SCHANNEL event logging
First, my thanks to Bhuvnesh Kumar for his help!

Time to figure out what's going on behind the curtain!
Are you seeing System Event Log, Event ID 36871 events?
Why does this matter?
Depending on OS versions and patches, the TLS Cipher Suites may not match on the various SCOM servers.
- If you're setting up TLS1.2, you need the SCOM servers to talk
- The bad part, is this isn't logged much on the GW but log more often on MS
- Sometimes the 36871 events come with 36874, but in my experience they occur after Event Logging is enabled.
The unanswered question is "why are we seeing the 36871 events?"
In my example, the events only happened once a day, roughly 24 hours
Event Viewer 
Are events related to the Cipher Suite, or is it a MP trying to run the old SQLOLEDB method?
This article will focus on verifying Cipher Suite on a server
See this article for MP analysis for SQL methods
SCHANNEL event logging setup
From Holman's blog
| Decimal | Description |
| 0 | Do not log |
| 1 | Log Error messages |
| 2 | Log Warnings |
| 3 | Log Error and Warning messages |
| 4 | Log Informational and Success events |
| 5 | Log Error, Informational and Success events |
| 6 | Log Warnings, Informational and Success events |
| 7 | Log Everything (Warnings, Errors, Informational and Success events |
I’d recommend setting it to 3 to see errors and warnings, or 7 to see everything.
Remember to set this back to 1 when done resolving any issues.
Add
From Command Prompt or PowerShell (as administrator)
reg add "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL" /v "EventLogging" /t REG_DWORD /d 7 /f
Disable
reg delete "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL" /v "EventLogging"
Verification
reg query "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL" /v "EventLogging"
PowerShell verification 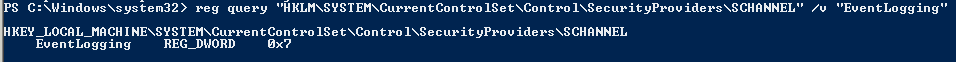
RegEdit Verification 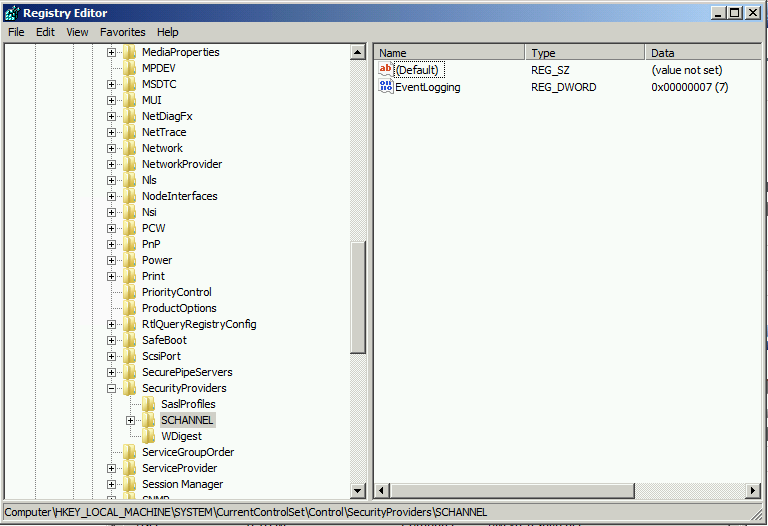
Time to reboot!
Verify SCHANNEL events
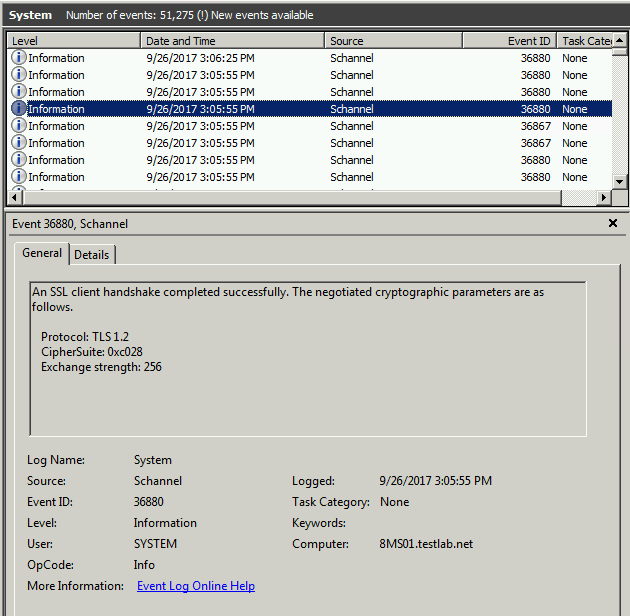
Look at the System Event log, and filter for 36880 and 36874 events for clues
36880 provides Cipher Suite details
Event ID 36874 definitely describes the scenario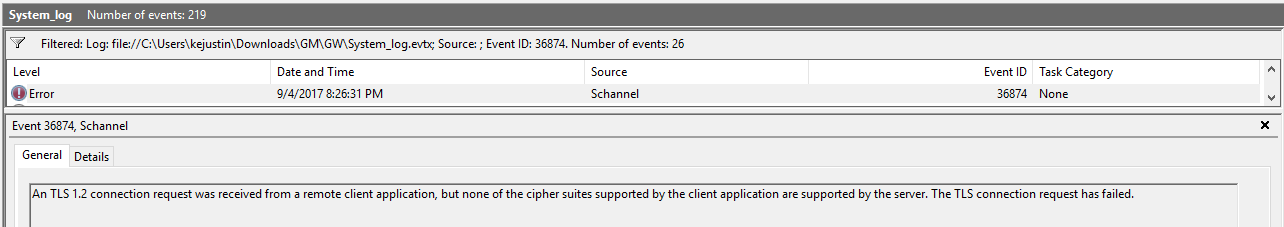
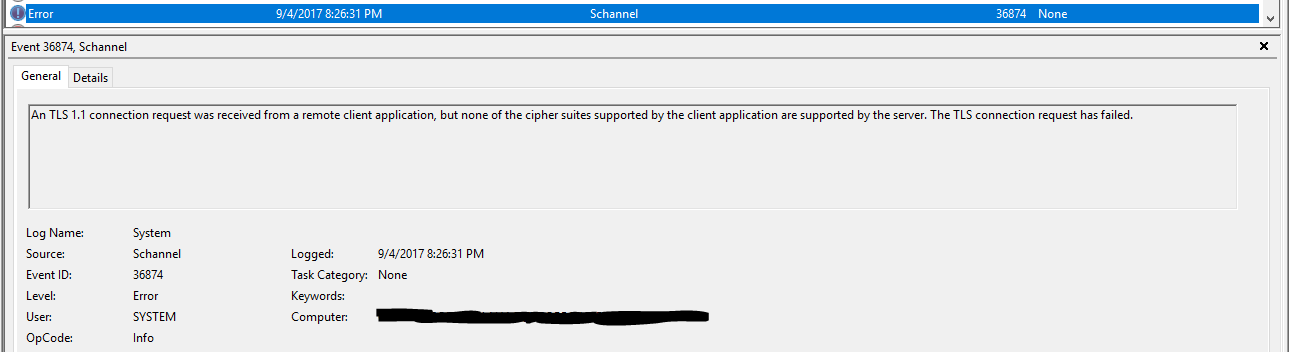
The easy answer to solve the cipher suite is to ask - is this server patched with latest security and .NET patches?
After all this, in my example, we confirmed that simple step was assumed, and inaccurate.
References
36871 event https://technet.microsoft.com/en-us/library/dn786445(v=ws.11).aspx#BKMK_36871
SCHANNEL events https://technet.microsoft.com/en-us/library/dn786445(v=ws.11).aspx
SChannel error codes https://msdn.microsoft.com/en-us/library/windows/desktop/dd721886(v=vs.85).aspx
SChannel events https://technet.microsoft.com/en-us/library/dn786445(v=ws.11).aspx
SSL errors https://support.microsoft.com/en-us/help/305088/schannel-error-message-36871-when-receiving-an-ehlo-smtp-command
Troubleshooting /en-us/iis/troubleshoot/security-issues/troubleshooting-ssl-related-issues-server-certificate
Comments
- Anonymous
September 05, 2018
Interesting, this is exactly what I need, but its not returning results related to the error I'm investigating. Schannel 36871 reports"A fatal error occurred while creating a TLS client credential. The internal error state is 10013." but then the following errors that now appear as a result of the above reg keys only report smooth sailing, until the next 36871 shows up.- Anonymous
September 06, 2018
Mike,Yes, that is expected. Blog updated. In my example, the 36871 events only happened once a day, roughly every 24 hours. My example was a gateway checking in to MS.- Anonymous
September 06, 2018
Thanks for the speedy reply! In my case, i can repro the 36871 error, as it occurs each time outlook authenticates to a certain ADFS farm. I've looked at wireshark and from what i can tell, the handshake and ChangeCipherSpec occurs happily, yet, outlook re-prompts for auth and i get a 36871. I was hoping that this logging would give additional insight into what the problem is, but it doesn't have any complaints between the 36871 events. I've also tried looking at the outlook diag etl files through microsoft message analyzer and wireshark, but I'm not finding auth errors. :( Happy to take any advice, though I understand this is beyond the scope of your article!
- Anonymous
- Anonymous
- Anonymous
January 30, 2019
Very good contribution. I have a query within this theme:How can we know "when" a TLS protocol change was made in a Windows Server 2008 R2 server for example? For the purposes of forensic evaluations, it would be interesting to know- Anonymous
February 01, 2019
Hello,What do you use for validating compliance in your environment?There are various methods - registry key, patchI'd start by looking at these 2 sites for more information:https://support.microsoft.com/en-us/help/3140245/update-to-enable-tls-1-1-and-tls-1-2-as-default-secure-protocols-in-wihttps://docs.microsoft.com/en-us/windows-server/security/tls/tls-registry-settings
- Anonymous