The [unofficial] guide for SharePoint 2013 (and 2010) working with TLS 1.2 only
There are several resources out there claiming SharePoint 2013 and 2010 are not compatible with TLS 1.2 but no official stance from Microsoft either way until now. This post is still not the official response, but it is the first step in this direction. Official documentation to follow. The official supportability is explained in the links below and the information in this post is still valid:
Enable TLS and SSL support in SharePoint 2013
And
Enable TLS 1.1 and TLS 1.2 support in SharePoint Server 2010
*** UPDATED on 01/17/2019: I worked on a case where the previous keys both here and in TechNet were insufficient (for .NET) in some very rare cases. My friend and colleague Tony DeVere showed me a recent document from .NET team discussing these entries. I updated the post to reflect it and will request a change to TechNet. The .NET article is here.
Background
TLS stands for Transport Layer Security and it is the replacement for Secure Sockets Layer (SSL). SSLv3 is the latest of the SSL protocols and it is well long deprecated in real life and officially deprecated in 2015. TLS 1.0 and TLS 1.1 are still valid protocols but they are disabled by default by most modern browsers. New security patches for Windows disable old protocols. Mostly important is the fact that most companies are tightening security and making sure SSLv3, TLS 1.0 and TLS 1.1 are disabled and only the more secure TLS 1.2 is enabled.
Starting with October 2014 security bulletin there were several changes and patches to the way encryption and hash algorithms are treated in Windows. One of the most important is the one that disables SSLv3 in .NET. The patch is only for .NET 4 and beyond. This is what makes possible to SharePoint 2013 to work with TLS 1.2 without code change.
SharePoint 2010 leverages .NET 3.5, so all these patches mentioned before are of no use. This was the reason that prevented SPS 2010 from being compatible with TLS 1.2. This ended with a patch releases in May 2016: KB 3154518. Now SharePoint 2010 can also works with TLS 1.2 only.
SharePoint relies heavily on SQL and SQL server prior to SQL 2016 (i.e. SQL 2008/2008 R2/2012/2014) does not support TLS 1.2 before KB 3135244. If you are up-to-date with your patches you should be good on this point.
SharePoint relies on WebDAV for Explorer view. Windows Explorer prior to Windows Explorer for Windows 10 is not compatible with TLS 1.2 (this is actually a WinHTTP issue). This issue was resolved by KB 3140245
Steps to enable SharePoint 2013/2010 to work with TLS 1.2 and disable the other protocols
- Make a backup before making any changes
It goes without saying. Also make sure you do the changes in your test and staging farm before going to production.
- Update SQL Server (2008/2008 R2/2012 or 2014), Client Components and Windows to support TLS 1.2
It is possible you already have the build that supports TLS 1.2. You can check this and download and apply the necessary hotfixes if necessary here: https://support.microsoft.com/en-us/kb/3135244
Apply the server update to the SQL Server machines only and the client hotfixes to ALL machines in the farm. You may need to apply the Windows patches as well (all in the KB).
- Install hotfix for .NET 3.5.1 to enable TLS 1.2 for .NET (SharePoint 2010 ONLY)
Skip this step for SharePoint 2013. Download the x64 bits version of this .NET update to install in ALL servers in the farm: https://support.microsoft.com/en-us/kb/3154518
Open command prompt as administrator. Run these commands:
[text]
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727" /f /v DefaultSecureProtocols /t REG_DWORD /d 1
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727" /f /v SystemDefaultTlsVersions /t REG_DWORD /d 1
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727" /f /v SchUseStrongCrypto /t REG_DWORD /d 1
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" /f /v DefaultSecureProtocols /t REG_DWORD /d 1
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" /f /v SystemDefaultTlsVersions /t REG_DWORD /d 1
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" /f /v SchUseStrongCrypto /t REG_DWORD /d 1
[/text]
- Enable Strong Cryptography for .NET 4+ (SharePoint 2013)
This functionality is already in .NET 4+ since October 2013. Make sure your bits are more recent than that.
This is necessary to enable TLS 1.x for SharePoint.
Open command prompt as administrator and run these commands:
[text]
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319" /f /v SchUseStrongCrypto /t REG_DWORD /d 1
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319" /f /v SystemDefaultTlsVersions /t REG_DWORD /d 1
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" /f /v SchUseStrongCrypto /t REG_DWORD /d 1
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" /f /v SystemDefaultTlsVersions /t REG_DWORD /d 1
[/text]
- Disable the protocols you DO NOT want. See this: https://support.microsoft.com/en-us/kb/245030
In the example below, you are making TLS 1.2 default and disabling SSL but you are not disabling the other TLS protocols:
1. Open command prompt as administrator
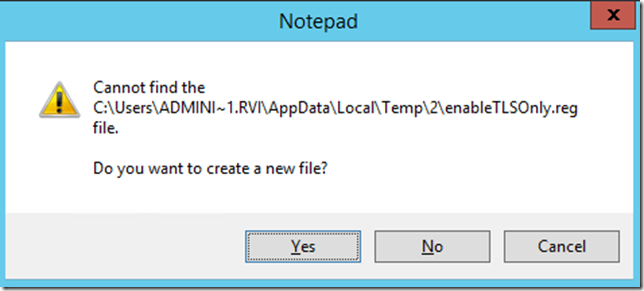
2. Run: notepad %temp%\enableTLSOnly.reg
3. Click yes to the warning below:
3. Paste this into notepad
[text]
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
"Enabled"=dword:00000001
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"Enabled"=dword:00000001
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
"Enabled"=dword:00000001
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
"Enabled"=dword:00000001
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
"Enabled"=dword:00000001
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
"Enabled"=dword:00000001
"DisabledByDefault"=dword:00000000
[/text]
4. Save the file (File | Save or type Ctrl + S)
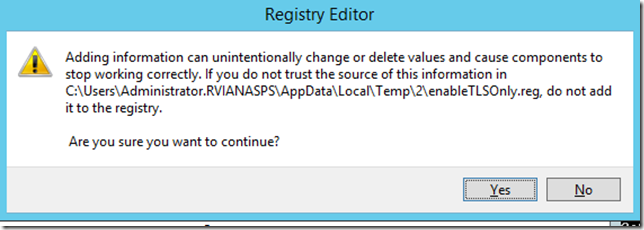
5. Back on command prompt run: start %temp%\enableTLSOnly.reg
6. Click yes to apply the changes to the warning below:
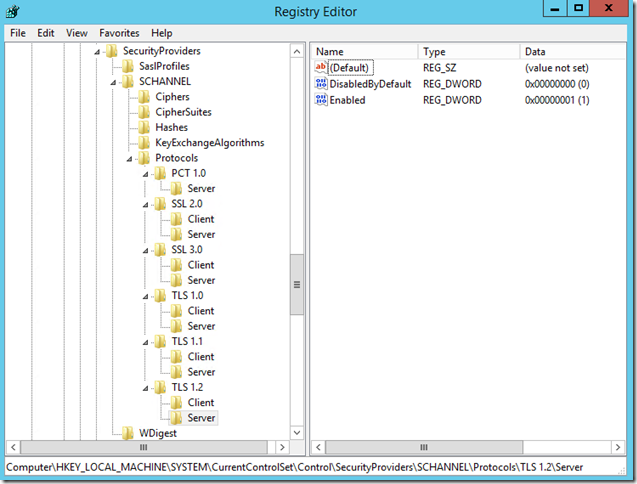
7. The registry should look like this
In the example below you enable only TLS 1.2:
1. Open command prompt as administrator
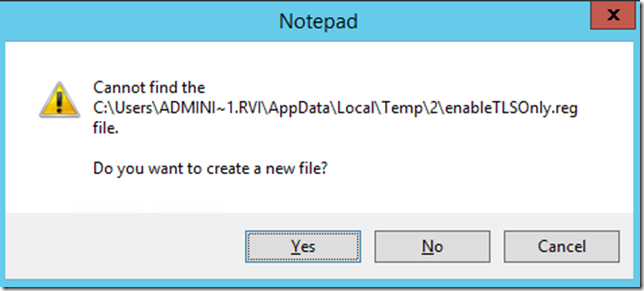
2. Run: notepad %temp%\enableTLS12Only.reg
3. Click yes to the warning below:
3. Paste this into notepad
[text]
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
"Enabled"=dword:00000001
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
"Enabled"=dword:00000001
"DisabledByDefault"=dword:00000000
[/text]
4. Save the file (File | Save or type Ctrl + S)
5. Back on command prompt run: start %temp%\enableTLS12Only.reg
6. Click yes to apply the changes to the warning below:
- On ALL Servers in the farm and in machines consuming document libraries in Explorer view it is necessary to patch Windows
The crawler contains .NET and C++ components. The C++ components use another API, called WinHttp, which is not patched for TLS 1.2 via .NET patches. WebDAV, the protocol for Explorer View, is also accomplished via WinHttp protocol. By default, Windows Explorer will not support TLS 1.2 in Windows 7 and Windows Server 2008 R2. This update is tricky because unlike the others, this UPDATE goes into the CLIENT MACHINES accessing SharePoint document libraries in Explorer view, and also in the servers in the farm. It is however recommended that you also apply the hotfix in the servers. This update is not necessary for Windows 10. Link to the KB with the hotfix: https://support.microsoft.com/en-us/kb/3140245
After applying the update or if you have Windows 10:
Open command prompt as administrator
Run the commands below:
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp" /f /v DefaultSecureProtocols /t REG_DWORD /d 0x0000A80
%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp" /f /v DefaultSecureProtocols /t REG_DWORD /d 0x0000A80
- Wrapping up
I have received feedback from customers that went through these steps and they were able to have SharePoint working with TLS 1.2 enabled. I do not have a end to end case with SharePoint 2010 but it should work too. Please leave feedback so others can know how people are succeeding (or failing).
Comments
- Anonymous
July 05, 2016
Confirm SP 2010 Working with TLS 1.0 Disabled, on SBS 2011. - Anonymous
July 13, 2016
Hi , Thanks for the information.we are trying to enable TLS 1.2 on our sharepoint server.Our Sharepoint2010 web/app server OS is windows server 2008 r2 standard. but our SQL database(SQL Server 2008 Enterprise Edition) is in different server and its OS is Windows server 2003 R2.As TLS is OS level setting and can not compatible with Windows server 2003, so can we enable TLS 1.2 on our sharepoint server?- Anonymous
July 13, 2016
Hi Madhukiran,I don't believe you will be able to have TLS 1.2 on your Windows 2003. You will have to move your SQL Server to a newer OS.
- Anonymous
- Anonymous
September 06, 2016
Anyone else having an issue when trying to run this fix on a win7/office2010 machine? tls 1.2 enabled on the server. all functions seem ok except we are unable to set automatic replies in outlook. we receive error: "Your automatic reply settings cannot be displayed because the server is currently unavailable. Try again later".- Anonymous
September 28, 2016
Tony,On machines running office, follow the steps in section "On machines consuming document libraries in Explorer view it is necessary to patch Windows".
- Anonymous
- Anonymous
October 10, 2016
SharePoint 2013 TLS 1.2User profile sync services are working.Failed to connect to the database Sync_DBconnection open SSEcreate credentials ssl security error- SQL connectivity issue.- Anonymous
October 10, 2016
The comment has been removed- Anonymous
October 12, 2016
The comment has been removed- Anonymous
October 13, 2016
Update- issue is resolved after installing Microsoft SQL Server 2008 R2 Native client competent..- Anonymous
November 29, 2018
Hi Naveen,Could you please tell which exact Microsoft SQL Server 2008 R2 Native client patch you have installed.In the link below the patch for Microsoft SQL Server 2008 R2 Native client is no longer exists.https://support.microsoft.com/en-us/help/3135244/tls-1-2-support-for-microsoft-sql-server
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
October 12, 2016
I have followed the above configuration guidelines, we have a SharePoint 2013 service running on Windows Server 2012 R2.SharePoint works but we are unable to get Office Web Apps to work with a TLS 1.2 configuration, symptoms as per https://support.microsoft.com/en-gb/kb/3160699This article states OWA requires TLS 1.0Can anyone confirm that they have OWA working on TLS 1.2- Anonymous
October 13, 2016
Chris,Did you follow all steps in this article? Did you install this on the machines consuming SPS?– On machines consuming document libraries in Explorer view it is necessary to patch WindowsWebDAV is accomplished via WinHTTP protocol. By default, Windows Explorer will not support TLS 1.2 in Windows 7 and Windows Server 2008 R2. This update is tricky because unlike the others, this UPDATE goes into the CLIENT MACHINES accessing SharePoint document libraries in Explorer view, not the servers. It is however recommended that you also apply the hotfix in the servers. This update is not necessary for Windows 10. Link to the KB with the hotfix: https://support.microsoft.com/en-us/kb/3140245After applying the update or if you have Windows 10:Open command prompt as administratorRun the commands below: %windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp" /f /v DefaultSecureProtocols /t REG_DWORD /d 0x0000A80%windir%\system32\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp" /f /v DefaultSecureProtocols /t REG_DWORD /d 0x0000A80
- Anonymous
- Anonymous
October 13, 2016
The comment has been removed- Anonymous
October 18, 2016
Hi Naveen,Apply this on all machines consuming SQL server (and SQL Servers too):https://support.microsoft.com/en-us/kb/3135244- Anonymous
January 26, 2017
Hi, So, https://support.microsoft.com/en-us/kb/3135244 is required both for Sql boxes plus all SharePoint boxes (I were originally assuming this is just required for SharePoint boxes only )- Anonymous
January 26, 2017
The SQL Server and the machines consuming SQL (SQL Clients and SharePoint servers at the same time) must be updated.- Anonymous
January 27, 2017
Hi Rodney,Thanks for quick response and great information .Is it true if Sql servers are upgraded with SP3 we don't require to apply https://support.microsoft.com/en-us/kb/3135244 individually towards Sql Side , However we have to apply all machines/Servers in SharePoint 2013 Farm ?
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
October 25, 2016
Trying this in SP2013 but having trouble with Workflow Manager unless SSL3/TLS1.0 remains available. Is there a separate set of updates required for workflow to work with only TLS1.2 available?- Anonymous
November 23, 2016
Follow the instructions for WebDAV and install the .NET 3.5 hotfix.
- Anonymous
- Anonymous
October 26, 2016
Good info. Any comments on when this page might change to supported? https://technet.microsoft.com/en-us/library/mt757340.aspx- Anonymous
November 23, 2016
The information was updated to include the full support. See links in the beginning of the post.
- Anonymous
- Anonymous
October 28, 2016
Good news. Microsoft officially announced it that SharePoint 2013 does not fully support TLS 1.1 and TLS 1.2. See complete guide on below url.https://technet.microsoft.com/en-us/library/mt757340.aspx- Anonymous
November 23, 2016
As I told in the post, the official support was close. Now it is official. I updated the post with the appropriate links.- Anonymous
November 23, 2016
Thank you Rodney for updating the article.Microsoft updated their documentation saying that SharePoint 2013 now supports below TLS and SSL protocols.1. TLS 1.22. TLS 1.13. TLS 1.04. SSL 3.0However SSL 3.0 is still not recommended. See more details below.https://technet.microsoft.com/en-us/library/mt757340.aspxVisit below link for enabling TLS for SharePoint.https://technet.microsoft.com/en-us/library/mt773991.aspxRegards - Anonymous
April 04, 2017
Hi Rodeny, after TLS1.0Server disabled in SharePoint 2013 , everything is working fine so far but we have one issue "Service Bus message broker" Service stuck at starting , killed the process and restarted it but doesn't help .Installed Service Bus appear to be 1.0 Version any reported issue yet ? or Any fix for it Thanks,Mohan- Anonymous
April 22, 2017
I am having the same problem with the Service Bus Message Broker service stuck at the starting stage after disabling TLS 1.0. - Anonymous
April 25, 2017
Sorry, not an expert in service bus. Do you need service bus in your SharePoint server?- Anonymous
June 17, 2017
Yes. It's needed for the workflows to run.
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
August 23, 2017
Hello,Tried all the steps in technet "https://technet.microsoft.com/library/mt773993(v=office.16).aspx" for SharePoint 2016, but still have issues while accessing office documents in local office application (like open in Word) from SharePoint 2016 sites after disabling TLS1.0. Any suggestions?- Anonymous
August 29, 2017
Follow steps on section "On ALL Servers in the farm and in machines consuming document libraries in Explorer view it is necessary to patch Windows"
- Anonymous
- Anonymous
January 10, 2018
Question, When our registry changed for TLS 1.2 it shows 0x0000a80 instead of 0x0000A80. Lowercase 'a'. Will this cause issues?- Anonymous
January 10, 2018
Answered it myself.. - Anonymous
January 11, 2018
No, it is case insensitive.
- Anonymous
- Anonymous
March 15, 2018
The comment has been removed- Anonymous
March 15, 2018
- Q: "The step “Install hotfix for .NET 3.5.1 to enable TLS 1.2 for .NET (SharePoint 2010 ONLY)” should be completely skipped for SharePoint 2013, also the REG commands?"A: Yes, you should skip this step for SharePoint 2013/20162. Q: Where to download the KBA: Download here:http://www.catalog.update.microsoft.com/search.aspx?q=kb3140245
- Anonymous
- Anonymous
November 14, 2018
Is there any known impact/issue on the FAST Search running in SharePoint 2010 after disabling SSL 2.0, SSL 3.0, TLS 1.0 and 1.1 and enabling TLS 1.2? We've discovered the FAST Search certificate not trusted anymore after completing the procedure described at https://docs.microsoft.com/en-us/previous-versions/office/sharepoint-server-2010/mt773992(v=office.14).- Anonymous
November 14, 2018
Follow this step from the blog post:- On ALL Servers in the farm and in machines consuming document libraries in Explorer view it is necessary to patch Windows- Anonymous
November 16, 2018
Thanks Rodney.The Microsoft documentation at https://docs.microsoft.com/en-us/previous-versions/office/sharepoint-server-2010/mt773992(v=office.14) does not even mention the FAST Search servers.
- Anonymous
- Anonymous
- Anonymous
November 15, 2018
I am using Sharepoint 2013.User profile sync service and FIM Sync are not working after TLS1.2 udpate.Failed to connect to the database Sync_DB.Hotfix for SQL Server Native Client (for SQL Server 2008 R2) is not available in the link,Please suggest how to proceed.https://support.microsoft.com/en-us/help/3135244/tls-1-2-support-for-microsoft-sql-server- Anonymous
November 20, 2018
Download any newer SQL patch and it will include the fix for TLS 1.2- Anonymous
November 26, 2018
The comment has been removed
- Anonymous
- Anonymous
- Anonymous
November 16, 2018
It looks like the hotfix for SQL Server Native Client (x86 and x64) is no longer available. Do you know why this is the case?- Anonymous
November 20, 2018
Get anything more recent and it will include the support to TLS 1.2,- Anonymous
November 20, 2018
Do you mean any new SQL Server patch or any patch for the SQL client that is installed on SharePoint? I can't find any other updates for the SQL Server 2008R2 Native Client that is installed on each SharePoint Server.- Anonymous
December 04, 2018
Microsoft has updated the link,hotfix is avalaible now for SQL Server 2008R2 Native Client.https://docs.microsoft.com/en-us/SharePoint/security-for-sharepoint-server/enable-tls-and-ssl-support-in-sharepoint-2013https://www.microsoft.com/en-us/download/details.aspx?id=57606
- Anonymous
- Anonymous
- Anonymous