More on Get-Acl with Active Directory
In June I posted about searching Active Directory for principals that have the "Write Members" permission on a Distribution List.
I had a follow-up question, from an internal source, about deciphering each Access Control Entry (ACE) returned by Get-Acl against the Active Directory PS drive. I thought I'd convey the same information to the outside world.
First up, let's dump the ACL for our distribution group from the Active Directory PS drive:
(Get-Acl -Path "AD:CN=Distribution Group,OU=Groups").access
I'm going to pick out two ACEs:
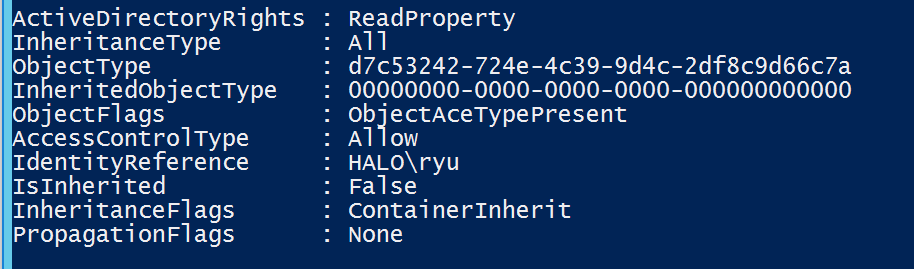
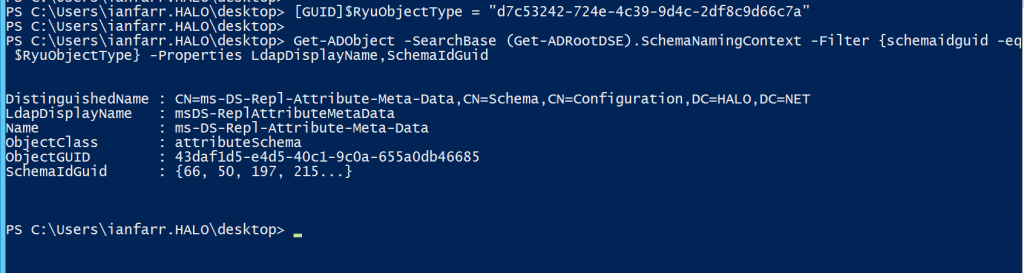
The first is a ReadProperty, i.e. read permission, for a user called HALO\ryu... but what can Ryu actually read? Here's where we need to look up the ObjectType (SchemaIDGuid) in the Schema partition:
#ObjectType / SchemaIdGuid
[GUID]$RyuObjectType = "d7c53242-724e-4c39-9d4c-2df8c9d66c7a"
Get-ADObject -SearchBase (Get-ADRootDSE).SchemaNamingContext -Filter {schemaidguid -eq $RyuObjectType} -Properties LdapDisplayName,SchemaIdGuid
So... Ryu can read the reapplication metadata of the distribution list... very interesting!
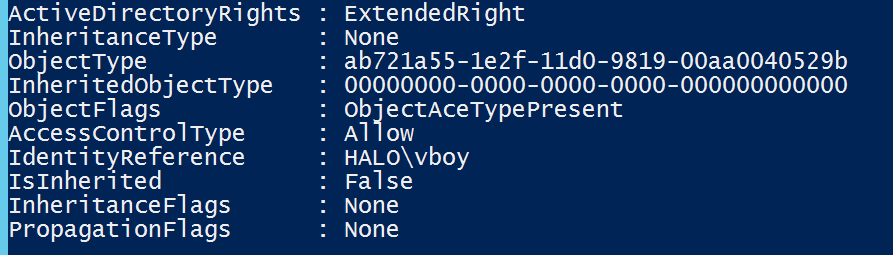
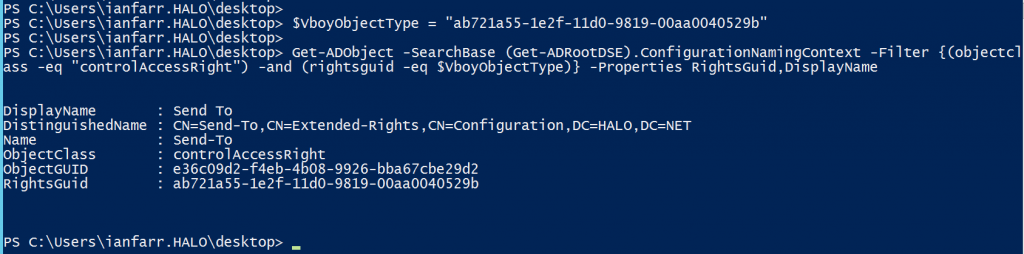
Now, for the second ACE, that of the Vault Boy (HALO\vboy). As the ActiveDirectoryRights are ExtendedRight, this tells me that I need to use a different method to understand the permission, specifically looking up the RightsGuid in the Configuration partition.
#ObjectType / RightsGuid
$VboyObjectType = "ab721a55-1e2f-11d0-9819-00aa0040529b"
Get-ADObject -SearchBase (Get-ADRootDSE).ConfigurationNamingContext -Filter {(objectclass -eq "controlAccessRight") -and (rightsguid -eq $VboyObjectType)} -Properties RightsGuid,DisplayName
So... Vault Boy has the extended right of Send To... nothing of concern for a distribution list.
"How do we see all Extended Rights?", someone asks. Well, I wrote this post previously:
Use PowerShell to List Active Directory Extended Rights
Here's a little snippet to capture all Extended Rights and the corresponding RightsGuid:
Get-ADObject -SearchBase (Get-ADRootDSE).ConfigurationNamingContext -LDAPFilter "(&(objectclass=controlAccessRight)(rightsguid=*))" -Properties RightsGuid,DisplayName | ForEach-Object {
$RightsGuid = [pscustomobject]@{
Name = $_.Name
RightsGuid = [GUID]$_.RightsGuid
DisplayName = $_.DisplayName
}
[array]$ExtendedRightsGuids += $RightsGuid
}
$ExtendedRightsGuids
And, finally, here's another snippet to capture all SchemaIdGuids:
Get-ADObject -SearchBase (Get-ADRootDSE).SchemaNamingContext -LDAPFilter "(schemaidguid=*)" -Properties LdapDisplayName,SchemaIdGuid | ForEach-Object {
$SchemaGuid = [pscustomobject]@{
Name = $_.LdapDisplayName
SchemaIdGuid = [GUID]$_.SchemaIdGuid
}
[array]$TotalGuids += $SchemaGuid
}
$TotalGuids
Comments
- Anonymous
November 19, 2017
Hi,Thank you the great articles on ACE.Is there a means for "Unexpire-Password" extended right be added to AD?Regards