Using OMS to Alert on Azure Service Outages
If you are unable to alert from the Azure Portal, or simple wish to have all your alerting from one source, consider leveraging OMS (Operations Management Suite). With the free tier option (7 days of day retained) there is no additional cost!
Azure Service events are logged automatically in the Azure Portal –> Monitoring –> Activity Log (only incidents believed to impact your subscription(s) will be listed). This article will show you how to use OMS to review and alert on these events. 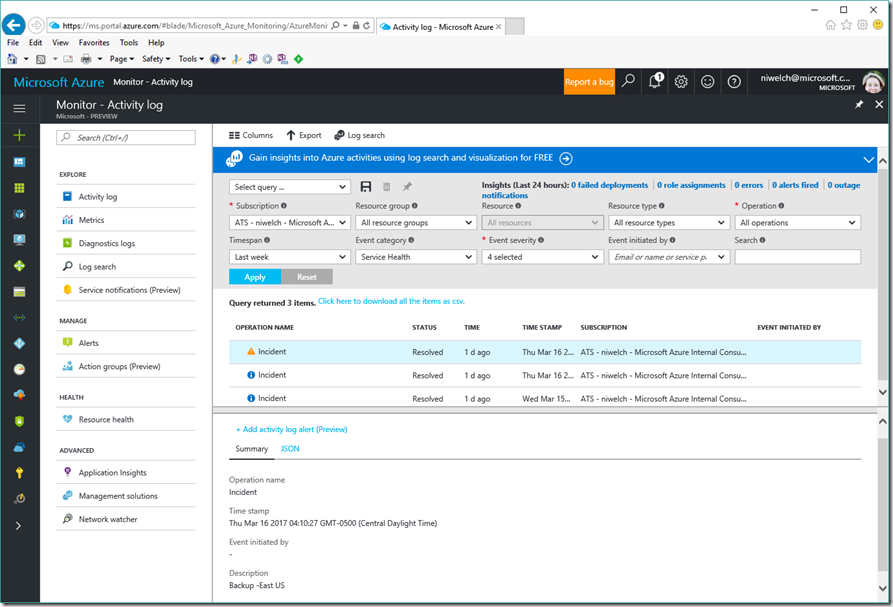
Setup OMS (if you do not already have an OMS workspace)
1. Create a new workspace - https://docs.microsoft.com/en-us/azure/log-analytics/log-analytics-get-started#2-create-a-workspace
- select the free pricing tier unless you have further plans for OMS
Configure OMS to Pull the Azure Activity Logs
1. Add the Activity Logs Analytics solution - https://docs.microsoft.com/en-us/azure/log-analytics/log-analytics-get-started#3-add-solutions-and-solution-offerings (only steps 1-4 are required)
Setup Alerting
1. Open the OMS portal (URL varies based on your cloud)
2. Click on Log Search
3. In the query window, enter: Type=AzureActivity Category=ServiceHealth
-
- This will looks for alerts from the Azure Activity logs of type Service Health. This is how Azure Service outages are categorized in the Azure Activity Logs
- it is OK if no results are returned. That just means there were no Azure Service Incidents that impacted your subscription the time range.
4. Click Alert in the top left
5.Configure the alerting options (see https://docs.microsoft.com/en-us/azure/log-analytics/log-analytics-alerts-creating#create-an-alert-rule for more details) 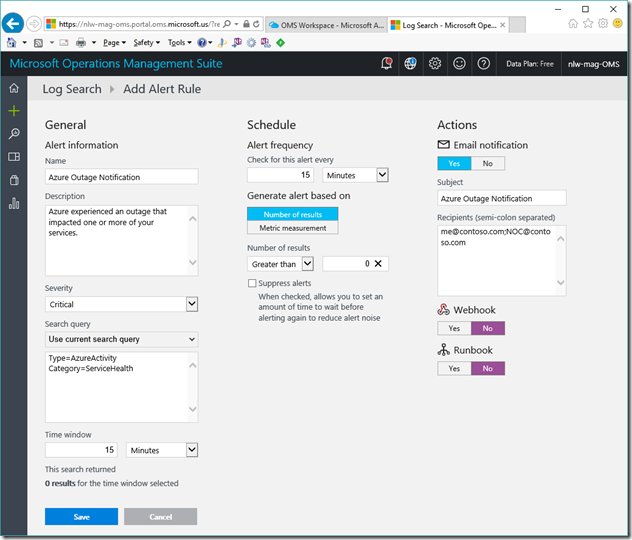
*The alert looks every 15min (alert frequency) for events matching the query that were raised in the past 15min (time window). If there are more than 0 found (number of results), then an email is sent to all recipients listed. These emails do NOT need to be associated with an Azure logon, etc. Any publically routable email address will work.
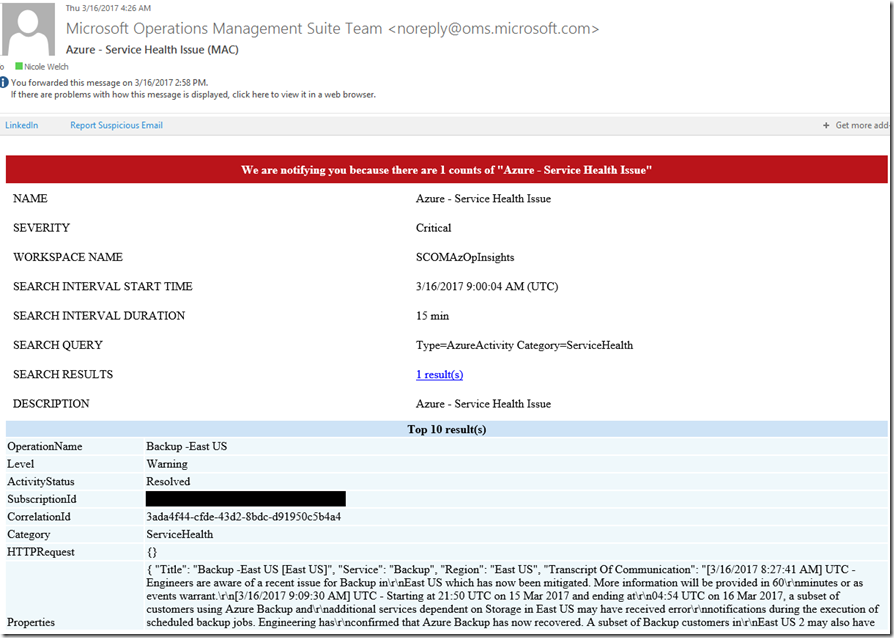
Your recipients will now receive an email for Azure Service incidents. It will look something like this: