OMS Gateway with SCOM support now in public preview
Summary: Learn about the public preview of the OMS Gateway with SCOM support.
Hi Everyone, Nini here, and today I’m pleased to announce the release of the public preview version of the OMS Gateway with SCOM support . Since the release of the first version of the Gateway (formerly known as the Log Analytics Forwarder), we received multiple requests for this functionality, and finally it is here! This release provides a way to send data from your SCOM Management Server and SCOM Agents to OMS. Note that installing this Gateway will replace previous versions of the Gateway that you have installed.
In this post, I'll walk you through the following:
- How to configure the Gateway to support your SCOM Management Server
- How to take advantage of network load balancer for high availability
- How to configure the Gateway to support your automation hybrid workers
- PowerShell cmdlets that you can use to update the Gateway’s configuration settings
Direct Agent 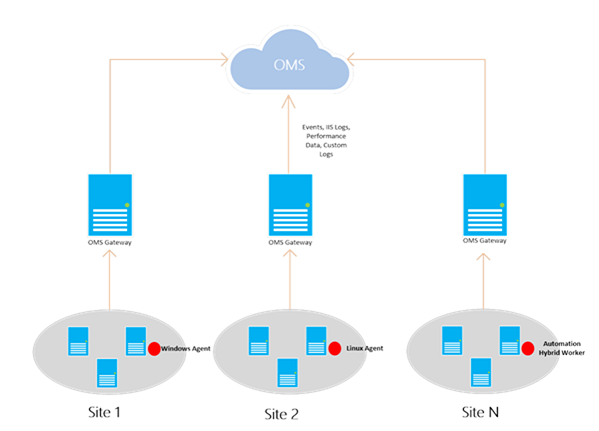
SCOM Management Server 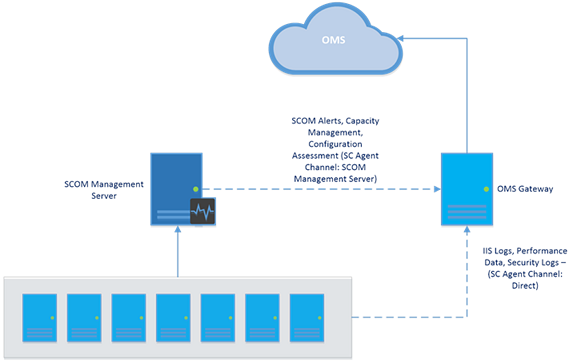
Notice that SCOM agents send some data, such as SCOM alerts, configuration assessment, instance space, and capacity data, through the Management Server. Other high-volume data, such as IIS logs, performance, security, etc., is sent directly to the OMS Gateway. See Add Log Analytics solutions from the Solutions Gallery to get a complete list of data that is sent through each channel.
Configure SCOM
To use the Gateway to support SCOM, you need to have the following:
- Microsoft Monitoring Agent (Agent version – 8.0.10900.0 and later) installed on the Gateway server and configured to OMS workspaces with which you want to communicate.
- Gateway must have Internet connectivity or be connected to a proxy server that does.
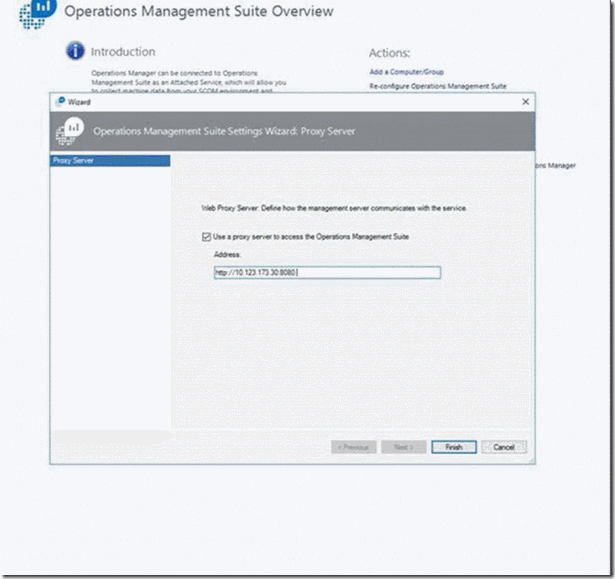
- Open the Operations Manager console, and select Configure Proxy Server:
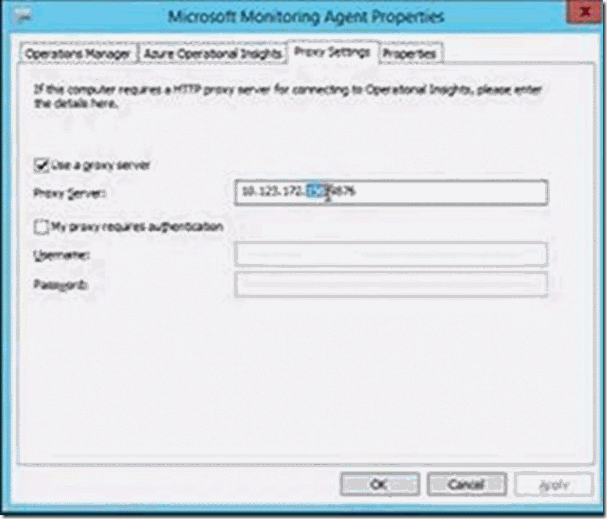
- Check the box that provides the option to use a proxy server to access the Operations Management Suite. Input the IP address of the OMS Gateway server. Be sure to start with the https:// prefix:
- Click Finish, and now you have your SCOM server connected to your Log Analytics workspace.
Take advantage of network load balancing
A common request that we have also received is the need for high availability for the Gateway. In this section, I’ll show you how you can use the network load balancer to do this.
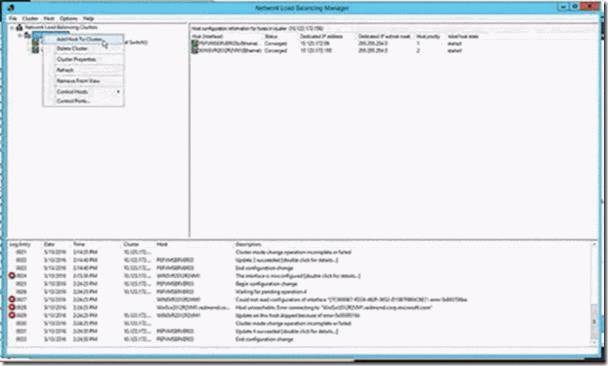
- Open the network load balancer and create a new cluster.
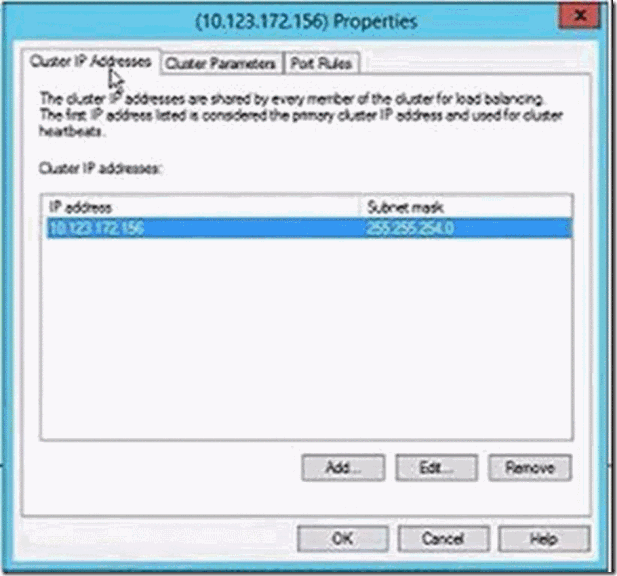
- Right-click the cluster before adding Gateways, and select Cluster Properties. Configure the cluster to have its own IP address:
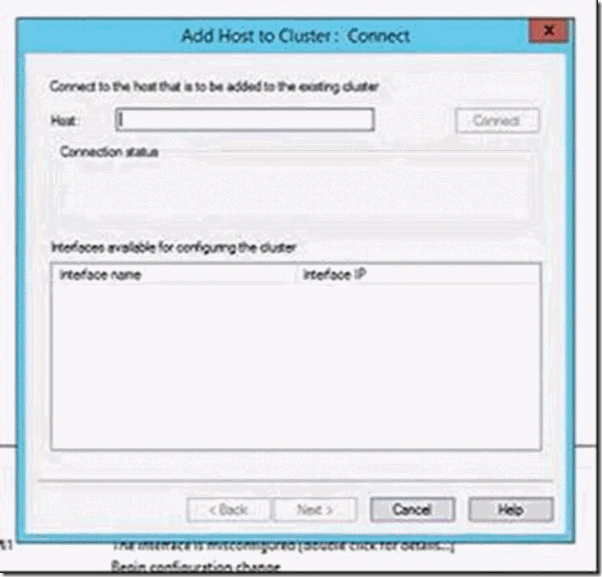
- To connect a Gateway server (with the Microsoft Monitoring Agent installed), right-click the cluster’s IP address, and then click Add Host to Cluster.
- Enter the IP Address of the Gateway’s server that you want to connect:
- On computers that do not have Internet connectivity, be sure to use the IP address of the cluster when you configure the Microsoft Monitoring Agent Properties:
The cluster will then manage traffic from your agents by redirecting the requested connections from the Microsoft Monitoring Agents across its nodes. If one Gateway server goes down, the traffic gets redirected to other nodes.
Configure the Gateway to support automation hybrid workers
If you have automation hybrid workers in your environment, these steps provide manual, temporary workarounds to configure the Gateway to support them.
- If your computer is registered as a hybrid worker automatically for patching via the Update Management solution, use these steps:
1) Add the Job Runtime Data service URLs to the Allowed Host list on the OMS Gateway:
Add-OMSGatewayAllowedHost we-jobruntimedata-prod-su1.azure-automation.net
2) Restart the OMS Gateway Service by using the following PowerShell cmdlet:
Restart-Service OMSGatewayService
- If your computer is on-boarded to Azure automation by using the hybrid worker registration cmdlet, use these steps:
1) Add the agent service registration URL to the Allowed Host list on the OMS Gateway:
Add-OMSGatewayAllowedHost ncus-agentservice-prod-1.azure-automation.net
2) Add the Job Runtime Data service URLs to the Allowed Host list on the OMS Gateway:
Add-OMSGatewayAllowedHost we-jobruntimedata-prod-su1.azure-automation.net
3) Restart the OMS Gateway Service.
Restart-Service OMSGatewayService
Use the following tables as a reference for the right URL based on your region:
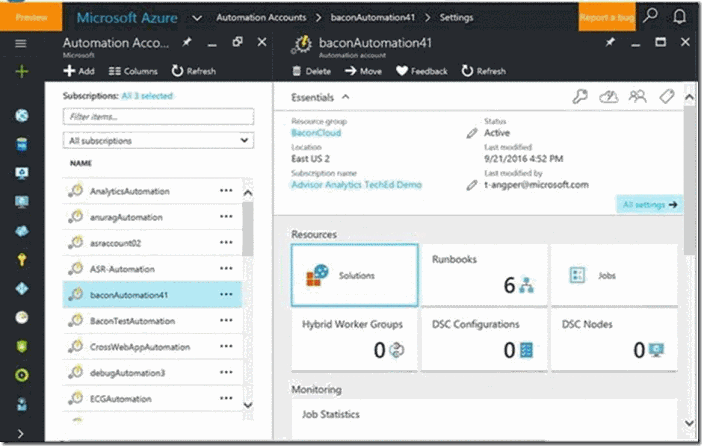
Note: To locate your region, do this:
- Sign in to the Azure portal.
- Select the Azure Automation service.
- Select the appropriate Azure Automation account.
- View your region under the Location field.
Job Runtime Dataservice URLs
| Region | URL |
|---|---|
| North Central US | ncus-jobruntimedata-prod-su1.azure-automation.net |
| West Europe | we-jobruntimedata-prod-su1.azure-automation.net |
| South Central US | scus-jobruntimedata-prod-su1.azure-automation.net |
| East US | eus-jobruntimedata-prod-su1.azure-automation.net |
| Central Canada | cc-jobruntimedata-prod-su1.azure-automation.net |
| North Europe | ne-jobruntimedata-prod-su1.azure-automation.net |
| South East Asia | sea-jobruntimedata-prod-su1.azure-automation.net |
| Central India | cid-jobruntimedata-prod-su1.azure-automation.net |
| Japan | jpe-jobruntimedata-prod-su1.azure-automation.net |
| Australia | ase-jobruntimedata-prod-su1.azure-automation.net |
Agent Service URLs
| Region | URL |
|---|---|
| North Central US | ncus-agentservice-prod-1.azure-automation.net |
| West Europe | we-agentservice-prod-1.azure-automation.net |
| South Central US | scus-agentservice-prod-1.azure-automation.net |
| East US | eus2-agentservice-prod-1.azure-automation.net |
| Central Canada | cc-agentservice-prod-1.azure-automation.net |
| North Europe | ne-agentservice-prod-1.azure-automation.net |
| South East Asia | sea-agentservice-prod-1.azure-automation.net |
| Central India | cid-agentservice-prod-1.azure-automation.net |
| Japan | jpe-agentservice-prod-1.azure-automation.net |
| Australia | ase-agentservice-prod-1.azure-automation.net |
Useful PowerShell cmdlets
These cmdlets enable you to carry certain tasks to update the OMS Gateway’s configuration settings. Before you use them, be sure to do the following:
- Install the OMS Gateway (MSI).
- Open the PowerShell window.
- Type this command to import the module – Import-Module OMSGateway.
- If no error occurred in the previous step, the module was successfully imported, and the cmdlets can be used. Type Get-Module OMSGateway.
- After you make changes by using these cmdlets, be sure to restart the Gateway service.
If you get an error in step 3, the module was not imported. This is usually caused because PowerShell was unable to find the module, but it can be found under the Gateway’s installation path: C:\Program File\Microsoft OMS Gateway\PowerShell.
| Cmdlet | Parameters | Description | Examples | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Set-OMSGatewayConfig |
|
Change the configuration of the service | Set-OMSGatewayConfig -Name ListenPort -Value 8080 | ||||||
| Get-OMSGatewayConfig | Key | Change the configuration of the service |
|
||||||
| Set-OMSGatewayRelayProxy |
|
Set address (and credential) of relay (upstream) proxy |
|
||||||
| Get-OMSGatewayRelayProxy | Set address of relay (upstream) proxy | Get-OMSGatewayRelayProxy | |||||||
| Add-OMSGatewayAllowedHost | Host (required) | Add host to the allowed list | Add-OMSGatewayAllowedHost -Host www.test.com | ||||||
| Remove-OMSGatewayAllowedHost | Host (required) | Remove host from the allowed list | Remove-OMSGatewayAllowedHost -Host www.test.com | ||||||
| Get-OMSGatewayAllowedHost | Get currently allowed host (only local configured allowed host, do not include automatically downloaded allowed hosts) | Get-OMSGatewayAllowedHost | |||||||
| Add-OMSGatewayAllowedClientCertificate | Subject (required) | Add client certificate subject to the allowed list | Add-OMSGatewayAllowedClientCertificate -Subject mycert | ||||||
| Remove-OMSGatewayAllowedClientCertificate | Subject (required) | Remove client certificate subject from the allowed list | Remove- OMSGatewayAllowedClientCertificate -Subject mycert | ||||||
| Get-OMSGatewayAllowedClientCertificate | Get currently allowed client certificate subjects (only local configured allowed subjects, do not include automatically downloaded allowed subjects) | Get-OMSGatewayAllowedClientCertificate |
Troubleshoot the OMS Gateway
We recommend that you install the OMS Agent on computers that have the Gateway installed. With the agent, you can collect events that the Gateway logs.
OMS Gateway Event IDs and descriptions
| Name | Description |
|---|---|
| 400 | Any application error that does not have a specific id |
| 401 | Wrong configuration. For example: listenPort = “haha” instead of an integer |
| 402 | Exception in parsing TLS handshake messages |
| 403 | Networking error. For example: cannot connect to target server |
| 100 | General information |
| 101 | Service has started |
| 102 | Service has stopped |
| 103 | Received a HTTP CONNECT command from client |
| 104 | Not a HTTP CONNECT command |
| 105 | Destination server is not in allowed list or the destination port is not secure port (443) |
| 106 | In any reason that the TLS session is suspicious and rejected |
| 107 | The TLS session has been verified |
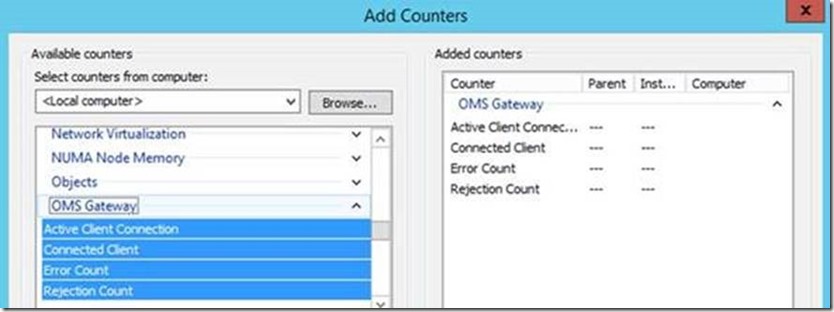
Performance counters to collect
| Name | Description |
|---|---|
| OMS Gateway\Active Client Connection | Number of active client network (TCP) connections |
| OMS Gateway\Connected Client | Number of connected clients |
| OMS Gateway\Rejection Count | Number of rejections due to any TLS validation error |
What's next?
Moving forward, we plan to list the automation hybrid worker and other URLs that you’d find useful so that they are provisioned automatically and make improvements based on your feedback!
That is all I have for you today. If you have feedback or questions, please leave a comment below or leave us feedback on our Uservoice under the OMS Gateway category.
You can get a free Microsoft Operations Management Suite (#MSOMS) subscription so that you can test it. You can also get a free subscription for Microsoft Azure.
Nini Ikhena
Microsoft Operations Management Team
Comments
- Anonymous
September 26, 2016
The images are illegible - Anonymous
September 28, 2016
@Isaias - we republished the images, and they should be clearer now. - Anonymous
October 03, 2016
The comment has been removed- Anonymous
October 03, 2016
Once the management server is configured with the proxy information, it gets propagated automatically to the agents reporting to it.
- Anonymous