Intune Managed mobile devices fail to list the apps deployed to security groups synched from on-premise
Recently I came across an interesting issue while working on an Intune deployment, and wanted to share the solution steps.
SCENARIO:
In the Intune portal, groups have been created with multiple levels of nesting. User membership criteria has also been configured for the nested groups. However, the users do not get the Intune managed applications on their portal even though they have been assigned.
RE-PRO AND TROUBLESHOOTING:
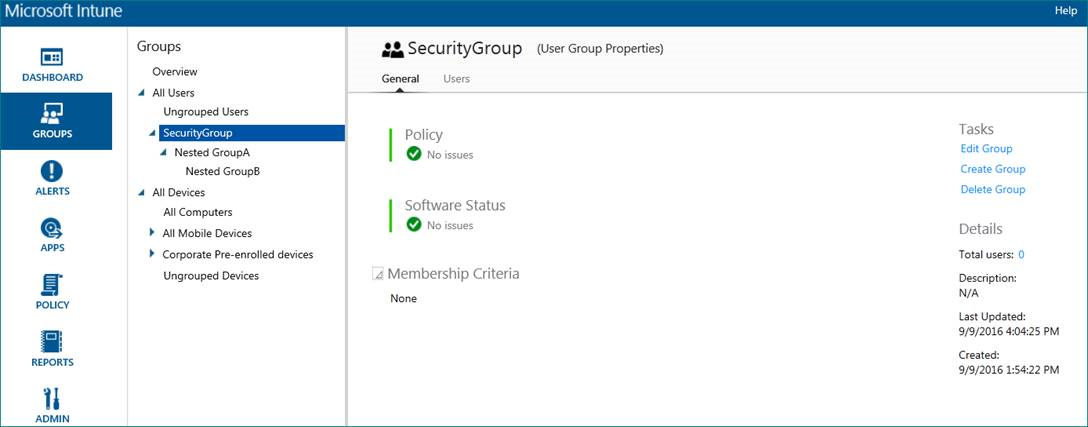
To validate if this is a tenant-specific issue, I went ahead and setup a test scenario in my lab tenant and I could quickly reproduce the same problem as the customer. As can be seen in the screen snippet below, the Parent group is named “Security Group" with two nested groups - Group A and Group B .
In-built LOB applications are deployed to the nested groups and none of the devices were receiving any of the deployed apps on the company portal. At this point, we should already have our security groups reflecting on the office 365 and Azure portals.
We checked the Azure AD sync(AADSync) environment and we could confirm that the nested groups are already linked with the necessary on-premise groups. But for some reason not known yet, the desired applications do not get listed on the company portal application on the end user devices.
The screen snippet below shows the membership criteria for the parent group where no criteria is assigned.
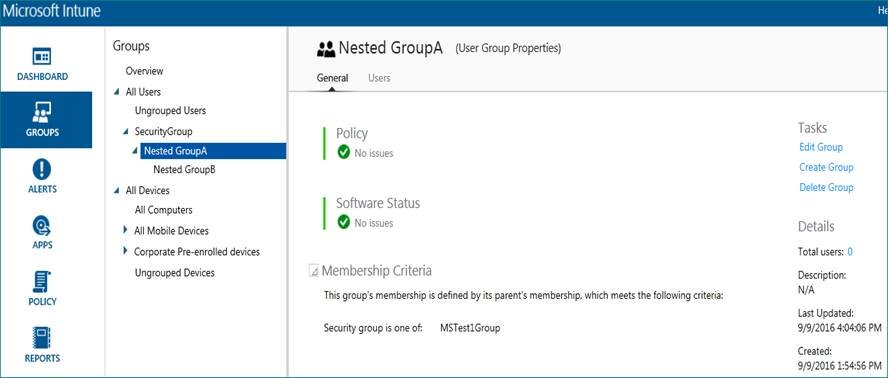
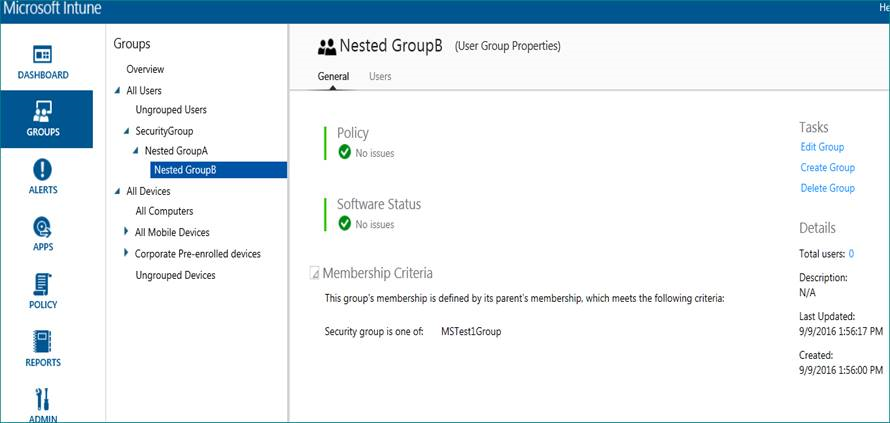
Whereas the nested groups are already assigned with membership Criteria. See screenshot below.
To rule out device specific issues, we tested it across various platforms but none of them listed the applications that were published for download.
After further research and troubleshooting we identified that the problem was related to Membership criteria inheritance. Even though we have added the membership criteria to the nested groups, the parent group ( top-level group) does not have any criteria configured. So, to resolve this issue we added the same on-premise synced security group to parent group(top-level group). Following that, we were able to see the users who are synced through Azure Active Directory and also deployed applications on the company portal for all device platforms.
I hope this blog provides the general troubleshooting approach, when you are seeing similar group issues with respect to applications deployed. The key takeaway here is to understand that parent security group should have on-premise synced groups as their membership criteria in order for the nested groups to inherit and apply the same.
Happy troubleshooting !!
Dheeraj Kollipara
Intune | Mobility Support Team
Comments
- Anonymous
October 17, 2016
Interesting ! Thanks for sharing it