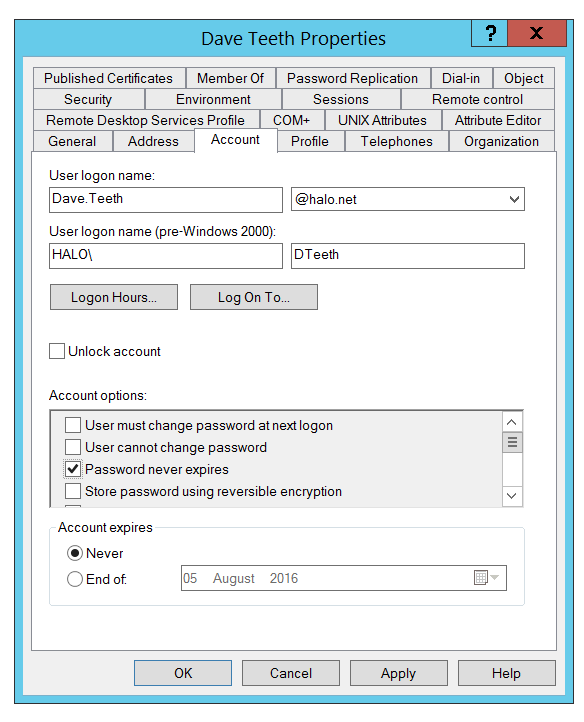
Security Focus One Liner: AD Privileged User and Password Doesn't Expire
I get to perform security assessments against Active Directory. It's always fascinating.
There's a check that lists privileged users that are configured to not expire their password.
Now, a proportion of flagged accounts are Service Accounts, but, there's sometimes human-associated administrative accounts listed. This poor administrative practice still happens... after all these years of Active Directory, and after all these years of high-profile compromises. It's an easy one to fix and monitor.
If you're not already actively monitory this scenario, here's some PowerShell to provide an insight into your own exposure.
#Loop through each domain in the forest
(Get-ADForest).Domains | ForEach-Object {
#Find objects configured with admincount = 1 and password set to not expire
$Findings = Get-ADUser -Filter {(AdminCount -eq 1) -and (PasswordNeverExpires -eq $true)} -Server $_ -ErrorAction SilentlyContinue
#If $Findings is populated, export to CSV
if ($Findings) {
#Get short domain name
$DomainName = (Get-ADDomain -Identity $_).Name.ToUpper()
$Findings | Export-Csv -Path ".\$($DomainName)_ADMIN_AND_DONT_EXPIRE_PASSWORD.csv"
} #End of if ($Findings)
} #End of ForEach-Object
A simple filter on Get-ADUser does the work for us, and if you're interested in learning more about AdminCount -eq 1, have a look here.