Part 2: Windows Server 2012 R2 AD FS - Federated Web SSO
This is Part 2 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution using Windows Server 2012's R2 AD FS role and the Web Application Proxy. In this part I will deploy CONTOSO's and FABRIKAM's domain controllers (AD DS), certificate services (AD CS), and DNS records. In case you missed it:
Here is Part 1 - Overview
Topology
The following topology highlights in yellow the two servers that will be built for this part and where they fit into the overall topology. If you wish to see the full topology click here.
Deploy CONTOSO Active Directory Domain Services (AD DS), Active Directory Certificate Services (AD CS), DNS
- Deploy Windows Server 2012 R2 AD DS and DNS
- Deploy a Windows Server 2012 R2 workgroup server and configure the IP addess, subnet mask, hostname, and DNS servers. For the purposes of this series the information will be as follows:
- Hostname: CONT-DC01
- IP Address: 192.168.30.2
- Subnet Mask: 255.255.255.0
- DNS Servers: 127.0.0.1
- Reboot the server after changing the name
- Enter the following PowerShell command from an elevated PowerShell window: Add-WindowsFeature ad-domain-services -IncludeManagementTools
- Enter the following PowerShell command from an elevated PowerShell window: Install-ADDSForest -DomainName contoso.com -InstallDNS. For more information on deploying a domain controller using PowerShell click here.
- The server will reboot. After the reboot it should be a domain controller in a new forest called contoso.com.
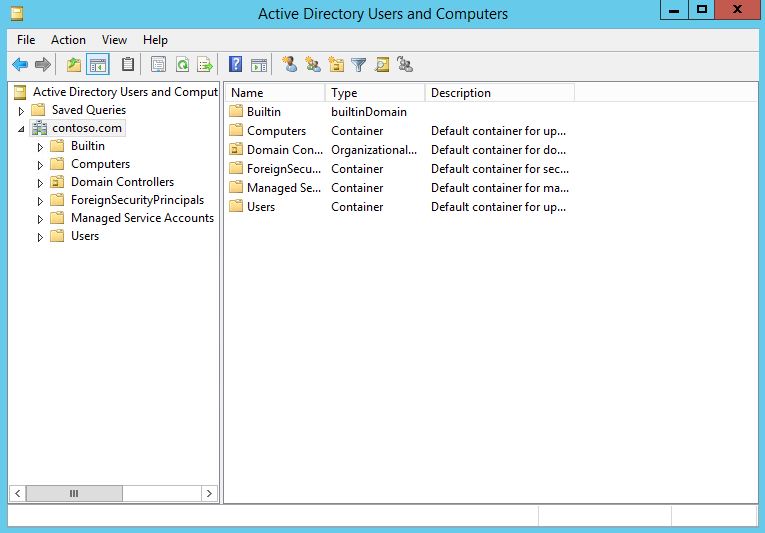
- Log into the domain controller after the reboot and go to Start > type dsa.msc to verify that the Active Directory Install was successful. The results should appear as shown in the following Figure.
- Install Active Directory Certificate Services (AD CS)
- Log into CONT-DC01 and type the following PowerShell command from an elevated window: Add-WindowsFeature Adcs-Cert-Authority -IncludeManagementTools
- Type the following PowerShell command from an elevated window: Install-AdcsCertificationAuthority -CAType EnterpriseRootCA. For more information on deploying a Certificate Authority from PowerShell click here.
- Go to Start > type certsrv to open the Certificate Authority management console. The results should appear as shown in the following Figure.
- Expand contoso-CONT-DC01-CA > Certificate Templates > Right click > Manage
- Right click the Web Server template > Properties > Security Tab
- Click Add > Type Domain Computers > OK.
- Give Domain Computers Read and Enroll permissions then click OK
- Create DNS Records
The following DNS records are needed for CONTOSO to properly resolve the planned CONTOSO Federation Services and SharePoint services.
- Log into CONT-DC01 and type the following PowerShell commands from an elevated window:
- Add-DnsServerResourceRecordA -ZoneName contoso.com -Name www -IPV4Address 192.168.30.4
- Add-DnsServerResourceRecordA -ZoneName contoso.com -Name sts -IPV4Address 192.168.30.7
- Verify that the entries were properly created by typing the following commands from a PowerShell or Command window. The results should appear as shown in the following Figure:
- nslookup -type=a www.contoso.com
- nslookup -type=a sts.contoso.com
Note: In the previous figure both records timed out for part of the query, this is due to the fact that a reverse DNS zone was not created and PTR records were not added for the forward records. If you wish to eliminate the DNS request timed out error, you will need to create a reverse lookup zone and add PTR records for the A records. Since PTR records are not needed for the Federation Service, I will skip the steps necessary to create the reverse zone and PTR records.
Deploy FABRIKAM Active Directory Domain Services (AD DS), Active Directory Certificate Services (AD CS), DNS
- Deploy Windows Server 2012 R2 AD DS and DNS
- Deploy a Windows Server 2012 R2 workgroup server and configure the IP addess, subnet mask, hostname, and DNS servers. For the purposes of this series the information will be as follows:
- Hostname: FABR-DC01
- IP Address: 192.168.30.20
- Subnet Mask: 255.255.255.0
- DNS Servers: 127.0.0.1
- Reboot the server after changing the name
- Enter the following PowerShell command from an elevated PowerShell window: Add-WindowsFeature ad-domain-services -IncludeManagementTools
- Enter the following PowerShell command from an elevated PowerShell window: Install-ADDSForest -DomainName fabrikam.com -InstallDNS. For more information on deploying a domain controller using PowerShell click here.
- The server will reboot. After the reboot it should be a domain controller in a new forest called fabrikam.com.
- Log into the domain controller after the reboot and go to Start > type dsa.msc to verify that the Active Directory Install was successful. The results should appear as shown in the following Figure.
- Install Active Directory Certificate Services (AD CS)
- Log into FABR-DC01 and type the following PowerShell command from an elevated window: Add-WindowsFeature Adcs-Cert-Authority -IncludeManagementTools
- Type the following PowerShell command from an elevated window: Install-AdcsCertificationAuthority -CAType EnterpriseRootCA. For more information on deploying a Certificate Authority from PowerShell click here.
- Go to Start > type certsrv to open the Certificate Authority management console. The results should appear as shown in the following Figure.
- Expand fabrikam-FABR-DC01-CA > Certificate Templates > Right click > Manage
- Right click the Web Server template > Properties > Security Tab
- Click Add > Type Domain Computers > OK.
- Give Domain Computers Read and Enroll permissions then click OK
- Create DNS Records
The following DNS records are needed for FABRIKAM to properly resolve the planned FABRIKAM Federation Services and SharePoint services.
- Log into FABR-DC01 and type the following PowerShell commands from an elevated window:
- Add-DnsServerResourceRecordA -ZoneName fabrikam.com -Name www -IPV4Address 192.168.30.22
- Add-DnsServerResourceRecordA -ZoneName fabrikam.com -Name sts -IPV4Address 192.168.30.35
- Verify that the entries were properly created by typing the following commands from a PowerShell or Command window. The results should appear as shown in the following Figure:
- nslookup -type=a www.fabrikam.com
- nslookup -type=a sts.fabrikam.com
Note: In the previous figure both records timed out for part of the query, this is due to the fact that a reverse DNS zone was not created and PTR records were not added for the forward records. If you wish to eliminate the DNS request timed out error, you will need to create a reverse lookup zone and add PTR records for the A records. Since PTR records are not needed for the Federation Service, I will skip the steps necessary to create the reverse zone and PTR records.
Conclusion
You now have two forests one named contoso.com and one named fabrikam.com along with the DNS records and certificate services needed to support SharePoint 2013 and AD FS. In the upcoming posts additional services will be deployed including SQL, SharePoint 2013, AD FS, and the Web Application Proxy.
Comments
- Anonymous
January 01, 2003
Thanks - Anonymous
August 29, 2014
Overview
The purpose of this series is to walk you through step-by-step from start to finish setting - Anonymous
September 02, 2014
This is Part 3 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 11, 2014
Thanks alot - Anonymous
September 16, 2014
This is Part 4a of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 16, 2014
This is Part 4b of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 25, 2014
This is Part 5a of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 25, 2014
This is Part 5b of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
February 16, 2015
This is Part 6a of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 26, 2015
This is Part 6b of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 27, 2015
This is Part 7 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 28, 2015
This is Part 8 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 28, 2015
This is Part 9 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution