Set up an Operations Management Suite alert that detects suspicious executables
Summary: Learn how to set up an MSOMS alert that detects suspicious executables in this step-by-step tutorial by Ed Wilson.
This post is the fourth post in a multi-part series of blog posts about OMS alerting. To fully understand this post, you should read the entire series in order.
Here are the posts in the series:
- OMS alerting is now generally available
- Learn how to get started using OMS alert management
- Use OMS to create alerts for missing security and other updates
- Set up an Operations Management Suite alert that detects suspicious executables
- Use the OMS log search feature to report on custom OMS alerts
Good morning everyone, Ed Wilson here, and today I want to talk about how to configure an alert that detects suspicious executables. This will illustrate the potential of Microsoft Operations Management Suite (OMS) alerting.
One of the cool things about OMS alerting is that it begins with search. This means that things that I can search on, I can retrieve and use to generate alerts.
Suspicious executables alert
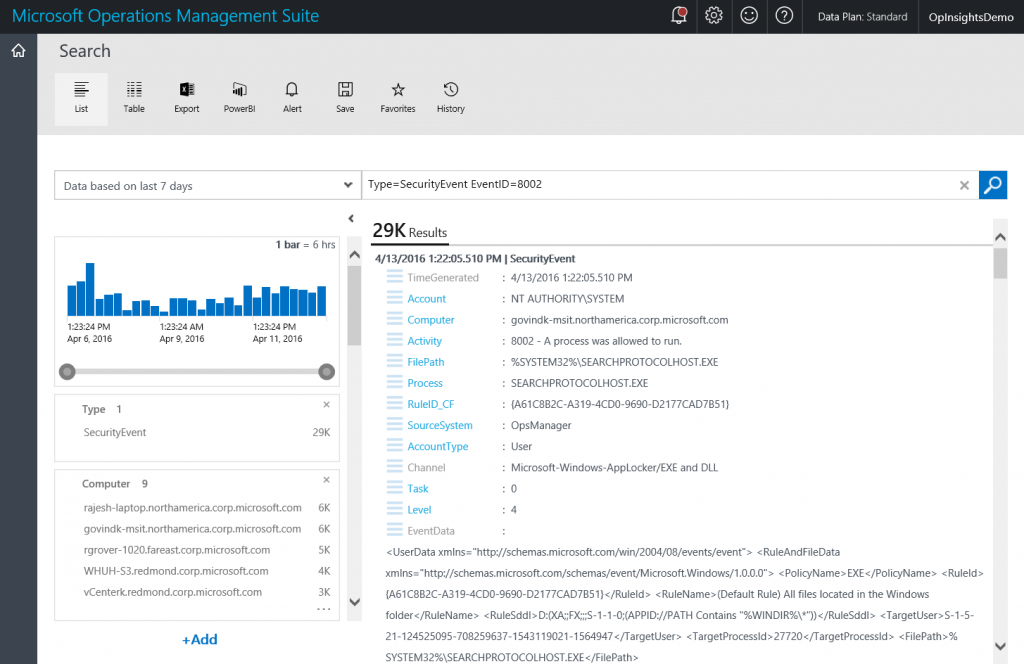
Security Event 8002 reports when a process runs. The event reports a lot of useful information such as the file path, the process name, file hash, and even the FQBN.
NOTE: FQBN stands for Fully Qualified Binary Name, and it is a string that is comprised of the following: publisher\product\file name\version.
A simple query that reports from Event ID 8002 is shown here:
Type=SecurityEvent EventID=8002
The query and sample output are shown here:
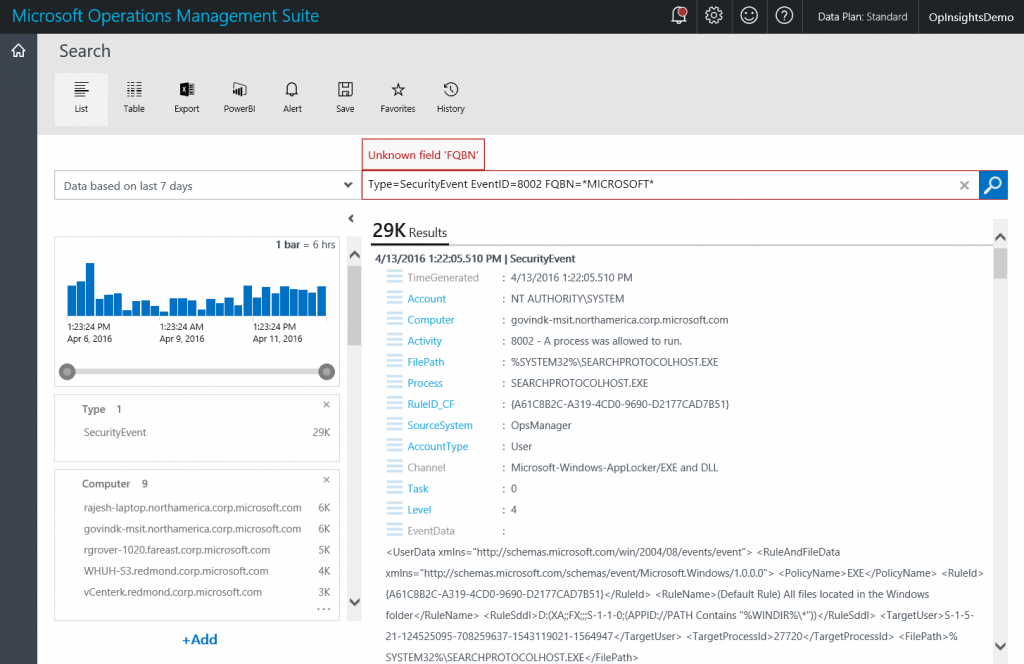
Now, I want to add the FQBN. The thing to keep in mind here is that the OMS search is case sensitive. I must capitalize it exactly as Fqbn. For example, if I have FQBN, I get an “Unknown field ‘FQBN’ error message that is shown in the figure here:
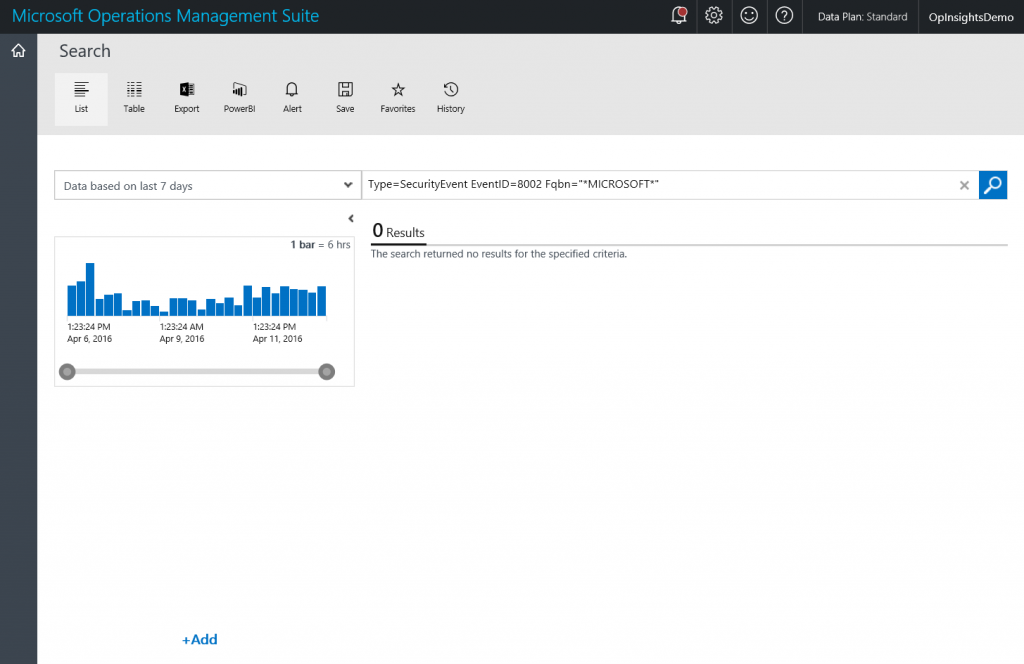
One other thing to keep in mind is that if I use quotation marks, the * character will be considered as a literal character and not as a wild card. This will cause search to return no records, but it does not generate an error as you see in the following screenshot:
So, my sample query now appears here:
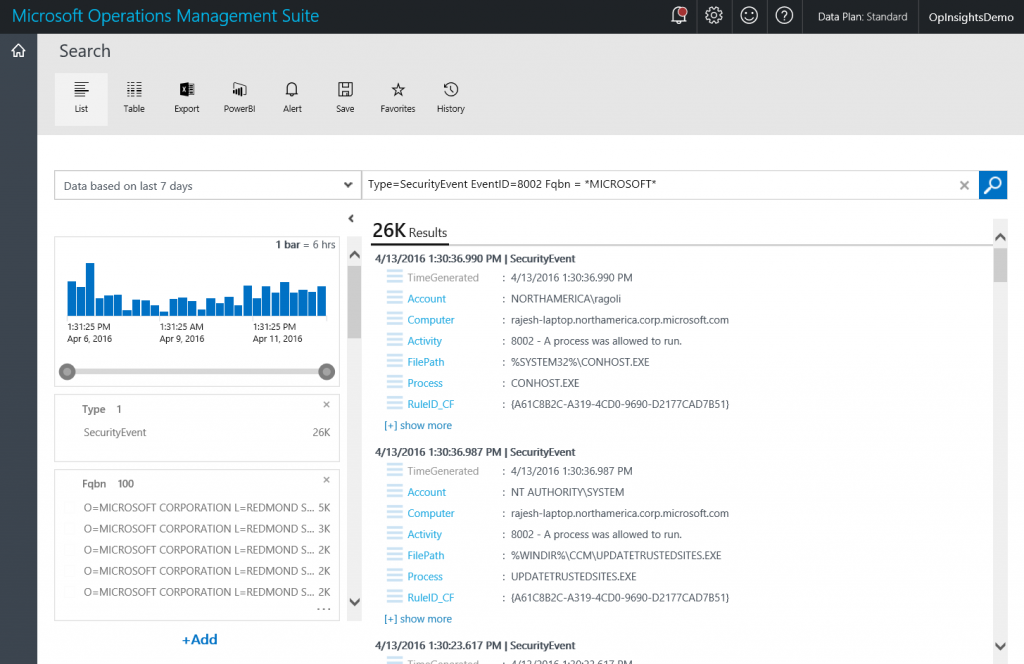
Type=SecurityEvent EventID=8002 Fqbn = *MICROSOFT*
NOTE: MICROSOFT is case sensitive in this query as well. Therefore *Microsoft* will return no records.
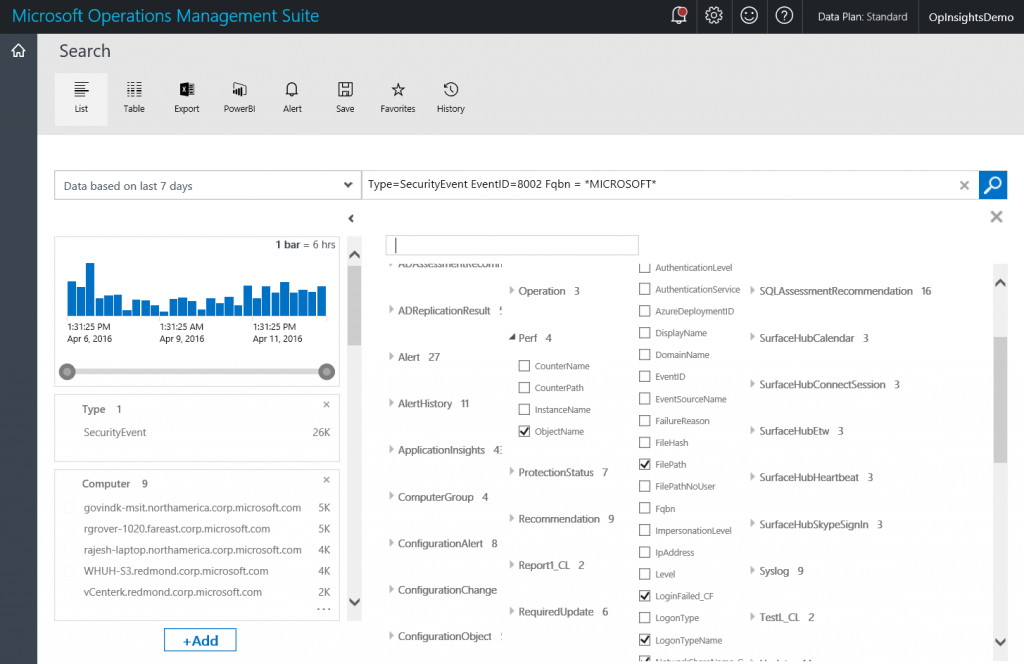
The output from the query in the detail pane does not display the Fqbn unless I click the [+] show more link. However, I can add the Fqbn to the quick look pane by using the +Add button and checking Fqbn. This is shown here:
After I do this, I get a great summary of Fqbn that matches *MICROSOFT*. This is shown here:
Measure count
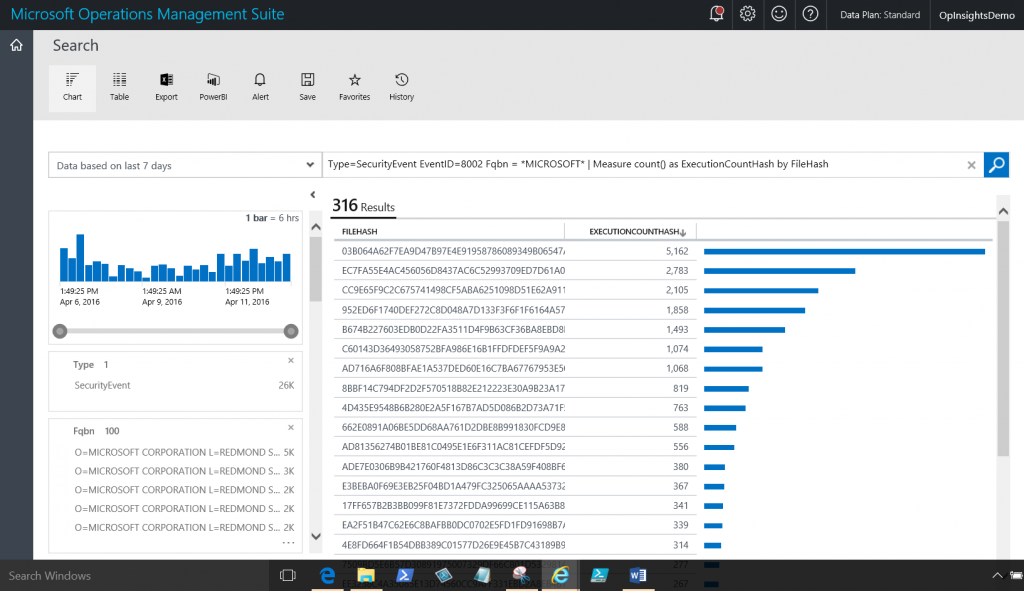
Now I want to use the Measure command to count the ExecutionCountHash and organize it by the file hashes of the files that execute. I also get a count of each one of these. The command is shown here:
Type=SecurityEvent EventID=8002 Fqbn = *MICROSOFT* | Measure count() as ExecutionCountHash by FileHash
And the command and the output appear here:
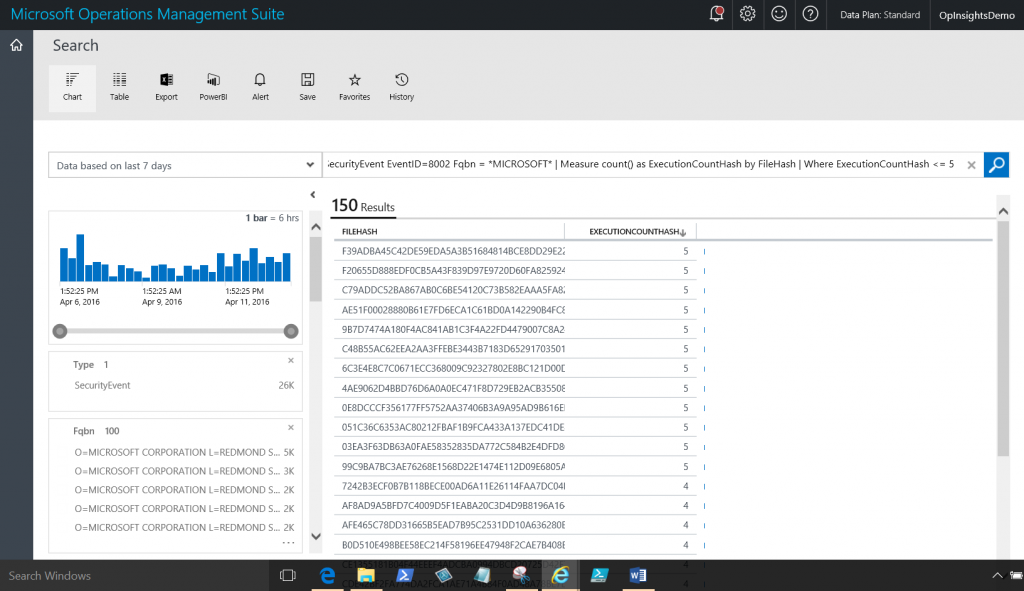
The last thing to do is to add a Where filter to the end of the command. I am only interested in cases where the ExecutionCountHash occurs greater than or at least equal to 5. The command is shown here:
Type=SecurityEvent EventID=8002 Fqbn = *MICROSOFT* |
Measure count() as ExecutionCountHash by FileHash |
Where ExecutionCountHash <= 5
The command and output is shown here:
Now convert the search to an alert
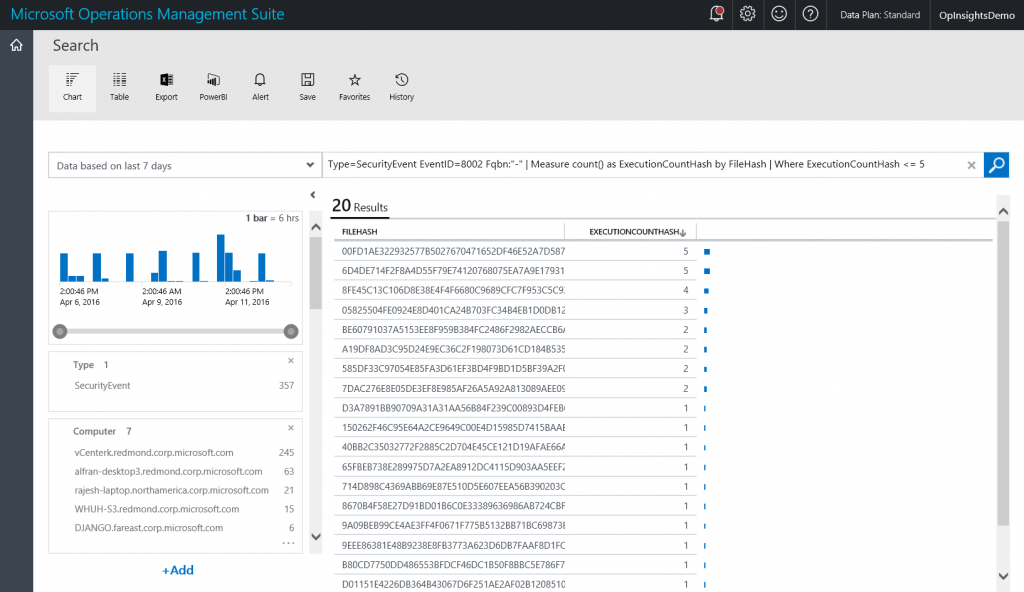
Now, in reality, I am not interested in searching for program execution where the Fqbn has Microsoft in it. However, because I knew that query would return data, I used it as I built up my actual query. The actual query I want is the one where the Fqbn equals “-“. So I modify the query one last time:
Type=SecurityEvent EventID=8002 Fqbn:"-" | Measure count() as ExecutionCountHash by FileHash | Where ExecutionCountHash <= 5
NOTE: Make sure the double quotes are straight and not “smart quotes”, or the query will not return any data. Unfortunately, it will not generate an error.
The query and output are shown here:
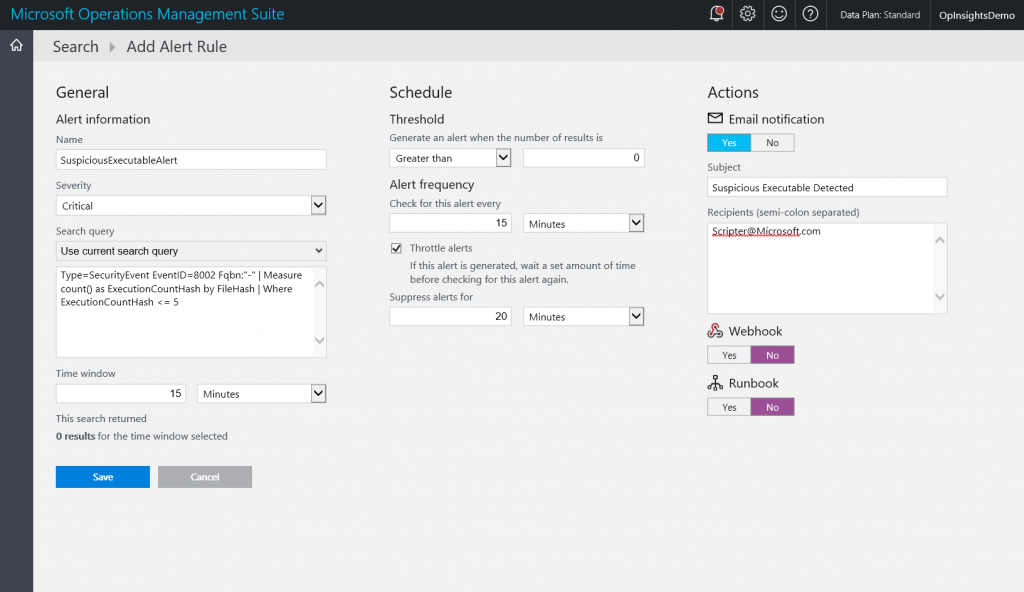
Now that I know that I have a good query, it’s time to generate the alert. I provide the following:
- Name: SuspiciousExecutableAlert
- Severity: Critical
- Search query: Type=SecurityEvent EventID=8002 Fqbn:"-" | Measure count() as ExecutionCountHash by FileHash | Where ExecutionCountHash <= 5
- Time window: 15 minutes
- Threshold: greater than 0
- Alert frequency: Every 15 minutes
- Throttle alerts: 20 minutes
- Email: Yes
- Subject: Suspicious Executable detected
- Recipient: Scripter@Microsoft.Com
NOTE: Many of these are defaults or are prepopulated, so it takes less than a minute to fill in the form.
The alert is shown here:
That is all I have for you today. Join me tomorrow when I’ll talk some more about OMS alerting.
I invite you to follow me on Twitter and the Microsoft OMS Facebook site. If you want to learn more about Windows PowerShell, visit the Hey, Scripting Guy Blog. If you have any questions, send email to me at scripter@microsoft.com. I wish you a wonderful day, and I’ll see you tomorrow.
Ed Wilson
Microsoft Operations Management Team