Port 3389, Remote Web Workplace, and the Terminal Services Gateway
You may have noticed we no longer call out port 3389 when we talk about the ports for EBS and SBS. Why, you might ask? Well, since both Small Business Server 2008 and Essential Business Server 2008 are based off of Windows Server 2008, we 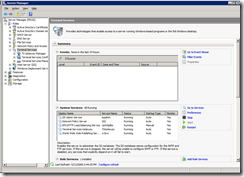 leverage a role known as Terminal Services Gateway. What this allows us to do is via SSL (443) connect to the Terminal Services Gateway (TSG) and then more securely connect to an internal RDP session.
leverage a role known as Terminal Services Gateway. What this allows us to do is via SSL (443) connect to the Terminal Services Gateway (TSG) and then more securely connect to an internal RDP session.
We use this technology when you connect to machines in your environment when you use Remote Web Workplace. For those of you who like to know more of the workings keep reading.
In the SBS world this role is enabled on your first server. I've added a picture of the Server Manager MMC so you can see the role and the services it creates and/or works against. I'll dig a little more into the RDP client settings further down for those that want to see it done manually. All you need to do is publish the 443 port on your network firewall and users can  connect via TSG to any connected machine that supports RDP on your network.
connect via TSG to any connected machine that supports RDP on your network.
In the EBS world, things work a little different with three servers. We place the TSG on the Messaging Server as we share many of these resources with Remote Web Workplace and Exchange. In order to present this to the outside world we create a Forefront Threat Management Gateway (TMG) publishing rule on the Security Server. The Terminal Services Gateway role shares this listener with Outlook Anywhere (formerly RPC/HTTPS) and requires the remote.<domainname>.com certificate.
At this point an external user could connect to the remote.<domainname>.com listener on port 443. TMG checks the certificate and bridges the SSL connection to the Messaging server. Once connected to the Messaging server we do another local policy check to prevent potential internal misuse, and follow best-practice of a least access security environment. Once connected to TSG you're able to connect more securely to other machines on your network via the standard RDP port 3389.
Sound complicated? A little bit, remember all of this happens for you when you use Remote Web Workplace out of the box. I like to think of it this way. All of the traffic is sent via the SSL port secured using a trusted certificate to your  Security server. The Security server checks to make sure you're connection isn't doing anything naughty, it then passes it to the Messaging server which runs the RDP session on your behalf. Easy!
Security server. The Security server checks to make sure you're connection isn't doing anything naughty, it then passes it to the Messaging server which runs the RDP session on your behalf. Easy!
Let's look at the manual RDP client setting to make this all work. When setting up the session click advanced and then settings which I've highlighted in the red box. This will bring up the TSG settings and  you then enter the FQDN for your environment (this is by default the RWW address). Remember you'll need to have your certificate installed as it requires this to connect.
you then enter the FQDN for your environment (this is by default the RWW address). Remember you'll need to have your certificate installed as it requires this to connect.
Once you've set that up you can enter the name of the machine you want to connect to. Hit connect and you should pop up the RDP window of that machine via the TSG!
So there you have it. The nuts and bolts behind the Connect to button on Remote Web Workplace, the reason why you don't see 3389 in our port mappings any more, and a cool way to connect to machines in your environment from outside the firewall in a more secure fashion.
Comments
- Anonymous
January 01, 2003
No in fact the separation is logical when you break it down this way.
- The edge device (security server) ensures that connection is valid and meets the predetermined rule set. Specifically is the certificate valid, is it going to a valid service, and is the connect expected.
- Following the above passing, the traffic then moves to the TSG which then applies trusted resource policy to ensure the right devices/connections are enabled/permitted. Think of this as the external TS connections trusted landing.
- 3389/RDP is not designed for external publishing, but internally in a trusted network it is readily available. Using TSG (SSL/RDP) and the above configuration reduces complexity, and ensures better security.
- Anonymous
March 09, 2009
Nick, So now RWW in EBS relies on two servers to be up in order for the connection to work? Doesn't this setup make troubleshooting more complex? Why would such a choice be made? Thanks, Jeff Loucks