Microsoft’s Identity Life Cycle Management Strategy And Roadmap - Part 1: Microsoft's philosophy and vision
In a previous post I promised to delve a little deeper into our Identity Lifecycle strategy and roadmap, so this post is the first of three to do exactly that. We'll start with Microsoft's philosophy on Identity Lifecycle Management. Future posts in the series will loom at where we are today in terms of ILM and where we will be going to, with the much anticipated release of ILM "2", scheduled for the beginning on 2009. So with no further ado, lets look at Microsoft's philosophy for ILM.
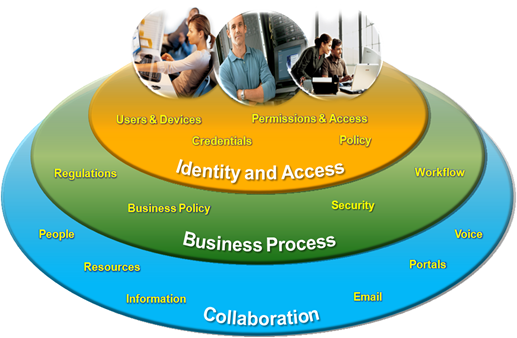
Basically Microsoft's position on ILM comes down to the concept of a People Ready business. Identity and access is at the centre of the People Ready business, and a robust identity and access infrastructure and management solution is critical to enabling the people in your organisation to be successful:
To enable the people in your organisation to be successful, they need an efficient and intuitive way to collaborate – to interact with other people, resources and information through tools such as email, portals, and voice. At the same time, the business needs to ensure that collaboration is taking place within the bounds of internal and external regulations, business policy and process, and security. At the centre of it all, is the identity and access infrastructure and tools that provides information on users, devices, their access, what credentials they need and how they are configured, and the rules or policies governing the behaviour of these objects. A strong identity and access solution can give the business the tools to ensure that process, security mandates and regulations are being followed, and ultimately provides a secure and efficient collaboration experience for the people.
In order to realize the vision of a People Ready business, the identity and access infrastructure and tools need to provide people with the right collaboration experience, in a way that complies with business process.
How do we ensure that our identity and access infrastructure and tools are enabling this People Ready vision? By overcoming a number of challenges. Today we know there are a number of challenges in the keep us from getting there…
1. Improving Operational Efficiency
- On average employees need access to 16 applications and systems
- Companies spend £15-30 per user per year for password resets
2. Reducing Security Risks
- 38% of users recycle old passwords, 18% write them down
- Governments moving to strong authentication for employees & contractors
3. Meeting External & Internal Regulations
- Implementing business process and policies to meet internal regulations
4. Enabling Key Business Objectives
- Improving connections with partners and customers
- Driving business decisions closer to decision-makers
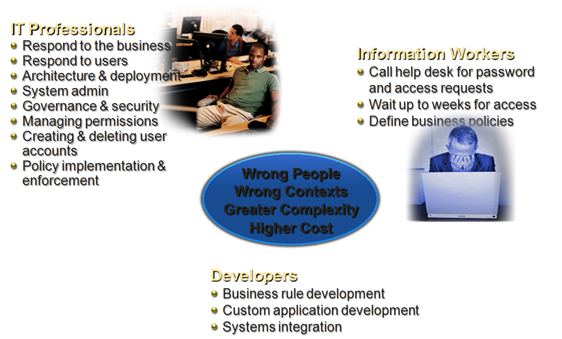
Today, the management burden is on IT
Today, we know that the burden of addressing these challenges is on IT. When you think about what identity and access management tasks IT typically involved in today, they include a number of things that IT should be doing – such as deploying and architecting software, administering systems, ensuring systems under their control are secure and compliant. But often IT is also burdened with additional, repetitive and often manual tasks such as managing end user requests such as password resets, creating and deleting user accounts and access in all the systems the end users need to do their jobs, and manually implementing, reporting on, and enforcing policies across these systems.
Meanwhile, end users are in a position where they are relying on IT for their requests. This means they are calling the helpdesk to get many credential and access related requests taken care of rather than focusing on their core job responsibilities, and they are waiting up to weeks for access to the systems they need to do their jobs when they join an organisation or switch roles. This can be very frustrating and unproductive for end users. Wouldn’t it make more sense for users to have the tools to do some of this work themselves and remove the burden from IT as well as themselves?
Developers are not immune from the complexity of this imbalanced management burden. Most organisations have a number of different identity and access management tools and a variety of underlying infrastructure, and developers (or external consultants) are often tasked with creating a series of one-off solutions stitching it all together. Shouldn’t this all be a lot easier to integrate?
Today identity and access management tasks are often being done by the wrong people, who are struggling with the complexity of existing systems and tools. In the end this means higher cost for the business:
Microsoft's Vision
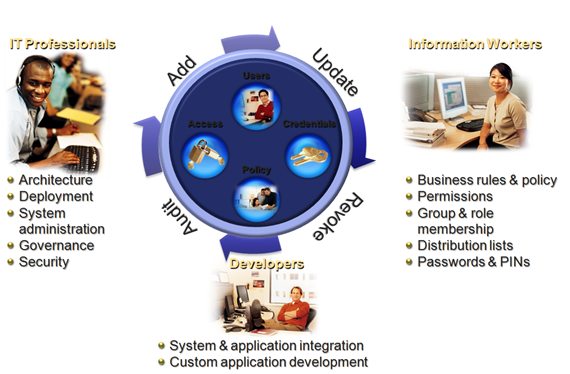
Microsoft has a vision for putting the identity and access lifecycle back into balance by aligning experiences with the right people.
IT professionals should be focused on what they do best – architecture, deployment, administration, governance, and security – roles that add value to the business and advance the view of IT as a strategic asset. IT should be in a position where they can put the controls and the tools in place to securely delegate those time-consuming user management requests to the users themselves.
Information workers should have familiar tools to manage their own information, credentials, access, and resources they own. For instance, if the sales organisation owns the CRM application, the business owner of that application should be able to make some of the rules and policy around who has access to the application and what permissions they have, rather than relying on IT to do this work. The business owner of this application needs a tool that where they can enter rules for the CRM system in natural language – not through writing code – and be able to report on the rules they have set as well as correct any violations. In addition, information workers should have tools within the applications and systems they use every day – such as self-service password reset integrated into the Windows logon, and the ability to manage their groups and distribution lists through Outlook and other Microsoft Office applications.
Developers shouldn’t have to spend their time stitching together systems. Microsoft’s vision for this space is to provide an identity lifecycle management solution that spans across a breadth of Windows and non-Windows infrastructure, and delivers management of users, access, credentials, and policy from a single, integrated solution that is easy to configure and customize if needed:
Changing the Equation
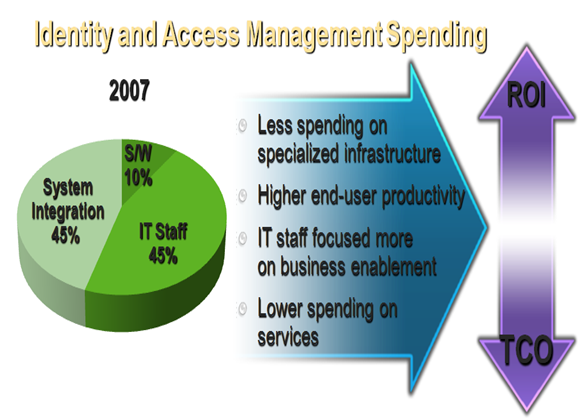
How will this alignment of experiences with the right people benefit your business? Lets look at the cost structure of identity and access management today for a typical company. Research from IDC, Gartner, and Microsoft shows that identity and access management software is only about 10% of the total amount that organisations spend. The rest of the identity and access management budget is spent on IT staff performing manual, repetitive tasks such as password reset and manual user provisioning and deprovisioning, and on internal developers or consultants writing custom code to integrate the complex infrastructure and tools in the environment.
What Microsoft wants to do is decrease the total amount your organisation spends on identity and access by providing a solution that reduces the need to spend all that IT budget on custom system integration and enables IT staff to do work that is more strategic for the business. The result of this decreased spend is
- Less spending on specialized infrastructure and tools to manage the complexity
- Higher end-user productivity from users who have the right tools at their fingertips, which are so easy to use they don’t call the help desk anymore
- IT staff focused more on business enablement than end user account, access, and credential related requests
- Lower spending on services since systems integration costs dramatically decrease
Microsoft believes that this solution will increase ROI and lower the TCO of your entire identity and access infrastructure. IDC recently completed a study comparing enterprise customers cost structures with some of these solutions in place. IDC found that customers can save
-£25 per PC per year with an automated user provisioning solution
-£60 per PC per year with a directory synchronization, password synchronization, and self-password reset solution
Roadmap for getting there
At the RSA Conference 2007, Microsoft announced a roadmap for helping customers realize this vision.
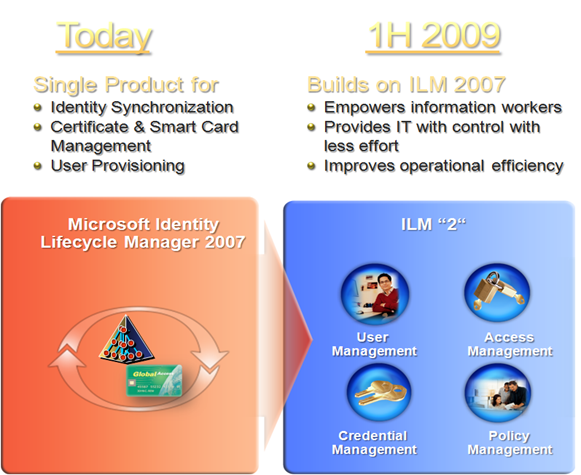
Today we have a product in market called Microsoft Identity Lifecycle Manager (ILM) 2007, a solution that builds on the metadirectory and user provisioning capabilities in Microsoft Identity Integration Server 2003 (MIIS) and adds new capabilities for managing strong credentials such as smart cards, providing an integrated approach that pulls together metadirectory, digital certificate and password management, and user provisioning across Windows® and other enterprise systems.
ILM 2007 is a unique offering in the marketplace today, no other vendor has a single product to manage users and their strong credentials. ILM 2007 also gets you on the path to achieve the vision of IT control with less effort by dramatically lowering the cost of deploying strong credentials as well as providing self-service tools for users to reset their smart card PIN.
In the 1st half of 2009, Microsoft plans to deliver Identity Lifecycle Manager ”2”, a comprehensive solution for managing user accounts, access via groups and roles, password and certificate-based credentials, and policies across Windows and heterogeneous environments. ILM “2” will extend the functionality of ILM 2007 with new capabilities that will (1) empower end users with integrated self-service tools in Office and Windows; (2) put IT in control through a robust delegation model and business process framework, and (3) increase operational efficiency by automating common identity lifecycle management tasks and empowering end users with self-help solutions. In addition, Microsoft is implementing ILM “2” on a common set of services – including workflow, delegation, web services APIs, and logging – that customers and independent software vendors can use to customize and extend the functionality in ILM “2”.
So, there you have it. In the next article I'll have a look at ILM 2007, our current product which has been successfully deployed to many customers in Ireland. Stay tuned for the next instalment!