How to get a SAML Protocol Response from ADFS using C#
ADFS (Active Directory Federation Services) is a fancy name for Windows Identity Foundation Server. ADFS supports SAML protocol, however its client, Windows Identity Foundation (WIF), does not. As most of the problems of acquiring a token can be resolved with either WS-Federation and WS-Trust, you may use WIF for your federation needs since WIF supports SAML-Token (please notice SAML-Protocol is not the same as SAML-Token).
Lately I have received requests from partners and customers to acquire a SAML Protocol Response which would require SAML-Protocol to request. WIF unfortunately cannot be used to make a SAML-Protocol request and there is no out-of-the-box way of doing that. There are some paid NuGets implementing SAML-Protocol in C#, but none is free. I put together a workaround to request a SAML-Protocol response from ADFS in C# using HttpClient (from System.Net.Http library). System.Net.Http.HttpClient class comes with .NET 4.5 and 4.5.1 and can be added via NuGet to .NET 4.0. The idea is to leverage ADFS Idp Initiated Login page and follow the redirects to extract the SAML Response that happens during the process of logging in to a SAML-Protocol endpoint.
Requirements
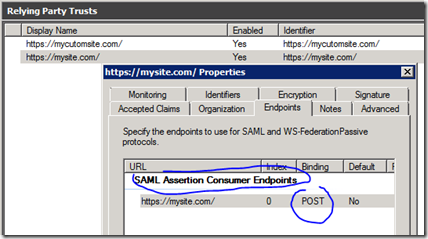
You have to create a SAML-Protocol Assertion Endpoint with POST binding in your reliant party configuration. This endpoint can co-exist with a Federation endpoint.
Code
I put together two samples. One that shows step-by-step using a Windows Forms application how to acquire a SAML Response (you can download it here):
Windows Forms Snippet
using System;
using System.Collections.Generic;
using System.ComponentModel;
using System.Data;
using System.Drawing;
using System.Linq;
using System.Net.Http;
using System.Text;
using System.Threading.Tasks;
using System.Windows.Forms;
using System.Xml;
using System.Text.RegularExpressions;
using System.Web;
using System.IO;
using System.IO.Compression;
//The code samples are provided AS IS without warranty of any kind.
// Microsoft disclaims all implied warranties including, without limitation,
// any implied warranties of merchantability or of fitness for a particular purpose.
/*
The entire risk arising out of the use or performance of the sample scripts and documentation remains with you.
In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts
be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption,
loss of business information, or other pecuniary loss) arising out of the use of or inability to use the sample scripts
or documentation, even if Microsoft has been advised of the possibility of such damages.
*/
namespace GetSaml
{
public partial class Form1 : Form
{
public Form1()
{
InitializeComponent();
}
private string getUrl = null;
private string GetUrl
{
get
{
if (!String.IsNullOrEmpty(getUrl))
return getUrl;
StringBuilder domain = new StringBuilder();
domain.Append(Environment.GetEnvironmentVariable("USERDNSDOMAIN"));
if (domain.Length > 0)
{
domain.Clear();
domain.Append(Environment.UserDomainName);
}
//return String.Format("https://{0}.{1}.lab/adfs/ls/MyIdpInitiatedSignOn.aspx?loginToRp=https://mysyte.com", Environment.MachineName.ToLower(), Environment.UserDomainName.ToLower());
return String.Format("https://{0}.{1}.lab/adfs/ls/IdpInitiatedSignOn.aspx", Environment.MachineName.ToLower(), Environment.UserDomainName.ToLower());
}
}
private void Form1_Load(object sender, EventArgs e)
{
textBox1.Text = GetUrl;
}
protected List<KeyValuePair<string, string>> forms;
private HttpClient client = null;
private HttpClientHandler handler;
private HttpClient Client
{
get
{
if (client == null)
{
handler = new HttpClientHandler();
handler.UseDefaultCredentials = true;
handler.AllowAutoRedirect = false;
handler.CookieContainer = new System.Net.CookieContainer();
handler.UseCookies = true;
client = new HttpClient(handler);
client.MaxResponseContentBufferSize = 256000;
client.DefaultRequestHeaders.Add("User-Agent", "Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; WOW64; Trident/6.0)");
client.DefaultRequestHeaders.Add("Connection", "Keep-Alive");
client.DefaultRequestHeaders.ExpectContinue = false;
}
return client;
}
}
private async void button1_Click(object sender, EventArgs e)
{
string url = String.Format("{0}?loginToRp={1}", textBox1.Text, HttpUtility.UrlEncode(comboBox1.SelectedItem.ToString()));
// Limit the max buffer size for the response so we don't get overwhelmed
HttpResponseMessage result;
textBox3.Text="============== Start ===============";
var nl = Environment.NewLine;
string text;
do
{
textBox3.AppendText(String.Format("{1}********** GET {0}{1}", url, Environment.NewLine));
result = await Client.GetAsync(url);
text = await result.Content.ReadAsStringAsync();
IEnumerable<string> values;
if(result.Headers.TryGetValues("location", out values))
{
foreach(string s in values)
{
if (s.StartsWith("/"))
{
url = url.Substring(0, url.IndexOf("/adfs/ls")) + s;
}
else
url = s;
}
} else
{
url = "";
}
textBox3.AppendText(String.Format("{0}[Headers]{0}", Environment.NewLine));
foreach(var pair in result.Headers)
{
string key = pair.Key;
foreach(var val in pair.Value)
textBox3.AppendText(String.Format(" {0}={1}{2}", key, val, Environment.NewLine));
}
textBox3.AppendText(text);
} while (!String.IsNullOrEmpty(url));
Regex reg = new Regex("SAMLResponse\\W+value\\=\\\"([^\\\"]+)\\\"");
MatchCollection matches = reg.Matches(text);
string last = null;
foreach (Match m in matches)
{
last = m.Groups[1].Value;
textBox3.AppendText(String.Format(" {1}{1}{1}SAMLResponse={0}{1}", last, Environment.NewLine));
}
if(last != null)
{
byte[] decoded = Convert.FromBase64String(last);
string deflated = Encoding.UTF8.GetString(decoded);
XmlDocument doc = new XmlDocument();
StringBuilder sb = new StringBuilder();
doc.LoadXml(deflated);
using(StringWriter sw = new StringWriter(sb))
{
using (XmlTextWriter tw = new XmlTextWriter(sw) { Formatting = Formatting.Indented })
{
doc.WriteTo(tw);
}
}
textBox3.AppendText(String.Format(" {1}{1}{1}XML Formated:{1}{0}{1}", sb.ToString(), Environment.NewLine));
}
}
private void DysplayError(Exception ex)
{
MessageBox.Show(String.Format("Error: {0}{1}Stack:{1}{2}", ex.Message, Environment.NewLine, ex.StackTrace));
}
private async void button2_Click(object sender, EventArgs e)
{
try
{
var response = await Client.GetAsync(textBox1.Text);
response.EnsureSuccessStatusCode();
comboBox1.Items.Clear();
string text = await response.Content.ReadAsStringAsync();
Regex reg = new Regex("option\\W+value\\=\\\"([^\\\"]+)\\\"");
MatchCollection matches = reg.Matches(text);
foreach(Match m in matches)
{
comboBox1.Items.Add(m.Groups[1].Value);
}
if (matches.Count == 0)
{
MessageBox.Show("No Reliant Party found");
button1.Enabled = false;
} else
{
button1.Enabled = true;
comboBox1.SelectedIndex = 0;
}
} catch(Exception ex)
{
DysplayError(ex);
return;
}
}
}
}
I also organized the code in a class library that can be used in any C# application. You can download the code and test application here.
Class to get SAML Response
using System;
using System.Collections.Generic;
using System.Text;
using System.Threading.Tasks;
using System.Net.Http;
using System.Text.RegularExpressions;
using System.Web;
using System.Xml;
using System.IO;
//The code samples are provided AS IS without warranty of any kind.
// Microsoft disclaims all implied warranties including, without limitation,
// any implied warranties of merchantability or of fitness for a particular purpose.
/*
The entire risk arising out of the use or performance of the sample scripts and documentation remains with you.
In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts
be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption,
loss of business information, or other pecuniary loss) arising out of the use of or inability to use the sample scripts
or documentation, even if Microsoft has been advised of the possibility of such damages.
*/
namespace Microsoft.Samples.AdfsSaml
{
/// <summary>
/// Class to get a SAML response from ADFS.
/// it requires that the SAML endpoint with POST binding is configured in ADFS
/// </summary>
public class SamlResponse
{
/// <summary>
/// If true, ADFS url will not be validated
/// </summary>
public bool EnableRawUrl
{
get;
set;
}
private Uri serverAddress = null;
private HttpClient client = null;
private HttpClientHandler handler;
private HttpClient Client
{
get
{
if (client == null)
{
handler = new HttpClientHandler();
handler.UseDefaultCredentials = true;
handler.AllowAutoRedirect = false;
handler.CookieContainer = new System.Net.CookieContainer();
handler.UseCookies = true;
client = new HttpClient(handler);
client.MaxResponseContentBufferSize = 256000;
client.DefaultRequestHeaders.Add("User-Agent", "Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; WOW64; Trident/6.0)");
client.DefaultRequestHeaders.Add("Connection", "Keep-Alive");
client.DefaultRequestHeaders.ExpectContinue = false;
}
return client;
}
}
/// <summary>
/// Url of ADFS server (e.g. https://adfs.contoso.com)
/// </summary>
public Uri ServerAddress
{
get
{
return serverAddress;
}
set
{
if(EnableRawUrl)
{
serverAddress = value;
return;
}
string host = value.Host;
string scheme = value.Scheme;
if(scheme != "https")
{
throw new ArgumentException("ADFS rquires scheme https. Set EnableRawUrl to true to override it", "ServerAddress");
}
serverAddress = new Uri(String.Format("https://{0}//adfs/ls/IdpInitiatedSignOn.aspx", host));
}
}
/// <summary>
/// Initialize the class
/// </summary>
public SamlResponse()
{
}
/// <summary>
/// Initialize the class
/// </summary>
/// <param name="Url">Urn of reliant party as defined in ADFS. Ise GetReliantPArtyCollection to get the list</param>
/// <param name="IsRawUrl">If true, ADFS url will not be validated</param>
public SamlResponse(Uri Url, bool IsRawUrl = false)
{
EnableRawUrl = IsRawUrl;
ServerAddress = Url;
}
private async Task<string[]> GetReliantPartyCollectionInternal()
{
if (serverAddress == null)
{
throw new NullReferenceException("ServerAddress was not set");
}
var response = await Client.GetAsync(serverAddress);
response.EnsureSuccessStatusCode();
string text = await response.Content.ReadAsStringAsync();
Regex reg = new Regex("option\\W+value\\=\\\"([^\\\"]+)\\\"");
MatchCollection matches = reg.Matches(text);
if(matches.Count == 0)
{
return null;
}
string[] rps = new string[matches.Count];
uint i = 0;
foreach (Match m in matches)
{
rps[i++]=m.Groups[1].Value;
}
return rps;
}
/// <summary>
/// Get the list of Reliant Parties with SAML endpoint with binding POST in ADFS
/// </summary>
public string[] GetReliantPartyCollection()
{
return GetReliantPartyCollectionInternal().Result;
}
/// <summary>
/// Retrieve the SAML Response from ADFS for ReliantPartyUrn
/// </summary>
/// <param name="ReliantPartyUrn">Urn of reliant party as defined in ADFS. Ise GetReliantPArtyCollection to get the list</param>
public string RequestSamlResponse(string ReliantPartyUrn)
{
if(serverAddress == null)
{
throw new NullReferenceException("ServerAddress was not set");
}
if(String.IsNullOrEmpty(ReliantPartyUrn) && !EnableRawUrl)
{
throw new ArgumentException("Reliant Party Urn cannot be empty if EnableRawUrl is not true");
}
return SamlResponseInternal(ReliantPartyUrn).Result;
}
private async Task<string> SamlResponseInternal(string ReliantPartyUrn)
{
StringBuilder url = new StringBuilder(String.Format("{0}?loginToRp={1}", serverAddress, HttpUtility.UrlEncode(ReliantPartyUrn)));
HttpResponseMessage result;
do
{
result = await Client.GetAsync(url.ToString());
string text = await result.Content.ReadAsStringAsync();
IEnumerable<string> values;
if (result.Headers.TryGetValues("location", out values))
{
foreach (string s in values)
{
if (s.StartsWith("/"))
{
string newUrl = url.ToString().Substring(0, url.ToString().IndexOf("/adfs/ls"));
url.Clear();
url.Append(newUrl);
url.Append(s);
}
else
{
url.Clear();
url.Append(s);
}
}
}
else
{
url.Clear();
}
if (url.Length == 0)
{
Regex reg = new Regex("SAMLResponse\\W+value\\=\\\"([^\\\"]+)\\\"");
MatchCollection matches = reg.Matches(text);
foreach (Match m in matches)
{
return m.Groups[1].Value;
}
}
} while (url.Length > 0);
throw new InvalidOperationException("Unable to get a SAMLP response from ADFS");
}
public static string SamlToXmlString(string EncodedResponse)
{
byte[] decoded = Convert.FromBase64String(EncodedResponse);
string deflated = Encoding.UTF8.GetString(decoded);
XmlDocument doc = new XmlDocument();
StringBuilder sb = new StringBuilder();
doc.LoadXml(deflated);
using (StringWriter sw = new StringWriter(sb))
{
using (XmlTextWriter tw = new XmlTextWriter(sw) { Formatting = Formatting.Indented })
{
doc.WriteTo(tw);
}
}
return sb.ToString();
}
}
}
Comments
Anonymous
September 22, 2014
Most excellent utility. Thank you.Anonymous
October 23, 2014
I have attempted to use the Form to pull a SAMLResponse from the AWS Relying Party trust off of my ADFS server however it doesn't show the SAMLResponse output anywhere. Thoughts?Anonymous
October 23, 2014
The comment has been removedAnonymous
October 27, 2014
Yes I have ran this against the 2 other sites in the Target Name drop down list. None show the SAMLResponse. It's a lot of text including SAMLRequest and Page information. Just doesn't include your SAMLResponse shown above. I simply downloaded the Form code, and ran the .exe and put in my adfs server name and then chose the AWS site.Anonymous
October 27, 2014
Todd, Can you show me an output?Anonymous
October 27, 2014
Do I need to be installing anything before running the GetSaml.exe? I am not a master coder by any means so I was running the form rather than trying to do a C# application. Here is the output: ============== Start =============== ********** GET https://ADFS/adfs/ls/IdpInitiatedSignOn.aspx?loginToRp=urn%3aamazon%3awebservices [Headers] Pragma=no-cache Cache-Control=no-cache Date=Mon, 27 Oct 2014 19:40:24 GMT Location=https://ADFS/adfs/ls/?SAMLRequest=7b0HYBxJliUmL23Ke39K9UrX4HShCIBgEyTYkEAQ7MGIzeaS7B1pRyMpqyqBymVWZV1mFkDM7Z28995777333nvvvfe6O51OJ%2fff%2fz9cZmQBbPbOStrJniGAqsgfP358Hz8iHjfZolw9Ol638%2bWr%2fBet86ZNz55%2b9tHvn%2b09zCf5w3z7PLu3u70%2fvT%2fbzvJ7B9v39w5me7uzbDp9%2bPCj9Cfzuimq5Wcf7Y13PkrPmmadny2bNlu29NHO7v727s723oM3uw8f7e882n84%2fnR356c%2bSp9SL8Uya%2fnNeduumkd377Zt0zbjts5mxfKizafzZVVWF0XejKfV4m42O2%2fuls3dj9KTatnkgL%2bul4%2bqrCmaR8tskTeP2umj18dfPH9EqDyaSqNH62WzyqfFeZHPPkrfLcpl84gHvPntVV211bQqPzp6zEOq5dXNL2VNk9cY0kdHGNLtRkSvXBbTvLnb1uumfXxXujt6TIOcFQDWvGfXj4%2fXsyJfTvNXROO6mOJT9%2bERoGSL7AfV8tFVPjG9P75rG7hfAwB3HUL0R59njv4f&Signature=haV26bjGqbuPcg0sywh3h3pwsbZ3WdPy20r2GTax%2b4Or0qVJ9rZiIi4CQToev83N0Iyah%2bi%2btbowVj8Au7HYau43vlSkz%2foQondUYEnkUNHi8PaExLIXZ8vPCVYCWSu%2bbIEHTQh%2fOiGFNRFL47o7eGfdFoc87rmHcTWrxbJyO9BdiHT%2fVvG6h5LjtD%2fk1YbR0ZcMwnJlIujnaYVJ8mp9kc908vsG4Jp8yyUD8f1R09TXjgEGV9oExOjcOHcZf6KDwfp6vRKGXjhaBAivdIbHzlCUsfSjrJIukuif6ng6FKvvqBd%2bNh%2fMjoYXIiGcQ%2bSyPTKsnc%2fJvHM0RKIhvByBgOf2G2ieTlnU2aPf5Vwnzo1nTUwI7PVvIWRDfI1d727pDBhK%2f%2fXFDe%2b9nK8BF3MOYdqWE650ISwhPQyQP9d75DhOdG%2fd%2fRp4q8ogjyb%2fv4oy02szfH66Ezlx1elXn7WQsKC41FgyMFmhqvqJsn7In7tgmXXkKIFhJN13bOIDIqXnef8uZsDGYWG8topaYgnCtgVa6KQr9fQxiI9ZmeJ1TpuXG1WDXmGcwZ4U3yq2hGFebliAzhqj9ePgVShwrFTctKifjrMugBdDE8gQLaQXXBSJC0F54gfG9jYUksYwxT9RUfOB%2b0NvVq4lhIxc3n0nO%2fN3AShDG2jRjzdQ5KTsO4c%3d&SigAlg=http%3a%2f%2fwww.w3.org%2f2001%2f04%2fxmldsig-more%23rsa-sha256 Server=Microsoft-IIS/7.5 X-AspNet-Version=2.0.50727 X-Powered-By=ASP.NETAnonymous
October 27, 2014
<html><head></head><body> <h2>Object moved to <a href="https://ADFS/adfs/ls/?SAMLRequest=7b0HYBxJliUmL23Ke39K9UrX4HShCIBgEyTYkEAQ7MGIzeaS7B1pRyMpqyqBymVWZV1mFkDM7Z28995777333nvvvfe6O51OJ%2fff%2fz9cZmQBbPbOStrJniGAqsgfP358Hz8iHjfZolw9Ol638%2bWr%2fBet86ZNz55%2b9tHvn%2b09zCf5w3z7PLu3u70%2fvT%2fbzvJ7B9v39w5me7uzbDp9%2bPCj9Cfzuimq5Wcf7Y13PkrPmmadny2bNlu29NHO7v727s723oM3uw8f7e882n84%2fnR356c%2bSp9SL8Uya%2fnNeduumkd377Zt0zbjts5mxfKizafzZVVWF0XejKfV4m42O2%2fuls3dj9KTatnkgL%2bul4%2bqrCmaR8tskTeP2umj18dfPH9EqDyaSqNH62WzyqfFeZHPPkrfLcpl84gHvPntVV211bQqPzp6zEOq5dXNL2VNk9cY0kdHGNLtRkSvXBbTvLnb1uumfXxXujt6TIOcFQDWvGfXj4%2fXsyJfTvNXROO6mOJT9%2bERoGSL7AfV8tFVPjG9P75rG7hfAwB3HUL0R59njv4f&Signature=haV26bjGqbuPcg0sywh3h3pwsbZ3WdPy20r2GTax%2b4Or0qVJ9rZiIi4CQToev83N0Iyah%2bi%2btbowVj8Au7HYau43vlSkz%2foQondUYEnkUNHi8PaExLIXZ8vPCVYCWSu%2bbIEHTQh%2fOiGFNRFL47o7eGfdFoc87rmHcTWrxbJyO9BdiHT%2fVvG6h5LjtD%2fk1YbR0ZcMwnJlIujnaYVJ8mp9kc908vsG4Jp8yyUD8f1R09TXjgEGV9oExOjcOHcZf6KDwfp6vRKGXjhaBAivdIbHzlCUsfSjrJIukuif6ng6FKvvqBd%2bNh%2fMjoYXIiGcQ%2bSyPTKsnc%2fJvHM0RKIhvByBgOf2G2ieTlnU2aPf5Vwnzo1nTUwI7PVvIWRDfI1d727pDBhK%2f%2fXFDe%2b9nK8BF3MOYdqWE650ISwhPQyQP9d75DhOdG%2fd%2fRp4q8ogjyb%2fv4oy02szfH66Ezlx1elXn7WQsKC41FgyMFmhqvqJsn7In7tgmXXkKIFhJN13bOIDIqXnef8uZsDGYWG8topaYgnCtgVa6KQr9fQxiI9ZmeJ1TpuXG1WDXmGcwZ4U3yq2hGFebliAzhqj9ePgVShwrFTctKifjrMugBdDE8gQLaQXXBSJC0F54gfG9jYUksYwxT9RUfOB%2b0NvVq4lhIxc3n0nO%2fN3AShDG2jRjzdQ5KTsO4c%3d&SigAlg=http%3a%2f%2fwww.w3.org%2f2001%2f04%2fxmldsig-more%23rsa-sha256">here</a>.</h2> </body></html> ********** GET https://ADFS/adfs/ls/?SAMLRequest=7b0HYBxJliUmL23Ke39K9UrX4HShCIBgEyTYkEAQ7MGIzeaS7B1pRyMpqyqBymVWZV1mFkDM7Z28995777333nvvvfe6O51OJ%2fff%2fz9cZmQBbPbOStrJniGAqsgfP358Hz8iHjfZolw9Ol638%2bWr%2fBet86ZNz55%2b9tHvn%2b09zCf5w3z7PLu3u70%2fvT%2fbzvJ7B9v39w5me7uzbDp9%2bPCj9Cfzuimq5Wcf7Y13PkrPmmadny2bNlu29NHO7v727s723oM3uw8f7e882n84%2fnR356c%2bSp9SL8Uya%2fnNeduumkd377Zt0zbjts5mxfKizafzZVVWF0XejKfV4m42O2%2fuls3dj9KTatnkgL%2bul4%2bqrCmaR8tskTeP2umj18dfPH9EqDyaSqNH62WzyqfFeZHPPkrfLcpl84gHvPntVV211bQqPzp6zEOq5dXNL2VNk9cY0kdHGNLtRkSvXBbTvLnb1uumfXxXujt6TIOcFQDWvGfXj4%2fXsyJfTvNXROO6mOJT9%2bERoGSL7AfV8tFVPjG9P75rG7hfAwB3HUL0R59njv4f&Signature=haV26bjGqbuPcg0sywh3h3pwsbZ3WdPy20r2GTax%2b4Or0qVJ9rZiIi4CQToev83N0Iyah%2bi%2btbowVj8Au7HYau43vlSkz%2foQondUYEnkUNHi8PaExLIXZ8vPCVYCWSu%2bbIEHTQh%2fOiGFNRFL47o7eGfdFoc87rmHcTWrxbJyO9BdiHT%2fVvG6h5LjtD%2fk1YbR0ZcMwnJlIujnaYVJ8mp9kc908vsG4Jp8yyUD8f1R09TXjgEGV9oExOjcOHcZf6KDwfp6vRKGXjhaBAivdIbHzlCUsfSjrJIukuif6ng6FKvvqBd%2bNh%2fMjoYXIiGcQ%2bSyPTKsnc%2fJvHM0RKIhvByBgOf2G2ieTlnU2aPf5Vwnzo1nTUwI7PVvIWRDfI1d727pDBhK%2f%2fXFDe%2b9nK8BF3MOYdqWE650ISwhPQyQP9d75DhOdG%2fd%2fRp4q8ogjyb%2fv4oy02szfH66Ezlx1elXn7WQsKC41FgyMFmhqvqJsn7In7tgmXXkKIFhJN13bOIDIqXnef8uZsDGYWG8topaYgnCtgVa6KQr9fQxiI9ZmeJ1TpuXG1WDXmGcwZ4U3yq2hGFebliAzhqj9ePgVShwrFTctKifjrMugBdDE8gQLaQXXBSJC0F54gfG9jYUksYwxT9RUfOB%2b0NvVq4lhIxc3n0nO%2fN3AShDG2jRjzdQ5KTsO4c%3d&SigAlg=http%3a%2f%2fwww.w3.org%2f2001%2f04%2fxmldsig-more%23rsa-sha256Anonymous
October 27, 2014
[Headers] Pragma=no-cache Cache-Control=no-cache Date=Mon, 27 Oct 2014 19:40:24 GMT Server=Microsoft-IIS/7.5 X-AspNet-Version=2.0.50727 X-Powered-By=ASP.NET <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "www.w3.org/.../xhtml1-transitional.dtd"> <html xmlns="www.w3.org/.../xhtml" dir="ltr"> <head><meta http-equiv="X-UA-Compatible" content="IE=8" /><link rel="stylesheet" type="text/css" href="MasterPages/StyleSheet.css" /><meta name="robots" content="noindex, nofollow" /></head> <body> <form name="aspnetForm" method="post" action="/adfs/ls/?SAMLRequest=7b0HYBxJliUmL23Ke39K9UrX4HShCIBgEyTYkEAQ7MGIzeaS7B1pRyMpqyqBymVWZV1mFkDM7Z28995777333nvvvfe6O51OJ%2fff%2fz9cZmQBbPbOStrJniGAqsgfP358Hz8iHjfZolw9Ol638%2bWr%2fBet86ZNz55%2b9tHvn%2b09zCf5w3z7PLu3u70%2fvT%2fbzvJ7B9v39w5me7uzbDp9%2bPCj9Cfzuimq5Wcf7Y13PkrPmmadny2bNlu29NHO7v727s723oM3uw8f7e882n84%2fnR356c%2bSp9SL8Uya%2fnNeduumkd377Zt0zbjts5mxfKizafzZVVWF0XejKfV4m42O2%2fuls3dj9KTatnkgL%2bul4%2bqrCmaR8tskTeP2umj18dfPH9EqDyaSqNH62WzyqfFeZHPPkrfLcpl84gHvPntVV211bQqPzp6zEOq5dXNL2VNk9cY0kdHGNLtRkSvXBbTvLnb1uumfXxXujt6TIOcFQDWvGfXj4%2fXsyJfTvNXROO6mOJT9%2bERoGSL7AfV8tFVPjG9P75rG7hfAwB3HUL0R59njv4f&Signature=haV26bjGqbuPcg0sywh3h3pwsbZ3WdPy20r2GTax%2b4Or0qVJ9rZiIi4CQToev83N0Iyah%2bi%2btbowVj8Au7HYau43vlSkz%2foQondUYEnkUNHi8PaExLIXZ8vPCVYCWSu%2bbIEHTQh%2fOiGFNRFL47o7eGfdFoc87rmHcTWrxbJyO9BdiHT%2fVvG6h5LjtD%2fk1YbR0ZcMwnJlIujnaYVJ8mp9kc908vsG4Jp8yyUD8f1R09TXjgEGV9oExOjcOHcZf6KDwfp6vRKGXjhaBAivdIbHzlCUsfSjrJIukuif6ng6FKvvqBd%2bNh%2fMjoYXIiGcQ%2bSyPTKsnc%2fJvHM0RKIhvByBgOf2G2ieTlnU2aPf5Vwnzo1nTUwI7PVvIWRDfI1d727pDBhK%2f%2fXFDe%2b9nK8BF3MOYdqWE650ISwhPQyQP9d75DhOdG%2fd%2fRp4q8ogjyb%2fv4oy02szfH66Ezlx1elXn7WQsKC41FgyMFmhqvqJsn7In7tgmXXkKIFhJN13bOIDIqXnef8uZsDGYWG8topaYgnCtgVa6KQr9fQxiI9ZmeJ1TpuXG1WDXmGcwZ4U3yq2hGFebliAzhqj9ePgVShwrFTctKifjrMugBdDE8gQLaQXXBSJC0F54gfG9jYUksYwxT9RUfOB%2b0NvVq4lhIxc3n0nO%2fN3AShDG2jRjzdQ5KTsO4c%3d&SigAlg=http%3a%2f%2fwww.w3.org%2f2001%2f04%2fxmldsig-more%23rsa-sha256" id="aspnetForm"> <div> <input type="hidden" name="__VIEWSTATE" id="__VIEWSTATE" value="/wEPDwUKMTY2MTc3NjUzM2Rk" /> </div> <div>Anonymous
October 27, 2014
Are you calling from the same machine ADFS is installed? If so, it will not work because of the loopback check (which you can disable). Short of it, the SAMLRequest seems to be right.Anonymous
October 27, 2014
Character limit, I apologize for having to break it up like this.Anonymous
October 27, 2014
Nope, I am running this from my own machine and targeting the ADFS machine. I was looking to get the SAMLResponse which it just is not giving me in the output.Anonymous
October 27, 2014
I am running the .exe from my own machined and targeting the ADFS server and AWS site. Weird I am not getting that SAMLResponse I need. I should simply just be able to download your code form .exe and run it right?Anonymous
October 27, 2014
Calling from my machine and targeting the ADFS server and AWS relying site I configured. Just doesn't have the SAMLResponse I need to run an API command. I should just be able to download and run the getsaml.exe and target this right, no extra config?Anonymous
June 29, 2015
Thank you for this article, Please advise me how to configure ADFs to Test this code. Thank you.Anonymous
July 12, 2015
I'm new to SSO, ADFS and the like, but unfortunately I got thrown into a project that wants to use their legacy web forms login page but still use the ADFS federation to be able to seamlessly navigate to a partner's site without logging in there as well. Is the idea of this project that I can build a request using the markup obtained by running your tool and then posting that page to achieve the login?Anonymous
July 12, 2015
Tim, Federation is a different protocol that is covered in Windows Identity Foundation (WIF). There are several tutorials on how to do that. This is for SAML-Protocol which is not supported in WIF.Anonymous
July 12, 2015
Rod, I don't/can't use passive federation because the client demands we use their login page. So I am not fixated on using WIF if I cannot use that in addition to using the existing legacy login page. I have not found an example of using active federation in a web forms app either, at least not one that relies upon classes and members of classes that have been deprecated. So if you have any pointers on how I can tweak your code to work in my situation or some other way to accomplish my requirement, I'm all ears.Anonymous
July 12, 2015
The comment has been removedAnonymous
July 12, 2015
Tim, You need to use WS-Trust 1.3 to request a bearer token from ADFS and use this token to call the 3rd-party: leastprivilege.com/.../wcf-and-identity-in-net-4-5-external-authentication-with-ws-trustAnonymous
July 13, 2015
Rod, thanks for the link. I had already found that link. My problem is that the sample code does not compile ( WSTrustChannelFactory no longer has a "Credentials" member, for example) and I am not familiar enough with the inner workings of WS-Trust to determine the current way of accomplishing what the sample code suggests.Anonymous
July 13, 2015
Tim, Right now I am on vacation without a development environment. Post a question to the WIF forum at MSDN so someone can follow up with this. Don't forget to mention your .NET version.Anonymous
December 22, 2015
Where is the authentication? Shouldn't you post the username, password and SAMLResponse to the relying party? I've extracted the contents of the authentication flow between browser -> RP, browser -> ADFS and browser -> RP again with Fiddler and wanted to replicate in code this without the ADFS login form showing. Its a poor man's version of single sign on. Its similar to what you're doing, but its brute force and also could it be a kind of replay attack? What is the Single Sign On solution for Windows7 development using ADFS 3.0?Anonymous
December 23, 2015
Daniel, Password is not passed over, but a NTLM or Kerberos token instead. SAML tokens do not contain a password, only the claims configured for the reliant party (RP). If the RP configuration includes a signing certificate even the claims are encrypted at message level, so Fiddler reverse-engineer is of no use. ADFS does not make a brute force attack any easier. My application (and library) is not getting any data that would not be available to the person authenticating.Anonymous
April 01, 2016
The comment has been removed- Anonymous
October 11, 2017
So did you get this to work? Are you authenticating with ADFS in terms of retrieving specific information our to be authenticated for SSO purposes?We're wanting to use our custom app to authenticate with ADFS for SSO purposes but without actually directing the user to the ADFS IdpInitiatedSignOn.aspx page. From what I've read and tried, this is not possible and the request to authenticate with ADFS to get an SSO token has to originate from the ADFS sign on page...What we're wanting to do:: user signs into our custom app, custom app then authenticates said user to ADFS ("in the background") returning the authenticated token back to our custom app. Now linking to any relying party trust apps connected to ADFS via our custom app the user will already be signed in....We are wanting to due this to to multiple reasons, including: our custom app has multiple audiences, both with AD accounts and those without.. 2. the ADFS sign on page is hardly customizable, wouldn't be able to make it look anything like our custom app login page.
- Anonymous
Anonymous
September 11, 2018
Hi Rodney,Currently working on a project where I need to extract the SAML2 Protocol Response just like you have with your C# code. When i run the downloaded page, either the pre-compiled form program or recompiled on my machine, i get the same issue as "Todd - October 23, 2014" posted. In my instance i can see get several get requests with returned header output (mainly cookie related) and then a heap of html and JavaScript code. No where in the output can i find the SAML Response.Just wondering if you have any ideas of what could be wrong? We are using our internal ADFS setup... Not AWS as Todd was.CheersCraigAnonymous
September 11, 2018
Hi Rodney,Currently working on a project where I need to extract the SAML2 Protocol Response just like you have with your C# code. When i run the downloaded page, either the pre-compiled form program or recompiled on my machine, i get the same issue as "Todd - October 23, 2014" posted. In my instance i can see get several get requests with returned header output (mainly cookie related) and then a heap of html and JavaScript code. No where in the output can i find the SAML Response.Just wondering if you have any ideas of what could be wrong? We are using our internal ADFS setup... Not AWS as Todd was.CheersCraig- Anonymous
September 14, 2018
The code was written for ADFS 2.0 and it does not work on ADFS 3.0.
- Anonymous
Anonymous
September 11, 2018
Hi Rodney, This looks great!!! I am currently working on a project where I need to extract the SAML2 Protocol Response just like you have with your C# code. When i run the downloaded page, either the pre-compiled form program or recompiled on my machine, i get the same issue as "Todd - October 23, 2014" posted. In my instance i can see get several get requests with returned header output (mainly cookie related) and then a heap of html and JavaScript code. No where in the output can i find the SAML Response. Just wondering if you have any ideas of what could be wrong? We are using our internal ADFS setup... Not AWS as Todd was. Cheers Craig- Anonymous
September 13, 2018
Hi Craig_Han,This was designed for ADFS 2.0. If you use ADFS 3.0 it will not work.I will revisit the code at some point to adapt to ADFS 3.0.
- Anonymous