SYSK 305: What is a MITM attack?
MITM stands for man-in-the-middle… A MITM attack is where an attacker is able to read, insert and modify messages between two parties without either party knowing that the link between them has been compromised.
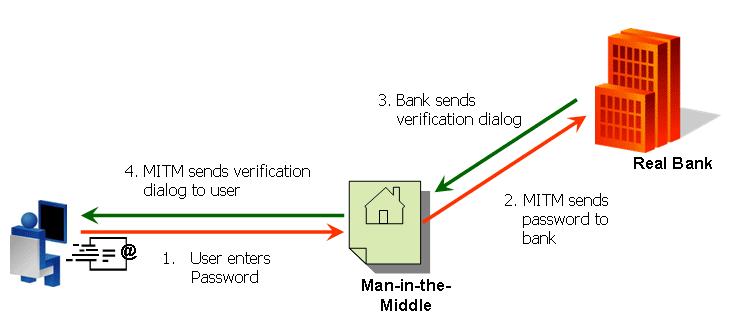
For following picture from http://www.arcot.com/mitm/index.html demonstrates the concept:
Some may think that using secure HTTP (https) eliminates the possibility of a MITM attack. Unfortunately, there are several ways a malicious person can perform a MITM attack even if SSL is used, including ARP poisoning, DNS hijacking, DNS cache poisoning, DHCP message subversion/take-over, gateway take-over with GARP, HSRP, VRRP, IRDP, STP, EIGRP, ICMP redirects, etc.
So, what can you do to protect against these types of attacks?
For starters, don’t use your wireless connection for transmitting any sensitive information. Next, make sure you’re using a web application firewall, in addition to your traditional firewall/router.
Finally, get educated about IPSec encryption, DNSSEC for DNS, DHCP Snooping, IP/MAC Source-Guard, Dynamic ARP Inspection, and static ARP entries. While, as an individual user some of this is not under your control, understanding security issues and ways to address them should enable you to make smarter decisions about the sites you use, the companies you do business with, etc.
And, as always, keep checking for what’s new in the world of security – hackers are becoming increasingly more sophisticated and it’s a constant tug-a-war between the “good guys” and those who are trying to access data without authorization or just to harm.
Sources:
http://en.wikipedia.org/wiki/Man_in_the_middle
http://www.arcot.com/mitm/index.html
http://sla.ckers.org/forum/read.php?6,7024,7048#msg-7048
Comments
Anonymous
March 13, 2007
It is quite easy if you want a nice local demonstration chec out Fiddler2 <a href="http://www.fiddler2.com/fiddler2/">Anonymous
March 13, 2007
Great advice as always, Irena. There is just one thing I didn't really get a grip on and that was "use a web application firewall". Never heard of it and can't even imagine what it could be :PAnonymous
March 13, 2007
The following is copied from http://www.cgisecurity.com/questions/webappfirewall.shtml: Standard firewalls are designed to restrict access to certain ports, or services that an administrator doesn't want unauthorized people to access. Web Application Firewalls are often called 'Deep Packet Inspection Firewalls' because they look at every request and response within the HTTP/HTTPS/SOAP/XML-RPC/Web Service layers. Some Web Application Firewalls look for certain 'attack signatures' to try to identify a specific attack that an intruder may be sending, while others look for abnormal behavior that doesn't fit the websites normal traffic patterns. Web Application Firewalls can be either software, or hardware appliance based and are installed in front of a webserver in an effort to try and shield it from incoming attacks. Information on the types of 'signatures' that a web application firewall may use can be found in the "Fingerprinting Port 80 Attacks" papers in our Articles section An open sourced Web Application Firewall for the Apache Webserver named Mod_Security can be found at http://www.modsecurity.org