Step by Step: Configuring CRM 2013 Internet facing deployment (IFD)
This blog covers all the steps you have to follow to configure Internet facing deployment (IFD) for a CRM 2013 Onpremise deployment
Before we proceed here are a few details of the environment.
CRM Server 2013 Installed on Windows Server 2012
ADFS 2.1 on a separate box on Windows Server 2012
Important:
With AD FS 2.0, you had to download and install the AD FS 2.0 software to deploy your AD FS server infrastructure.
ADFS 2.1 was released to Windows Server 2012 as part of the operating system and therefore can be installed as a Role from Server Manager.
Prerequisites
- Install and configure Dynamics CRM 2013
- Install and configure IIS on the ADFS Server
- Purchase the appropriate certificates for the IFD configuration
- You will need to choose the type of certificate that will work best in your environment. Most people have chosen to use a wildcard for their external domain so in my example it would be *.fabrikam.com so I can use it for all the URLs. If you were to get a SAN certificate you would need to know all of your URLs now and future (if you were going to add more orgs)
- If ADFS will be on the same server as CRM, ADFS will need to be on the default website using the default port so CRM will need to use something else.
I will break down the entire process into 5 major sections.
Section 1: Binding Certificates
Section 2: Setup ADFS
Section 3: DNS Configuration
Section 4: Configuring CRM server for claims based authentication
Section 5: Configuring CRM server for IFD
Alright, let’s get this started.
Section 1: Binding Certificates
After you have obtained and installed a certificate, the certificate must be bound to the default Web site before you can use AD FS
On the ADFS Server
Step1: Open IIS Manager and in the Connections pane, expand the Sites node in the tree, and then click the Default Web Site
Step2: In the Actions pane, click Bindings.
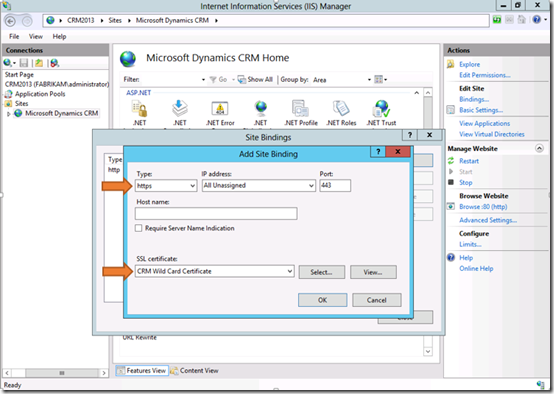
Step3: In the Site Bindings dialog box, click Add.
Under Type, select https.
Under SSL certificate, select your SSL certificate and then click OK and then Close
On the CRM 2013 Server
When enabling claims-based authentication, the Dynamics CRM Server 2013 Web site must be accessible via HTTPS. You must bind your SSL certificate to the Dynamics CRM Server 2013 Web site.
Step4: Open IIS Manager and in the Connections pane, expand the Sites node in the tree, and then click the Microsoft Dynamics CRM Web site
Step5: In the Actions pane, click Bindings.
Step6: In the Site Bindings dialog box, click Add.
Under Type, select https.
Under SSL certificate, select your SSL certificate and then click OK and then Close
Step 7: The CRMAppPool account and the Microsoft Dynamics CRM encryption certificate
The CRMAppPool account will need to have rights to the certificate being used for the CRM website. If the application pool is running as Network Service as in the example then you will need to give Network Service read rights to that certificate.
You can use IIS Manager to determine what account was used during setup for the CRMAppPool account. In the Connections pane, click Application Pools, and then check the Identity value for CRMAppPool.
Launch the MMC console and go to File menu and select Add-Remove Snap In
Select Certificates from the available snap-ins and click Add
Select Computer Account and click Next in the Certificates Snap-In window.
Click Finish on the next window and then click Ok
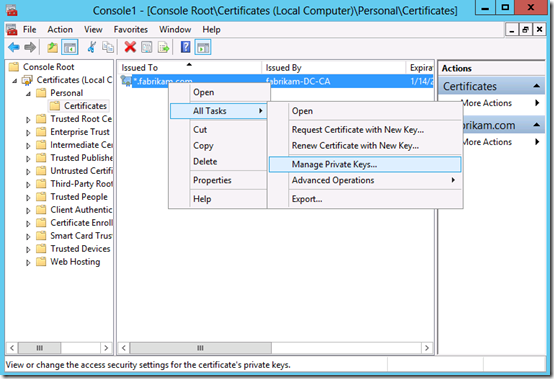
Expand Certificates->Personal->Certificates ->Right click on Manage Private keys
Add the identity which is running the CRM application pool and give it read permissions and then Ok
In my case its Network Service.
You are now done configuring the certificates.
Section 2: Setup ADFS
Step1: Launch Server manager and click on Add roles and features
Step2: Click Next on the first page in the wizard
Step3: Select Role-based or feature based installation and click Next
Step4: Select a server from the server pool and click Next
Step5: Select Active Directory Federation Services
Step6: Click on Add Features and then click Next
Step7: Continue to click on Next until you reach the Confirmation page and then click Install.
Now that we have installed ADFS, lets go ahead and configure it.
Step8: Launch Administrative tools and then select ADFS management.
Step9: Click on ADFS Federation Server Configuration Wizard and on the welcome page select Create a new Federation Service
Step10: Select Stand Alone or Farm Deployment.
Depending upon your requirement you can choose the appropriate option. The wizard explains each of the options.
I will choose Stand-alone federation server.
Step11: Specify the Federation Service Name
Step12: Shows you the summary of what is about to be installed. Click Next to continue
Step13: Wait for the configuration process to complete and click the Close button.
Section3: DNS Configuration
You should configure your domain records in DNS so the various Dynamics CRM Server endpoints resolve correctly.
Step1: Open DNS Manager by clicking Start, pointing to Administrative Tools, and then clicking DNS.
Step2: Expand Forward lookup Zones and then select the <Domain name>.com and create the below CNAME records.
Name |
|
|
| auth | Point it to the machine that as CRM 2013 installed |
This record will be used by the AD FS server when retrieving the Microsoft Dynamics CRM IFD federationmetadata.xml file |
| Dev | Point it to the machine that contains the discovery web service |
Microsoft Dynamics CRM Discovery Web Service domain |
| Internalcrm | Point it to the machine that as CRM 2013 installed |
Internal URL used to access Microsoft Dynamics (for example, internalcrm.fabrikam.com). |
<CRM organization name> |
Point it to the machine that as CRM 2013 installed |
External URL used to access Microsoft Dynamics - Web Application Server domain (for example, orgname.contoso.com). |
| ADFS | Point it to the machine that has ADFS installed |
AD FS 2.1 server |
Here is a screen shot of all the DNS records created
You must also set your firewall to allow inbound traffic on the ports used for Dynamics CRM Server 2013 and AD FS 2.1
Section 4: Configuring CRM server for claims based authentication
Once ADFS is setup and the certificate/s are bound to the websites, you will need to prepare CRM for Claims Authentication.
On The CRM Server
Step1: Set Microsoft Dynamics CRM Server 2013 binding to HTTPS and configure the root domain Web addresses
Start the Deployment Manager=>Actions pane=>Properties=>Web Address tab=>Binding Type select HTTPS.
You can now enter your internal URL for CRM. This will be the URL that users can use if they want to access CRM within the network without being prompted for credentials. Click on 'Apply'
Step2: In the Deployment Manager console tree, right-click Microsoft Dynamics CRM, and then click Configure Claims-Based Authentication. Click Next on the Welcome page
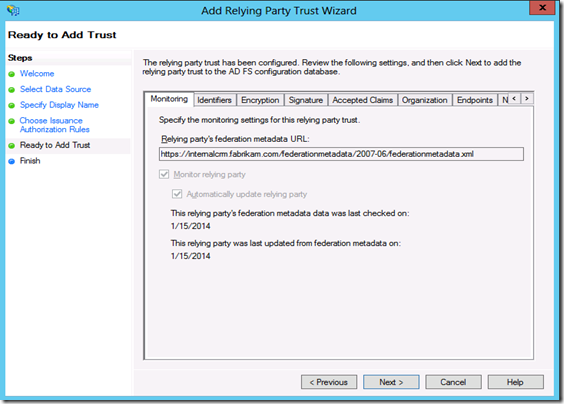
Step3: On the Specify the security token service page, enter the Federation metadata URL, such as https://adfs.fabrikam.com/federationmetadata/2007-06/federationmetadata.xml.
This data is typically located on the Web site where the Active Directory Federation Services (AD FS) 2.1 is running. To verify the correct URL, open an Internet browser by using the URL to view the federation metadata. Verify that no certificate-related warnings appear.
Step4: On Specify the encryption certificate page, specify the encryption certificate
Step5: On the System Checks page, review the results, perform any steps required to fix problems, and then click Next.
Step6: On the Review your selections and then click Apply page, verify your selections, and then click Apply.
Step7: Click View log file and scroll to the bottom and copy the Federation metadata URL to avoid typos
You will need to use the federation metadata URL that was created during Claims-Based Authentication configuration in CRM to setup the Relying Party Trust in ADFS 2.1
On The ADFS Server
After enabling claims-based authentication, the next step is add and configure claims provider trusts and relying party trusts in AD FS 2.1
Step8: Start AD FS 2.1 Management. In the Navigation Pane, expand Trust Relationships, and then click Claims Provider Trusts. Under Claims Provider Trusts, right-click Active Directory, and then click Edit Claims Rules.
Step9: In the Rules Editor, click Add Rule, In the Claim rule template list, select the Send LDAP Attributes as Claims template, and then click Next
Step10: Create the following rule
Claim rule name: UPN Claim Rule (or something descriptive)
Attribute store: Active Directory
LDAP Attribute: User Principal Name
Outgoing Claim Type: UPN
Click Finish, and then click OK to close the Rules Editor
After you enable claims-based authentication, you must configure Dynamics CRM Server 2013 as a relying party to consume claims from AD FS 2.1 for authenticating internal claims access.
Step11: Start AD FS Management. On the Actions menu located in the right column, click Add Relying Party Trust. In the Add Relying Party Trust Wizard, click Start.
Step12: On the Select Data Source page, click Import data about the relying party published online or on a local network, and then type the URL you copied earlier from the log file. So that will be https://internalcrm.fabrikam.com/FederationMetadata/2007-06/FederationMetadata.xml. Verify that no certificate-related warnings appear by opening it in the browser.
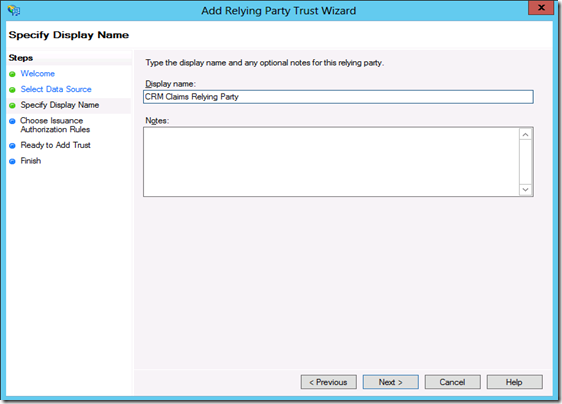
Step13: On the Specify Display Name page, type a display name, such as CRM Claims Relying Party, and then click Next.
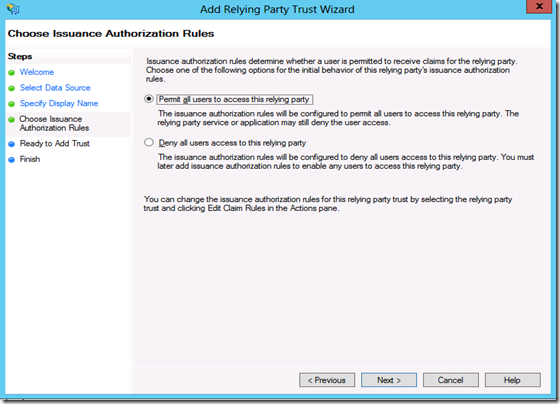
Step14: On the Choose Issuance Authorization Rules page, leave the Permit all users to access this relying party option selected, and then click Next.
Step15: On the Ready to Add Trust page, click Next, and then click Close.
Step16: If the Rules Editor appears, click Add Rule. Otherwise, in the Relying Party Trusts list, right-click the relying party object that you created, click Edit Claims Rules, and then click Add Rule.
Step17: In the Claim rule template list, select the Pass Through or Filter an Incoming Claim template, and then click Next.
Step18: Create the following Rule #1
Claim rule name: Pass Through UPN (or something descriptive)
Incoming claim type: UPN
Pass through all claim values
Click Finish.
Step19: In the Rules Editor, click Add Rule, in the Claim rule template list, select the Pass Through or Filter an Incoming Claim template, and then click Next
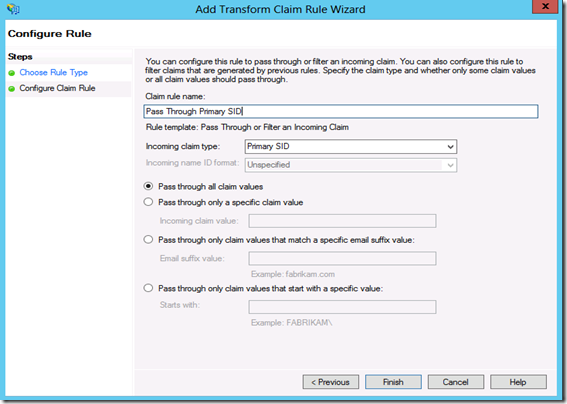
Step20: Create the following Rule #2
Claim rule name: Pass Through Primary SID (or something descriptive)
Incoming claim type: Primary SID
Pass through all claim values
Click Finish
Step21: In the Rules Editor, click Add Rule. In the Claim rule template list, select the Transform an Incoming Claim template, and then click Next.
Step22: Create the following rule #3
Claim rule name: Transform Windows Account Name to Name (or something descriptive)
Incoming claiming type: Windows account name
Outgoing claim type: Name
Pass through all claim values
Click Finish, and when you have created all three rules, click OK to close the Rules Editor.
So now we have claims setup for CRM.
In both Servers (ADFS and CRM) go to IE -> tools -> IE options -> security-> local intranet -> sites -> add internal URL and ADFS URL (https://internalcrm.fabrikam.com and https://adfs.fabrikam.com ) This would have to done on any machines that are accessing the internal access points so that ADFS and CRM can pass those Kerberos tickets without being prompted for credentials.
Type the internal url in CRM server: https://internalcrm.fabrikam.com see how it hits the ADFS and then launches the CRM page.
Section 5: Configuring CRM server for IFD
Now you are ready to configure Internet-Facing Deployment within the Microsoft Dynamics CRM 2013 Deployment Manager.
On The CRM Server
Step1: Start the Deployment Manager. In the Deployment Manager console tree, right-click Microsoft Dynamics CRM, and then click Configure Internet-Facing Deployment. Click Next.
Step2: Enter the URLs for the Web Application Server Domain, Organization Web Service Domain and the Discovery Web Service Domain and click on the Next button.
Important things to consider
. Specify domains, not servers.
· If your deployment is on a single server or on servers that are in the same domain, the Web Application Server Domain and Organization Web Service Domain will be identical.
· The Discovery Web Service Domain must be a resolvable host name and not a root domain. For example: dev.fabrikam.com.
· The Discovery Web Service domain must not match an organization's fully qualified domain name (FQDN). For example, the Discovery Web Service Domain should not be: orgname.fabrikam.com.
· The domains must be valid for the SSL certificate's common name or names.
· The domains must be set to resolve correctly in DNS to your Microsoft Dynamics CRM servers holding the server roles.
· The domains can be in a different domain than the domain which the Microsoft Dynamics CRM servers reside.
Step3: In the Enter the external domain where your Internet-facing servers are located box, type the external domain information where your Internet-facing Microsoft Dynamics CRM Server 2013 servers are located, and then click Next.
The domain you specify must be a sub-domain of the Web Application Server Domain specified in the previous step. By default, "auth." is pre-pended to the Web Application Server Domain.
Important things to consider
· The external domain is used by the AD FS server when retrieving the Microsoft Dynamics CRM IFD federationmetadata.xml file.
· The external domain must not contain an organization name.
· The external domain must not contain an underscore character (“_”).
· The external domain must be valid for the SSL certificate's common name or names.
· The external domain must be set to resolve correctly in DNS to your Microsoft Dynamics CRM server holding the Web Application Server role.
Step4: On the System Checks page, review the results, fix any problems, and then click Next.
Step5: On the Review your selections and then click Apply page, verify your selections, and then click Apply and Finish
Step6: Run the following command at a command prompt: iisreset
On the ADFS Server
After you have enabled IFD on the Microsoft Dynamics CRM Server 2013 you will need to create a relying party for the IFD endpoint on the AD FS server.
Step6: Start AD FS Management. On the Actions menu located in the right column, click Add Relying Party Trust. In the Add Relying Party Trust Wizard, click Start.
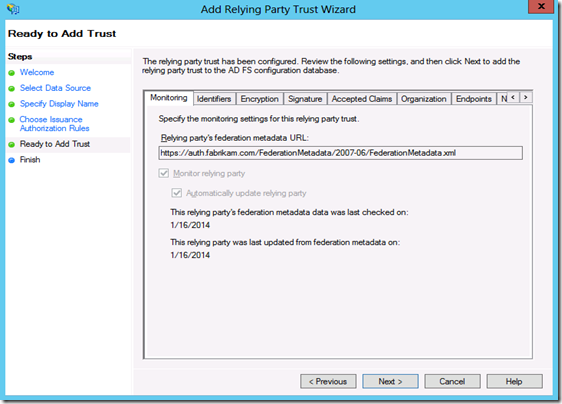
Step7: On the Select Data Source page, click Import data about the relying party published online or on a local network, and then type the URL to locate the federationmetadata.xml file. This federation metadata is created during IFD Setup.
For example, https://auth.fabrikam.com/FederationMetadata/2007-06/FederationMetadata.xml.
Type this URL in your browser and verify that no certificate-related warnings appear.
Step8: On the Specify Display Name page, type a display name, such as CRM IFD Relying Party, and then click Next
Step9: On the Choose Issuance Authorization Rules page, leave the Permit all users to access this relying party option selected, and then click Next.
Step10: On the Ready to Add Trust page, click Next, and then click Close.
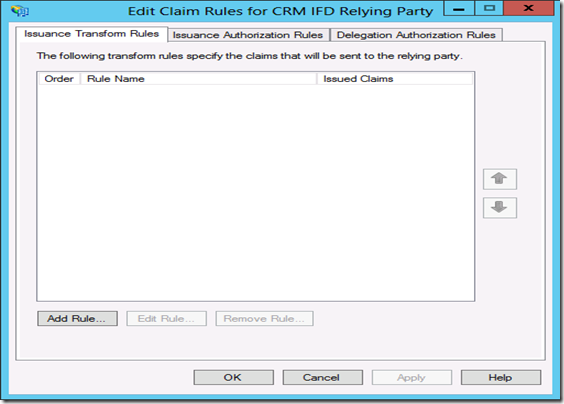
Step11: If the Rules Editor appears, click Add Rule. Otherwise, in the Relying Party Trusts list, right-click the relying party object that you created, click Edit Claims Rules, and then click Add Rule
Step12: In the Claim rule template list, select the Pass Through or Filter an Incoming Claim template, and then click Next.
Step13: Create the following rule#1
Claim rule name: Pass Through UPN (or something descriptive)
Incoming claim type: UPN
Pass through all claim values
Click Finish
Step14: In the Rules Editor, click Add Rule, and in the Claim rule template list, select the Pass Through or Filter an Incoming Claim template, and then click Next
Step15: Create the following rule#2
Claim rule name: Pass Through Primary SID (or something descriptive)
Incoming claim type: Primary SID
Pass through all claim values
Click Finish
Step16: In the Rules Editor, click Add Rule. In the Claim rule template list, select the Transform an Incoming Claim template, and then click Next.
Step17: Create the following rule #3
Claim rule name: Transform Windows Account Name to Name (or something descriptive)
Incoming claim type: Windows account name
Outgoing claim type: Name
Pass through all claim values
Click Finish, and when you have created all three rules, click OK to close the Rules Editor.
Test external claims-based authentication
You should now be able to access Microsoft Dynamics CRM Server 2013 externally using claims authentication. Browse to your Microsoft Dynamics CRM Server 2013 Web site's external address (for example: https://orgname.fabrikam.com). You should see a screen like the following
Sign in and verify that you have external access to Microsoft Dynamics CRM Server 2013
tada….
You have successfully configured Internet facing deployment for Dynamics CRM 2013.
Hope this article was useful.
Comments
Anonymous
January 15, 2014
How does this change for Windows 2012 R2 and ADFS 2.2? A bunch of us are having problems with it, see these threads: community.dynamics.com/.../114317.aspx community.dynamics.com/.../114725.aspx I opened a support ticket with Microsoft to help me get this sorted out but they eventually just told me that CRM 2013 is not supported on Server 2012 R2 and there was nothing they could do. Can you verify this?Anonymous
January 22, 2014
Great info! Can ADFS 2.0 be used with Windows 2012 R2?Anonymous
January 22, 2014
Thanks for the instructions, followed this with a crm2011 ru15 on 2008r2 with adfs 2.1 on 2012. Worked great, thanksAnonymous
February 17, 2014
Thank you! What if I want install two crm environment (for test and production)? When we are configuring IFD on this servers Discovery Web Service Domain will be different but Web Application Server Domain and Organization Web Service Domain the same, correct?Anonymous
February 28, 2014
Great Post. Its steps are very clear and understandable. Thanks for the post.Such types of posts are really rare.Anonymous
March 03, 2014
Really great post, very clear ! Thanks !Anonymous
March 19, 2014
There is an updated whitepaper on CRM 2011 and 2013 IFD. You can download it from here www.microsoft.com/.../details.aspx. This will answer you questions on ADFS on Windows Server 2012R2.Anonymous
April 09, 2014
Hi, great post, however what will happen if users from multiple domains access CRM, having multiple emails (having different exchange servers). How are you going to configure email-router for this scenario ?Anonymous
April 15, 2014
Hi I have followed these instructions but I have hit a road block, I am getting a redirect loop error when trying to access the internalcrm url. (I have installed the ADFS and CRM on the same server using different ports ie: 443 and 444). If I could have some help on what to do to resolve this that would be great. Kind Regards CharlesAnonymous
April 24, 2014
Hi Niran, Great post. We're trying to configure CRM 2013 Claims & IFD but we're having issues. Would you please take a look and see if there's anything you can help us with. social.microsoft.com/.../crm-2013-claims-based-authentication-ifd-configuration-errors-help Thanks. ProgCRMAnonymous
April 24, 2014
Hi Niran Great post. I have configured Internet Facing Deployment for Dynamics CRM 2013 with ADFS 2.1 using SelfSSL and everything configured perfect. Now I can access CRM within Both Server ADFS and CRM with myorgname.dynamicscrm.com but the problem is that I can't access it through another system it showed blank page within same network internally :( What should be the issue?Anonymous
May 04, 2014
Hi , Can i do federation without encrypting the assertions? Is there a way to disable encryption in CRM.Anonymous
May 12, 2014
Really gr8 post..thanks you so much.....Anonymous
May 13, 2014
Hi, I have a question regarding the certificates. I am used the same wild card cert to bind to ADFS IIS and CRM Server IIS which is from godaddy and is *.mydomain.com. When installing the ADFS role it didn't see this certificate. I imported it and then used it. Should I be using a different certificate for the ADFS role, your screenshots seem to imply that you did. So basically when setting up the ADFS role for the SSL Certificate I clicked import --> found the wildcard PKF file I used for IIS. Then it asked for a federation name either *.mydomain.com or mydomain.com. If I try using *.mydomain.com it doesnt work so for Federation service name I selected mydomain.com and for the federation display name I just entered in my company name and it seems to have taken that. Can you let me know if I am doing this correctly?Anonymous
May 14, 2014
An additional note I got through your config guide all the way up until going into CRM and configuring the IFD. However, whenever I try to go to internalcrm.company.com its trying to redirect me to lwgconsulting.com/.../ls <--- there is no sub domain there listed. The Internal domain is crm.lwgconsulting.com. When I open ADFS management and look at CRM Claims relying party and then go to indetifiers it shows just the domainname.com nothing ahead of it like ADFS or CRM. I am not sure where I went wrong but seems like from teh wildcard cert which is *.lwgconsulting.com any assistance would be appreciated, I have never done this before.Anonymous
May 27, 2014
this did not help, As a Newb to Dynamics, I was not able to set my version for external access. There must be something missing about pointing the external domain to the internal server records. Either way its not helped. I need to use a Self-Assigned Cert and only a single virtual machine. This is only for testing, I cannot believe the amount of hassle to just set up external access. Thanks for your efforts, back to research for me.Anonymous
June 17, 2014
Hi Niran, Excellent Post! I've used your posting as a guide for several IFDs and I found it thorough and easy to follow and even a great basis for other IFD complexities like multiple adfs servers.Anonymous
June 18, 2014
Hi Niran, Great post. But my solutions not worked ((. I configured Microsoft Dynamics CRM 2013 (6.0.0.0809 version) and deploy separate ADFS service on Windows server 2012R2, configured claims-based authentication and IFD. All configuration wizards are complete successfully, I have 404 error after logging to CRM 2013 via IFD/ADFS. Please help to solve the problem? Thanks.Anonymous
June 19, 2014
Hi Sergey, I assume you are using Web Application Proxy to publish everything and you are redirected to https://auth.contoso.com after auth. Check article blogs.msdn.com/.../publishing-crm-internet-facing-deployment-using-web-application-proxy-and.aspx BestAnonymous
June 19, 2014
Hi Marcin, I using SonicWALL to publishing stand-alone ADFS server. Thanks.Anonymous
June 28, 2014
The comment has been removedAnonymous
August 14, 2014
We had problemens with authentication between de ADFS server en CRM. I imported the self-signed certificates as trusted now it works.Anonymous
September 09, 2014
Thank you very much for this tutorial! was very helpful for me!. I would like to add that I tried to configure it in Windows 2012 R2 and after few hours I found a PDF in Microsoft webpage to configure IFD and it states in page 32 that "In AD FS in Windows Server 2012 R2, forms authentication is not enabled by default.", I don't know if someone had that authentication issue but I did. PDF link: www.microsoft.com/.../details.aspx Cheers!Anonymous
October 02, 2014
Hi Niran, Great article and thanks for the detailed explanation. Can this be done in Window 2008 R2 ADFS 2.0 Implementation as well? Is there any additional steps we need to be doing to achive this. Please clarify. Also the need of enabling forms authentication. Would be great help if could clarify theseAnonymous
October 08, 2014
You can't write a guide to configure CRM and ADFS in two servers without explain that you have to setup ADFS with a service account, as per you explain ADFS pool account will be Network Services and this will cause future intermittent authentication issues as you explain in one of your KB articles, so very bad for you.Anonymous
October 14, 2014
Jorge - could you elaborate on your note from 9th October? I think I may be on the cusp of solving one of my biggest headaches with your help!Anonymous
October 27, 2014
Can you please clarify why you recommend that internal URLs are used in Deployment Manager for all services? Using internalcrm for all of those will cause the Discovery service to return that as the URL for all services. So if you have a 3rd party or custom app which calls the Discovery Service to find the URL of the other services, as it's supposed to do, then they will all be using the internalcrm address, which presumably wouldn't be desired.Anonymous
December 14, 2014
I am working on configure CRM2013 and ADF2.0 in single VM. relaytrust pary is having connection issue with the CRM. Can you help on this Thanks RajAnonymous
December 18, 2014
Hi, Is there an equivilant tutorial using Windows Server 2008 R2? I thought I could get by with this one, but many of the steps (like the installing of Active Directory Federation Services role) are quite different. :-/ GrahamAnonymous
January 20, 2015
Can someone provide me some clarification on action steps that I need to take in my setup. I currently have CRM 2011 with ADFS and GP 2010 installed all on one server running server 2008 R2 (call is sql_old). I am creating a new environment to take over this current production environment and I have two servers running server 2012 R2. One server is for sql (call it sql1) and the other server is for crm (call it crm1). The old server is going to be turned into a dev environment for future testing. So currently ADFS is set up for CRM with SSL cert, etc. What is the best practice when installing the new CRM server? CRM is already on there, so I am in the process of installing ADFS, but it's asking me if I want to add the new server to the current ADFS farm or not. Should I do that considering that the old server will not be serving the same SQL CRM database anyway. My gut says to create a new ADFS farm for the new server.Anonymous
February 23, 2015
Clarification on steps. This is a blog that provides a similar step by step for IFD with CRM 2015. The environment is a single server with the exception of AD that runs externally. www.interactivewebs.com/.../how-to-set-up-crm-2015-ifd-on-windows-2012-and-adfs-3-0Anonymous
June 14, 2015
The comment has been removedAnonymous
July 08, 2015
Great info, I have been struggling with configuring Single Sign On reading this article pointed me in the right direction by creating an internalcrm url.Anonymous
January 10, 2016
can you check same with 2016? and use http://orgname.fabrikam.com [http in the url] - we recently did the configuration but getting windows login popup if explicitly mention http in the url. NOTE : https://....... Working fine and redirecting to ADFS sign in page.Anonymous
January 25, 2016
Hi! thanks for the article but i did not get the ADFS management console i don't know why?Anonymous
February 07, 2016
I have my AD server with domain.local and my SSL is with domain.com, example (AD server abc.local and SSL certificate having xyz.com. Please confirm whther we can configure MS CRM 2015 having above scenario.