Azure Disk Encryption - How to recover BEK file from Azure Key Vault
In today’s blog, we will demonstrate behavior of Azure Disk Encryption Extension and how it integrates with Key Vault and the Azure Platform to create and read the (BEK) secrets. It will also describe how you can recover the BEK file from the Key Vault in a scenario where you need to recover the data manually and need to unlock the drive.
If the Volume is encrypted with KEK then use steps in the blog -
How does Azure Disk Encryption unlock the disk
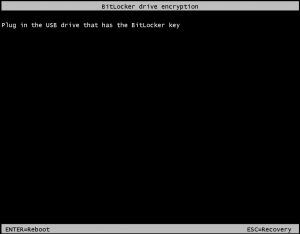
When we start the VM the encrypted key is read from the BEK volume which is on azure platform. If they BEK volume is encrypted or the BEK key is not present in BEK volume, then VM will not boot and you will see the below screen.
Steps:
- Stop the VM from Azure Management Portal. VM will go in Deallocated State.
- Copy the VHD file of the OS disk to a storage account to create a backup. You can use storage explorer to copy the vhd file. (https://storageexplorer.com ).
- Attach this copy of VHD file to a running Windows Server test VM as a data drive from azure portal.
- RDP to the running test VM and you can see the data disk with a drive letter. It will be locked by BitLocker, so you will need to use below steps to get the secret from azure key vault and unlock the volume.
How can you recover BEK files stored in Key Vault
It is possible to retrieve and extract these BEK files from Key Vault if you have a requirement to manually recover data from a VHD where the OS may not boot. This may also be useful if you are migrating a VM or restoring a VM in a Disaster Recovery scenario.
The BEK files are uploaded to the Key Vault as secrets of the Content Type “BEK”. The secrets themselves are recorded as the name of the BEK, and Tags are used to indicate the Machine Name and Volume Letter. To find the secrets for a specific VM you are working with you can use the below steps using Azure PowerShell command:
Pre-requisites: Install Azure Power Shell from /en-us/azure/powershell-install-configure
Connect to Azure Subscription using the below PS command.
Login-AzureRmAccount
Steps:
$vmName = "VMName"
$vault = "KeyVaultServerName"
# Get the Secret from Azure Key Vault if VM was encrypted with BEK
Get-AzureKeyVaultSecret -VaultName $vaultName | where {($_.Tags.MachineName -eq $vmName) -and ($_.Tags.VolumeLetter -eq "C:\") -and ($_.ContentType -eq 'BEK')}
OR
# Use the below command to get BEK keys for all the Volumes
Get-AzureKeyVaultSecret -VaultName $vault | where {($_.Tags.MachineName -eq $vmName) -and ($_.ContentType -eq 'BEK')}
#Convert the KeyVaultSecret to Base64
$keyVaultSecret = Get-AzureKeyVaultSecret -VaultName $vault -Name 06327EF7-XXXX-XXXX-XXXX-XXXXXXXXXXXX
$bekSecretBase64 = $keyVaultSecret.SecretValueText
The next step is to convert the Base64 encoded value to Bytes and then Write the output to a file. Please note, the BEK file name must match the original BEK GUID if using USB unlock option
$bekFileBytes = [Convert]::FromBase64String($bekSecretbase64)
$path = "c:\BEK\06327EF7-XXXX-XXXX-XXXX-XXXXXXXXXXXX.BEK"
[System.IO.File]::WriteAllBytes($path,$bekFileBytes)
Detail Steps with Results:
PS C:\> $vmName = "VMName"
$vault = "KeyVaultServerName"
PS C:\> Get-AzureKeyVaultSecret -VaultName $vault | where {($_.Tags.MachineName -eq $vmName) -and ($_.ContentType -eq 'BEK')}
Vault Name : keyvault
Name : 06327EF7-xxxx-xxxx-xxxx-xxxxxxxxx
Version :
Id : https://keyvault.vault.azure.net:443/secrets/06327EF7-XXXX-XXXX-XXXX-XXXXXXXXXXXX
Enabled : True
Created : 11/16/2016 10:06:12 PM
Updated : 11/16/2016 10:06:12 PM
Content Type : BEK
Tags : Name Value
VolumeLetter C:\
MachineName VMName
DiskEncryptionKeyFileName 06327EF7-XXXX-XXXX-XXXX-XXXXXXXXXXXX.BEK
DiskEncryptionKeyEncryptionAlgorithm RSA-OAEP
Once the BEK file is created on your PC, copy the BEK file to the azure VM where you can unlock the OS disk.
Open elevated command prompt and run below command, where F is the drive letter of the data disk.
C:\>manage-bde -status f:
BitLocker Drive Encryption: Configuration Tool version 10.0.14393
Copyright (C) 2013 Microsoft Corporation. All rights reserved.
Volume F: [Label Unknown]
[Data Volume]
Size: Unknown GB
BitLocker Version: 2.0
Conversion Status: Unknown
Percentage Encrypted: Unknown%
Encryption Method: AES 256
Protection Status: Unknown
Lock Status: Locked
Identification Field: Unknown
Automatic Unlock: Disabled
All Key Protectors:
External Key
Numerical Password
Since the volume is encrypted by BitLocker, it does shows that it is locked.
C:\>manage-bde -unlock f: -rk C:\06327EF7-4C0A-4846-95AB-9AEC07CCE257.BEK
BitLocker Drive Encryption: Configuration Tool version 10.0.14393
Copyright (C) 2013 Microsoft Corporation. All rights reserved.
The file "C:\06327EF7-4C0A-4846-95AB-9AEC07CCE257.BEK" successfully unlocked volume F:.
If the above command fails to unlock the drive, it means either the BEK file which you got from KeyVault is incorrect.
OR
The drive which is locked does not have the External Key Protector and someone has removed the protector manually using manage-bde command.
To check the External Key protector, use the below command from elevated command prompt:
manage-bde -protectors -get F:
where F is the drive letter of the volume.
References:
Azure Disk Encryption: https://azure.microsoft.com/en-us/documentation/articles/azure-security-disk-encryption/
Whitepaper with detail steps: https://gallery.technet.microsoft.com/Azure-Disk-Encryption-for-a0018eb0
Comments
- Anonymous
December 09, 2016
The comment has been removed- Anonymous
January 05, 2017
The comment has been removed
- Anonymous