Identity in Your Own Apps with Windows Azure Active Directory - Part 2
Editor’s note: The following post was written by Office 365 MVP Martina Gromand Client Development MVP Toni Pohl . This is the second of a 4 part series . Read part 1 here .
Identity in your own apps with Windows Azure Active Directory
Part 2: Whats happening in WAAD
In part 1 (link) we created an ASP.NET MVC app with authentication against an Office 365 domain. We didn´t have to code anything in our website, Visual Studio 2013 handles all steps for us, includes the libraries and creates the settings and code for the project. That´s cool stuff.
Now let´s have a look into the Windows Azure Active Directory (WAAD). Can we do that? Yes, there are several ways, we´ll show two scenarios. Let´s start with the management-possibilities in this article.
The easiest way is to use the Windows Azure portal. For Azure you need – of course - a valid Azure-account. Depending, how you created the WAAD you can see this domain and administer it directly in the Azure portal. If you didn´t use Windows Azure but created a new Office 365 tenant, we need to add this domain to the portal. We did that, so here are the steps for adding the domain.
Login to https://manage.windowsazure.com/ with your Azure account and go to the Active Directory module close to the bottom in the left menu. In the list of all AD´s you see already connected WAAD´s.
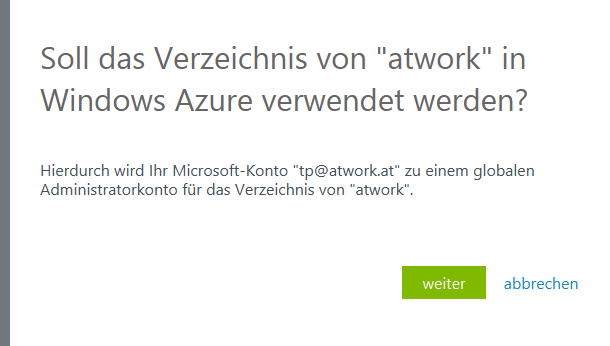
So, let´s add our Office 365 domain here. Click Add on the bottom menu. In the dialog choose use existing directory from the dropdown - Otherwise you can create a new AD here too. Check the ready to be signed out-switch. It´s a good idea to delete all cookies before so that IE isn´t confused with already existing cookies and identities.
Now Azure redirectes to another login form. Choose Use another account here. Now use your Office 365 admin account and password here. In the next step add your personal Azure account as global administrator in the Office 365 AD. Click Next.
Azure prompts the user with a final message that you can use the AD now in your Azure portal with your Azure-account. Click Logout now and reuse your existing Azure-account to login into Azure again.
When going back to the Active Directory list you see a new entry (in our case it´s AD number 9 with name “atwork”). Click on it to rename it and look into the details.
First we want to rename this AD in the Configure menu. Let´s give this AD it´s real name mvpdemo2014.onmicrosoft.com to identify it easily. After that click Save.
Now comes the interesting part. Look into Applications to see what happened here.
The Visual Studio Wizard created an app “MyPortal” with the app URL https://localhost:44324 in the WAAD. Open the app to see the app settings. Here´s the App URI and the address of the WS federation document as well as some more settings.
When clicking on Configure we can modify App name, URL, client ID and so on. If the app secret key is compromised, we can create a new one for 1 or 2 years. When saving the settings, a new key is generated. We can use this key to replace the old one in our app (web.config, key ida:Password).
So all keys we need in our app can be managed here in the Azure portal. They are stored directly in the WAAD.
We also can manage users and groups here. Change to the Users or Groups menu and add new objects into the AD. By default we have the user who created the AD – in our case the admin-user admin@mvpdemo2014.onmicrosoft.com who created the Office 365 tenant – and the second admin-user tp@atwork.at (a Microsoft Account which is the login for our Azure tenant) we needed to add to access this WAAD from our Azure portal.
The portal offers all standard functions up to resetting a user´s password. Simply add users and groups. It´s the same procedure as in the Office 365 https://portal.microsoftonline.com portal. You can choose if the new user object is a new one or even connect other users as in this screenshot.
The important information here is that if your app uses an user account for accessing WAAD (f.e. in the Visual Studio wizard for connecting a new project with Single Sign on) this user has to be a global administrator – it cannot be a standard user. Only admins can access the GraphAPI (see part 3).
All changes are made instantly because they are immediately stored directly in the WAAD. You can also add custom domains in the Azure portal like f.e. mvpdemo2014.com and define if Directory Integration is allowed or not. So it´s the same as in the Office 365 portal, wih the same rules. Custom domains must be verified and Hybrid-scenarios with ADFS or DirSync also work.
It´s a relatively new feature since fall 2013 that you can add more than one AD into your Azure tenant. An interesting part is that you cannot delete WAAD´s here in the Azure portal. It seems this function is to come, otherwise it´s going to be a little be confusing in our Azure tenant with many AD´s.
So we have a tool to manage our WAAD in the cloud: The Windows Azure Portal. As we mentioned at the beginning there´s a second way a second way to view and manage our WAAD. This is covered in part 3.
About the authors
Toni Pohl has worked for nearly 20 years as an independent IT expert. Toni began his IT career in the early 1990s as a trainer. After working as a trainer, his emphasis changed to the field of consulting and developing software solutions using database systems. In 1999 Toni Pohl founded atwork information technology group along with Martina Grom. They share the business administration. He is responsible for new business development, technology, and quality assurance. Toni Pohl has been awarded in 2013 by Microsoft with the Most Valuable Professional Award (MVP) for his expertise in Client Development. Toni blogs about new technologies for the atwork-blog, in Microsoft-TechNet-Team-Austria Blog, in codefest.at, the Austrian MSDN Blog and in cloudusergroup and is writing technical articles for various magazines. You can connect with him on Twitter, Facebook, or Linkedin.

Martina Grom works as IT-Consultant & is co-founder and CEO of atwork information technology. atwork is located in Austria/Europe and is specialized in development of Online Solutions. Martina & Toni founded atwork in 1999, and she has worked in IT since 1995. Martina is recognized as an expert in Microsoft Office Online Services solutions and was worldwide one of the first 8 MVP’s awarded in 2011 for her expertise in Office 365. She writes numerous articles and blog posts. Her passion is Online & Social Media, cloud computing and Office 365. Martina consults companies on their way to the cloud. Martina has a master degree in international business administration of University of Vienna, You can connect with her on Twitter,Facebook, Linkedin or join her cloudusergroup.
About MVP Monday
The MVP Monday Series is created by Melissa Travers. In this series we work to provide readers with a guest post from an MVP every Monday. Melissa is a Community Program Manager, formerly known as MVP Lead, for Messaging and Collaboration (Exchange, Lync, Office 365 and SharePoint) and Microsoft Dynamics in the US. She began her career at Microsoft as an Exchange Support Engineer and has been working with the technical community in some capacity for almost a decade. In her spare time she enjoys going to the gym, shopping for handbags, watching period and fantasy dramas, and spending time with her children and miniature Dachshund. Melissa lives in North Carolina and works out of the Microsoft Charlotte office.