What do I need to build a claims-aware wcf service in VS 2013?
In Visual 2012, one can use the “Identity and Access” tool to configure a WCF application to be a claims aware enabled.
I already posted some couple blogs on how to enable claims in VS 2012. You can refer to these blogs:
- Claims Aware WCF using WIF in .Net 4.5
- Claims Aware MVC4 App using WIF Identity and Access tool in .Net 4.5 Part I
- Claims Aware MVC4 App using WIF Identity and Access tool in .Net 4.5 Part II
- Create claims aware Wcf Service using WIF on Framework 4.0
However, Visual Studio 2013 does not include the “Identity and Access” tool. This means that everything has to be done by hand.
Scary right?
Not really as only few changes need to be made to build a claims-aware WCF service in Visual Studio 2013:
1- You must first add a reference to assemblies System.IdentityModel, System.IdentityModel.Services and System.IdentityModel.Tokens.ValidatingIssuerNameRegistry
The third assembly System.IdentityModel.Tokens.ValidatingIssuerNameRegistry may not exist in the Reference Library. To avoid the above issue, use Manage NuGet Packages Menu to install and add a reference to System.IdentityModel.Tokens.ValidatingIssuerNameRegistry in the WCF project.
Otherwise, the following exception may occur during runtime:
[TypeLoadException: ID8030: The value of the 'type' property could not be parsed. Verify that the type attribute of '<issuerNameRegistry type="System.IdentityModel.Tokens.ValidatingIssuerNameRegistry, System.IdentityModel.Tokens.ValidatingIssuerNameRegistry"><authority name="https://WIN-ADFS/adfs/services/trust"><keys><add thumbprint="2D17AD79B8730A77C1F995186633C2FBF8AF4D80" /></keys><validIssuers><add name="https://WIN-ADFS/adfs/services/trust" /></validIssuers></authority></issuerNameRegistry>' element is correct.]
System.IdentityModel.Configuration.TypeResolveHelper.Resolve(ConfigurationElementInterceptor customTypeElement, Type customType) +866868
System.IdentityModel.Configuration.IdentityConfiguration.GetIssuerNameRegistry(IssuerNameRegistryElement element) +203
System.IdentityModel.Configuration.IdentityConfiguration.LoadHandlerConfiguration(IdentityConfigurationElement element) +1548
System.IdentityModel.Configuration.IdentityConfiguration.LoadConfiguration(IdentityConfigurationElement element) +299
System.IdentityModel.Configuration.IdentityConfiguration..ctor() +228
System.ServiceModel.Description.ServiceCredentials.set_UseIdentityConfiguration(Boolean value) +16787980
System.ServiceModel.Configuration.ServiceCredentialsElement.ApplyConfiguration(ServiceCredentials behavior) +813
System.ServiceModel.Configuration.ServiceCredentialsElement.CreateBehavior() +267
System.ServiceModel.Description.ConfigLoader.LoadBehaviors(ServiceModelExtensionCollectionElement`1 behaviorElement, KeyedByTypeCollection`1 behaviors, Boolean commonBehaviors) +302
Once the assemblies are successfully referenced in the WCF project, we need to add the required WIF configurations to the Web.Config file.
Find below the configurations needed to make the WCF a claims aware service:
1- Register ADFS’s Federation Metadata
Adfs exposed a FederationMetadata which needs to be referenced as follows:
1 <appSettings>
2 <add key="ida:FederationMetadataLocation" value="https://win-adfs/FederationMetadata/2007-06/FederationMetadata.xml" />
3 <add key="ida:ProviderSelection" value="productionSTS" />
4 </appSettings>
5
FederationMetadataLocation specifies the URL of ADFS FederationMetadata.
2- Add the System.IdentityModel declaration under the configSections element of the configuration section:
1 <configSections>
2 <section name="system.identityModel" type="System.IdentityModel.Configuration.SystemIdentityModelSection, System.IdentityModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=B77A5C561934E089" />
3 </configSections>
4
This area registers the classes that WCF needs in order to read and parse the config sections used by WIF to model the WS-Federation flow and authentication settings.
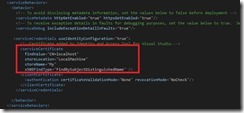
3- Configure the identity Settings
a- “1”: When a user returned a Saml Token back from the STS, it contains the intended recipient URL of the token. This is described as follows in the Saml Token:
1 <saml:AudienceRestrictionCondition>
2 <saml:Audience>https://nape-Lab/Test/WcfWifService091014/Service1.svc</saml:Audience>
3 </saml:AudienceRestrictionCondition>
4
One can immediately notice that AudienceRestrictionCondition specified the Audience value which is evaluated to Valid if it matches one of the values of audienUris. These two values have to match in order for the Relying Party (Wcf service) to accept the token as the intended recipient.
In ADFS, the same value is configured as the “Relying Party Identifier”.
b- “2”: represents the thumbprint of the certificate used by ADFS to sign the Saml Token granted to the User. The public key of this thumbprint’s certificate is used to validate the integrity of the incoming SAML Token. Below is a screenshot of how the sign-in cert looks like in ADFS:
4- This step Specifies the encryption certificate:
The certificates shown in the screenshot was auto-generated by Visual Studio for testing purpose. Note that a real certificate provided by a well-known certificate Authority must be used in a production environment.
The .cer of this certificate must be added as the Encryption cert to WCF Relying Party in ADFS during its creation as follows:
5- Configure the communication binding:
1 <bindings>
2 <ws2007FederationHttpBinding>
3 <binding name="">
4 <security mode="TransportWithMessageCredential">
5 <message>
6 <issuerMetadata address="https://win-adfs/adfs/services/trust/mex" />
7 </message>
8 </security>
9 </binding>
10 </ws2007FederationHttpBinding>
11 </bindings>
Comments
Anonymous
June 19, 2015
Thanks Napegadie for this article. Came in as savior :). I have another question, while hosting the WCF service what authentication scheme to use? I guess it would to be anonymous, but then we would not be able to debug the service using WCFTestClient, would I? Just an insight: We have the services using Integrated Authentication but we constantly run into the double hop issue where we have to either create SPNs, delegation etc.. What I am trying to evaluate is that if we enable claims based authentication on the website and take the claims down to all the services to authenticate, would that work, and would we be able to debug the services using the wcftestclient. I would appreciate any help on this.Anonymous
February 04, 2016
Thanks Napegadie Would be helpful if you could share a sample web.config file