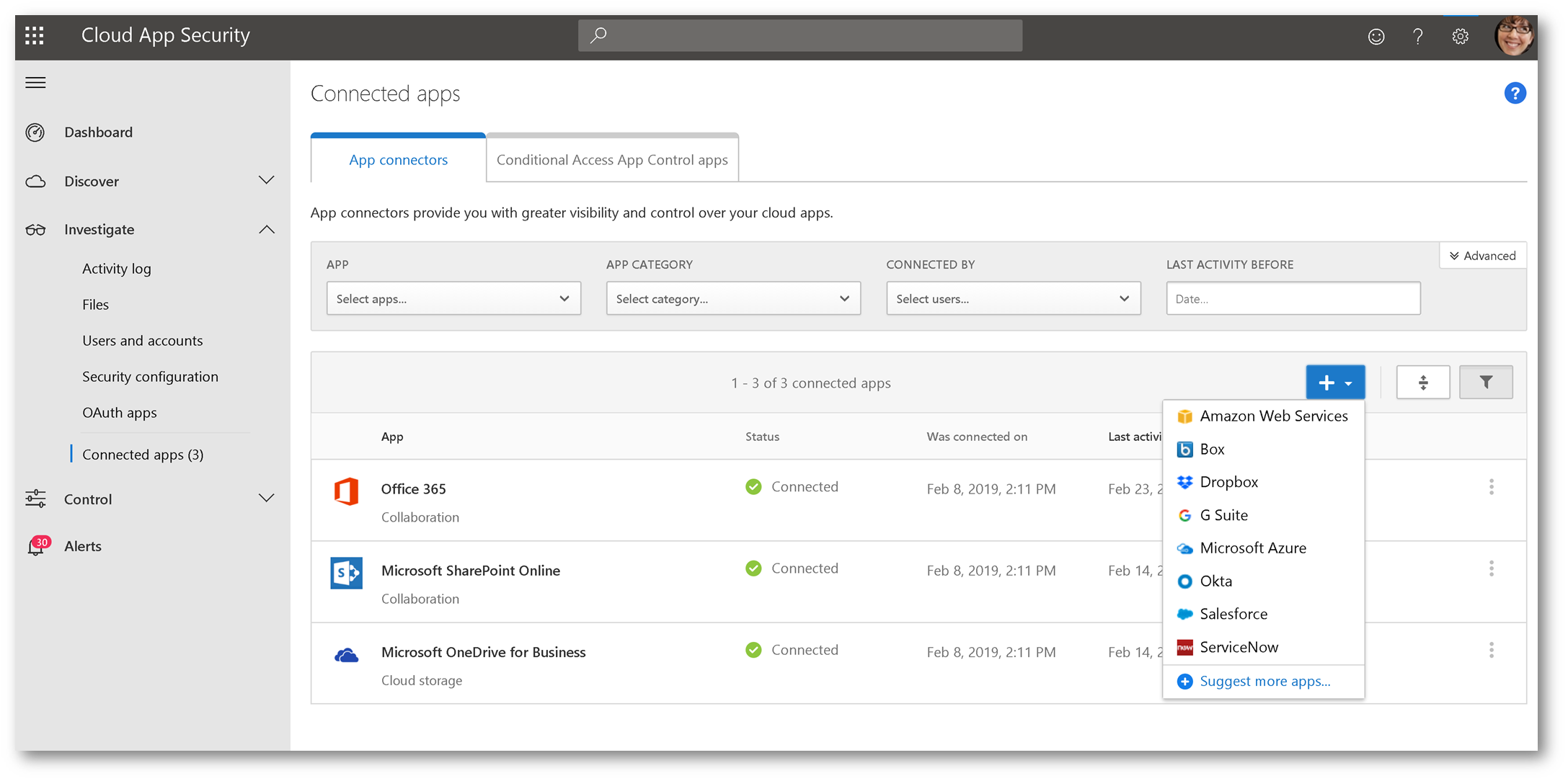
From within Cloud App Security, click Investigate then select Connected Apps:
Click the + sign and select G Suite:
Type in a name and click Connect G Suite:

We need to pull the appropriate details from G Suite. Open a new browser instance and navigate to your G Suite admin portal using your admin credentials:
 Once signed in, navigate to https://cloud.google.com/console/projectand click Create Project:
Once signed in, navigate to https://cloud.google.com/console/projectand click Create Project:
Give the project a name and click Create Project

Click Google Cloud Platform then click Go To APIs Overview:
Click API Library and enable the following APIs:
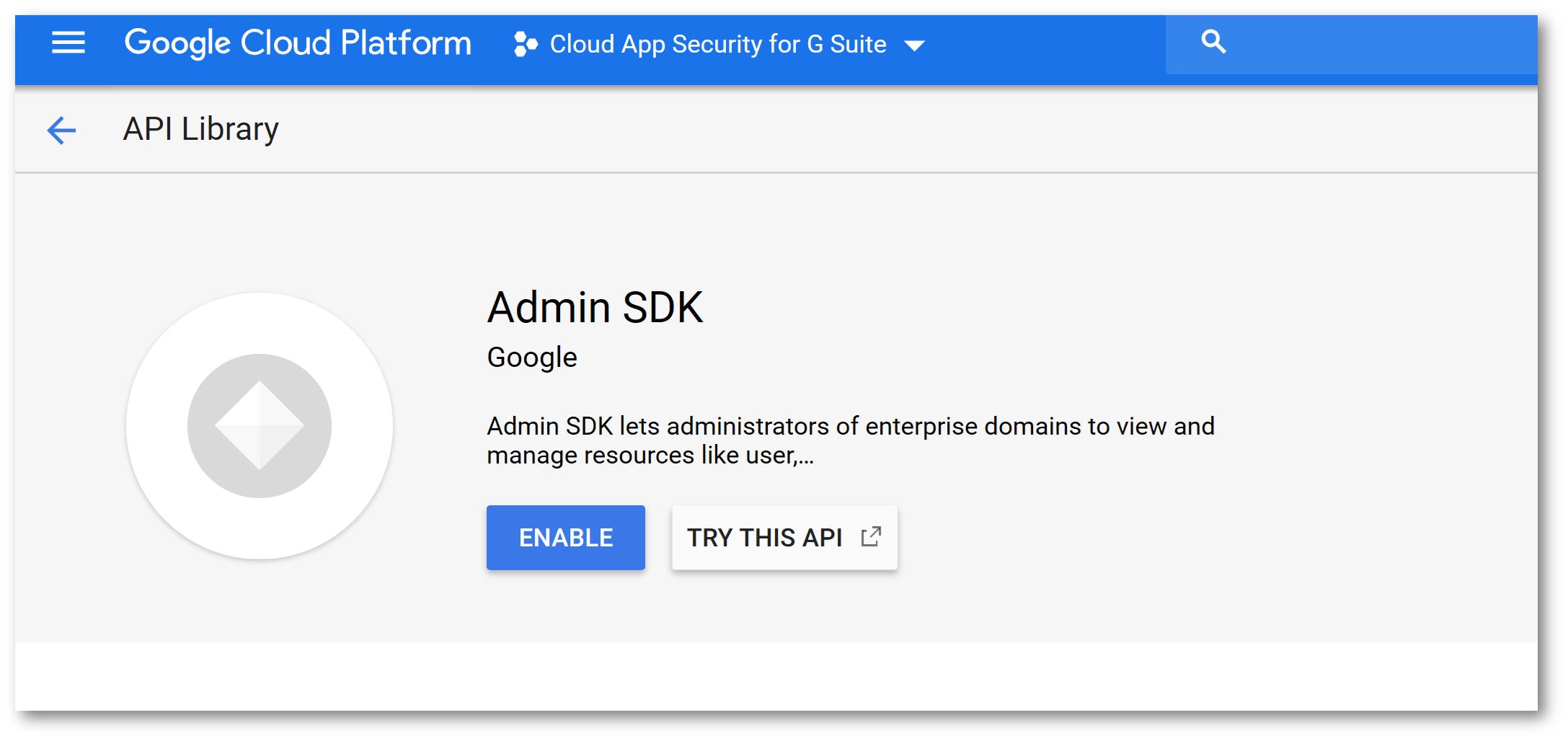
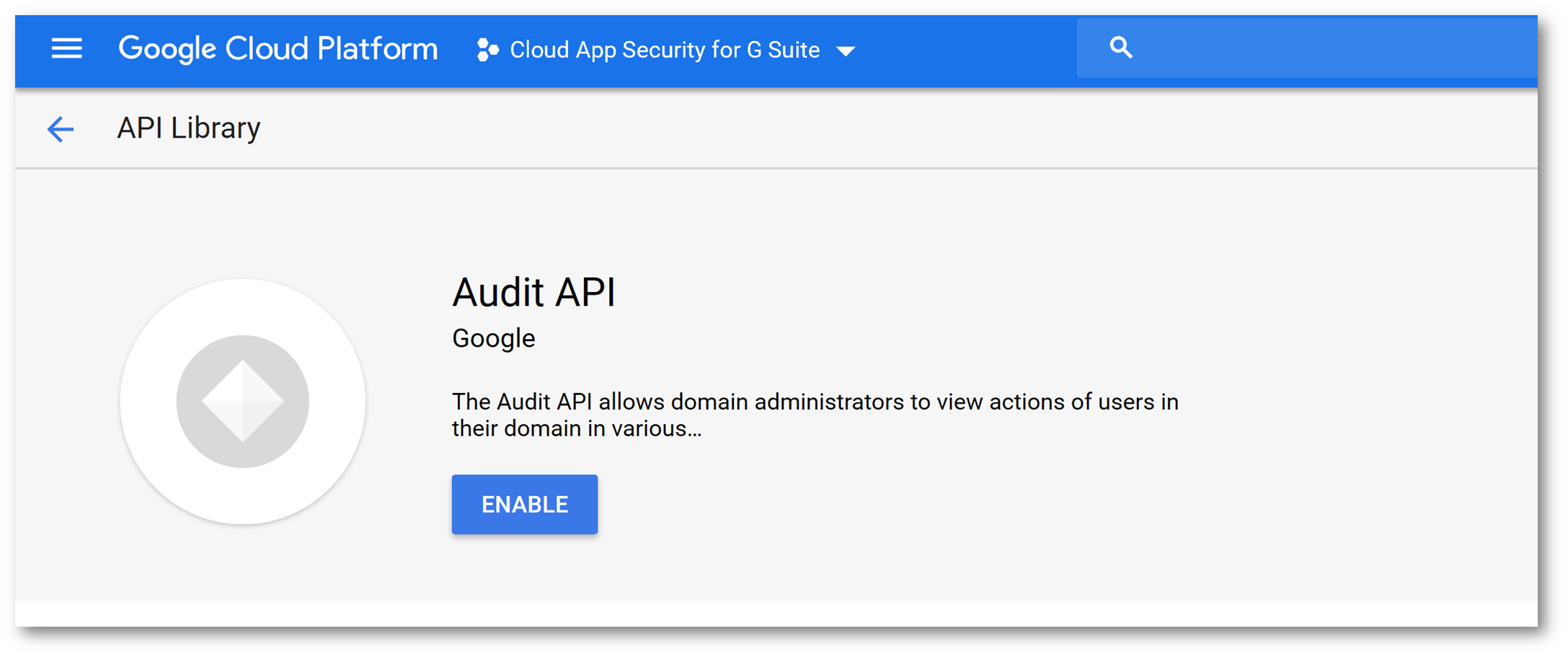
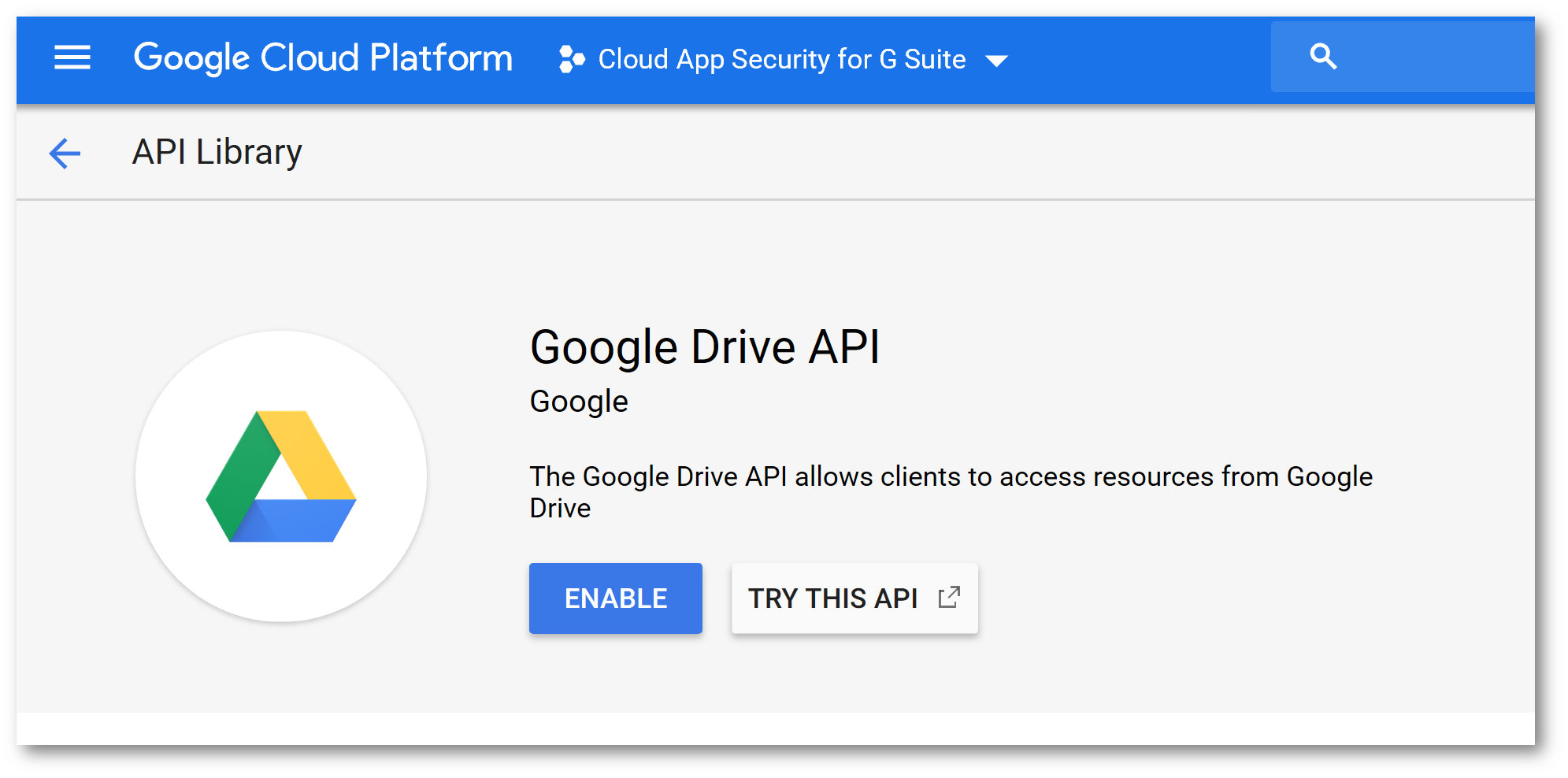
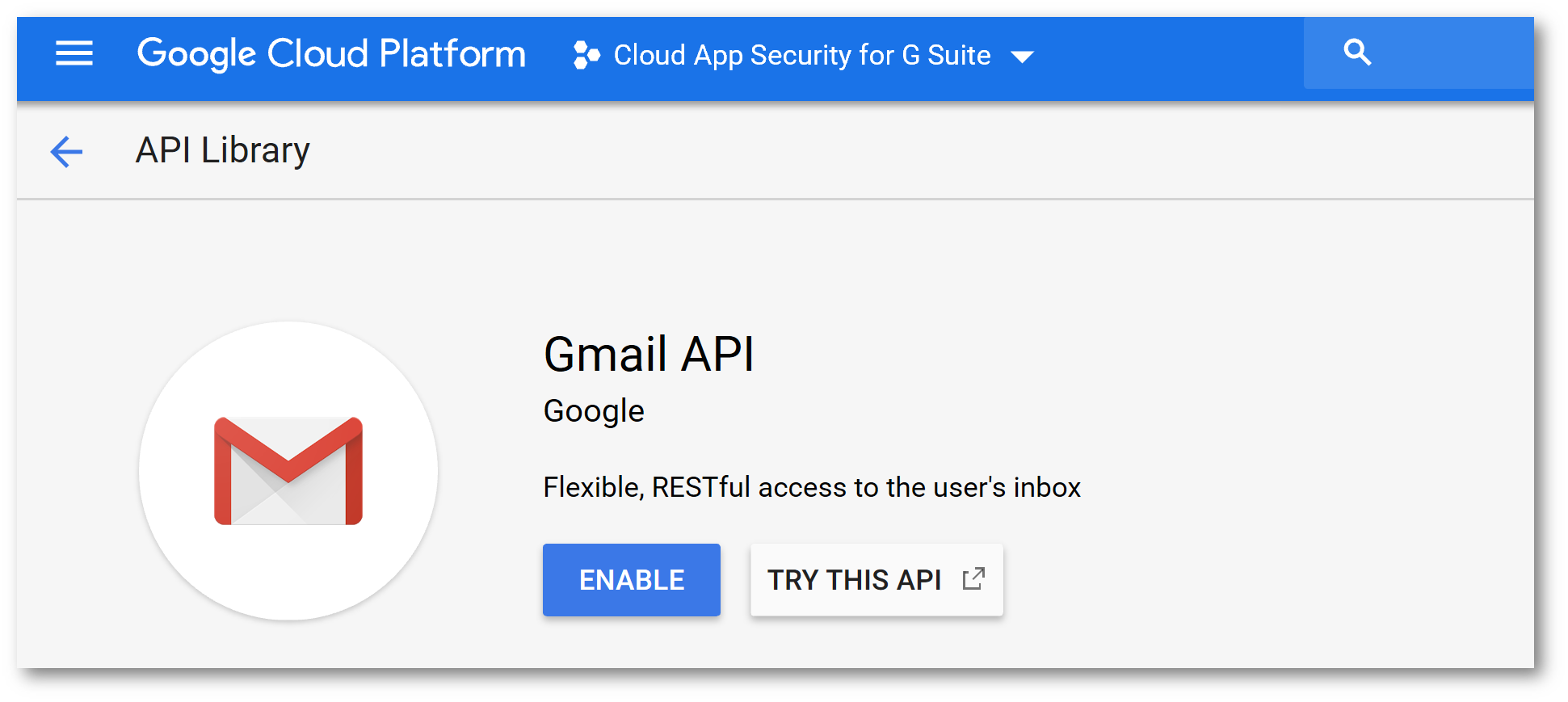
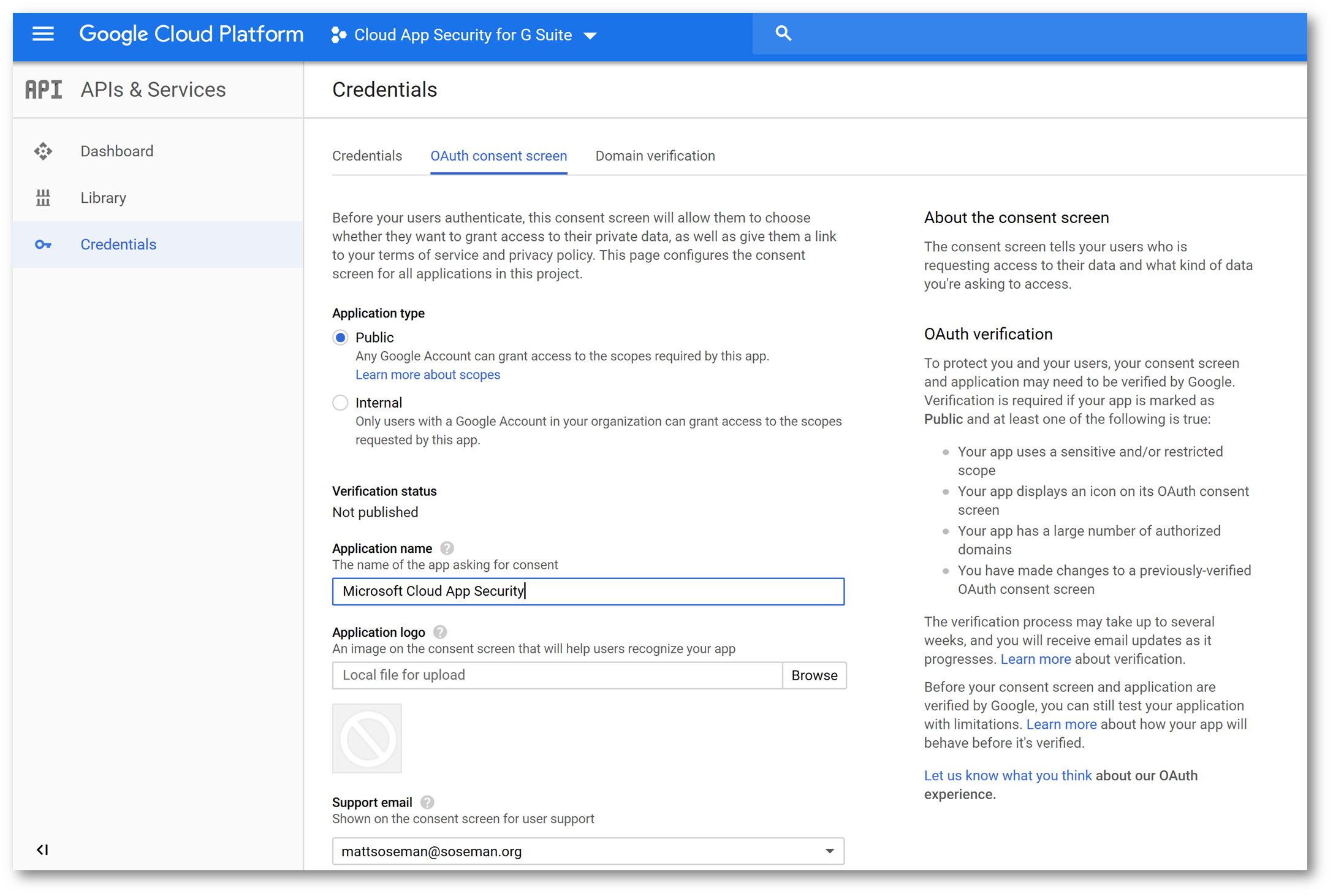
Back on the APIs and Services screen, click Credentials click the OAuth Consent Screen then in Application Name type Microsoft Cloud App Security and click Save:
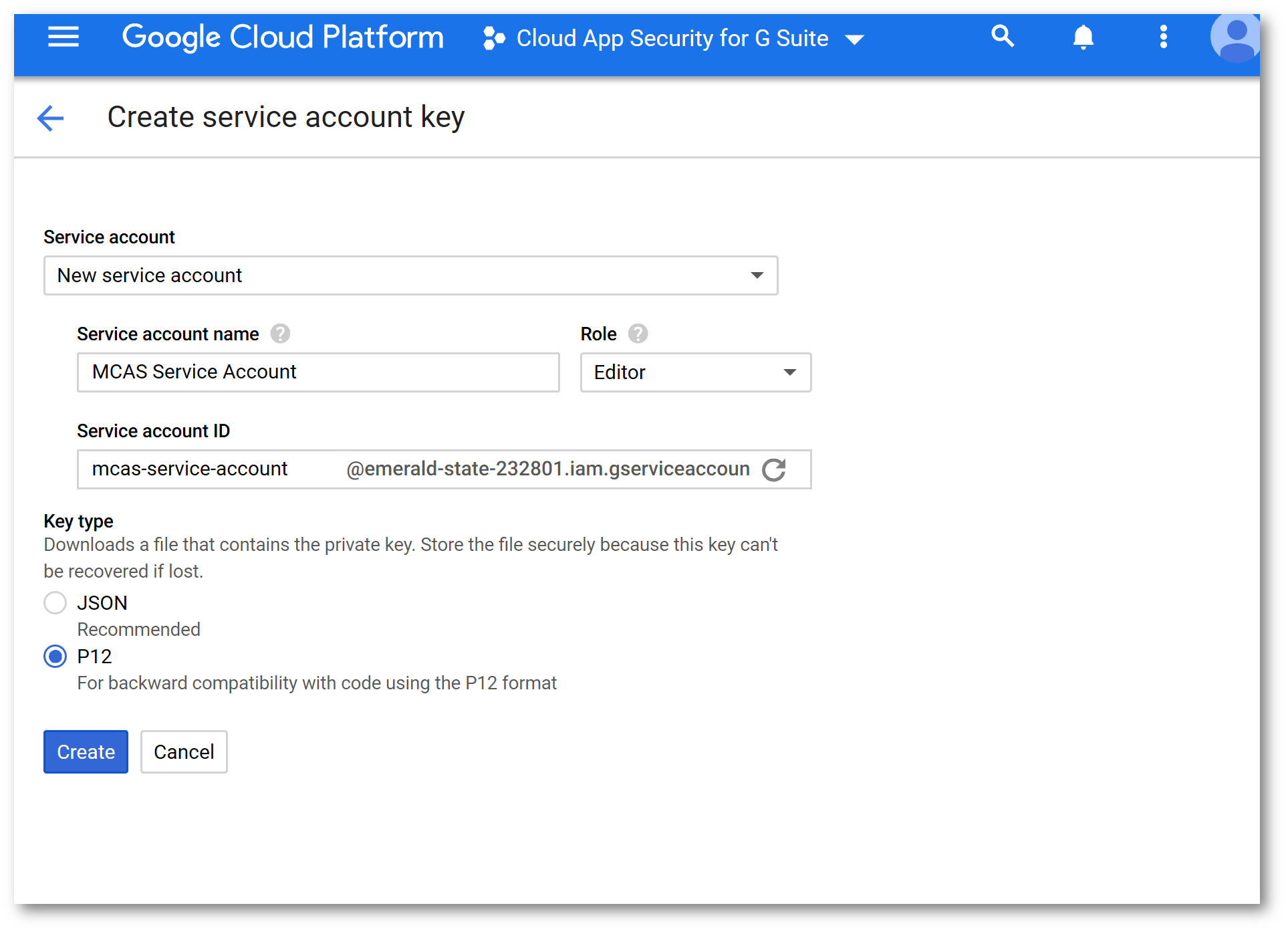
Back on the Credentials tab click Create Credentials and select Service Account Key:

Configure the Service Account Key and click Create. Copy the secret to a scratchpad area. Download the certificate.
Back on the Credentials screen click Manage Service Accounts

Edit the Service Account:
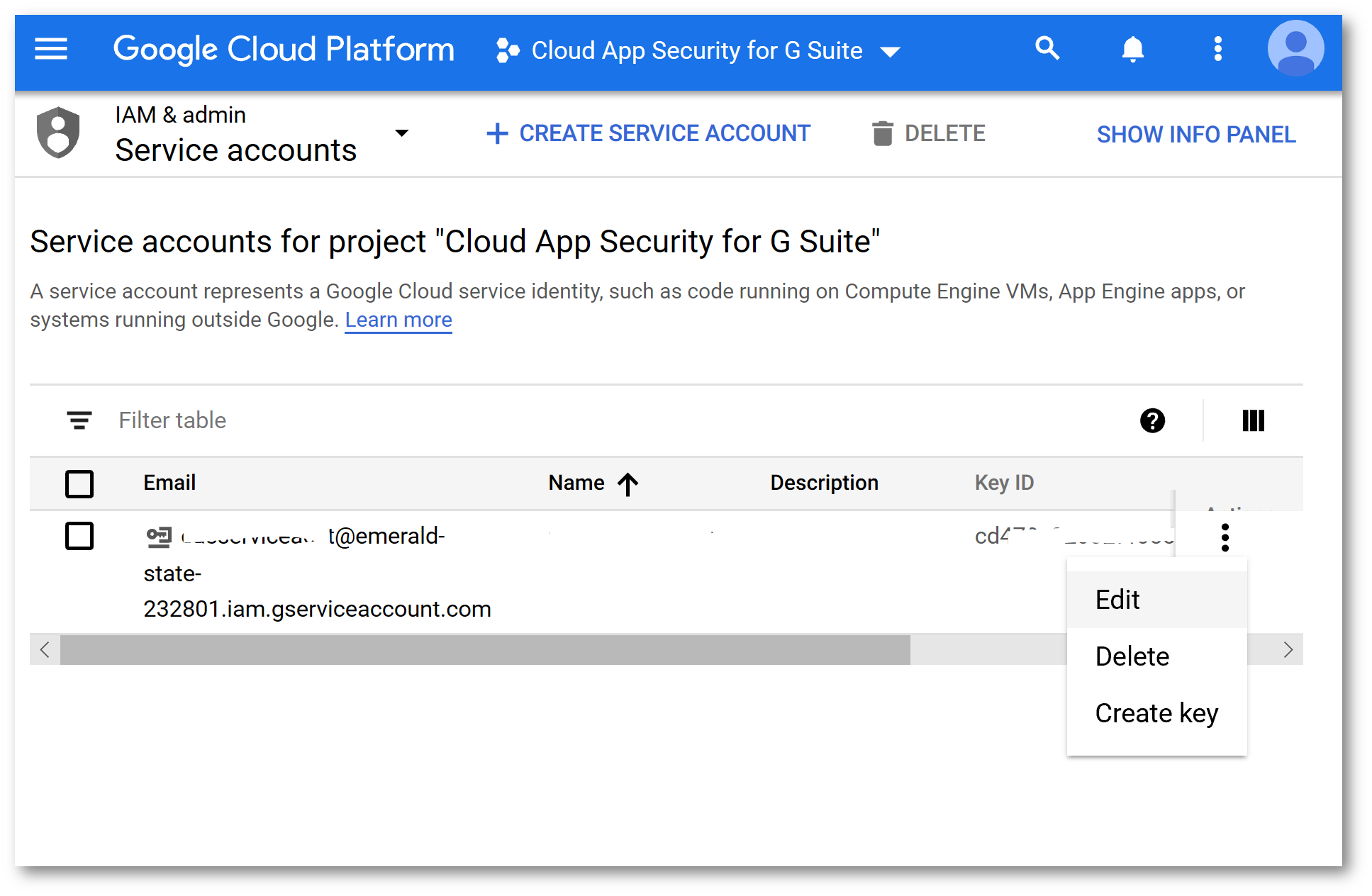
Check the box next to Enable G Suite Domain Wide Delegation and click Save:
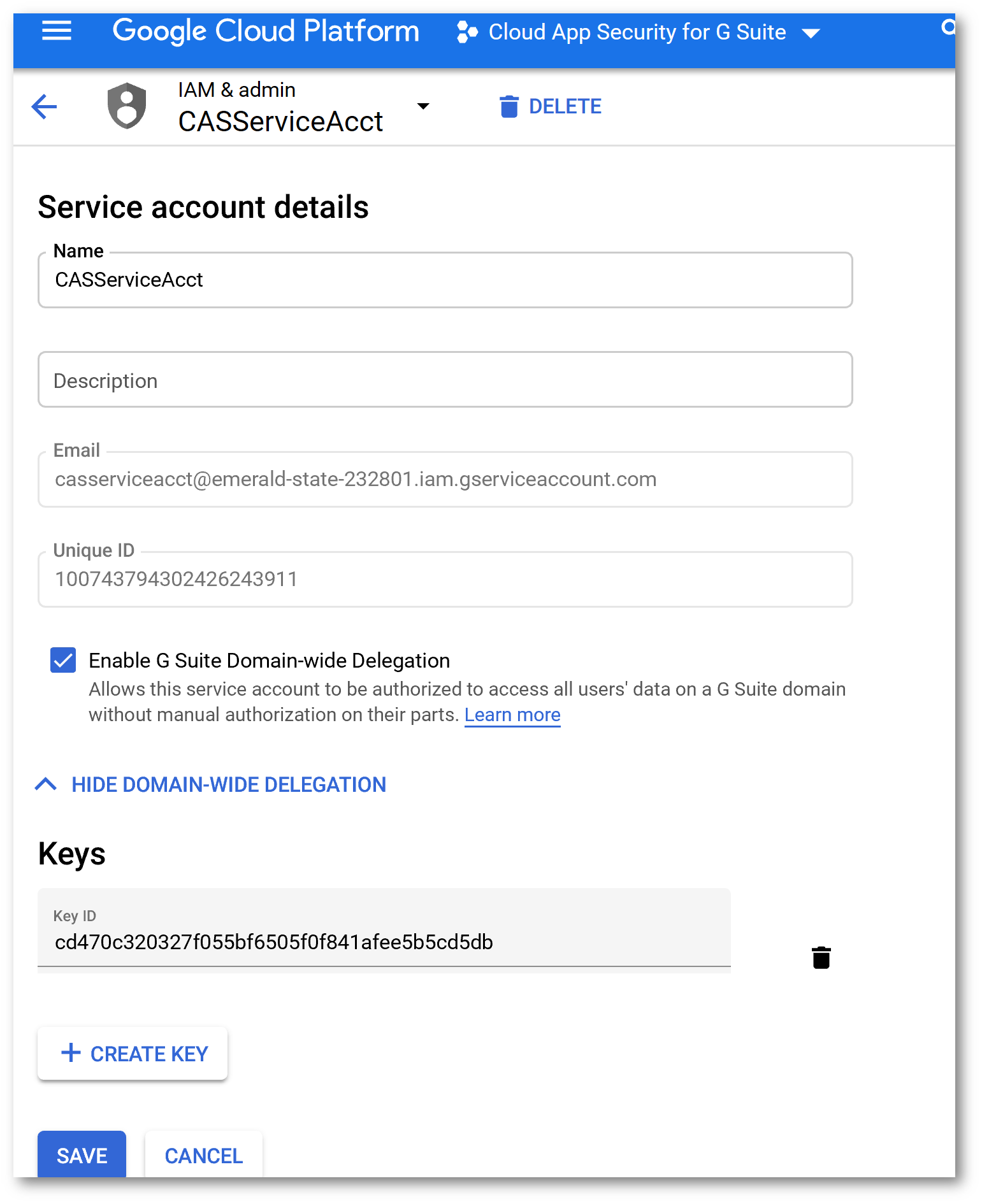
In the search box at the top type Google Drive API and press Enter
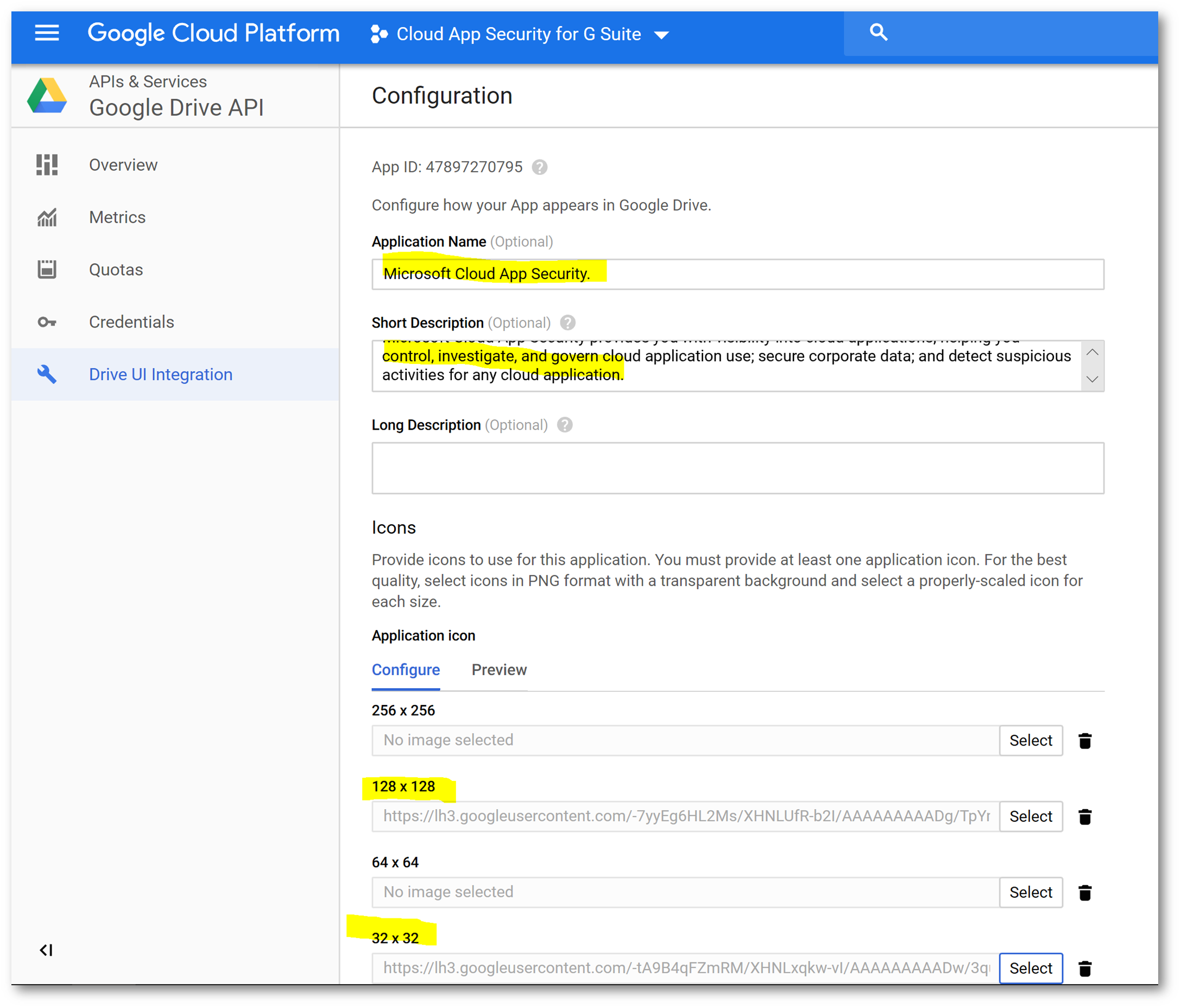
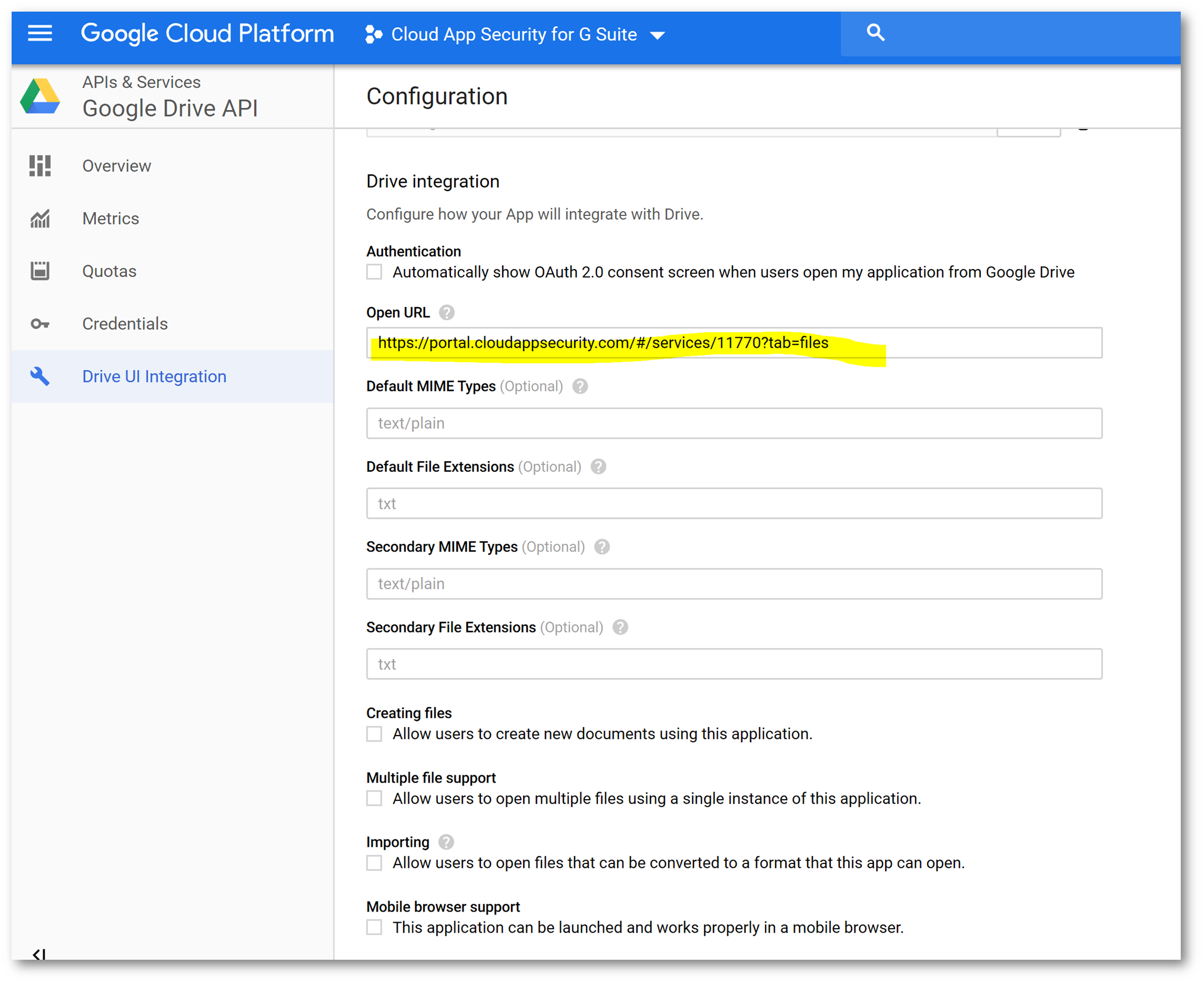
Click on Drive UI Integration, and configure using the following parameters (you can get the icons from here) and click Save Changes when finished:
In the search box type G Suite Marketplace
SDK and press Enter
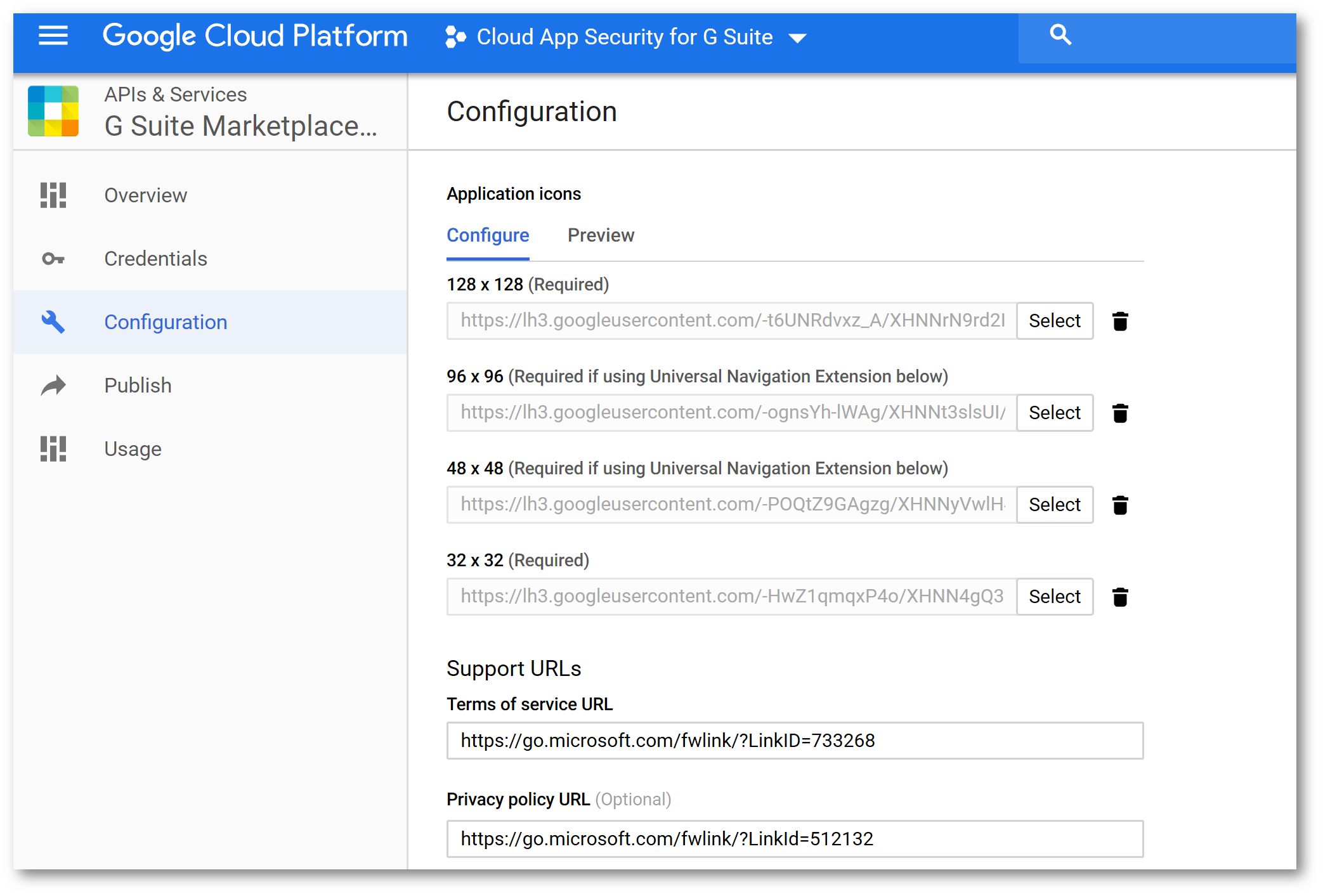
On the Configuration tab, copy the Project Number to a scratch pad area :

Upload the same icons you used previously, and configure the following URLs:
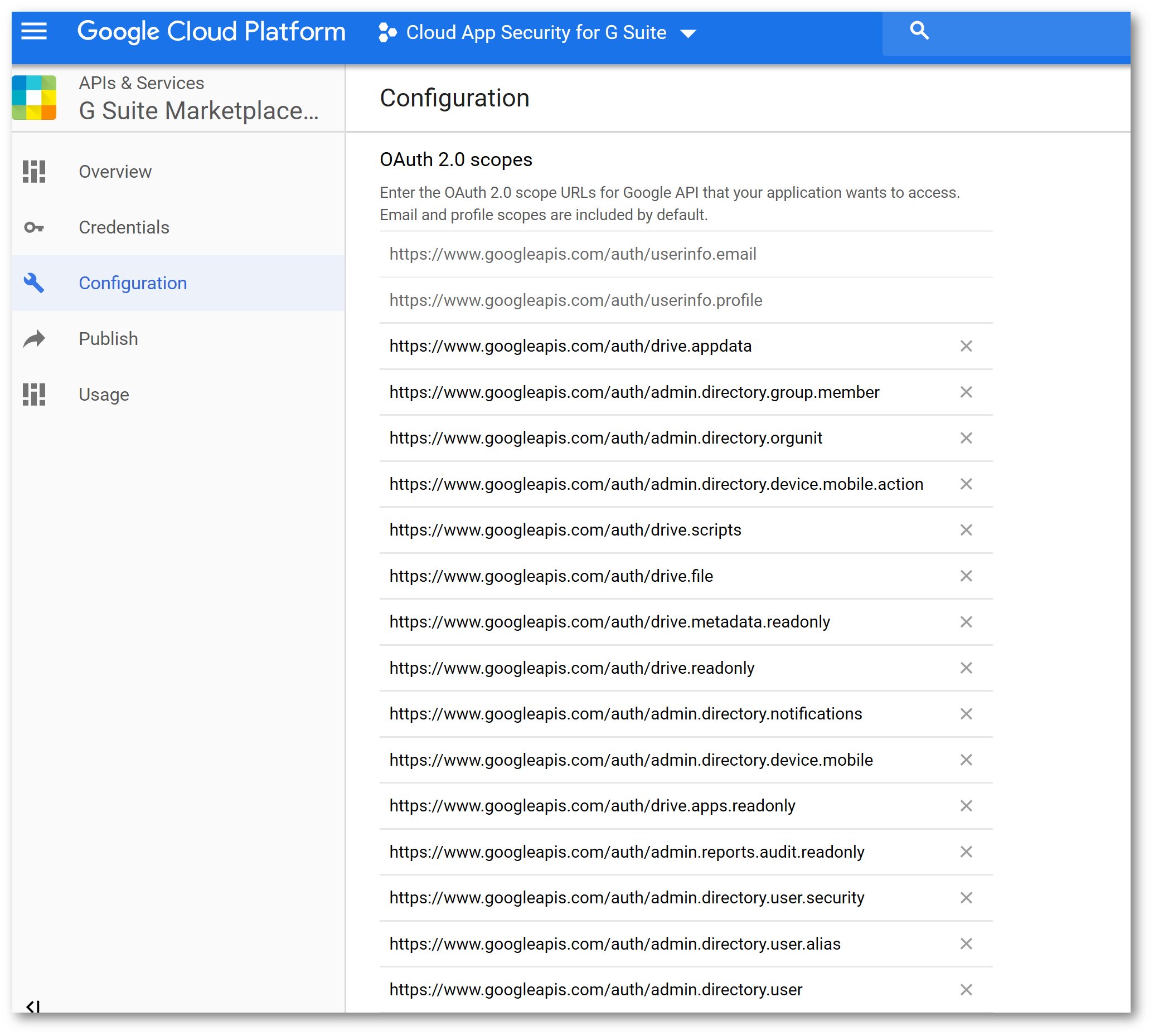
Configure the following URL scopes:
https://www.googleapis.com/auth/admin.reports.audit.readonly
https://www.googleapis.com/auth/admin.reports.usage.readonly
https://www.googleapis.com/auth/drive
https://www.googleapis.com/auth/drive.appdata
https://www.googleapis.com/auth/drive.apps.readonly
https://www.googleapis.com/auth/drive.file
https://www.googleapis.com/auth/drive.metadata.readonly
https://www.googleapis.com/auth/drive.readonly
https://www.googleapis.com/auth/drive.scripts
https://www.googleapis.com/auth/admin.directory.user.readonly
https://www.googleapis.com/auth/admin.directory.user.security
https://www.googleapis.com/auth/admin.directory.user.alias
https://www.googleapis.com/auth/admin.directory.orgunit
https://www.googleapis.com/auth/admin.directory.notifications
https://www.googleapis.com/auth/admin.directory.group.member
https://www.googleapis.com/auth/admin.directory.group
https://www.googleapis.com/auth/admin.directory.device.mobile.action
https://www.googleapis.com/auth/admin.directory.device.mobile
https://www.googleapis.com/auth/admin.directory.user
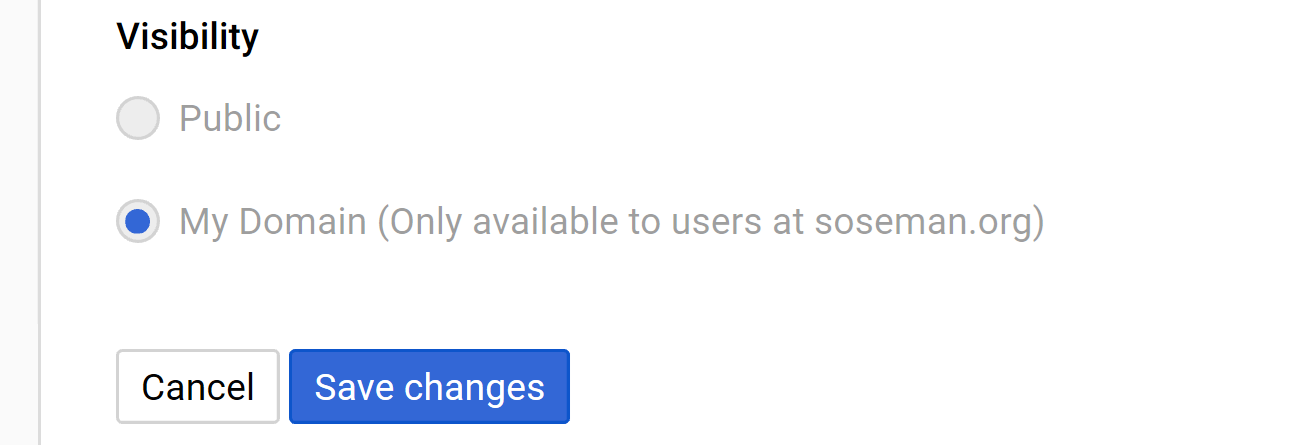
Under Visibility select My Domain and click Save Changes:
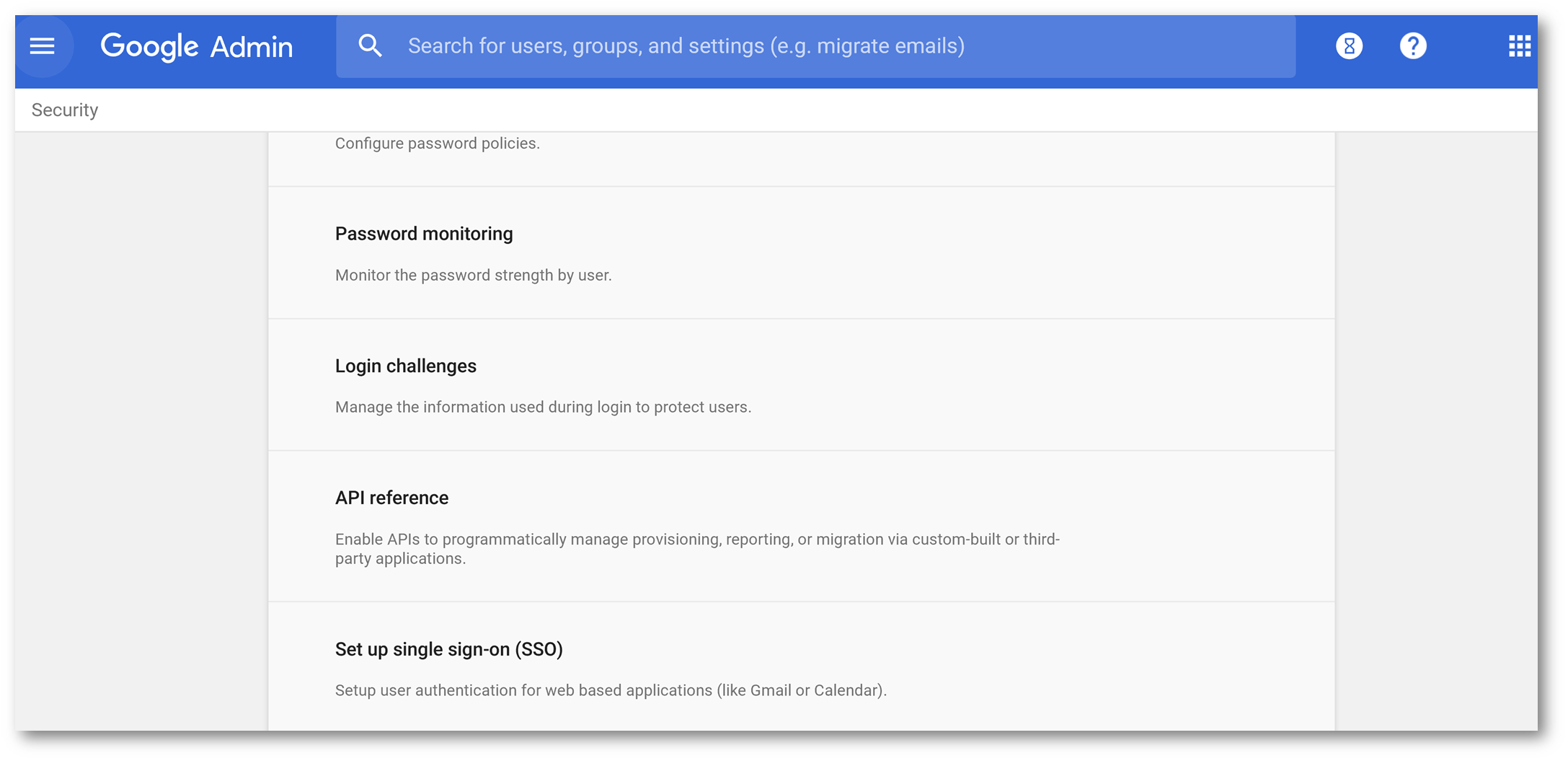
Browse back to admin.google.com and click on Security

Select API Reference:
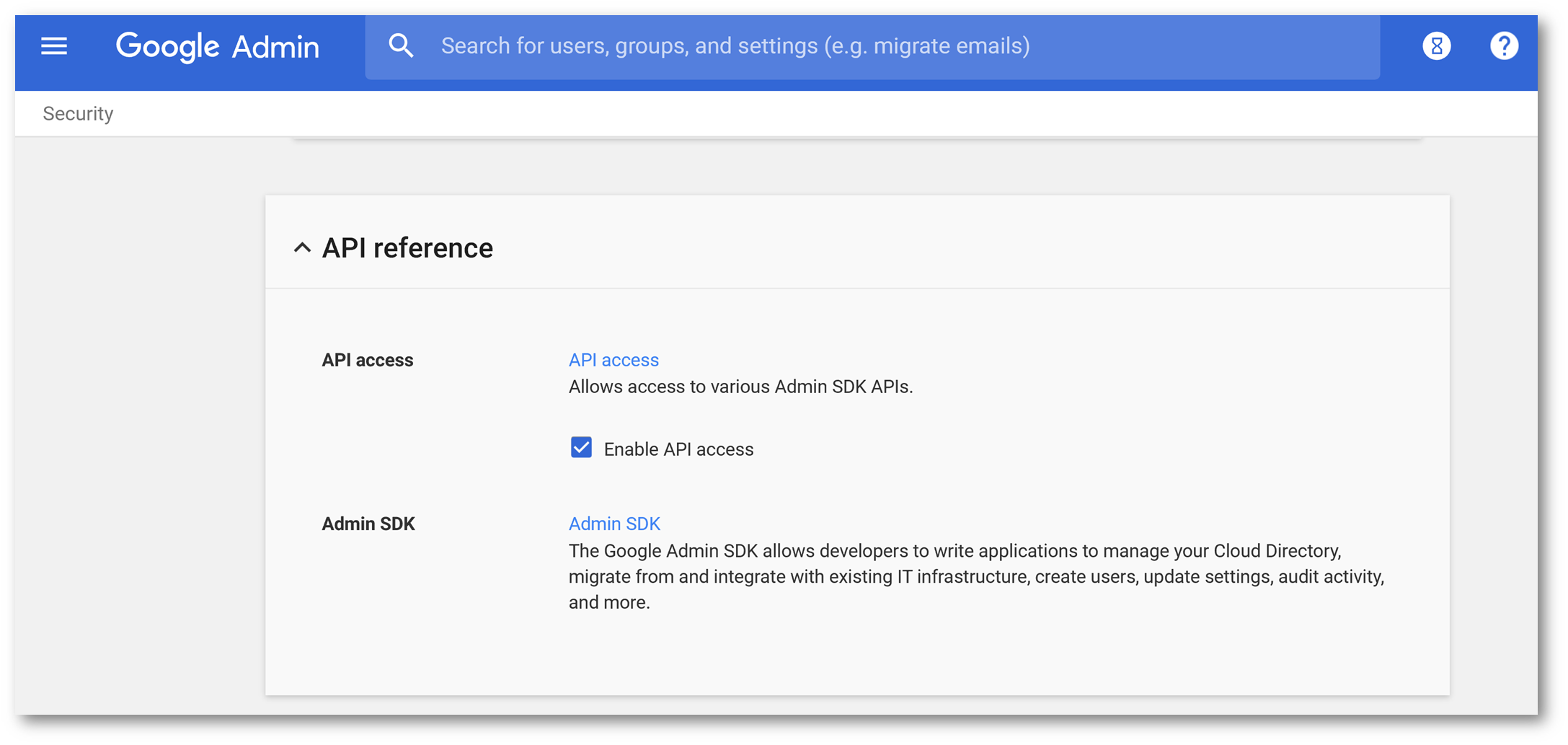
Click Enable API Access and then click Save Changes
Finalize Cloud App Security Configuration:
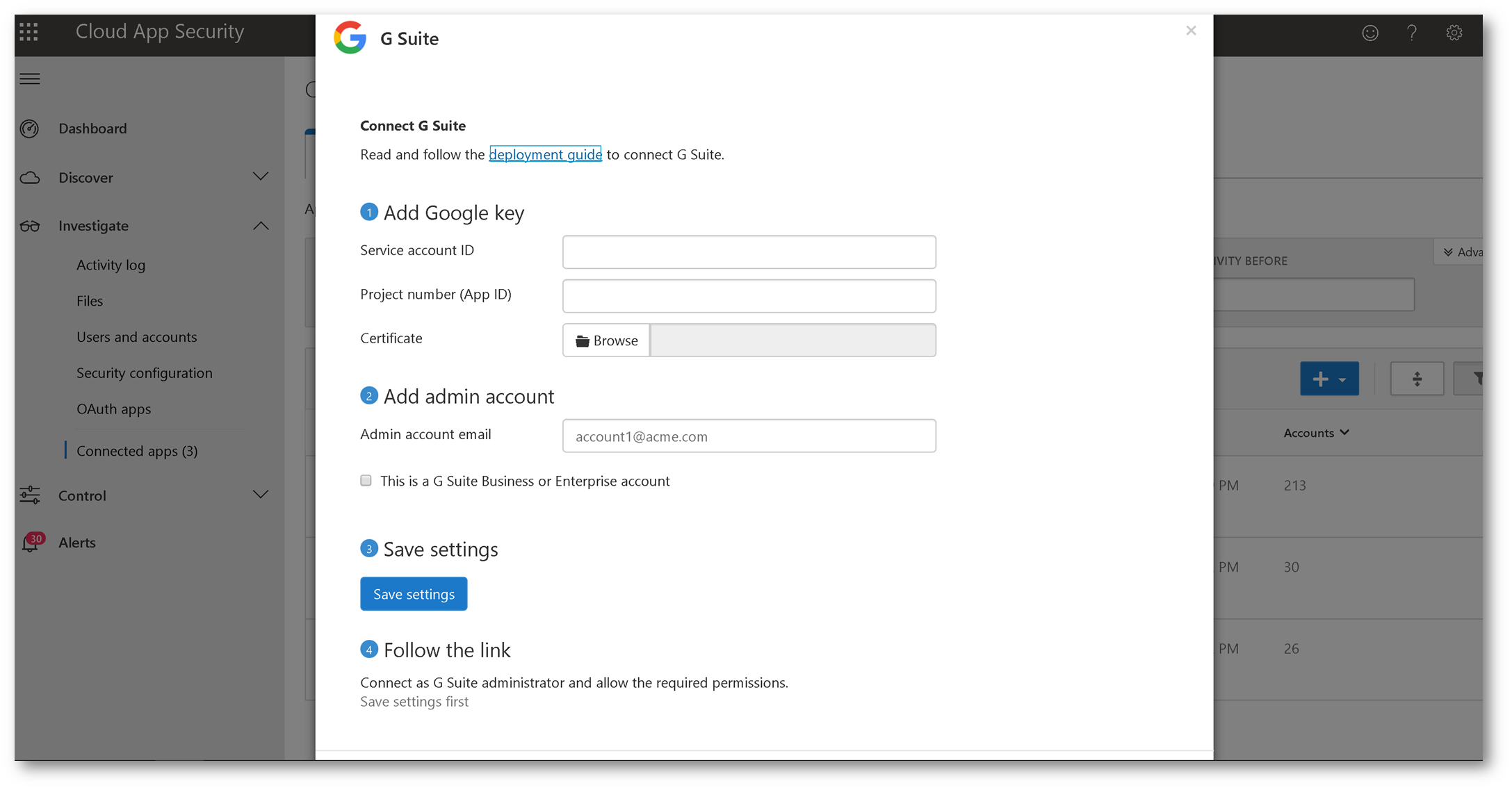
Back on the Cloud App Security portal, fill in the fields using the information you configured from the G Suite tenant:
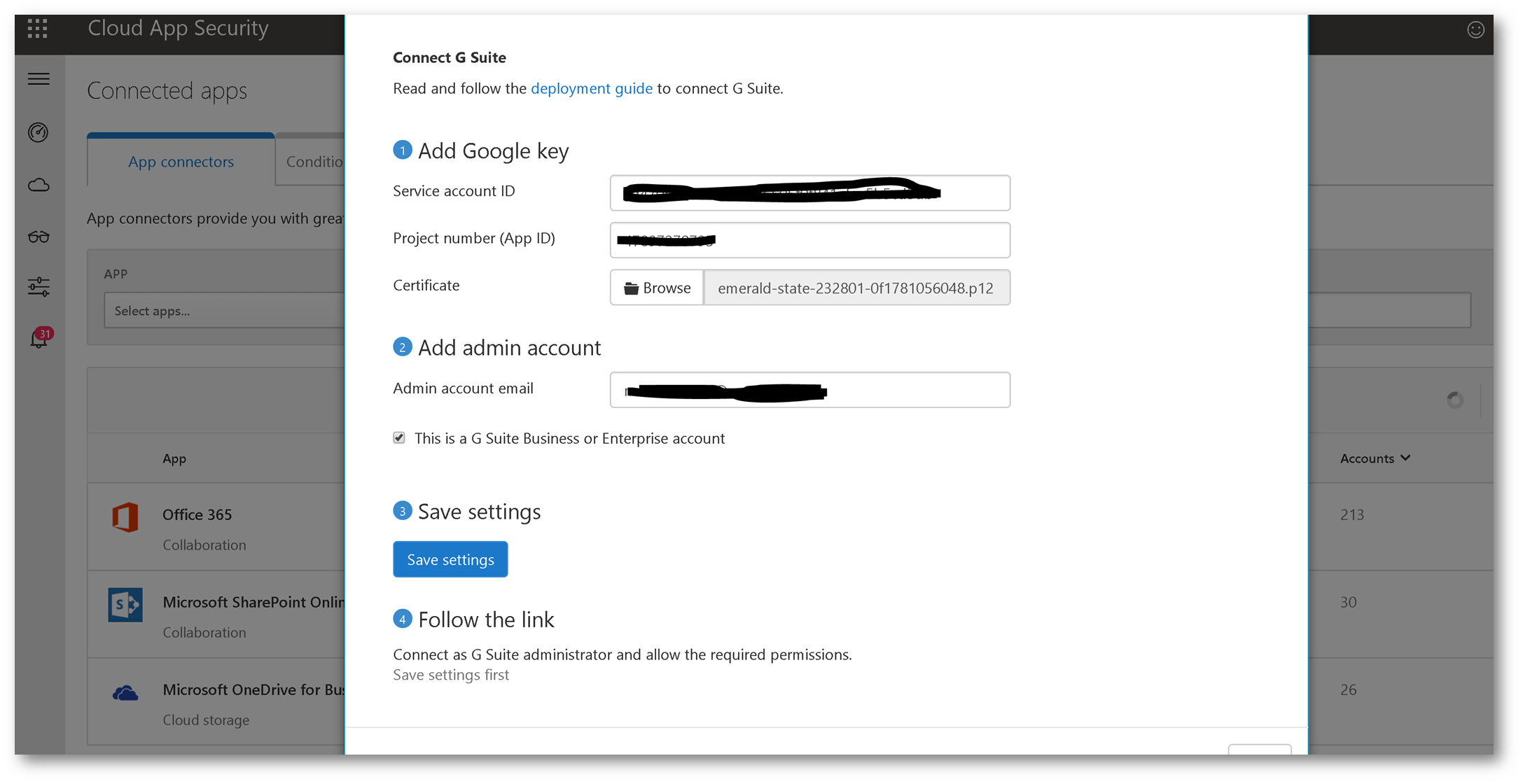
Once you save the settings click follow this link
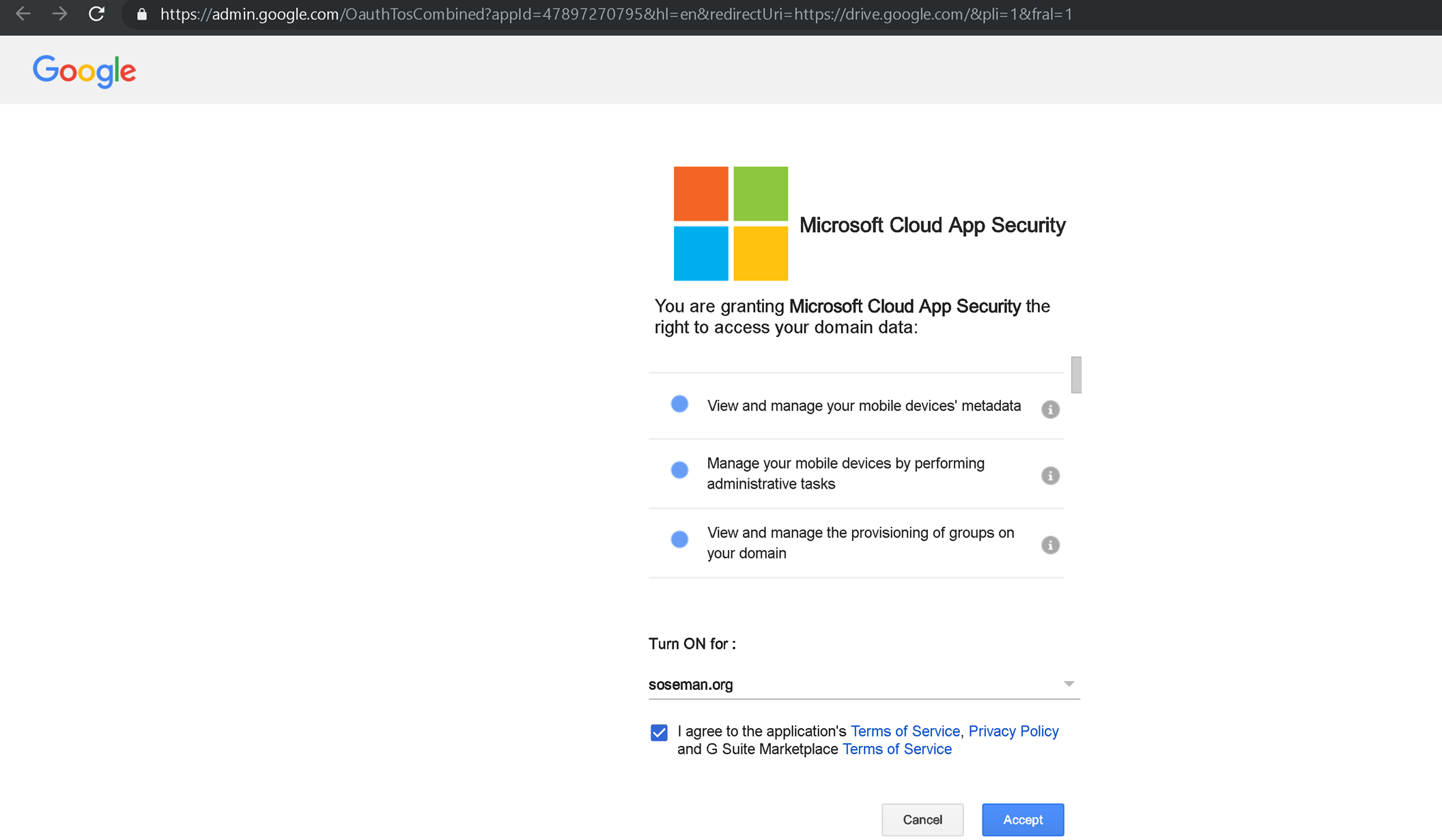
On the next screen, turn on the API and click Accept:
Once connected you should see:
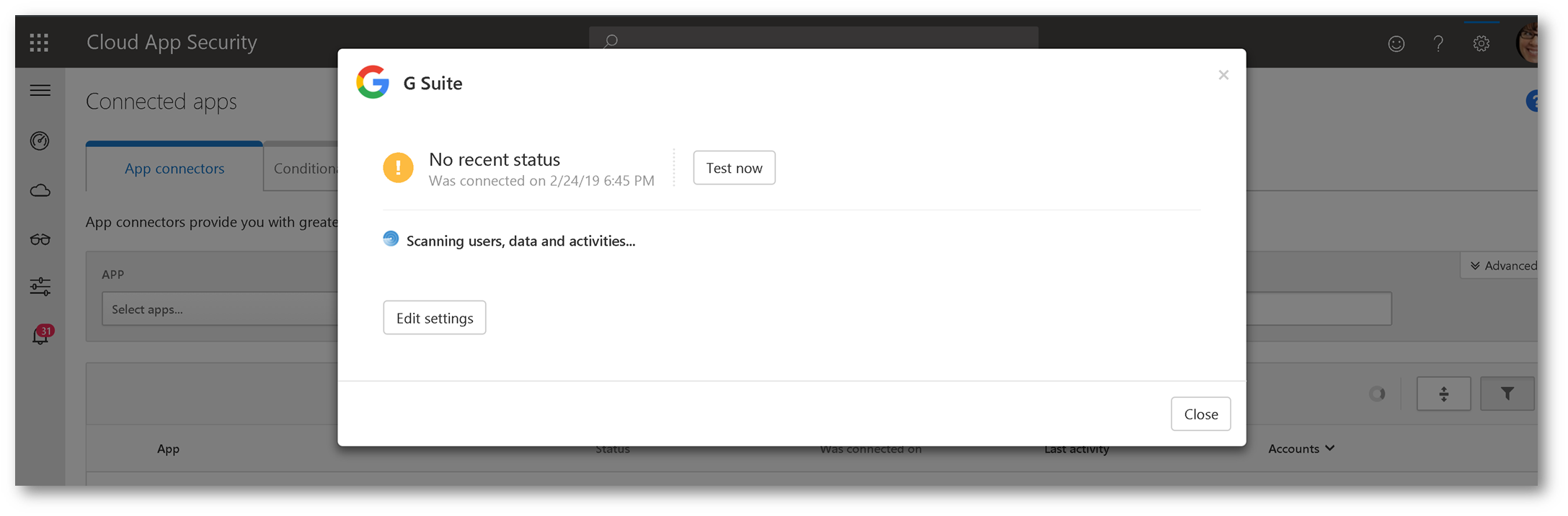
IMPORTANT: I have seen where it can take several hours upon initial connection for data to be populated in Microsoft Cloud App Security. You may want to let this run overnight.
Let's test it!
Once the connection is configured between Microsoft Cloud App Security (CAS) and G Suite, it's time to test. Generate some activity by logging into G Suite, accessing files, making setting changes, etc. Then, within CAS, navigate to Investigate -> Activity Log. Then change your app filter to G Suite. Notice the activity in G Suite!

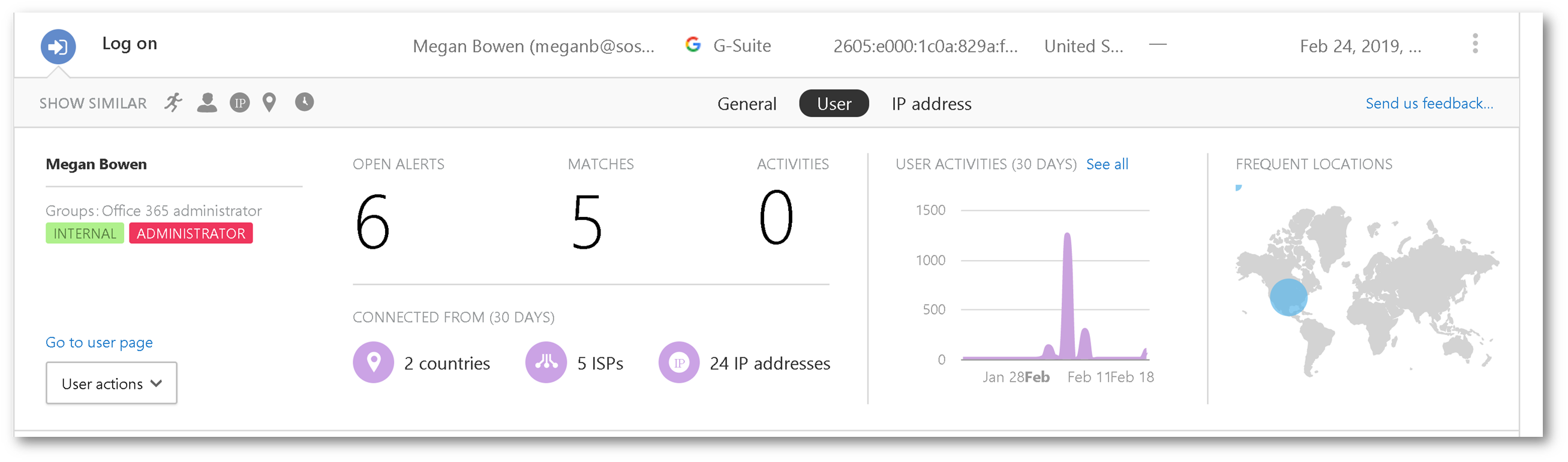
Expanding one of the activity entries, gives you additional context and telemetry:
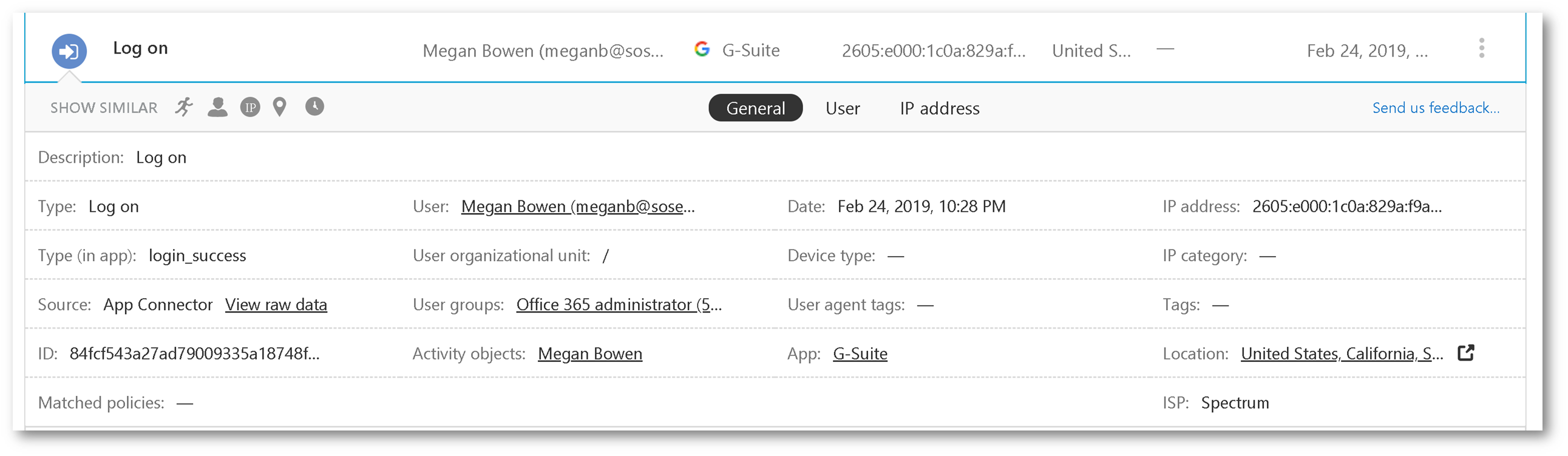
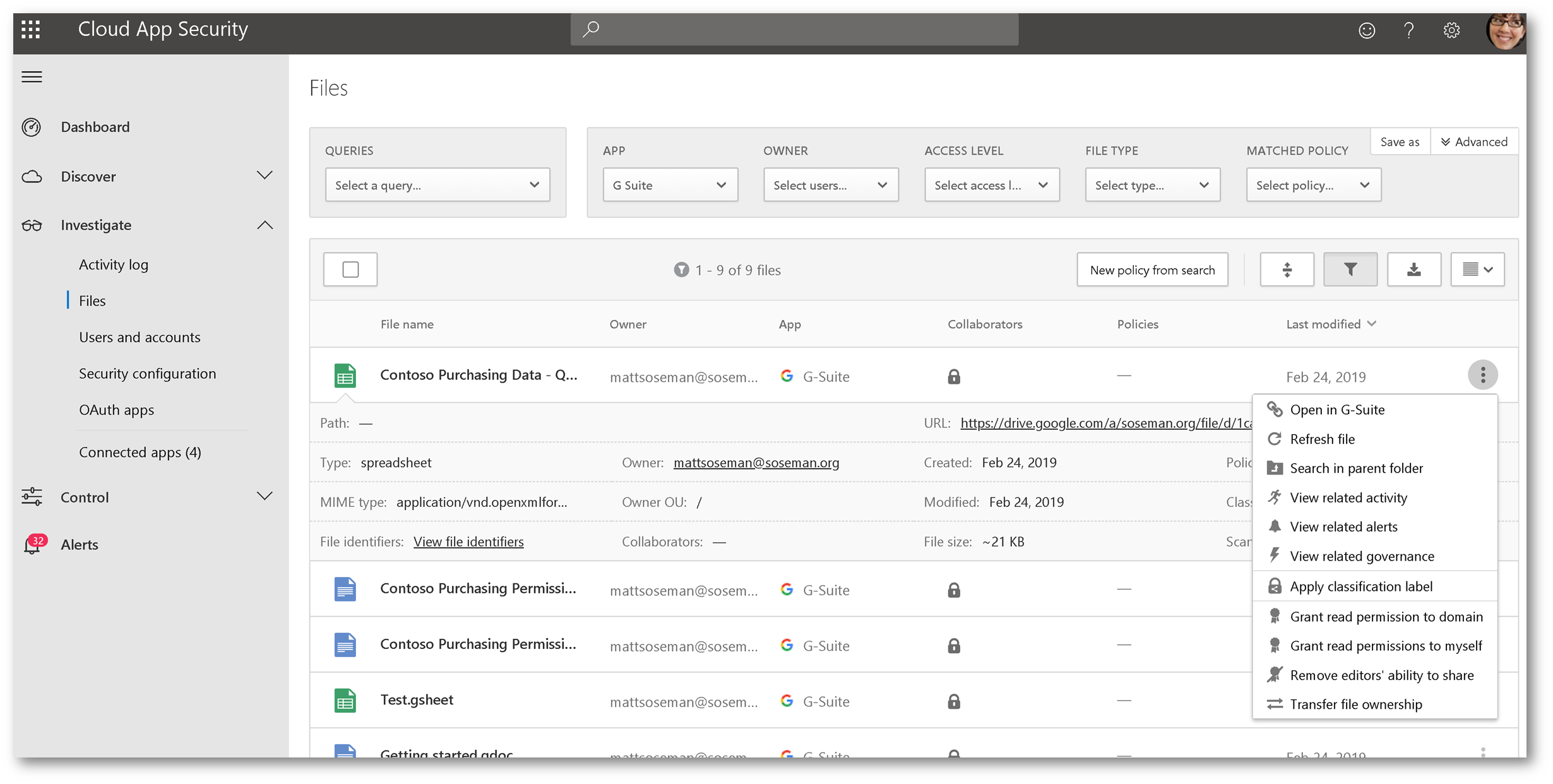
Browsing to Investigate -> Files then changing your app filter to G Suite allows you to see file activity in G Suite:
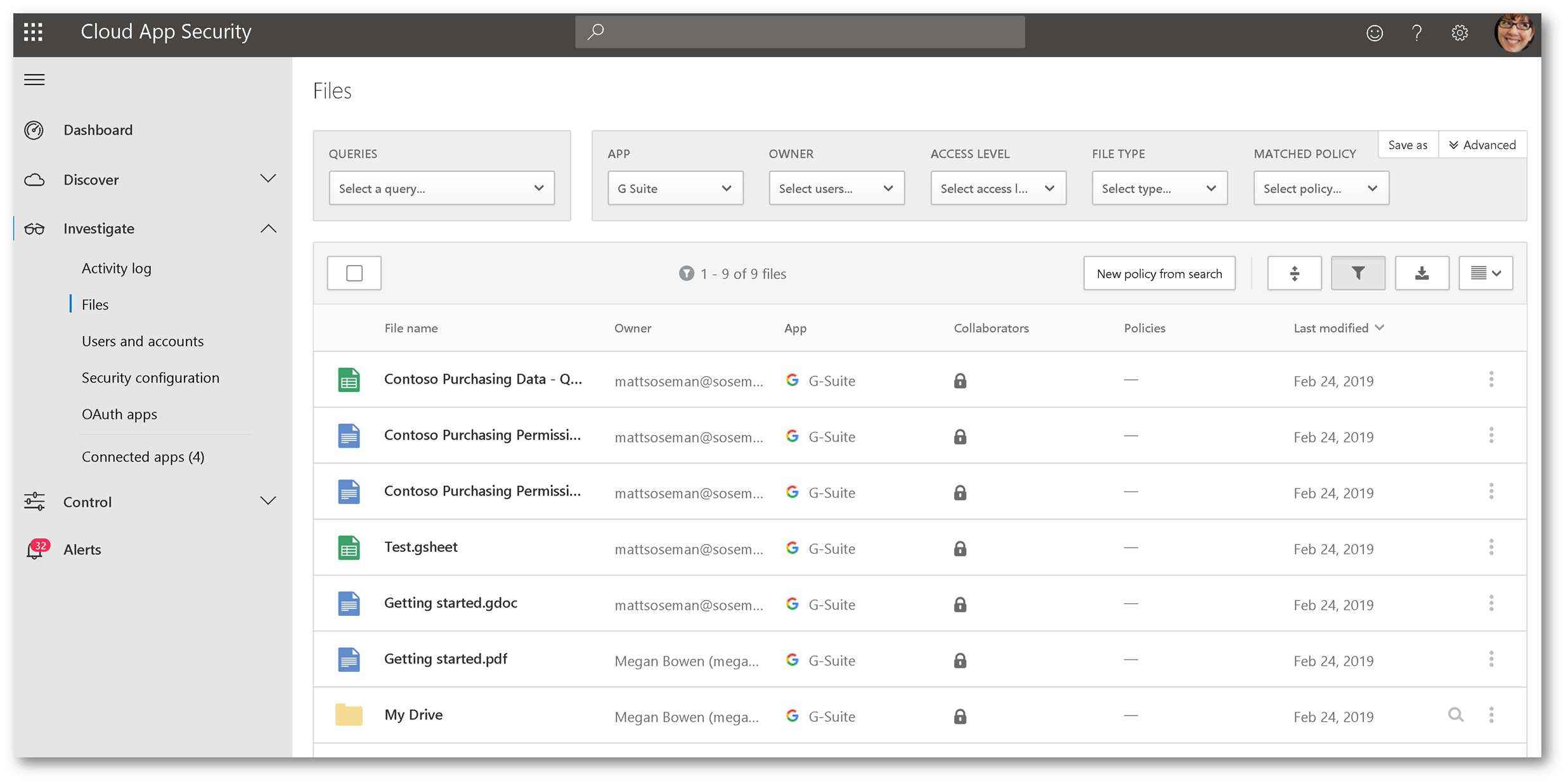
Expanding an individual file allows you to see additional information about it, and clicking the ellipsis gives you additional control over that file, in G Suite: