The Security Pyramid
Security is still one of the most prevalent problems in the IT industry. Even though we've been preaching about it for years now, it still dogs today's IT systems. I've been in many client sites to do system reviews or talk about Threat Modeling and secure development, and it never ceases to amaze me how little security is actually in place. More often than not everyone wants security, but no one pushes it. Since I work mostly on the development side of the fence, the reasons I usually hear are: "My manager won't send me to training.", "We're too busy to add that security stuff.", and "We would like to but we don't know how to do it."
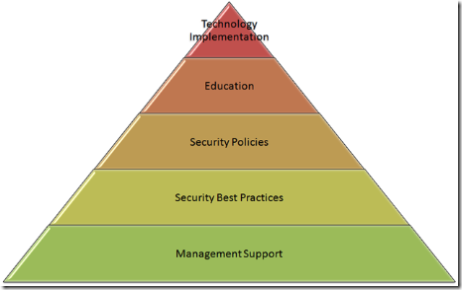
It's very difficult to push the security wheel-barrow up hill. Any good security initiative needs a strong management foundation to get started. That is the basis for implementing security best practices, which are described in security policies. The employees, users, administrators and development teams all need to be educated on these policies. Then, technology can be used to implement some of them.
Below, is my IT Security Pyramid. It illustrates these principals.
Management Support
Any successful security initiative starts with a good foundation of Management Support! Ultimately all the security implications fall to executive management. I'm sure we've all heard a radio or TV announcer say something like "Then the car he was driving struck a tree." What they should have said is either "He lost control of his car and struck a tree" or "He drove the car into a tree". Ultimately, the car ending up wrapped around the tree is the drivers fault. Ultimately, if there is a security breech at a company, it is the executive managements fault since they are the designated driver for the company.
I'm lucky enough to work for a company that has a very 'switched on' set of executives. They knew this several years ago and did something about it. Almost everyone know's of Bill Gates' famous "Drop Everything And Fix Security" email. The very top of the management tree took action and now Microsoft in and industry leader in IT Security. Think what you want, but all of the real statistics demonstrate that fact.
Many times security initiatives have failed because management didn't provide, or demonstrate support for them. So people ignored them, or pushed them aside for more 'visible' things. If a supervisor decides to do something, and enforces some inconvenient policy on people, if there isn't a manager supporting it, it very quickly dissolves into some blob of corpora-goo that slithers away into some dusty corner to die. But if senior management demonstrate to their staff the benefits and backing of a good security initiative, people will follow their lead.
Security Best Practices
I can hear it now, "But Rocky, it's not that simple, we don't know where to start!", yes my children it is a big task, but fear not for we are not alone. Many have gone before us, and through their benevolent wisdom have left behind, 'Best Practices' (cue the angelic choir).
As we are so fond of reminding people about crypto, 'Don't re-invent the wheel'. You don't have to go on a huge 5 year long research quest to discover how to do these things. There are volumes of books, whitepapers, checklists, and punch cards already made that describe exactly what to do. There are documentation templates, processes, software applications, and a plethora of consulting agencies just dying to be used and abused for your security pleasure. Please use them.
My team is an example of this. At Microsoft we realized that we have been pouring a lot of time, money, and people into researching just how to fix these things. We established internal teams to turn this knowledge into guidance, the SDL and SDL-IT, and consult with our internal developers on how to secure their software. Then a very bright person realized that our customers could really benefit from this knowledge as well. So the ACE Services team was created to take all the best practices we've developed over the past 5 or 6 years, and offer the same services to our customers that we provide to internal development teams. We have training and consulting on Threat Modeling, SDL-IT, Application Security and code reviews. Even if you don't like us, I don't care, ask someone you to like to help you, but please ask!
Security Policies
Policies are how Management spells out it's plans, and desires for a good IT Security practice. Executive management are rarely coders and administrators and therefore, need to spell out what they want in policies. We don't need to dream tem up from scratch either. There are already many policies templates around that are based on many years of paranoia and best practices from small companies to military organizations. This is a good thing. We can base our policies on existing, proven ones that have already seen the rough side of the tracks. Policies work on several levels, Education, and Beat Stick.
Policies are designed to inform people of the proper creation, management, use, care and feeding of IT systems. They are designed to be very clear as to what should be done, how to do it, and what happens if it isn't done. Everyone needs to be made aware of these policies. Like many an ISO compliance officer have seen, Policies need to be available for anyone with the proper permissions to access and read. Awareness of the corporate policies will at least bring things to people's minds that they may not have thought of before.
Now, just because people are aware of and have read a policy, doesn't mean that they will actually follow it. That's where Dr. Jeckyl Policy turns into Mr. Hyde Beat Stick.
The second, and sometimes more important aspect of policies is that they give you a leg to stand on in court. If you do not have policies in place to enforce good practices, then when push comes to shove the guilty party can plead ignorance and they win. If however, you have policies in place, and people are made aware of them and agree that they have read them, then at the very least you can get them on violation of corporate policy, and fire them. You may even be able to take them to court for damages if their actions lead to a sever security breach. With the growing threat of malicious insiders, this can save the corporate bacon.
Education
One of the most important things to do once you've begun building your pyramid, is to educate your staff. I get a kick out of doing lunch session during my consulting engagements for the staff. I get up there, and I show them how some basic attacks work and how dangerous this stuff can be. They get all pale faced and start calling the administrators. :-) They may not understand how the attack works, but they know that it's bad.
This little bit of knowledge may be enough to stop a social engineering attack, phishing attack, or virus from screwing up your day. With education comes awareness, and if they are doing something and hesitate for that split second and think "Wow, this might be one of those bad things they told us about, maybe I shouldn't do this", it's paid for itself.
Another aspect of education is making people realize why these nasty policies exist. Make them aware that security problems are expensive, and if bad enough can bring down the whole company. Empower them to help stop IT Security problems by making them aware. Give people a sense of pride that they are doing something to help stop the infectious spread of viruses. Make them part of the cure, not a hurdle in it's implementation.
Technology Implementation
When it comes right down to it, the actual technology is a rather small part of the security picture. Sure, it's probably the most expensive part, and it's the part with the cool flashing lights. There are more things written about implementing security technology that I could ever mention, so you can check them for the details. Overall technology is just there to enable educated users to comply with policies that were based on best practices that management used to make the company a better corporate citizen.
So I challenge you to see if you can wake your management up to the fact that it all starts with them. They are driving the car, and there are plenty of trees.
Wanna chat to me about this, look me up at Tech Ed!