The Reverse Engineering Mindset – The Reverse Engineering Principle (REP) Series
Hello friends – It would be neglectful for the INT 3 blog to initialize without discussing the fundamental principles necessary to develop the reverse engineering mindset. Last month I spoke at an internal, biyearly Microsoft conference in Seattle. The talk focused on my experience debugging a troublesome z-order bug causing a logon window to disappear while users attempted to logon to a third-party application from their field locations. Debugging z-order issues is an ugly business. Before stepping the audience through the debugger output projected on the big screen in the session room, I asked the question, “where do you start debugging an issue when there is no error message generated, no crash dump created, no blocking threads to examine, no event log message logged, nor any ETW trace output generated? Where is the debugging entry point for an elusive disappearing logon window?”
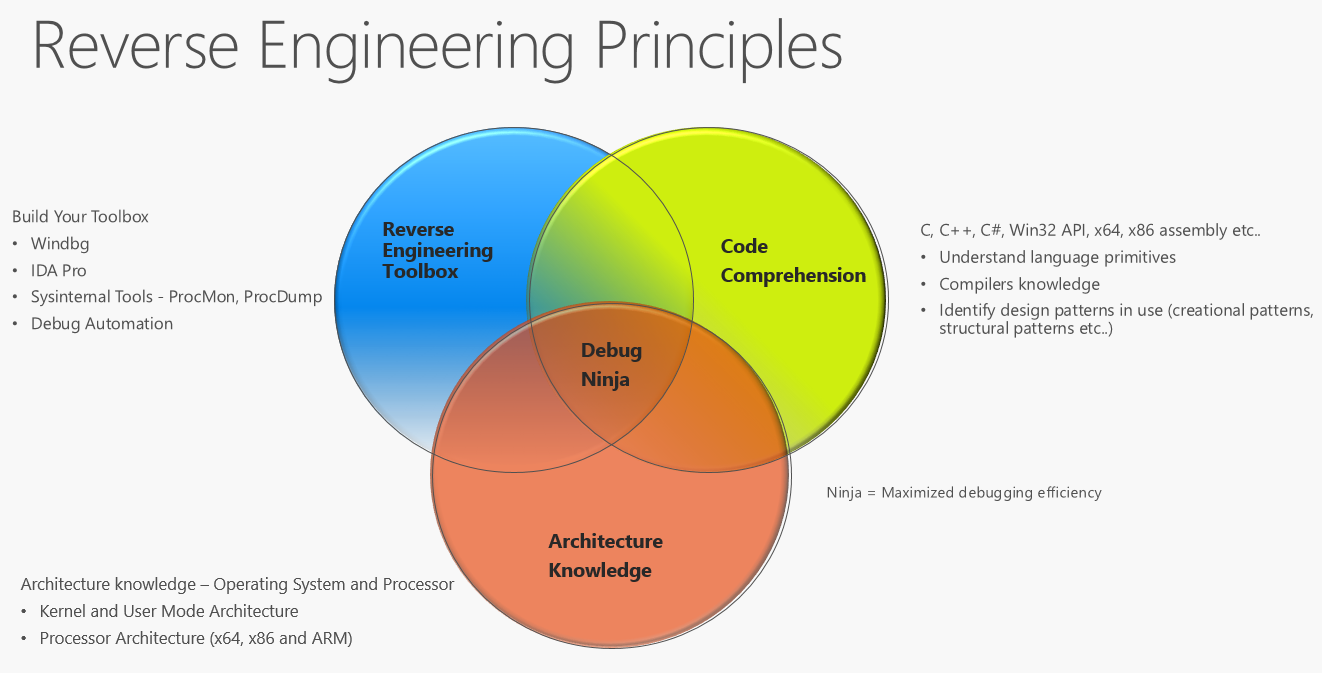
The answer culminated into a discussion of the three “Reverse Engineering Principles” I have strived to cultivate over the last eighteen years. First I discussed the importance of building your reverse engineering toolbox by mastering tools such as Windbg, IDA Pro, debug extensions such as MEX, debug scripts, and the Sysinternals suite. Note: IDA Pro is great to have but there are also free disassemblers available including BeaEngine located here. We spent time discussing the importance of solid code comprehension skills which includes understanding language primitives, identifying design principles and possessing a familiarity with compiler specifics. This includes assembly language for both x64, x86 or whatever target platform is necessary. Then I wrapped up by deliberating on the importance of having a reasonable level of architecture knowledge including both operating system and processor semantics. Growing in all three of these areas will continue to develop the reverse engineering mindset.
Over the next couple of months, I will unpack these principles in a 'Reverse Engineering Principles' series named REP for short. The series will be loaded with sample assembly snippets, C code examples and Windbg walkthroughs. The first REP article in the series will pay homage to Matt Pietrek’s ‘Under the Hood’ article from February of 1998 with extended register and assembly walk-throughs. You can also count on Trey and Dan to run concurrent series and articles discussing other topics.
If you’re curious about the debugging starting point for the disappearing logon window issue, knowing the GDI architecture and how WinEvents operate (e.g. REP Principle of Architecture Knowledge) pointed me to my debug entry point.
And one more thing before we part ways this week - I mentioned the MEX tool above. MEX is a newly released debug extension for Windbg sustained by my team. Our design goal is to make you ‘faster as a debugger’. Download MEX, load it into Windbg with the .load command and check it out.
-Ron
Comments
- Anonymous
September 29, 2016
I wonder why this is where I get when I go to https://blogs.msdn.microsoft.com/blog ...Also, I think there''s a typo in your title/logo: there should probably not be a space between INT and 3 if you want the single-byte breakpoint instruction. Fortunately, the URL already lacks the space :-)And I'm kind of confused by the red highlight, as the instruction has no operand field, and in any case 00110011 doesn't particularly resemble CCh or 3.- Anonymous
September 29, 2016
Samuel - Section 2.1.4 of the Intel® 64 and IA-32 Architectures Software Developer’s Manual located at http://download.intel.com/design/processor/manuals/253668.pdf classifies the instruction as "INT 3" with the space. That was our intent too. The red highlight of the 3 was an ASCII to binary translation of the character '3' represented as 0011 0011 (http://www.bing.com/images/search?q=ascii+to+binary&view=detailv2&&id=0C0096C5C20FDA6C6ECC717D4C4387631A7BFD90&selectedIndex=0&ccid=Bh5obNeg&simid=608004715585736400&thid=OIP.M061e686cd7a03e3fb0742cbcf73a14e9o0&ajaxhist=0). Just a raw memory dump but something we can easily change to 00000011:) Let me know if you would like an INT 3 t-shirt. We're working on a batch to send out near the end of the year. Thanks for the comments.
- Anonymous
