Audit Alert Scenarios: System Center Operations Manager (OpsMgr) 2007 R2
The other day I was asked to assist with implementing the scenarios below:
- Scenario 1: Alert for changes to the ‘Domain Admin’ group membership
- Scenario 2: Alert when the Audit Policy is changed (Default Domain or Domain Controller)
- Scenario 3: Alert when xx number of unsuccessful logons occur within nn hours
- Scenario 4: Account locked out x number of times in a 24 hour period
I’ve decided to blog about it as I am likely to need it again in the future and it may help someone else as well!
Scenario 1: Alert for changes to the ‘Domain Admin’ group membership
Prerequisites
- OpsMgr agent installed on domain controllers (more info...)
- Notification Channel, Subscriber & Subscription configured (more info...)
- Enable ‘Audit Account Management’ for the ‘Default Domain Controllers Policy’ (more info... and how to)
Step-by-Step
Create an ‘Alert Generating Rule’ as below:
(more info... and how to)
Note: Rules are used here instead of monitors as monitors will affect Parent Monitors while rules will not.
1.
<table>
<colgroup>
<col style="width: 50%" />
<col style="width: 50%" />
</colgroup>
<tbody>
<tr class="odd">
<td><p>Operations Console > Authoring > Rules > Create a new rule</p>
<p><strong>Note</strong></p>
<p>Create a new destination management pack if required.</p>
<p>Next</p></td>
<td><p><a href="https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/nzdse/WindowsLiveWriter/AuditAlertScenariosSystemCenterOperation_F6F4/image_6.png"><img src="https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/nzdse/WindowsLiveWriter/AuditAlertScenariosSystemCenterOperation_F6F4/image_thumb_2.png" title="image" alt="image" width="544" height="484" /></a></p></td>
</tr>
<tr class="even">
<td>Select > ‘Windows Domain Controller’ <strong>Note</strong> Un-tick the ‘Rule is enabled’ checkbox. Next</td>
<td><p><a href="https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/nzdse/WindowsLiveWriter/AuditAlertScenariosSystemCenterOperation_F6F4/image_8.png"><img src="https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/nzdse/WindowsLiveWriter/AuditAlertScenariosSystemCenterOperation_F6F4/image_thumb_3.png" title="image" alt="image" width="547" height="484" /></a></p></td>
</tr>
<tr class="odd">
<td>Select Security as the log name. Next</td>
<td><p><a href="https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/nzdse/WindowsLiveWriter/AuditAlertScenariosSystemCenterOperation_F6F4/image_10.png"><img src="https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/nzdse/WindowsLiveWriter/AuditAlertScenariosSystemCenterOperation_F6F4/image_thumb_4.png" title="image" alt="image" width="545" height="484" /></a></p></td>
</tr>
<tr class="even">
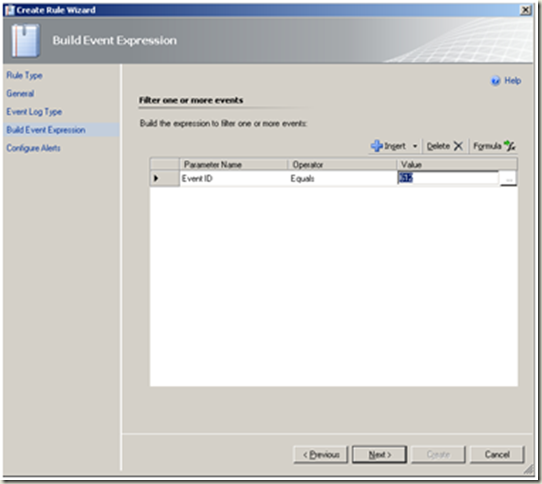
<td><p>Configure the event expression as depicted in the image.</p>
<p>Next</p>
<p> </p></td>
<td><p>We will use the following event id’s in this section:</p>
<p>632 – A member was added to a global group.</p>
<p>633 – A member was removed from a global group.</p>
<a href="https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/nzdse/WindowsLiveWriter/AuditAlertScenariosSystemCenterOperation_F6F4/image_2.png"><img src="https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/nzdse/WindowsLiveWriter/AuditAlertScenariosSystemCenterOperation_F6F4/image_thumb.png" title="image" alt="image" width="547" height="484" /></a>
<p><strong>Note there are two ways to do this:</strong></p>
<ol>
<li>Use Parameter 3 in screenshot above (more info <a href="https://support.microsoft.com/kb/299475/en-us">here</a> and <a href="https://support.microsoft.com/kb/301677/en-us">here</a>) or;</li>
<li>‘Use parameter name not specified above’ and ‘EventDescription’.</li>
</ol>
<p>Method 1 is preferred.</p></td>
</tr>
<tr class="odd">
<td>Change the severity and priority settings as required. Create</td>
<td><a href="https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/nzdse/WindowsLiveWriter/AuditAlertScenariosSystemCenterOperation_F6F4/image_4.png"><img src="https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/nzdse/WindowsLiveWriter/AuditAlertScenariosSystemCenterOperation_F6F4/image_thumb_1.png" title="image" alt="image" width="544" height="484" /></a></td>
</tr>
<tr class="even">
<td> </td>
<td><p><strong>Next steps:</strong></p>
<ol>
<li>Enable newly created rule for ‘all objects of class: Windows Domain Controller’ by using an override. (<a href="https://technet.microsoft.com/en-us/library/bb309719.aspx">more info...</a>)</li>
<li>Create a notification subscription for the rule. (<a href="https://technet.microsoft.com/en-us/library/dd440890.aspx">more info...</a>)</li>
</ol></td>
</tr>
</tbody>
</table>
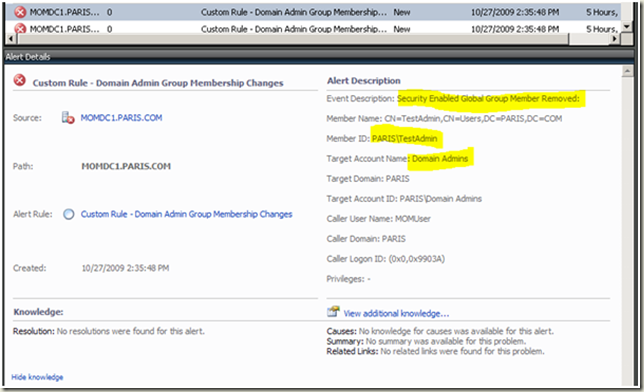
Alert example
 |
Scenario 2: Alert when the Audit Policy is changed (Default Domain or Domain Controller)
Prerequisites
- OpsMgr agent installed on domain controllers (more info...)
- Notification Channel, Subscriber & Subscription configured (more info...)
- Enable ‘Audit Policy Change’ for ‘Default Domain Policy’ (more info... and how to)
Step-by-Step
Create an ‘Alert Generating Rule’ as below:
(more info... and how to)
Operations Console > Authoring > Rules > Create a new rule Note Create a new destination management pack if required. Next |
 |
| Select > ‘Windows Domain Controller’ Note Un-tick the ‘Rule is enabled’ checkbox. Next |  |
| Select Security as the log name. Next | 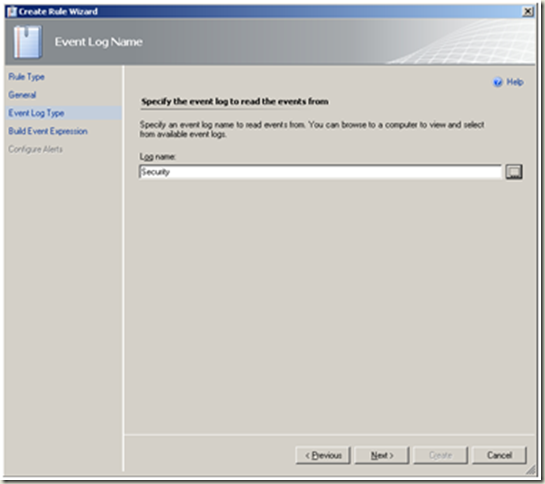 |
Configure the event expression as depicted in the image.
Next |
We will use the following event id in this section: |
| Change the severity and priority settings as required. Create | 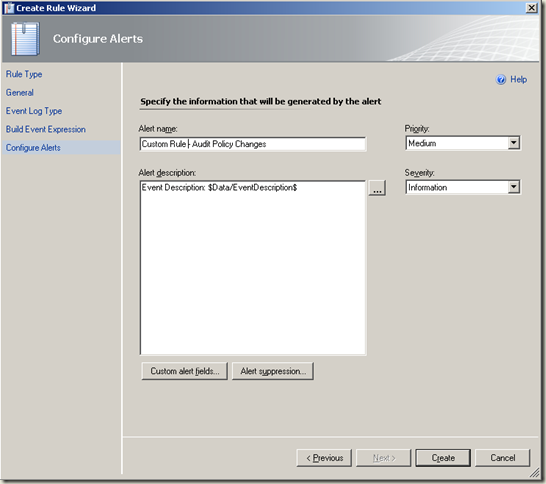 |
Next steps:
|
Alert example
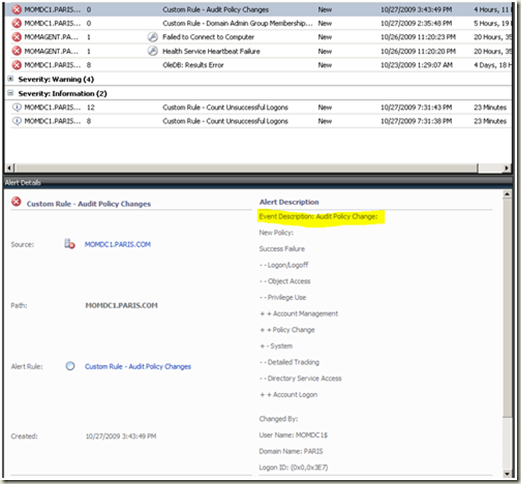 |
Scenario 3: Alert when xx number of unsuccessful logons occur within nn hours
Disclaimer: This is a complex scenario and I am not sure that my proposed solution is the simplest...it works though! :-)
The following is relatively easy to do though:
· Create an alert for each Unsuccessful Logon.
· Create an alert for each Unsuccessful Logon for a specific user.
· Create one suppressed alert (i.e. repeat count is increased) for all Unsuccessful Logons.
· Create one suppressed alert per user account that attempted an unsuccessful logon. Add 1 to the ‘RepeatCount’ for each subsequent occurrence in a 24 hour period. Create a rule to auto-resolve all related active alerts. Create a rule to send hourly notifications when the ‘RepeatCount’ exceeds xx. I documented only this scenario below.
Prerequisites
- OpsMgr agent installed on domain controllers (more info...)
- Notification Channel, Subscriber & Subscription configured (more info...) – not strictly speaking necessary for the proposed solution.
- Enable ‘Audit Account Logon Events’ for ‘Default Domain Controller Policy’ (more info... and how to)
Step-By-Step
(Create one suppressed alert per user account that attempted an unsuccessful logon. Add 1 to the ‘RepeatCount’ for each subsequent occurrence in a 24 hour period. Create a rule to auto-resolve all related active alerts. Create a rule to send hourly notifications when the ‘RepeatCount’ exceeds xx.)
Create an ‘Alert Generating Rule’ as below:
(more info... and how to)
Operations Console > Authoring > Rules > Create a new rule
Note Create a new destination management pack if required.
Next |
 |
| Select > ‘Windows Domain Controller’ Note Un-tick the ‘Rule is enabled’ checkbox. Next | 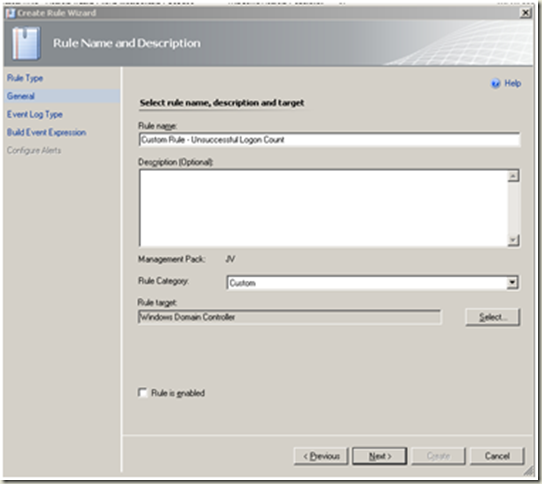 |
| Select Security as the log name. Next | 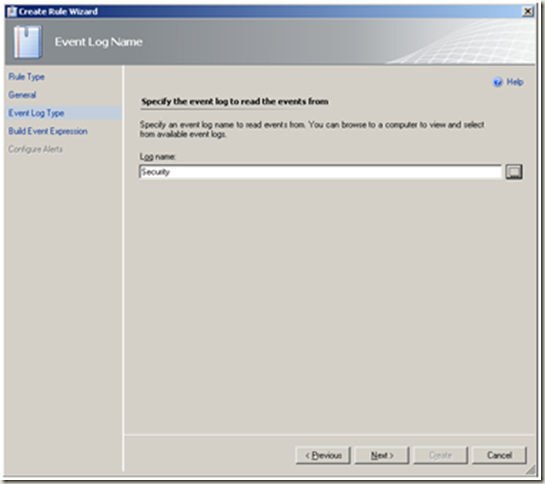 |
Configure the event expression as depicted in the image.
Next |
We will use the following event id in this section: 675 - Preauthentication failed. This event is generated on a Key Distribution Center (KDC) when a user types in an incorrect password. 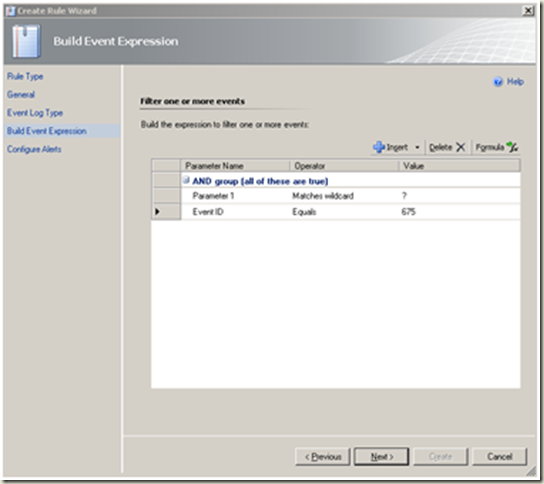 |
| Change the severity and priority settings as required. Alert Suppression | 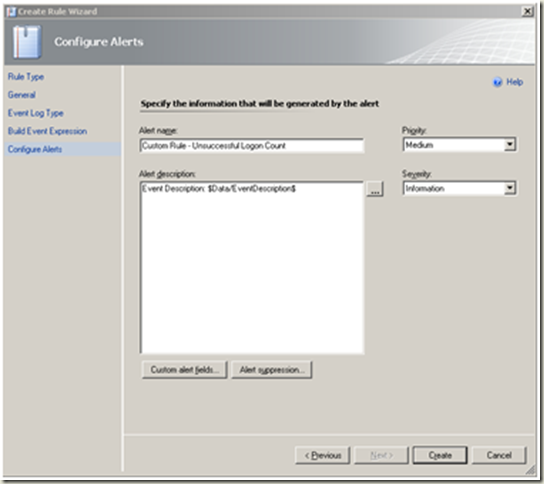 |
| Configure the alert suppression fields as depicted in the image. Ok | 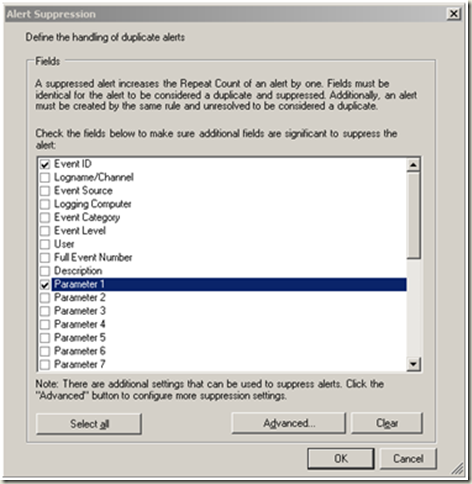 |
| Create | 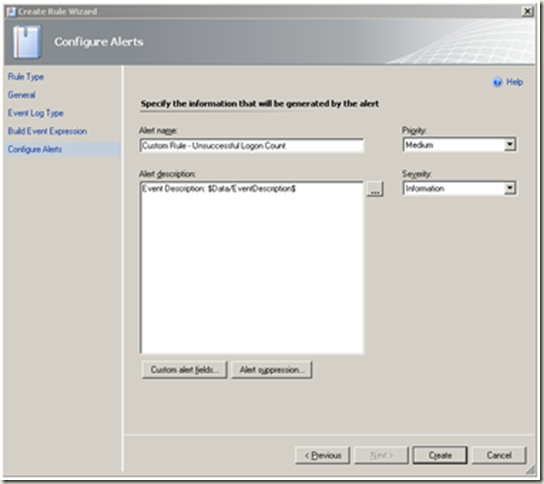 |
Next steps: Enable newly created rule for ‘all objects of class: Windows Domain Controller’ by using an override. (more info...) |
Alert example
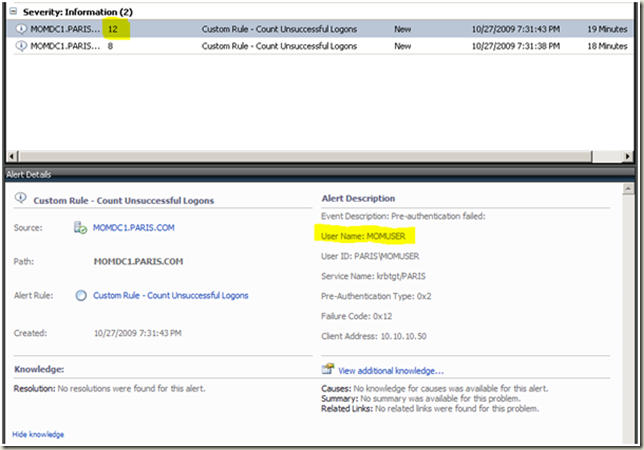 |
Create a rule to resolve all unsuccessful logon alerts on a daily basis
Operations Console > Authoring > Rules > Create a new rule
Note Create a new destination management pack if required. Next |
 |
| Select > ‘Root Management Server’ as the rule target. Note Un-tick the ‘Rule is enabled’ checkbox. Next | 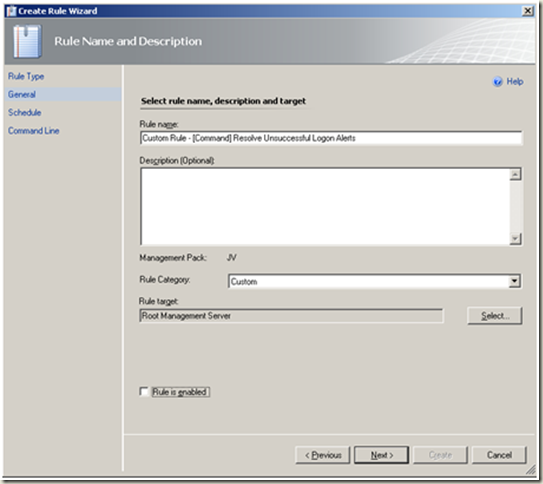 |
| Define the schedule as required. | 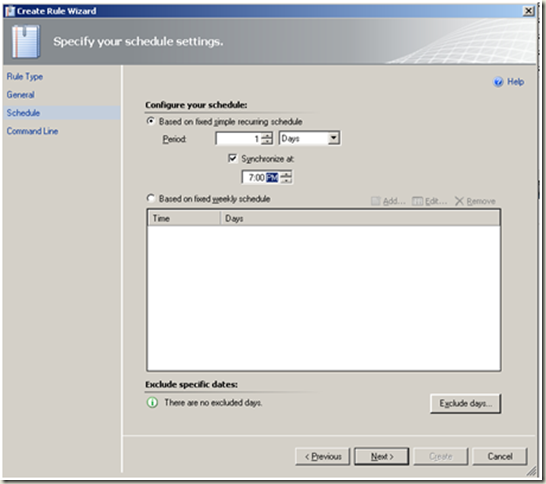 |
| Create a directory on the root management server i.e. c:\scripts > Save the following powershell script in the directory. Note Change the script as required i.e. path to OpsMgr startup.ps1 and rule name. | # ResolveUL.ps1 # Author: Johan Vosloo # Date: 29-10-2009 # Note: The name i.e. "Custom
Rule - Count Unsuccessful Logons" below must match the rule name that is used to create the surpressed alert. # Script requires Microsoft.EnterpriseManagement.OperationsManager.ClientShell.Startup.ps1 to be in "c:\Program Files\System Center Operations Manager 2007" - Change as required. add-pssnapin "Microsoft.EnterpriseManagement.OperationsManager.Client"; Set-Location "c:\Program Files\System Center Operations Manager 2007"; .\Microsoft.EnterpriseManagement.OperationsManager.ClientShell.Startup.ps1; get-alert | where {($_.Name -eq "Custom Rule - Count Unsuccessful Logons") -and ($_.ResolutionState -eq "0")} | resolve-alert -comment "CLOSE daily informational alerts" | out-Null; |
| Configure command line execution settings as depicted in the image. Create | 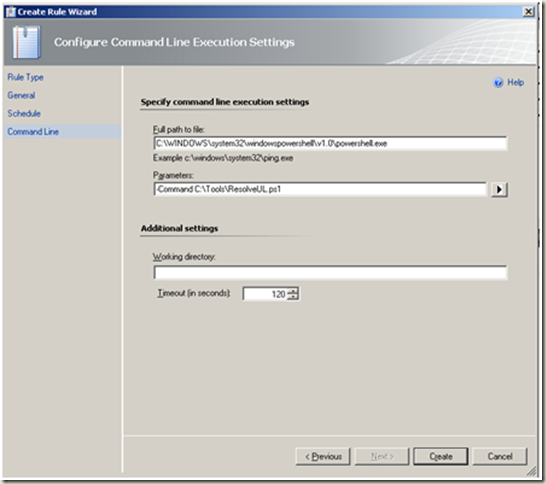 |
Next steps: Enable newly created rule for ‘all objects of class: Root Management Server’ by using an override. (more info...) |
Create a rule to send notification when alert ‘RepeatCount’ equal xx within nn hours
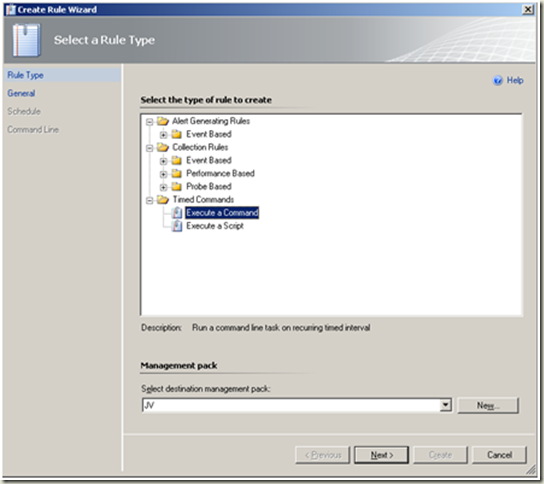
Operations Console > Authoring > Rules > Create a new rule
Note Create a new destination management pack if required. Next |
 |
| Select > ‘Root Management Server’ as the rule target. Note Un-tick the ‘Rule is enabled’ checkbox. Next | 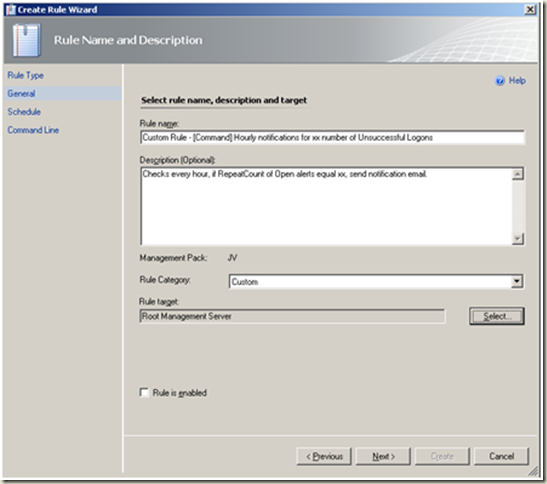 |
| Define the schedule as required. | 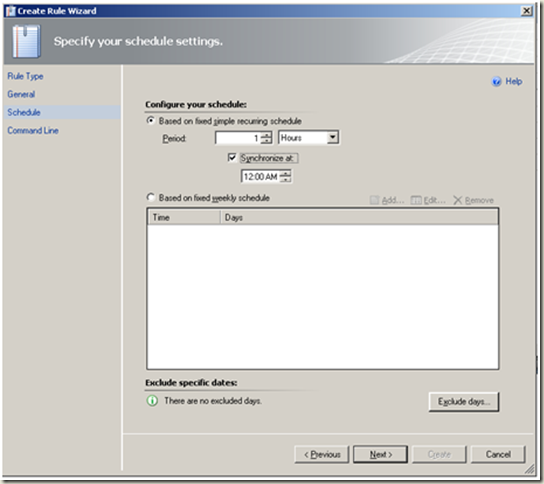 |
| Create a directory on the root management server i.e. c:\scripts > Save the following powershell script in the directory. Note Change the script as required i.e. path to OpsMgr startup.ps1 and rule name. | # NotifyULogon.ps1 # Author: Johan Vosloo # Date: 29-10-2009 # Credit: Adapted from https://contoso.se/blog/?p=290 # Script requires Microsoft.EnterpriseManagement.OperationsManager.ClientShell.Startup.ps1 to be in "c:\Program Files\System Center Operations Manager 2007" - Change as required.# Change the Notification Recipient below.$Recipient = security@paris.com;add-pssnapin "Microsoft.EnterpriseManagement.OperationsManager.Client";Set-Location "c:\Program Files\System Center Operations Manager 2007";.\Microsoft.EnterpriseManagement.OperationsManager.ClientShell.Startup.ps1;# The name i.e. "Custom Rule - Count Unsuccessful Logons" below must match the rule name that is used to create the surpressed alert.$alertdata = get-alert | where {($_.Name -eq "Custom Rule - Count Unsuccessful Logons") -and ($_.ResolutionState -eq "0") -and ($_.RepeatCount -gt "3") -and ($_.CustomField1 -lt 0)} | Foreach { $_.Id; $alert_id = $_.Id; $alert_name = $_.Name; $alert_TimeRaised = $_.TimeRaised; $alert_Desc = $_.Description; $alert_RepeatCount = $_.RepeatCount; $alert_Severity = $_.Severity; $alert_priority = $_.Priority; $alert_MonitoringObjectDisplayName = $_.MonitoringObjectDisplayName; If ($alert_RepeatCount -gt 3) { # Send Email If ($alert_ID -eq $NULL) {"Alert ID is NULL, dont send e-mail";} ELSEIF ($recipient -eq $NULL) {"Recipient is NULL, dont send e-mail";} ELSE { # Change the from address and the mailserver below $smtpServer = "mailserver.paris.com"; $smtpClient = new-object system.net.mail.smtpClient($smtpServer); $From = notification@paris.com; $To = $recipient; $Title = "Notification from Ops Mgr. $alert_name $alert_Severity"; $Body = @" Notification from Operations Manager 2007 RepeatCount: $alert_RepeatCount Raised: $alert_TimeRaised Name: $alert_name Object: $alert_MonitoringObjectDisplayName Priority: $alert_Priority Severity: $alert_Severity Description: $alert_description"@ $SmtpClient.Send($From,$To,$Title,$Body); # Update Custom Field 1 on the alert. Else the script will send multiple e-mails for the same alert $alert = Get-Alert | where {$_.Id -eq $Alert_ID}; $alert.Customfield1 = "Ops Mgr has sent e-mail to $recipient"; $alert.Update(""); }; };}; |
| Configure command line execution settings as depicted in the image. Create | 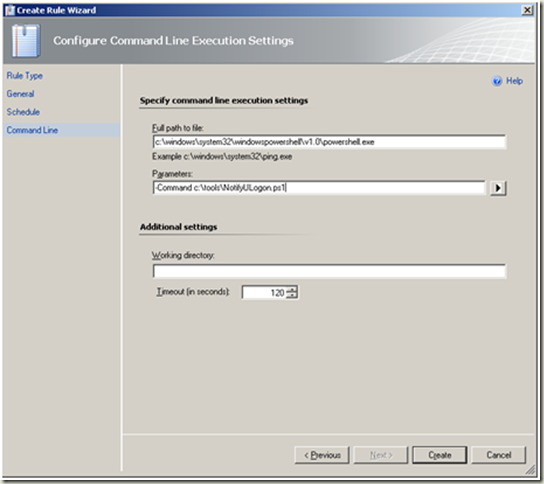 |
Next steps: Enable newly created rule for ‘all objects of class: Root Management Server’ by using an override. (more info...) |
Scenario 4: Account locked out x number of times in a 24 hour period
Disclaimer: This is another complex scenario and I am again not sure that my proposed solution is the simplest...it works though! J
Prerequisites
- OpsMgr agent installed on domain controllers (more info...)
- Notification Channel, Subscriber & Subscription configured (more info...)
- Enable ‘Audit Account Management’ for the ‘Default Domain Controllers Policy’ (more info... and how to)
Step-By-Step
(Create one suppressed alert per locked out user account. Add 1 to the ‘RepeatCount’ for each subsequent occurrence in a 24 hour period. Create a rule to auto-resolve all related active alerts. Create a rule to send hourly notifications when the ‘RepeatCount’ exceeds xx.)
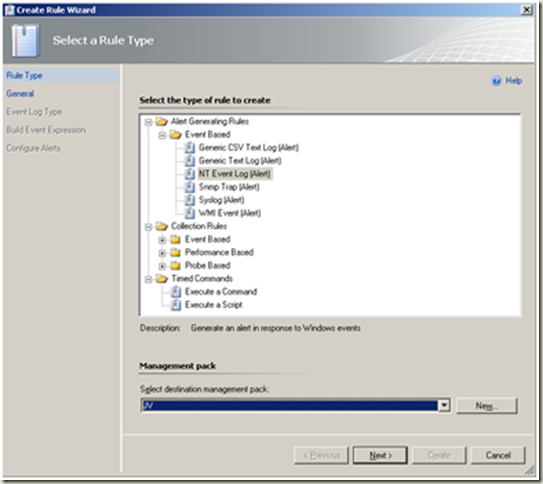
Create an ‘Alert Generating Rule’ as below:
(more info... and how to)
Operations Console > Authoring > Rules > Create a new rule
Note Create a new destination management pack if required. Next |
 |
| Select > ‘Windows Domain Controller’ Note Un-tick the ‘Rule is enabled’ checkbox. Next | 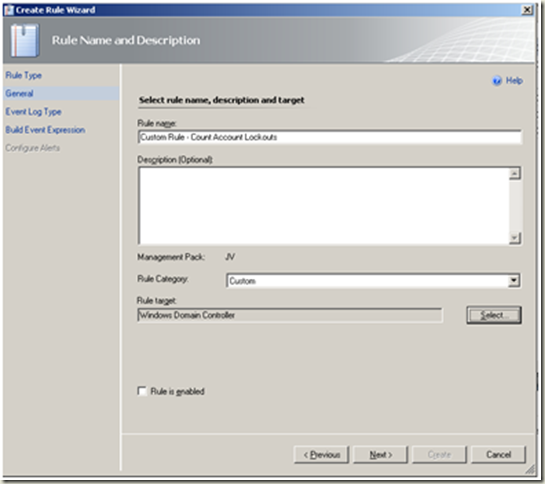 |
| Select Security as the log name. Next | 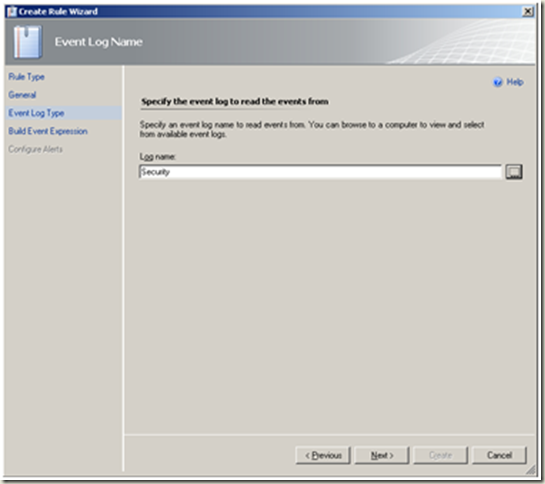 |
Configure the event expression as depicted in the image.
Next |
We will use the following event id in this section: 644 - A user account was auto locked. 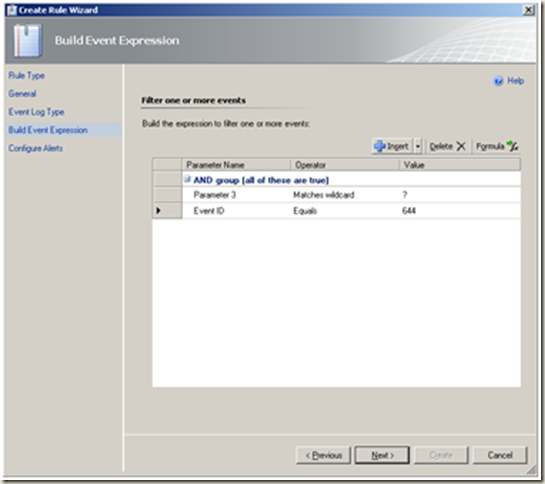 |
| Change the severity and priority settings as required. Alert Suppression | 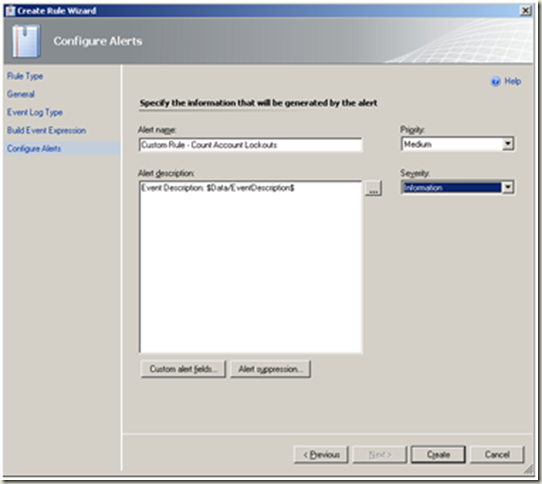 |
| Configure the alert suppression fields as depicted in the image. Ok | 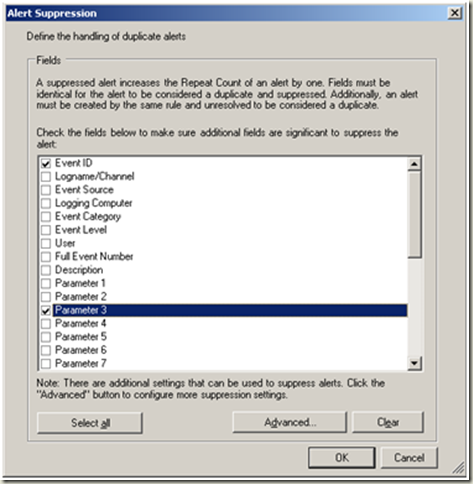 |
| Create |  |
Next steps:
|