Configure Privileged Access Management(PAM) in an Existing Domain
With the new release of Microsoft Identity Manager (MIM) 2016, a new feature PAM is added to help organizations restrict privileged access to some certain security groups. However, if you read through the TechNet guide, it is recommended to create a new trusted domain. Then is it a mandatory to have another new domain to leverage the PAM feature? The answer is NO, we can actually just leverage the JIT evaluation which is called “Priv Only” Mode.
Note: As PAM is part of the lateral movement protection controls for securing privileged access, "Priv only" mode is ONLY supported in lab environment not in Production.
In the lab environment, I deployed the PAM component and MIM Service in the existing CONTOSO domain. Then I run below PowerShell Cmdlets (PAM module) to prepare PAM environments. Please pay attention to the parameter switch PrivOnly allows you to indicate the group already exists in the contoso domain.
New-PAMGroup -SourceDomain contoso -SourceGroupName ITAdmins -PrivOnly
After the successful execution of the cmdlet, you shall be able to query the PAM groups as below screen shows. It is a manually managed security group with msidmPamEnabled set to True and some other pam related attributes set
Then it’s time to setup the PAM roles by specifying some parameters including the PAM groups , candidates and other advanced features like Approval and MFA. Here I just keep the default configuration: once any one of the candidates submit the PAM request, he/she will be added to the two security groups: ITAdmins and HRAdmin together for the next following hour.
Finally it’s time to test the privilege access either via Powershell cmdlet or the sample PAM portal. Once I submit the request via the portal, the access will be activated and the below events will be logged under Applications and Services Logs/Privileged Access Management 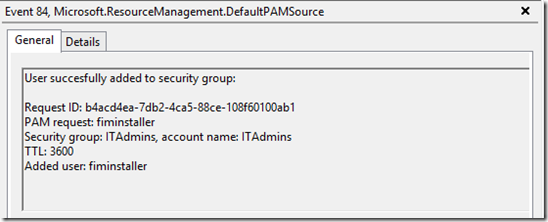
Then PAM monitor Service will remove them automatically when the access expires and log an event as below under the same event catalog.
In a nutshell, following above steps you shall still be able to setup the PAM solution without adding a new privileged domain.
Comments
- Anonymous
September 08, 2016
I just did a blog post on this topic (Using PAM in an existing forest) with more detailshttps://tlktechidentitythoughts.wordpress.com/2016/09/07/mim-2016-setting-up-privileged-access-management-pam-in-an-existing-domain-using-the-built-in-pam-tool/ - Anonymous
September 16, 2016
Very good post. I just did a blog post on this topic (Using PAM in an existing forest) with some more detailshttps://tlktechidentitythoughts.wordpress.com/2016/09/07/mim-2016-setting-up-privileged-access-management-pam-in-an-existing-domain-using-the-built-in-pam-tool/


