Analyze your Check Point logs with OMS Security
The Security & Compliance solution in the Operations Management Suite (OMS) provides security insights about many sources of security data from Windows and Linux machines, including any source that emits Syslog. Today, we are announcing a new capability, developed by Check Point, that enables you to send Check Point security gateway logs to the OMS Security & Compliance solution for further analysis.
After you forward your Check Point logs to the OMS Log Analytics service via the Linux agent, the data is indexed and security-related data is parsed. This makes it easy to search the data and use it in queries, alerts, and dashboards.
The result is a new type of log, called CommonSecurityLog,that lets you use the full power of the OMS search language to analyze the data that comes from your Check Point firewalls.
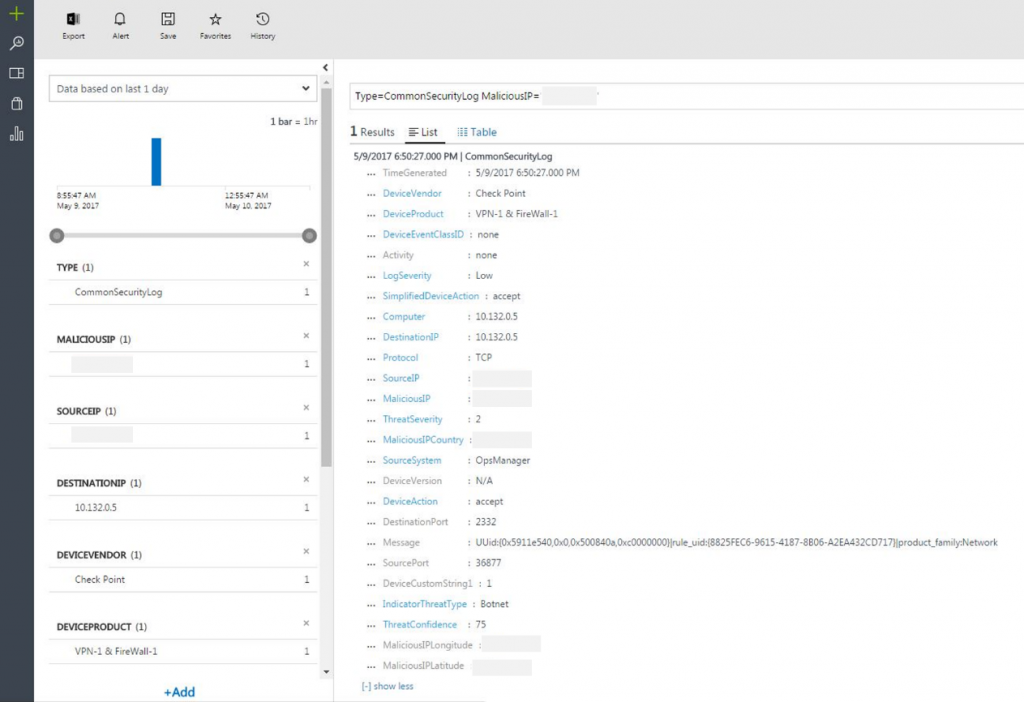
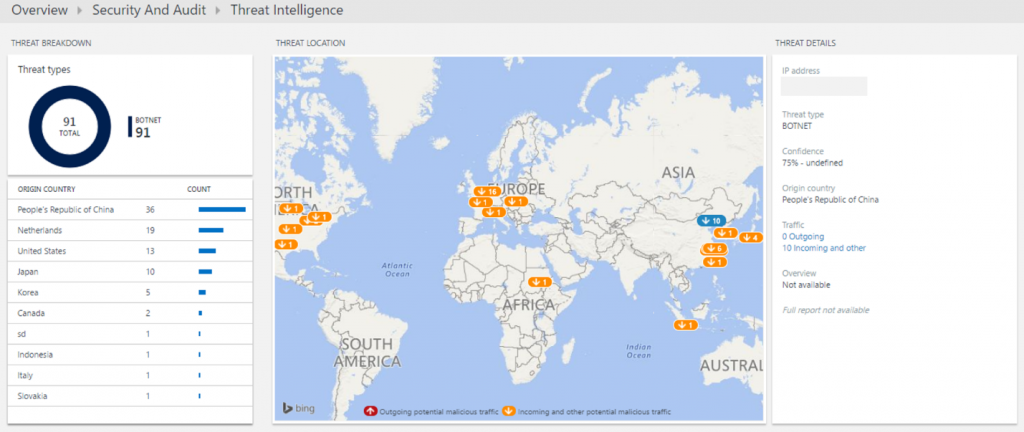
In addition, Security & Compliance uses Microsoft threat intelligence to identify IP addresses that are used by malicious actors. This provides valuable insight into failed and successful attempts by attackers to access your systems. It even highlights cases where your systems are communicating with malicious computers. This usually indicates that a system has been compromised, and is contacting its command and control or Exfiltrating data. An interactive map shows you the geographic source of these attacks, and makes it easy for you to investigate further. If additional information is known about the attacker, a threat attribution report provides details about the attacker's objectives and tactics.
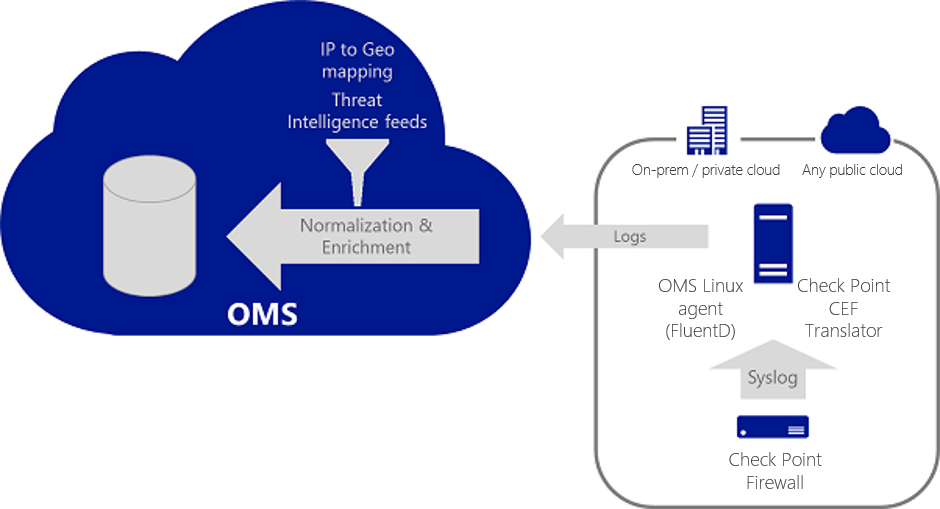
The following diagram shows an overview of the Check Point log processing architecture:
Let's get started with configuring Check Point integration with the OMS Security & Compliance solution.
For more general information and background, see Connecting your security products to the Operations Management Suite (OMS) Security and Audit Solution.
Comments
- Anonymous
July 13, 2017
Well said, but what is the difference with SIEM ?