Azure App Service Authentication - Using a Blob Storage for Token Cache
Chris had this note in his blog App Service Token Store
“As an alternative, you can provision an Azure Blob Storage container and configure your web app with a SaS URL (with read/write/list access) pointing to that blob container. This SaS URL can then be saved to the WEBSITE_AUTH_TOKEN_CONTAINER_SASURL app setting. When this app setting is present, all tokens will be stored in and fetched from the specified blob container.”
This is still in preview but very useful. For example, you would lose your token cache when doing a slot swap on your site from a test to production slot.
Here is a walkthrough on how to add this to your Azure Web App
Create a Storage resource in Azure using the defaults. Put it in the same region as your web app for performance reasons
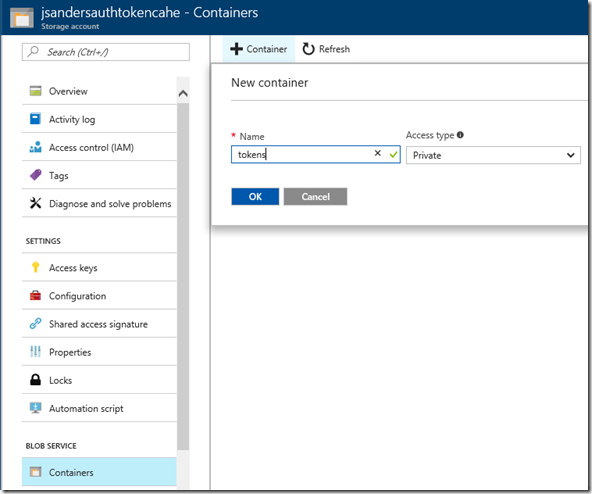
Create a container in the BLOB SERVICE of the storage you created using the default settings and call it tokens
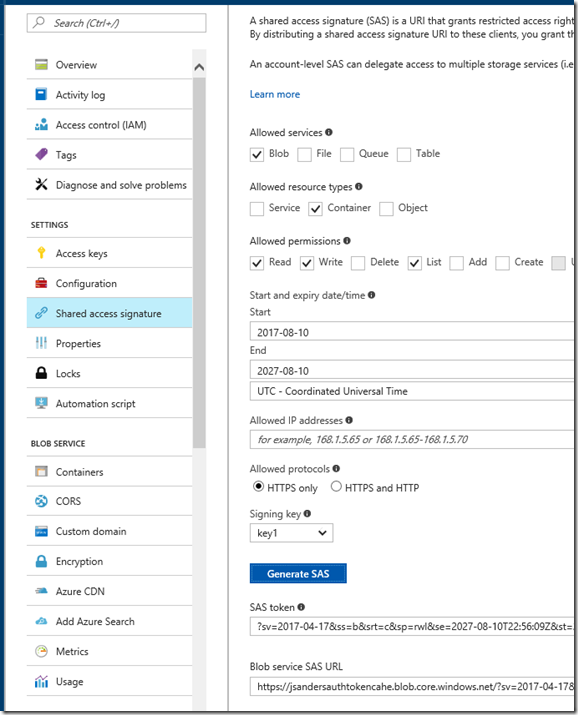
Create a Shared access signature (SaS) token so we can access that container. Note the options I chose and that I set the expiration date out 10 years in the future (You probably want a shorter date like 2 years out and renew it then):
Copy the Blob Service SAS URL, pasted in notepad and add the container name to the URL:
Open your Azure App Service, create an Application called WEBSITE_AUTH_TOKEN_CONTAINER_SASURL and paste the modified SAS Url you just created.
That is it!
Troubleshooting
Turn on verbose application logging in the Azure App Services and take a look at the application logs. They will give you any errors and reasons for those errors.
For instance:
2017-08-10T18:36:05 PID[15432] Verbose Calling into external HTTP endpoint PUT https://jsandersauthtokencahe.blob.core.windows.net/4ca06726d07351d870a15c6c9e8f21a9.json.
2017-08-10T18:36:06 PID[15432] Warning Call to HTTP endpoint https://jsandersauthtokencahe.blob.core.windows.net/4ca06726d07351d870a15c6c9e8f21a9.json failed: 404 (The specified container does not exist.). Partial response: <?xml version="1.0" encoding="utf-8"?><Error><Code>ContainerNotFound</Code><Message>The specified container does not exist.
RequestId:edd0e5f3-0001-0020-3707-12cfb6000000
Time:2017-08-10T18:36:04.1903028Z</Message></Error>
The problem was that I didn’t add tokens to the SAS URL
Success:
2017-08-10T18:39:19 PID[14048] Verbose Calling into external HTTP endpoint PUT https://jsandersauthtokencahe.blob.core.windows.net/tokens/f49bd000cd8e0ef29cf366858383b834.json.
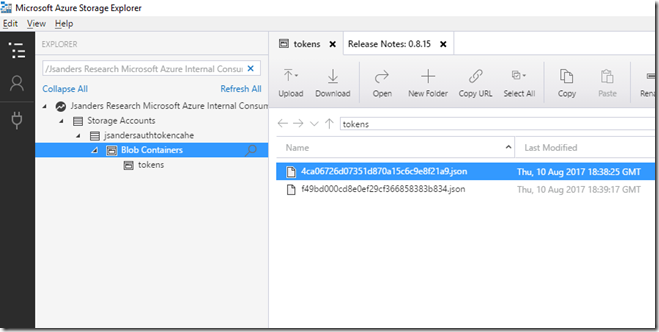
You can see these tokens for your self by using the Microsoft Azure Storage Explorer: https://storageexplorer.com/
Comments
- Anonymous
January 30, 2018
Do you know if this experimental feature soon will be available?Is it unsafe to enable this in production servers? I'm thinking that the disk space allocated for tokens could run out and then what do we do?- Anonymous
January 31, 2018
I do not know Martin. You can ask in his blog App Service Token Store (at the top of the article) or posting on StackOverflow (please tag your questions with azure-app-service or azure-web-sites)
- Anonymous