Enforcing Multi-Factor Authentication for External Users on SharePoint Online
Many of my customers have often asked if there is a way to require Multi-Factor Authentication (MFA) when external users connect to SharePoint Online or OneDrive for Business. If you are interested in requiring MFA for internal users, please read our existing support articles. Below I will outline a way to achieve this today for external users.
Using the AzureAD subscription associated with the Office365 tenant, we can accomplish this through creating a Dynamic Group for the "External Users", and then using this with a new Conditional Access policy which we can apply to SharePoint Online.
Create a Dynamic Access Group of "External User" accounts
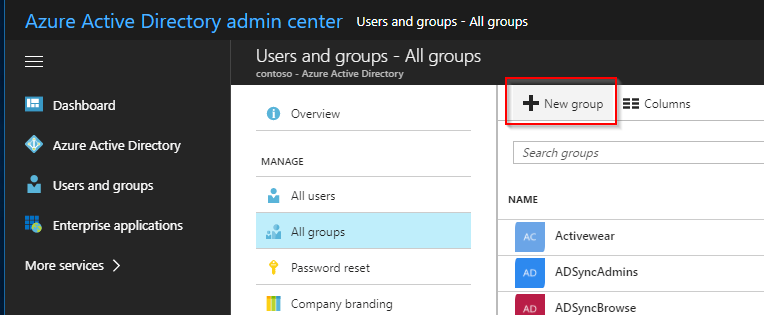
- Login to AzureAD Portal, and navigate to Azure Active Directory -> Users and Groups -> All groups and click on New Group
- Give your group a friendly name, description, and select Membership type of Dynamic User. If you do not see this Membership type, it may be that you do not have AzureAD Premium licenses in your subscription. (See licensing requirements below)
- Select Add dynamic query, and create a Simple Rule in which you add users where userType Equals Guest
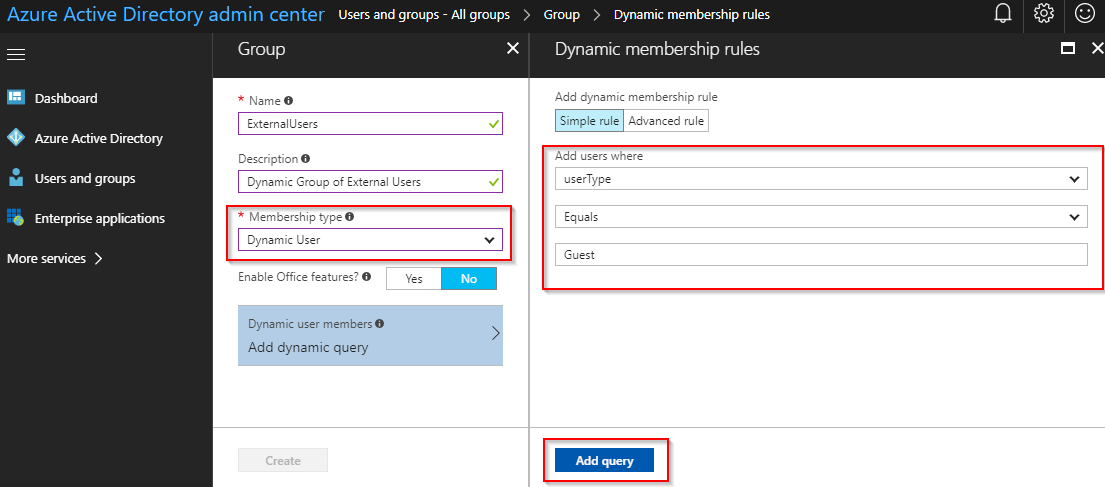
- Click Add query -> Create in order to make the dynamic group
For more advanced group targeting scenarios, please see here: /en-us/azure/active-directory/active-directory-groups-dynamic-membership-azure-portal
It will take some time for the group to populate, so take advantage and brew up a fresh batch of coffee because the fun hasn't ended yet.
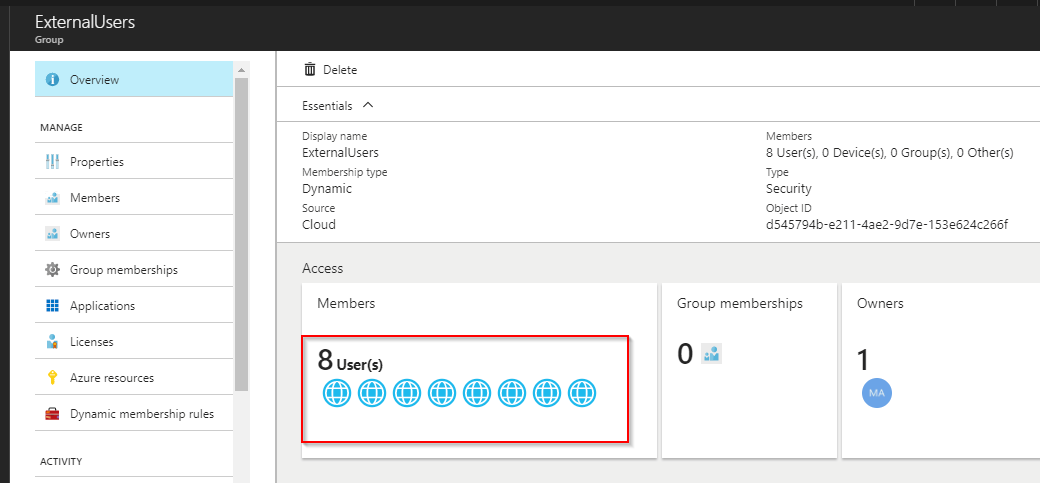
To confirm the dynamic group has external members, search for the friendly group name under Users and Groups -> All Groups and click on it to open it and review. Look at all those wonderful blue globe things representing the external users in the group!
Create a Conditional Access Policy for SharePoint Online
- Login to AzureAD Portal, and navigate to Enterprise applications -> Conditional access to show all Conditional access policies, and then click on New Policy
- On the New blade, in the name text box, type a friendly name for the policy
- On the Users and Groups blade, select Include -> Select users and group -> Select
- Search for the External Users group you created in the previous step and select that group
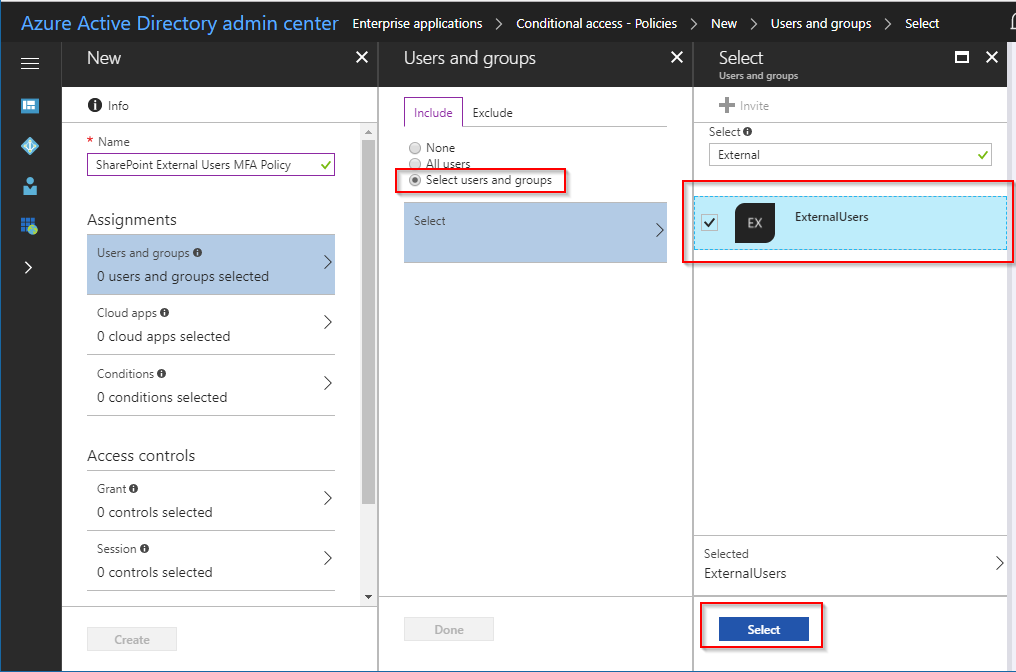
- Click Select and then click Done to ensure you are including the External Users group that you previously created
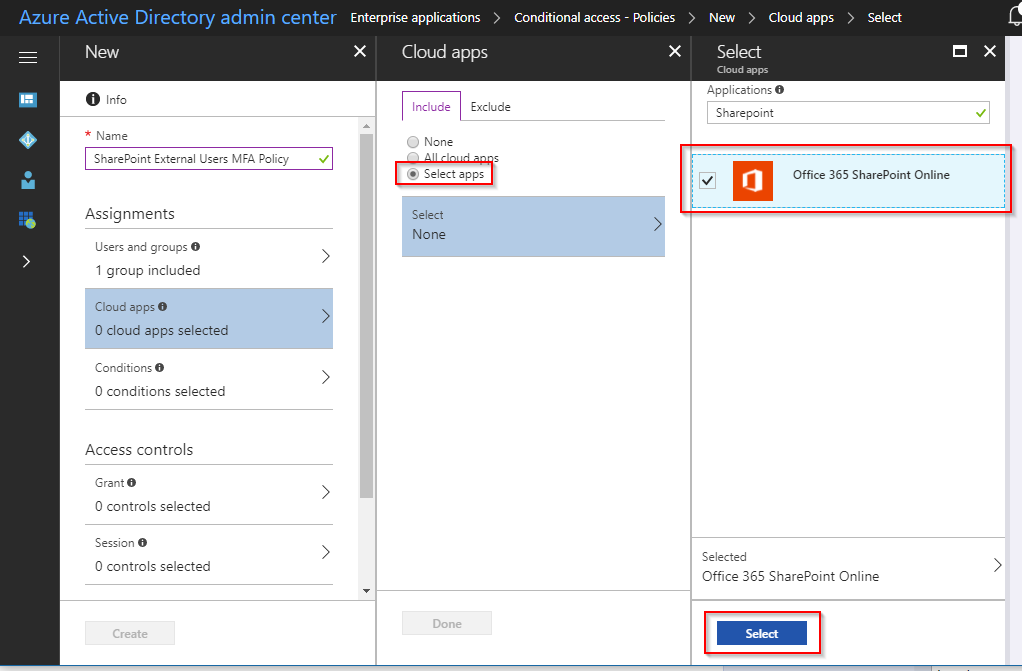
- On the Cloud Apps blade, click the options for Include -> Select apps -> Select
- Under Applications search for SharePoint and select Office 365 SharePoint Online. Apply this by clicking on Select and Done
- On the Conditions blade, select Locations. Select Yes for Configure. Include Any Location.
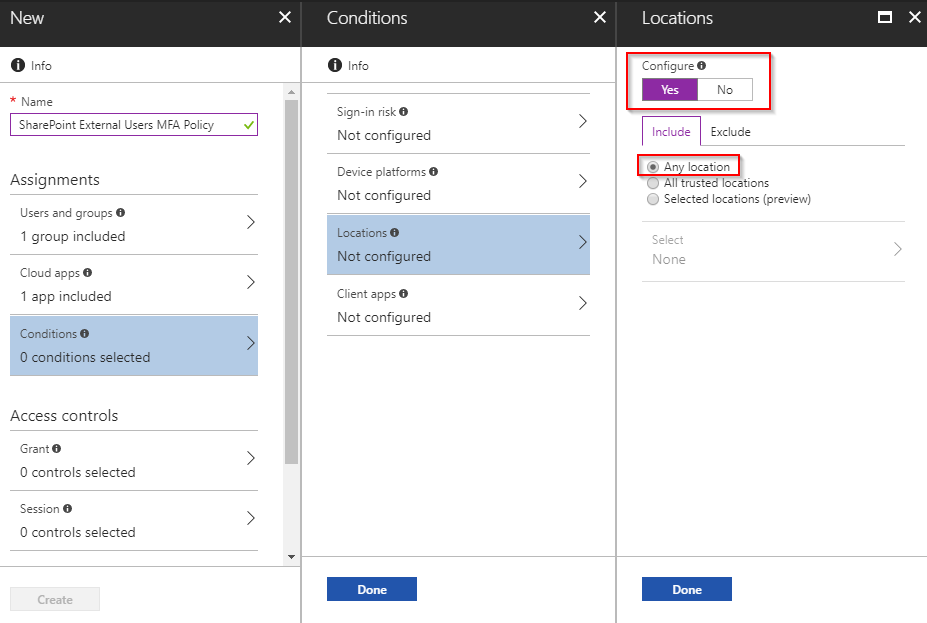
- Apply these by selecting the Done buttons
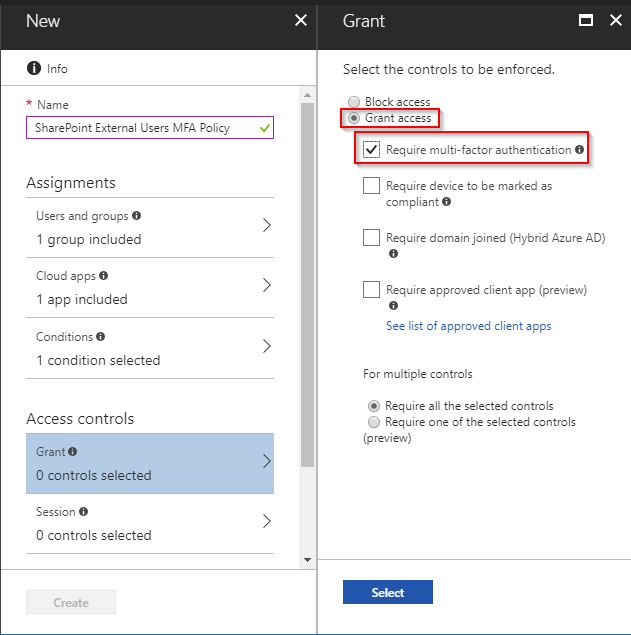
- On the Grant Blade, select Grant Access and Require Multi-Factor Authentication. Click Select to apply the Grant restrictions.
- Finally, toggle the Enable policy button to On, and then Create the policy
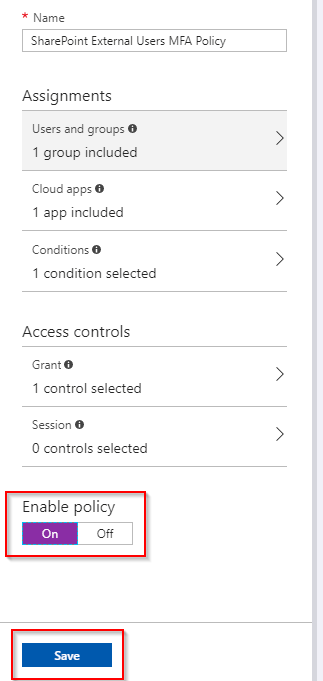
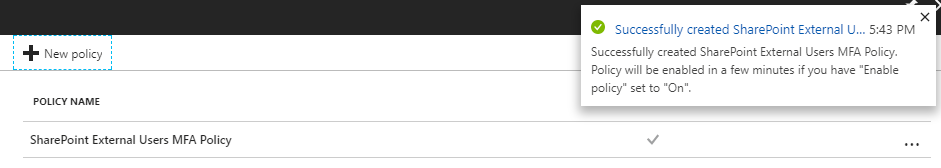
To verify the policy was created successfully you should now see it under the Conditional Access Policies
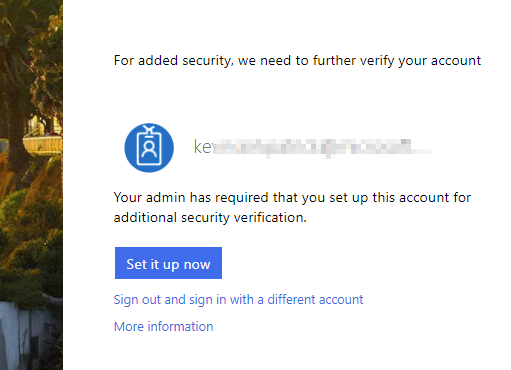
In a few minutes, when external users attempt to access a resource in SharePoint Online or OneDrive for Business, they should be prompted to set up MFA upon sign-in. Using MFA, external users would be required to acknowledge a phone call, text message, or app notification on their phone after completing their initial authentication process.
I am hoping this helps provide some guidance to enforcing MultiFactor Authentication for External Users
Licensing Notes*
One reason people use SharePoint Online is that you do not have to give an external user a license to use Office365. The approach I am outlining here will utilize some Azure AD Premium features, so there is the potential for licensing impact. However if your organization already leverages AzureAD Premium, this may be covered already in AzureAD B2B licensing..
Azure AD Premium features are used in two areas throughout this approach:
- AzureAD Dynamic Groups were used to group "all external users"
- AzureAD Conditional Access Policies
At the time of this writing, an inviting tenant with an Azure AD paid license has B2B collaboration use rights to an additional five B2B guest users invited to the tenant. So as an example, if you have 10,000 Azure AD Premium P1 licenses, you can leverage B2B collaboration features with up to 50,000 external guest users.
*This blog is absolutely not an official source for Microsoft's Licensing. If you have an official licensing query, please contact your Microsoft Licensing Specialist.
Additional References:
/en-us/azure/active-directory/active-directory-conditional-access-azure-portal /en-us/azure/active-directory/active-directory-accessmanagement-groups-with-advanced-rules
Comments
- Anonymous
February 13, 2018
Helped a lot. Thank you. - Anonymous
March 25, 2018
This only works where the invited party has an Azure AD account (i.e in their organisation). It doesn't work for consumer accounts such as @gmail.com. I logged a PS call to check as I couldn't get it to work for consumer accounts and the support team confirmed that B2B supports MFA but not B2C.