What is OMS Security Threat Intelligence and why do I need it?
Organizations were used to protect their system from adversaries by enhancing their own defense mechanisms. While each organization can fight them alone, threat intelligence offers a way to use knowledge that is gathered by other organizations and security researchers to make the defense more effective. OMS Security and Audit solution now provides you threat intelligence enrichment without any additional effort or payment.
Threat intelligence is shifting the security model and minimizing the extent of security incidents if analyzed correctly. In fact, security teams can drive a better and more informed responses to these security incidents. Threat Intelligence in OMS Security is based on feeds from leading Threat Intelligence vendors and on Microsoft data that is gathered while defending our own cloud services. Microsoft runs the biggest cloud services in the world, enabling us to achieve a unique view of the threat landscape. The insights we derive, informed by trillions of signals from billions of sources, create an intelligent security graph that we use to inform how we protect all endpoints, better detect attacks and accelerate our response. Our goal is to enable our customers to benefit from this knowledge to protect their resources. We want our customers to achieve this out-of-the-box without complex integration scenarios.
Threat Intelligence is enhances OMS Security and Audit by continuously feeding real-time intelligence into the log data. This is not yet another laundry list of bad IP addresses or other indicators that are dumped into your solution. While these threat capabilities are critical, understanding groups, actors and motivations is vitally important too. The threat intelligence you will find in OMS is much more evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice about an existing or emerging threats to your assets.
Here is the TI architecture in OMS: 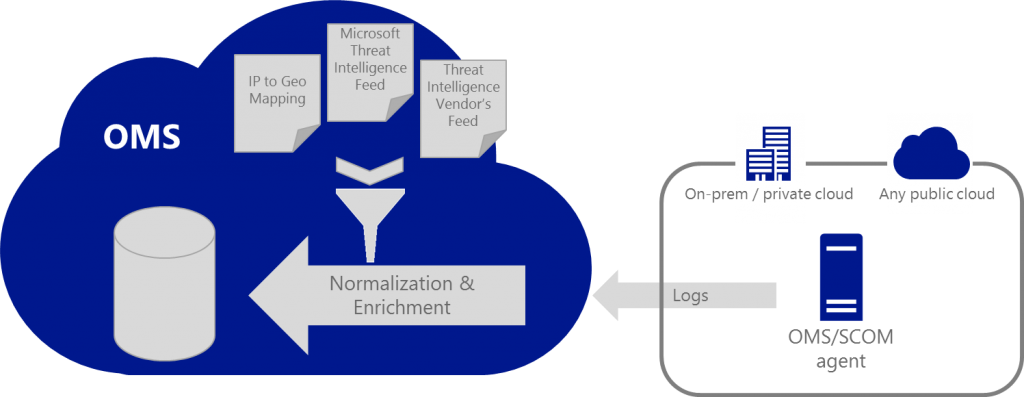
Threat Intelligence plays a couple of roles in OMS Security. The first is near real-time correlation of ingested records with threat data. This enables the security team to prioritize which events are most important and deliver more power to our event management capabilities. In the following screenshot you can see a sample search for IIS Log records that were enriched with threat intelligence in cases where the request arrives from an IP address that we identify as malicious: 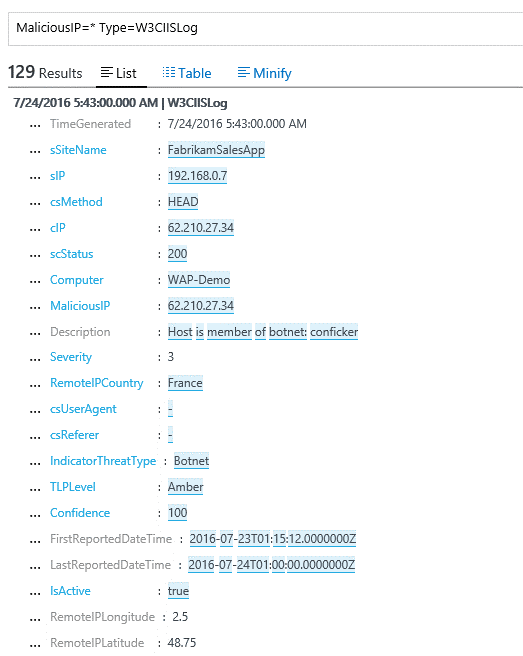
The other role has a different goal of helping understand who is targeting the organization and improve communication across the business, resulting in better informed response. This changes the communication from “We were hit by Botnet x” to “a group from Y is targeting us, and actively trying to steal data” .
The threat intelligence dashboard within OMS Security and Audit solution allows you to browse the various threats:
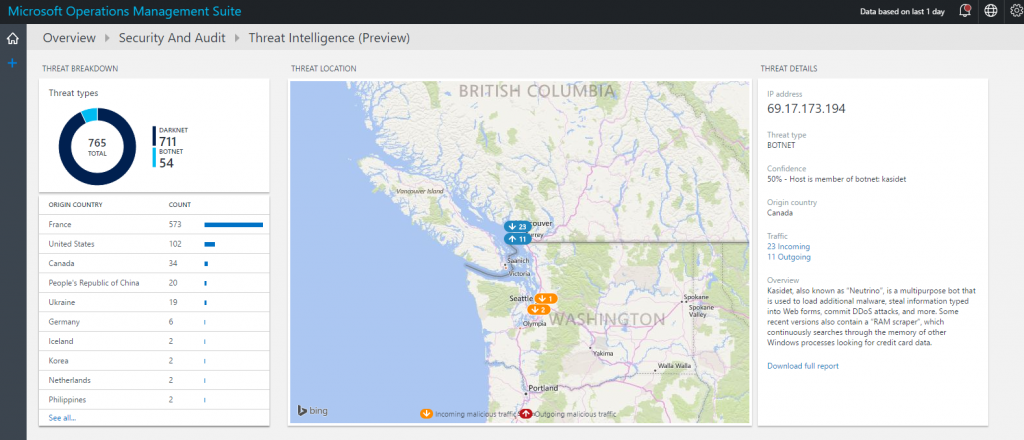
In some of the cases, it would allow you to download a full report with the details of the specific adversary including its common targets, method of attack, control architecture, attack samples and additional indication of compromises.
TI in OMS Security will help you figure out who is attacking you and fix what they are after:
- TI data aggregated from reliable sources and cross-correlated for accuracy to provide accurate, timely and complete (as possible)
- Tools and presentation methods for effective visualization and understanding of TI
- Ability to aggregate information from virtually every source and correlate the data with TI to provide full-picture view that wraps events with indicators of compromise
To learn more about how to use this capability, read Monitoring and responding to security alerts in Operations Management Suite Security and Audit Solution
Try it out!
I invite you to follow me on Twitter and the Microsoft OMS Facebook site. If you want to learn more about Windows PowerShell, visit the Hey, Scripting Guy Blog.
If you would like to get a free Microsoft Operations Management Suite (#MSOMS) subscription so that you can test it out, you can do so from here. You can also get a free subscription for Microsoft Azure as well by selecting this link.
Microsoft Operations Management Team
Comments
- Anonymous
August 10, 2016
If OMS is so powerfull why Microsoft chose to use Qualys Web Application Scanning as stated in https://www.qualys.com/customers/success-stories/reining-in-global-web-application-security-risk-at-microsoft/ ?- Anonymous
August 10, 2016
Hi Stephane, the two are not mutual exclusive. Qualys provides vulnerability detection which is an important prevention tool. OMS Security provide detection for breaches, investigation and visibility across the board.
- Anonymous
- Anonymous
August 18, 2016
Does Threat Intelligence require the Wire Data solution or any other data sources? - Anonymous
August 19, 2016
Interesting thoughts on OMS security. I am looking at similar topics for Siemens Convergence Creators and have an OMS for GSM-R flyer you might be interested in: http://www.convergence-creators.siemens.com/gsm-r-dispatcher.html.Let me know what you think about it and whether it was useful for you.Karla - Anonymous
August 22, 2016
Is there any way to trigger a Threat Detection for testing/demo purposes? Perhaps insert a dummy entry in to an IIS or Firewall log with a particular IP address that's always flagged? - Anonymous
June 21, 2017
If you had to select one over the other which would you select, OMS or Qualys?