Azure Disk Encryption - Convert BEK Disk Encryption to KEK for Azure Recovery Services
Convert BEK Disk Encryption to KEK for Azure Recovery Services
A common desire is to convert Azure IaaS VM's that were encrypted using only BEK to also using KEK in order to take advantage of Azure Recovery Services. In this scenario, you do not need to decrypt your VM, rather simply enable with a KEK key using the following steps:
Steps:
Pre-requisites: Install Azure Power Shell from /en-us/azure/powershell-install-configure
Connect to Azure Subscription using the below Azure Power Shell command.
Login-AzureRmAccount
To use Azure backups there is a requirement to use KEK to encrypt the VHD files using azure disk encryption process. You will use your existing Key Vault Server which is used for backing keys and secrets for disk encryption.
Step 1: If you have a VM which is already encrypted without BEK, then you want to encrypt with KEK, use the ARM template or PS cmdlet below to change from noKEK to KEK.
Use the below command to add a Keyvaultkey.
This command creates a software-protected key named ITSoftware in the vault named Contoso.
Add-AzureKeyVaultKey -VaultName 'Contoso' -Name 'ITSoftware' -Destination 'Software'
To get full version of KEK URL run below PS cmdlet.
Get-AzureKeyVaultKey -VaultName <KeyVaultName> -Name <KEKName>
Example:
{"kid":"https://keyvault.vault.azure.net/keys/deKEK/9e7ec10d95a84585abdbb2611070c820","kty":"RSA","key_ops":["encrypt","decrypt","sign","verify","wrapKey","unwrapKey"],"n":"oOEexAcY1zIFxEcKqM5Fn6rJYEiQsZubcuRwpoIzE6f5Fqfk4Huro-Gbn5WUPc81japyhzGVZMvBApUY0458F3HNCxvtc5Xszq570HOsMtyi9z8AgF_ZJUZ7rGgnpACcztuIhv2vsAASy-Wg3ELSU6AWA-6ijbehKLSoUG-1XRMLR7t8LQGZcv42V0P-crW17lUyk3AYF86KvA1hnux-6IKtqfGKZEzCeYoORtHka7R1d2G8AdYkHN7qcnIsm0Kxk71qU6PJzTiKRum69d581sZOcpNFGJQiF5dEfZBKnSTxdQvG1u9YDVekvXvHsnXqc9K6oHxs3PbpgAxWAr_qew","e":"AQAB" VaultName : <keyvaultname> Name : <keyencryptionkeyname> Version : 9e7ec10d95a84585abdbb2611070c820 Id : https://<keyvaultname>.vault.azure.net:443/keys/<KeyEncryptionKeyName>/9e7ec10d95a84585abdbb2611070c820
- Now you have the KEK URL, use the below ARM template to encrypt the VM, supply the KEK.
https://github.com/Azure/azure-quickstart-templates/tree/master/201-encrypt-running-windows-vm 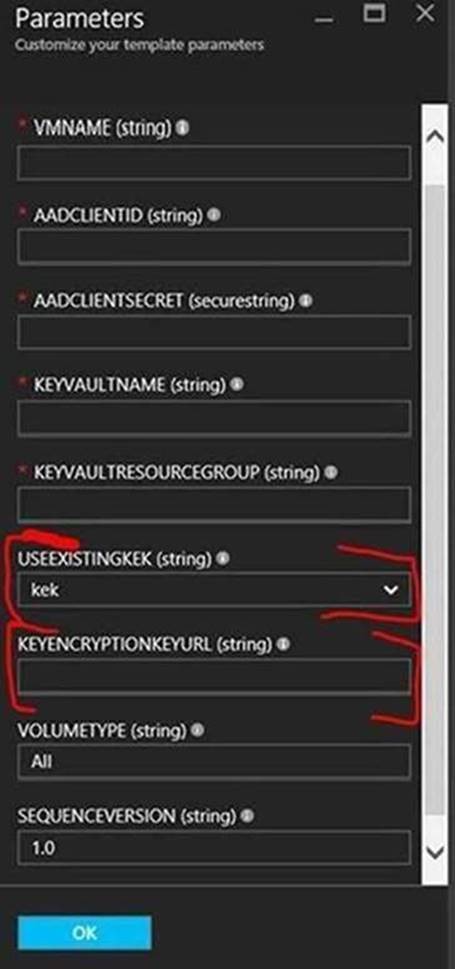
OR
PowerShell Command:
Set-AzureRmVMDiskEncryptionExtension -ResourceGroupName $rgname -VMName $vmName -AadClientID $aadClientID -AadClientSecret $aadClientSecret -DiskEncryptionKeyVaultUrl $diskEncryptionKeyVaultUrl -DiskEncryptionKeyVaultId $KeyVaultResourceId -KeyEncryptionKeyVaultId $KeyVaultResourceId -KeyEncryptionKeyUrl 'KEK URL which you got from above command where it shows the KEK id’ -VolumeType Data
Example of KEK id: https://keyvaultserver.vault.azure.net/keys/ITSoftware/1848053030b64216a476ab53f7c5fc5f
Azure backup:
To enable the protection on encrypted VMs [encrypted using BEK and KEK], you need to give permissions for Azure Backup service to read keys and secrets from key vault.
Set-AzureRmKeyVaultAccessPolicy -VaultName 'KeyVaultServerName' -ResourceGroupName 'RGName' -PermissionsToKeys backup,get,list -PermissionsToSecrets get,list -ServicePrincipalName 262044b1-e2ce-469f-a196-69ab7ada62d3
Get-AzureRmKeyVault -VaultName $keyVaultName
Get-AzureRmRecoveryServicesVault -Name "ARSName" | Set-AzureRmRecoveryServicesVaultContext
$pol=Get-AzureRmRecoveryServicesBackupProtectionPolicy -Name "NewPolicy"
Enable-AzureRmRecoveryServicesBackupProtection -Policy $pol -Name "NameofVMtoBackup" -ResourceGroupName "RGNameofVM"
Reference:
Deploy and manage backups for Resource Manager-deployed VMs using PowerShell
/en-us/azure/backup/backup-azure-vms-automation
Backup and restore encrypted VMs using Azure Backup: /en-us/azure/backup/backup-azure-vms-encryption
Taking backup of encrypted Azure VMs with ADE (Azure Disk Encryption) using Azure Backup in OMS
Add-AzureKeyVaultKey Reference: https://msdn.microsoft.com/en-us/library/dn868048.aspx