My working environment - Part 2
Second post on this subject. This time I will deal with the technical steps involved to build my environment.
Machines setup
Server Core configuration
I will not describe all the steps involved but I will give the commands I used on my Server Core servers to set the general settings of a server when it enters in production.
Add or install drivers
Add to the Driver Store :
PNPUTIL -a %homedrive%\<driver folder>\<driver>.inf
Add to the driver store and install :
PNPUTIL -i -a %homedrive%\<driver folder>\<driver>.inf
Rename a computer
NETDOM RENAMECOMPUTER %COMPUTERNAME% /NEWNAME:TOTO
Configure network connections and TCP/IP
Rename a network connection :
NETSH INT SET INT NAME="Local Area Connection" NEWNAME="CorpNet"
Set an IP v4 address, mask and gateway :
NETSH INT IPV4 SET ADDR NAME="CorpNet" STATIC 192.168.2.3 255.255.255.0 192.168.2.1
Add another IP v4 address, mask and gateway :
NETSH INT IPV4 SET ADDR NAME="CorpNet" STATIC 192.168.14.3 255.255.255.0 192.168.14.1
Specify DNS servers :
NETSH INT IPV4 SET DNSSERVER NAME="CorpNet" STATIC 192.168.14.60 BOTH
Netsh Commands for Wired Local Area Network (LAN)
Netsh Commands for Wireless Local Area Network (WLAN)
Join a domain
NETDOM JOIN %COMPUTERNAME% /DOMAIN:dom.local /userD:DOM\User /passwordD:*
Add a domain user/group to a local group
NETDOM LOCALGROUP Administrators DOM\User /add
Enable Remote Desktop for administration
CSCRIPT %WINDIR%\System32\scregedit.wsf /ar 0
Enable Windows Updates
CSCRIPT %WINDIR%\System32\scregedit.wsf /AU 4
Install Roles and Features
List roles and features :
OCLIST
Install a role :
START /W OCSETUP FailoverCluster-Core /QUIET /NORESTART
Uninstall a role :
START /W OCSETUP /UNINSTALL FailoverCluster-Core /QUIET /NORESTART
Enable remote administration
NETSH ADVFIREWALL SET ALLPROFILES SETTINGS REMOTEMANAGEMENT ENABLE
iSCSI Initiators configuration
As my cluster runs on Server Core servers, I had to use the CLI provided by the iSCSI components.
Configure the iSCSI service to start automatically :
SC CONFIG MSISCSI START= AUTO
Start the iSCSI service :
NET START MSISCSI
Add a iSCSI target portal :
ISCSICLI QADDTARGETPORTAL 192.168.2.2
List targets available :
ISCSICLI LISTTARGETS
You should have something like this as a result :
Microsoft iSCSI Initiator Version 6.0 Build 6000
Targets List: iqn.1991-05.com.microsoft:iscsiserver-s-iscsiclient-target The operation completed successfully.
Login to the target available :
ISCSICLI QLOGINTARGET iqn.1991-05.com.microsoft:iscsiserver-s-iscsiclient-target
Set the previous login persistent while restarting the computer :
ISCSICLI PERSISTENTLOGINTARGET iqn.1991-05.com.microsoft:iscsiserver-s-iscsiclient-target T * * * * * * * * * * * * * * * 0
Microsoft iSCSI Software Initiator Version 2.07
Cluster preparation
Continuing the configuration of the physical cluster under a command prompt I have to use cluster.exe.
First, I had to prepare the quorum disk (which is my disk 1, disk 0 being my system disk) :
C:\diskpart.exe
DISKPART> SELECT DISK1
DISKPART> ONLINE DISK
DISKPART> ATTRIB DISK CLEAR READONLY
DISKPART> CREATE PART PRI
DISKPART> ASSIGN LETTER Q:
DISKPART> FORMAT FS=NTFS LABEL=Quorum QUICK
DISKPART> AUTOMOUNT
DISKPART> DETAIL DISK
Note the DISK ID (if MBR then Disk Signature, if GPT then Disk GUID)
DISKPART> EXIT
I created my cluster :
C:\CLUSTER CLUSTER-FC /CREATE
C:\CLUSTER /CLUSTER:CLUSTER-FC RES "Quorum Disk" /CREATE /GROUP:"Cluster Group" /TYPE:"Physical Disk"
C:\CLUSTER /CLUSTER:CLUSTER-FC RES "Quorum Disk" /PRIV DiskSignature=0xA81F6D69
I used the DISK ID I identified in the previous step
C:\CLUSTER /CLUSTER:CLUSTER-FC RES "Quorum Disk" /ON
C:\CLUSTER /CLUSTER:CLUSTER-FC /QUORUM:"Quorum Disk"
I added the second node of my cluster :
C:\CLUSTER /CLUSTER:CLUSTER-FC /ADDNODE /NODE:NODE2
To create other resources in my cluster I used the Failover Clustering MMC from my laptop. It was quite easier !
Hyper-V installation
On my Hyper-V server, I first downloaded the Hyper-V Update for Windows Server 2008 x64 Edition (KB950050) and I ran the following command on my Hyper-V server (which is a Server Core) :
C:\WUSA C:\SRC\KB950050.MSU /QUIET
Then I installed the role :
C:\START /W OCSETUP Microsoft-Hyper-V
On my laptop, I downloaded the Hyper-V Remote Management Update for Windows Vista for x64-based Systems (KB952627) and installed it locally.
I was then able to manage my Hyper-V server remotely.
Virtual Server 2005 R2 SP1 installation
I first installed all IIS requirements :
- Web Server
- Common HTTP features
- Static Content
- Default Document
- Directory Browsing
- HTTP Errors
- Application Development
- CGI
- Health and Diagnostics
- HTTP Logging
- Request Monitor
- Security
- Basic Authentication
- Windows Authentication
- Digest Authentication
- Request Filtering
- Performance
- Static Content Compression
- Management Tools
- IIS Management Console
- IIS 6 Management Compatibility
- IIS 6 Metabase Compatibility
- IIS 6 WMI Compatibility
- IIS 6 Scriping Tools
- IIS 6 Management Console
- Common HTTP features
On my Virtual Server server I downloaded the following components and installed them as any other applications :
- Microsoft Virtual Server 2005 R2 SP1 - Enterprise Edition
- Microsoft Virtual Server 2005 R2 SP1 Update
Note : installing the update requires an elevated Command Prompt
Release Notes for Virtual Server 2005 R2 SP1
DPM 2007 installation
Some hints I used to install DPM 2007 on a Windows Server 2008 :
Manually Install Required Windows Components
Manually Install SQL Server 2005
Installing Protection Agents behind a Firewall
SCVMM 2008 installation
Well... I cannot explain how I did... the product is not released yet :-)
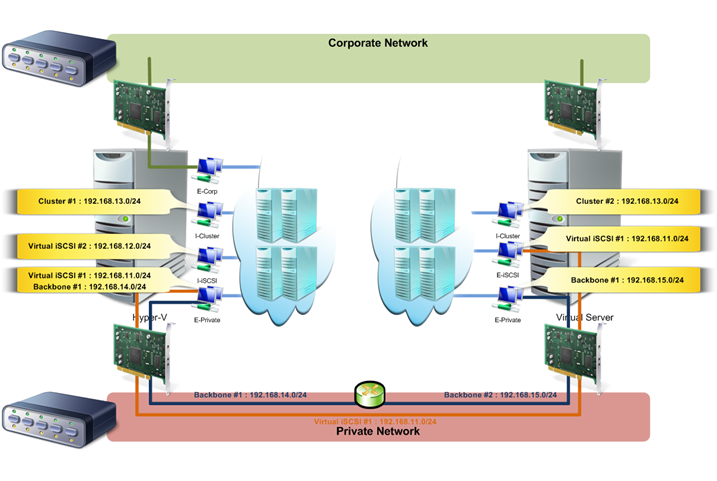
How did I set up my network ?
In my configuration I use two different physical networks. One is the Corporate Network on which I have no power at all and the second one is dedicated to private communication for my own stuff which consists of iSCSI and virtual machines traffic.
I have to use a separate network because we have strong security policies internally enforced to Windows Firewall and IPSec so I cannot run all scenarios I want on this side. All NICs connected on non-MS network do not suffer from that security and thus allowed me to set up my cluster with iSCSI without any trouble.
Additionally, I want to have two separated subnets on my private network two have an environment with a bit more complexity than a single IP range on a physical network.
Physical subnetting
I have nothing to say about the Corporate Network side. All my physical machines are connected to it and receive IPv4 and IPv6 addresses from the corporate DHCP server.
From the private network side, totally disconnected from the Corporate Network, here are the subnets used :
- 1 IP subnet for virtual machines hosted on the Hyper-V server
- Private Network #1 : 192.168.14.0/24
- 1 IP subnet for virtual machines hosted on the Virtual Server server
- Private Network #2 : 192.168.15.0/24
- 1 IP subnet for my physical iSCSI network
- iSCSI Network #1 : 192.168.12.0/24
In fact IP subnets of Private Network #1 and Private Network #2 are totally logical as they rely on the same network switch. These subnets exist because virtual machines on the Hyper-V server are configured with a 192.168.14.x address and virtual machines on the Virtual Server server are configured with a 192.168.15.x address.
In addition, my HP xw6200 has two IP addresses on the private NIC which are 192.168.14.1 and 192.168.15.1. As I installed the Routing and Remote Access Services role traffic between these two subnets is routed.
Virtual subnetting
I have several subnets configured :
- 1 IP subnet for a primary backbone (on the Hyper-V server)
- Backbone #1 : 192.168.14.0/24
- 1 IP subnet for a secondary backbone(on the Virtual Server server)
- Backbone #2 : 192.168.15.0/24
- 1 IP subnet for iSCSI traffic (on the Virtual Server server and on the Hyper-V Server)
- Virtual iSCSI #1 : 192.168.11.0/24
- 1 IP subnet for iSCSI traffic (on the Hyper-V server)
- Virtual iSCSI #2 : 192.168.12.0/24
- 1 IP subnet for clusters' traffic (on the Hyper-V server)
- Cluster #1 : 192.168.13.0/24
- 1 IP subnet for clusters' traffic (on the Virtual Server server)
- Cluster #2 : 192.168.13.0/24
All subnets still be logical as they rely on virtual network which reside on only one NIC on each virtualization server.
My HP xw6200 routes traffic as well between 192.168.14.1 and 192.168.15.1 subnets.
A schema to better understand
Routing
To allow routing between my two "backbones", I had to set up RRAS on my HP xw6200.
Routing and Remote Access Service configuration
- From Start | Programs | Administrative Tools | Routing and Remote Access
- Select the server you want to configure
- Menu Action | Configure and Enable Routing and Remote Access
- Click on Next
- Select Custom configuration and click on Next
- Select LAN Routing and click on Next
- Click on Finish
- Click on Start service
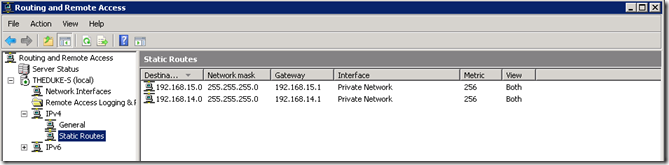
Routing configuration
- Select <Servername> | IPv4 | Static routes
- Menu Action | New static route…
- Interface : select the physical adapter to configure (ex : Private Network)
- Destination : IP address of the target network to route to (ex : 192.168.5.0)
- Network Mask : second IP subnet mask (ex : 255.255.255.0)
- Gateway : IP address of the first IP subnet's gateway (ex : 192.168.6.1)
- Click on OK
Apply the same steps for the second IP subnet, you should obtain this configuration :
If I had two physical interfaces for my private network, while configuring routing for the second subnet, I should select the second physical interface and repeat the steps.
DHCP Relay configuration
If I had two physical interfaces for my private network I should have to allow PXE broadcast over my two IP subnets to allow PXE traffic. Currently I don't need as broadcasts are on the same physical network.
In the case you have to enable it :
- Select <Servername> | IPv4 | General
- Menu Action | New Routing Protocol…
- Select DHCP Relay Agent and click on OK
- Select <Servername> | IPv4 | DHCP Relay Agent
- Menu Action | New Interface…
- Select the physical adapter which represent the subnet on which reside PXE clients and click twice on OK
- Menu Action | New Interface…
- Select the physical adapter which represent the subnet where the DHCP and/or WDS servers are located and click twice on OK
- Menu Action | Properties
- Add IP addresses of the DHCP and/or WDS servers and click on OK
Virtual networks configuration ?
I have then to configure some virtual networks on my Hyper-V and Virtual Server servers to make all my virtual machines communicate together.
Hyper-V virtual networks
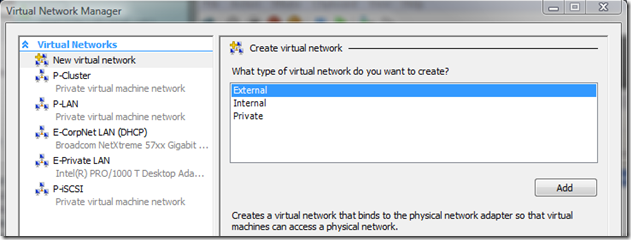
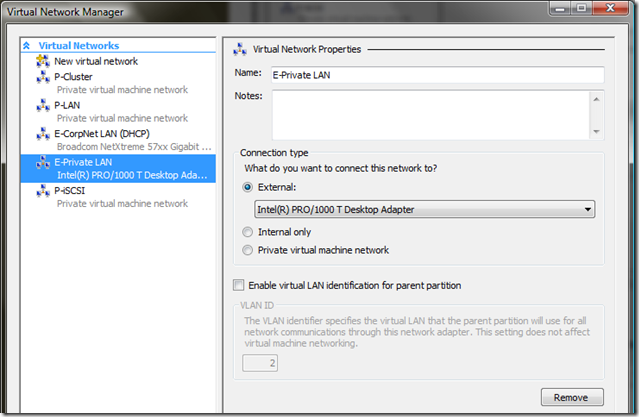
You should know that Hyper-V provides three types of virtual networks :
- External which is bound to a physical network adapter and allow communication of virtual machines on a physical network
- Internal which is a private network between virtual machines and their host
- Private which is a truly virtual network on which only virtual machines can be bound
I adopted a basic taxonomy for my virtual networks to be able to quickly identify which access a virtual network provides :
- For External networks : E-[Description]
- For Internal networks : I-[Description] [IP subnet definition)]
- For Private networks : P-[Description] [IP subnet definition)]
In my configuration I have this :
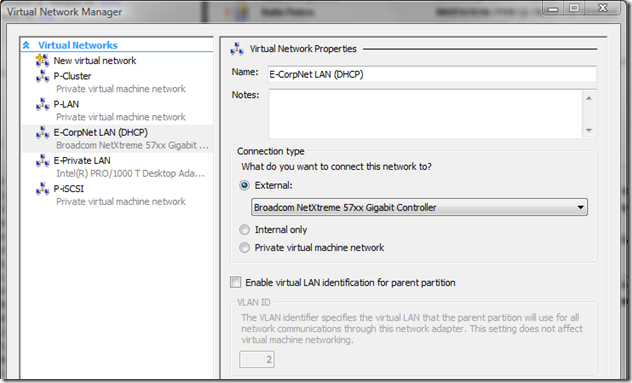
- E-CorpNet LAN configuration :
- Used to attach virtual machines to the Corporate Network
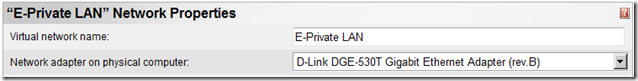
- E-Private LAN configuration :
- Used to provide communication over my private network to my virtual machines between my Hyper-V and Virtual Server servers
There is no specific configuration for the remaining virtual networks as they are Private networks and only used for virtual machines communications :
- P-Cluster : bound to Windows clusters to assume the private network between nodes
- P-iSCSI : bound to Windows clusters and some stand-alone servers for the virtual iSCSI network
- P-LAN : bound to any virtual machines not requiring access to other resources
Virtual Server virtual networks
The configuration on the Virtual Server is more simple as you can choose only between a virtual network bound to a physical network adapter or a virtual network allowing only guests communication.
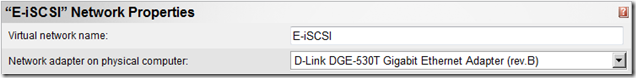
- The following virtual network is bound to the private NIC on the Virtual Server server and is intended to be used for iSCSI traffic to the HP xw6200 which services the iSCSI Software Target Initiator :
- The following virtual network is also bound to the private NIC on the Virtual Server server and used as a backbone for virtual machines :
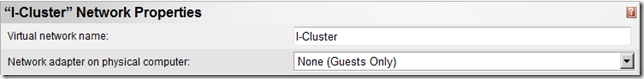
- The following virtual network is not bound to any physical NIC on the Virtual Server server and is used as the private network for virtual machines running in a cluster :
Well, quite a long post. I hope I covered the main points but if I missed some stuff or if you ask for more : let me know !
Next time I'll describe my virtual machines and how I used some technologies to set up virtual machines quickly.
To be continued...
~ Guillaume
Comments
Anonymous
January 01, 2003
PingBack from http://www.wlan-funktek.com/wlan/wordpress/2008/08/31/re-wenn-ich-wlan-hab-wlan-studie-unternehmen-unterschatzen-s-19/Anonymous
January 01, 2003
PingBack from http://www.mynetfaves.com/tags/subnet