Extracting modules (EXE, DLL, and other binaries) from memory dump..
Yet another debugging challenge.
Imagine a situation where you get a memory dump from customer and need modules (DLL, EXE, OCX etc.) to further debug.. (.NET modules can be used to look at source code by reverse engineering..)
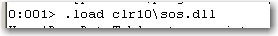
SOS.dll is at the rescue. We can use clr10\sos.dll inside windbg directory to save all the modules (loaded by target process at the time of taking the memory dump). Interesting fact is, sos.dll can not only extract managed modules, it can also save all the native/unmanaged modules!!
First, load the sos.dll in windbg.
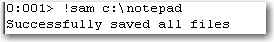
Then use !sam <path> OR !SaveAllModule <path> to extract the modules on specific disk location..
Thats it! Mission accomplished. Though, its not a long process, it can be useful in some scenario..
PS: Later version of sos.dll does not support !sam, you need to manually extract each and every module by providing the loading address.
Stay tuned..